Prisma Access
Cloud Identity Engine Authentication for Explicit Proxy Deployments (Strata Cloud Manager)
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Cloud Identity Engine Authentication for Explicit Proxy Deployments (Strata Cloud Manager)
Use the Cloud Authentication (CAS) component of the Cloud Identity Engine to
authenticate Prisma Access mobile users in a Mobile Users—Explicit Proxy deployment.
The Cloud Identity Engine provides both user
identification and user authentication for mobile users in a Prisma Access—Explicit
Proxy deployment. The Cloud Identity Engine integrates with the Explicit Proxy Authentication Cache Service (ACS) and
uses SAML identity providers (IdPs) to provide authentication for Explicit Proxy
mobile users.
To configure authentication for a Mobile Users—Explicit Proxy deployment using the
Cloud Identity Engine, complete the following steps.
- In Prisma Access (Managed by Strata Cloud Manager), set up Explicit Proxy for your tenant.Before you configure Explicit Proxy, be aware of how explicit proxy works and the guidelines to use when you configure it.If you have multiple tenants, configure Explicit Proxy for each of your tenants that require it.Log in to the hub and, from the Cloud Identity Engine app, set up an authentication type and authentication provider.You can view apps in the hub by tenant or by support account.
- Configure a SAML authentication type in the Cloud Identity Engine.The Cloud Identity Engine Getting Started guide has the procedures you need to configure a SAML IdP in the Cloud Identity Engine:Do not configure single logout, it is not supported.Set up an authentication profile in the Cloud Identity Engine and select the users and groups that can use this authentication method.You specify this profile when you create an authentication profile in Prisma Access (Managed by Strata Cloud Manager) in a later step.Return to Prisma Access (Managed by Strata Cloud Manager) and create an authentication profile to use with the Cloud Authentication Engine.
- Go to ConfigurationNGFW and Prisma AccessIdentity ServicesAuthentication, set the scope to Explicit Proxy, and add an authentication profile (Add Profile).Select an Authentication Method of Cloud Identity Engine.Give the profile a Profile Name.Select the Cloud Identity Engine Authentication Profile you created in a previous step.Save your changes.Set up user authentication in Explicit Proxy.
- Go to Configuration NGFW and Prisma AccessConfiguration ScopePrisma AccessExplicit Proxy and Set Up User Authentication.Select an Authentication Method of SAML/CIE.Select the authentication profile you created in Cloud Managed Prisma Access.Specify a Cookie Lifetime for the cookie that stores the users’ authentication credentials.After the IdP authenticates the user, Prisma Access stores the authentication state of the user in the Authentication Cache Service (ACS). The validity period of the authentication is based on the Cookie Lifetime value you specify here.To prevent issues with users not being able to download large files before the cookie lifetime expires, or the cookie expiring when users are accessing a single website for a long period of time, Palo Alto Networks recommends that you configure a Cookie Lifetime of at least one day. If Explicit Proxy users have a cookie lifetime expiration issue, they can browse to a different website to re-authenticate to ACS and refresh the ACS cookie.Save your changes.Verify that the Cloud Identity Engine is successfully authenticating your Explicit Proxy mobile users.
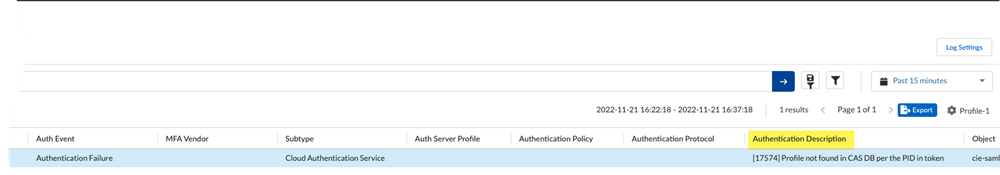
- From Prisma Access (Managed by Strata Cloud Manager), select Incidents & AlertsLog ViewerFirewall/Authentication.View the Auth Event status.If the authentication fails, view the Authentication Description for more details about the failure.
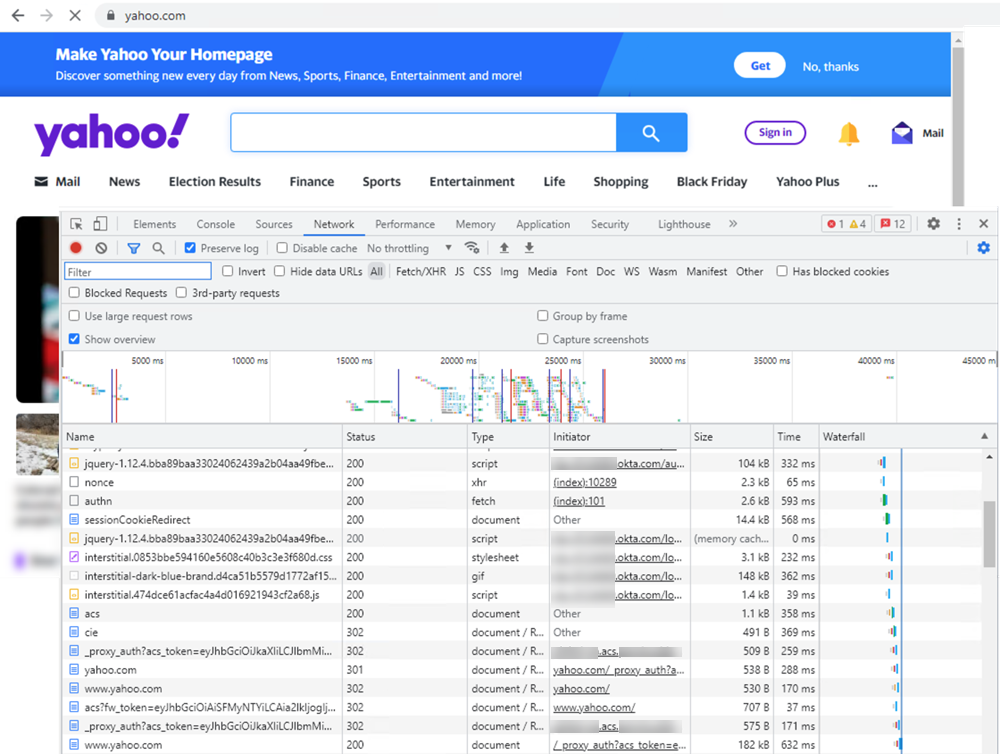
![]() From the mobile user’s endpoint, use dev tools to view the Cloud Identity Engine authentication flow.
From the mobile user’s endpoint, use dev tools to view the Cloud Identity Engine authentication flow.![]()