Prisma Access
Remove Plugin Access for a Tenant-Level Administrative User
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Remove Plugin Access for a Tenant-Level Administrative User
Learn how to remove plugin access for a tenant-level administrative user.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
In normal multitenant configurations, you use
access domains Add Tenants to Prisma Access and associate
each access domain with a tenant. To prevent a tenant-level administrative
user from viewing or making configuration changes to Prisma Access,
you create an access domain, but you do not associate it with a
tenant.
Because you associated the access domain to the device
groups and template stacks for the tenant, the tenant-level administrative
user has RBAC access at the tenant level and is able to perform
configuration for that tenant only. Because you did not associate
the access domain with a tenant in Prisma Access, the access domain
is unable to view the Cloud Services plugin, which provides access
to Prisma Access. In this way, you create a user who can perform
tenant-level configuration tasks without being able to access, view,
or make configuration changes to Prisma Access.
To remove
Prisma Access for an administrative-level user, complete
the following task.
This task assumes that you have Add Tenants to Prisma Access templates,
template stacks, and device groups for the tenant; you’ll be associating
them to the tenant-level administrative user.
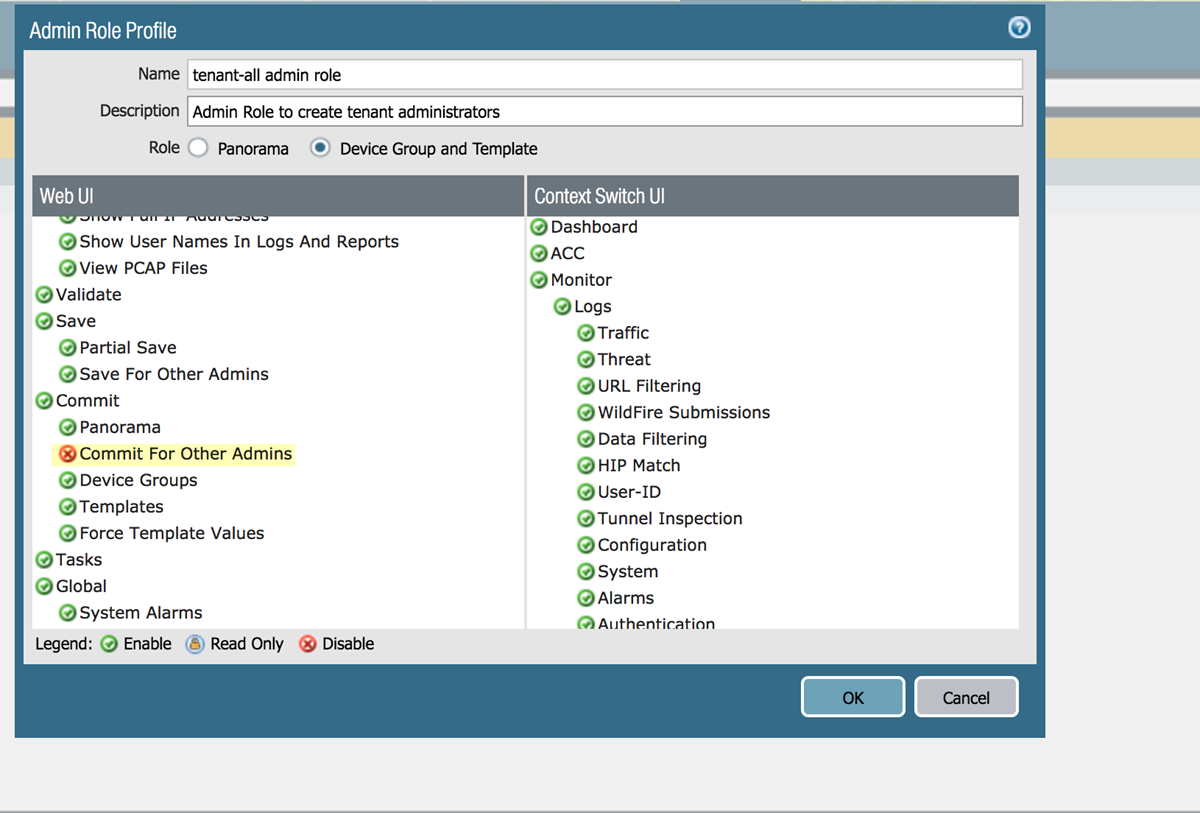
- Create an administrative role with a type of Device Group and Template.
- Select PanoramaAdmin Roles.Add an Admin Role Profile with a Role of Device Group and Template.Click OK.You can create a single Admin Role Profile and share it across multiple tenants.
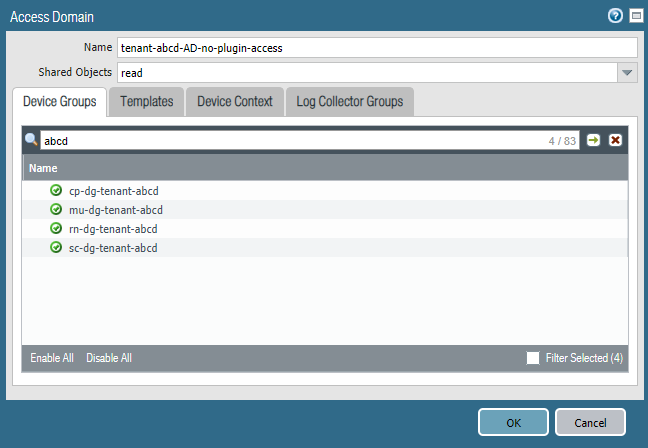
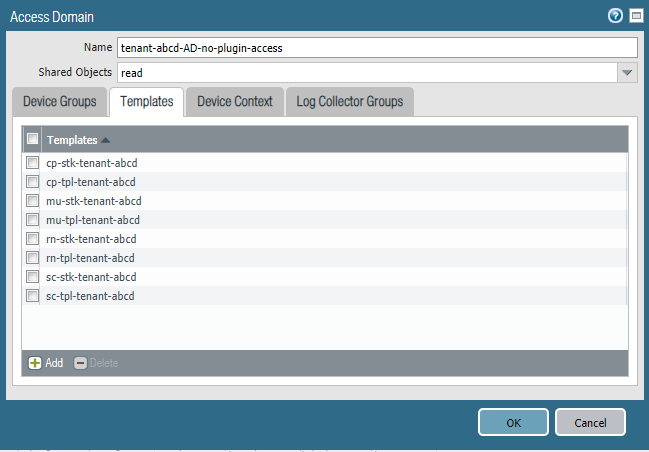
![]() Select PanoramaAccess Domain and Add an Access Domain.Specify the Device Groups and Templates associated with the tenant.If you created any device groups that are children or grandchildren of other device groups under the Shared parent device group, select only the device group at the lowest hierarchical level (child or grandchild); do not select the parent or you will have errors on commit.
Select PanoramaAccess Domain and Add an Access Domain.Specify the Device Groups and Templates associated with the tenant.If you created any device groups that are children or grandchildren of other device groups under the Shared parent device group, select only the device group at the lowest hierarchical level (child or grandchild); do not select the parent or you will have errors on commit.![]()
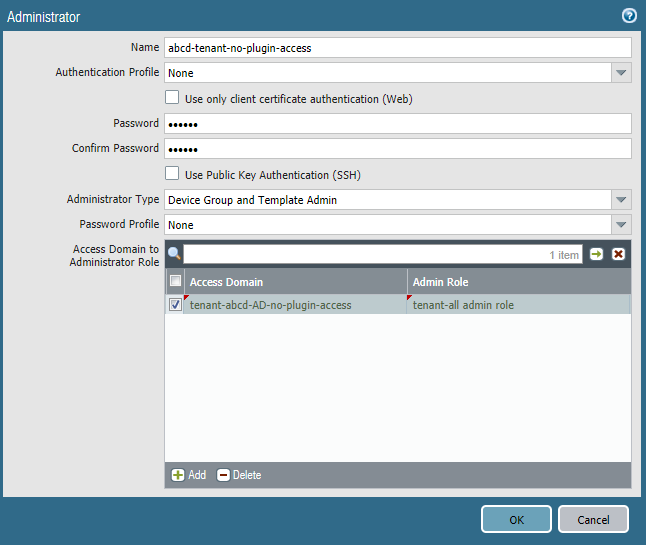
![]() Create and configure an Administrator for the tenant-level administrative user, specifying the Access Domain you just created.
Create and configure an Administrator for the tenant-level administrative user, specifying the Access Domain you just created.- Select PanoramaAdministrators.Add an Administrator.Enter and confirm a Password for the new Administrator.Specify an Administrator Type of Device Group and Template Admin.Specify the Access Domain that is associated with the device groups for that tenant.Specify the Admin Role that you created in Step 1 for the tenant.When you complete this example, the abcd-tenant-no-plugin-access Administrative user will have permissions based on what you defined in the Admin Role profile, but will not be able to view or configure the Cloud Services plugin (including Prisma Access). Note, however, that they will not be able to push any changes that they make to the cloud.
![]() Select CommitCommit to Panorama and Commit your changes.
Select CommitCommit to Panorama and Commit your changes.