Prisma Access
Configure Multiple Portals in Prisma Access (Panorama)
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Configure Multiple Portals in Prisma Access (Panorama)
Learn how to configure multiple portals with multiple authentication methods in Prisma Access (Managed by Panorama).
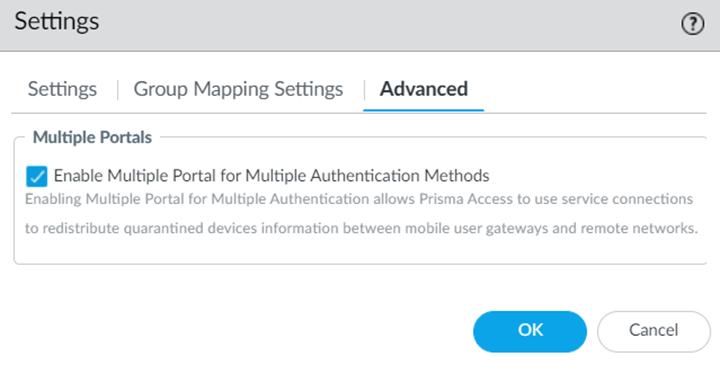
- Contact your Palo Alto Networks account representative to activate this functionality.When configuring multiple GlobalProtect portals with Traffic Steering, do not configure Accept Default Routes over Service Connections (PanoramaCloud ServicesConfigurationTraffic SteeringSettingsAccept Default Route over Service Connection); if you do, mobile users cannot connect to the secondary portal.Configure a mobile user and the authentication method for it.Select Cloud ServicesConfigurationMobile Users—GlobalProtectSettingsAdvanced.Enable Multiple Portal for Multiple Authentication Methods.
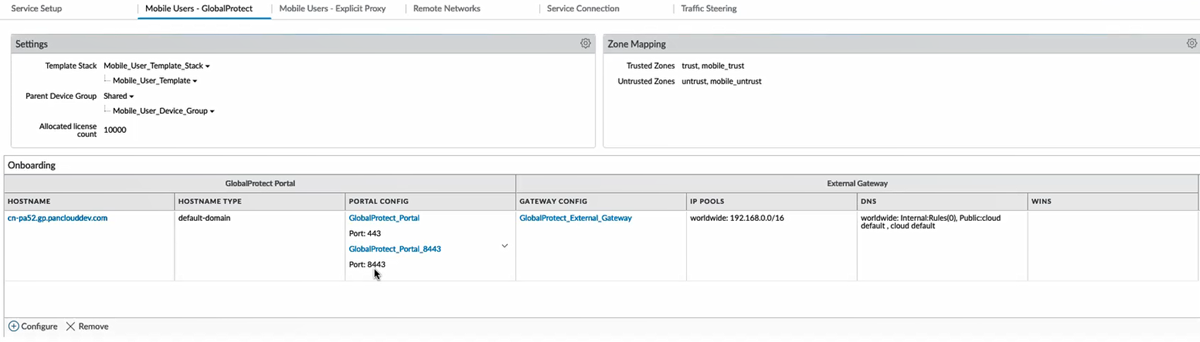
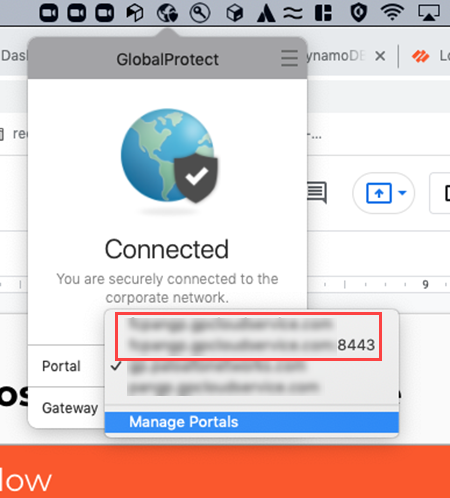
![]() The new portal appears for the 8443 port for the same tenant. This portal inherits the configuration settings from the original port, which is port 443.
The new portal appears for the 8443 port for the same tenant. This portal inherits the configuration settings from the original port, which is port 443.![]() Edit the portal configurations to update the authentication settings.
Edit the portal configurations to update the authentication settings.- Click the portal hyperlink or select PanoramaTemplatesNetworkGlobalProtectPortals and click the portal hyperlink.In the Authentication section, Add a Client Authentication with a different Authentication Profile.You can edit only the Client Authentication and Certificate Profile authentication settings.If you use certificate-based authentication in both portals, ensure that both portals use the same client certificate profile for authentication.
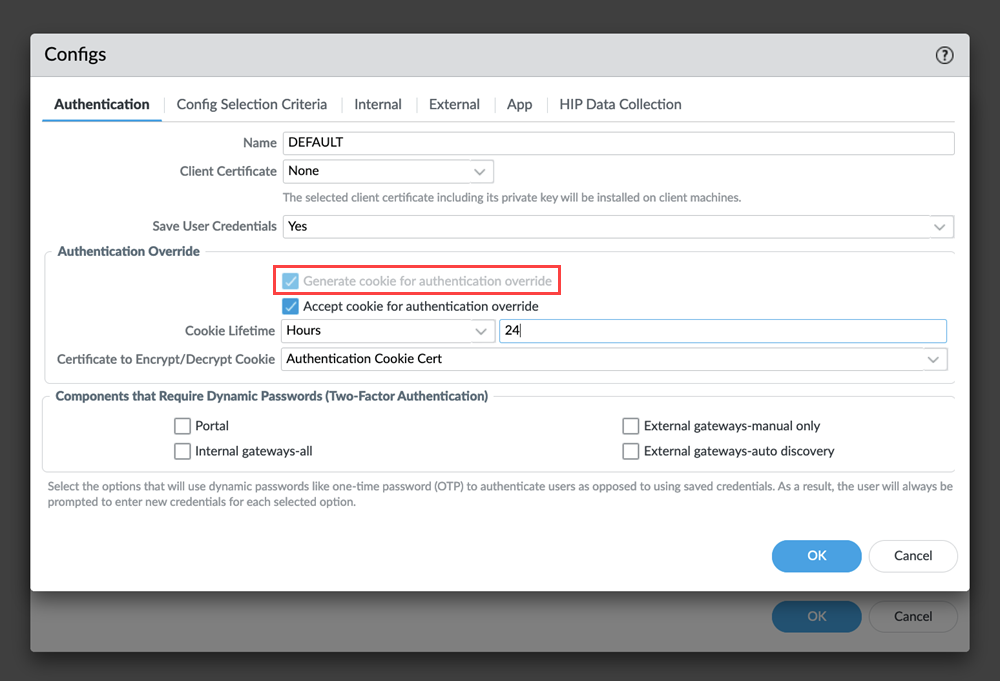
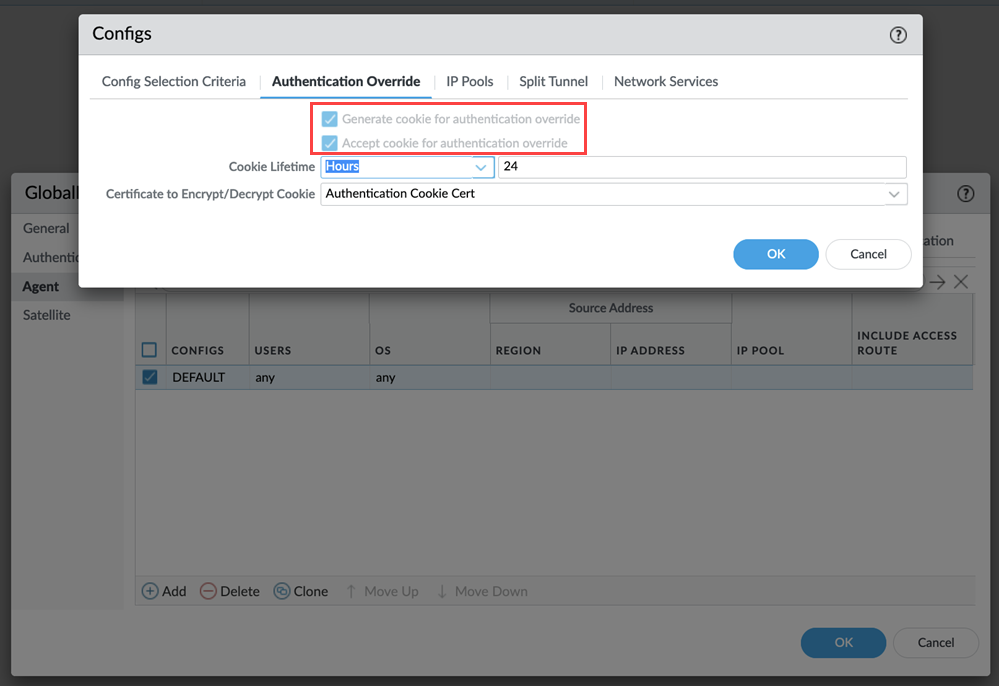
![]() This feature enables the authentication override settings to generate and accept cookie for both portals in the tunnel settings.
This feature enables the authentication override settings to generate and accept cookie for both portals in the tunnel settings.![]() Commit all your changes to Panorama and push the configuration changes to Prisma Access.
Commit all your changes to Panorama and push the configuration changes to Prisma Access.- Click CommitCommit and Push.Edit Selections and, in the Prisma Access tab, make sure that Mobile Users is selected in the Push Scope, then click OK.
![]() Click Commit and Push.Add the portals manually or using endpoint management software in the GlobalProtect app.Verify if you can connect to both portals with different authentication profiles for the gateway.
Click Commit and Push.Add the portals manually or using endpoint management software in the GlobalProtect app.Verify if you can connect to both portals with different authentication profiles for the gateway.- Log in to your Windows machine.Connect to the portals in your GlobalProtect app.When you change the connection between portals of different authentication methods, authenticate the user login.
![]() If the authentication cookie expires when you connect to the 8443 portal and switch to the manual gateway, GlobalProtect connects to the Best Available Gateway.If your GlobalProtect app uses cached portal configurations, fallback to portal does not work.View logs for both portals in MonitorLogsGlobalProtect to see the portal and authentication information.If you're using SAML-based authentication for the secondary portal, enter the values as follows while integrating:
If the authentication cookie expires when you connect to the 8443 portal and switch to the manual gateway, GlobalProtect connects to the Best Available Gateway.If your GlobalProtect app uses cached portal configurations, fallback to portal does not work.View logs for both portals in MonitorLogsGlobalProtect to see the portal and authentication information.If you're using SAML-based authentication for the secondary portal, enter the values as follows while integrating:- Single sign on URL: Enter
https://Portal-FQDN:443/SAML20/SP/ACSPortal-FQDN is the FQDN for the Prisma Access portalUse portal 443 even if you have configured the secondary portal (8443).
- Audience URI (SP Entity ID): Enter https://Portal-FQDN:443/SAML20/SP