Prisma Access
GlobalProtect — Customize Tunnel Settings (Panorama)
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
GlobalProtect — Customize Tunnel Settings (Panorama)
Define tunnel settings for GlobalProtect app.
You can configure split tunnel settings based on either Access Route or Domain and
Application.
- Configure split tunnel settings based on Access Route.
- Click Panorama > Network > GlobalProtect > Gateways and select the gateway you want to customize.
- Click Agent > Client Settings and select the config.
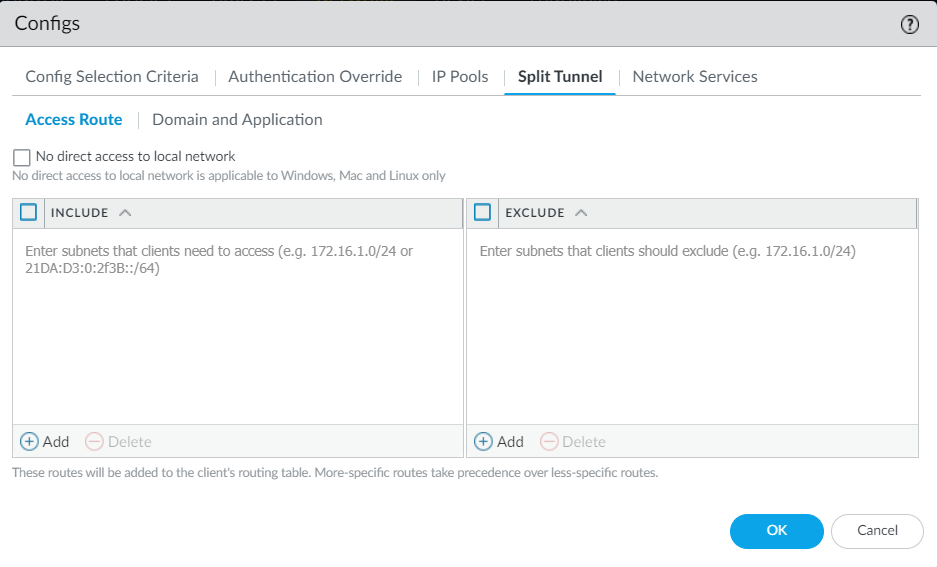
- Click Split Tunnel > Access Route. The split tunnel settings
are assigned to the virtual network adapter on the endpoint when the
GlobalProtect app establishes a tunnel with Prisma Access. You can
include or exclude specific destination IP subnet traffic from being
sent over the VPN tunnel.
![]()
- Enable No direct access to local network option to
stop users from sending traffic directly to proxies or local
resources while connected to GlobalProtect. Enable the No direct access to local network setting to reduce risks in untrusted networks such as rogue Wi-Fi access points.This setting is applicable to Windows, Mac and Linux endpoints only.
- Select Include and Add the destination subnets or address object (of type IP Netmask) to route only certain traffic destined for your LAN to GlobalProtect. You can include IPv6 or IPv4 subnets. To include all destination subnets or address objects, Include 0.0.0.0/0 and ::/0 as access routes.
- Select Exclude and Add the destination subnets or address object (of type IP Netmask) that you want the app to exclude. Excluded routes should be more specific than the included routes; otherwise, you may exclude more traffic than intended. You can exclude IPv6 or IPv4 subnets.You cannot exclude access routes for endpoints running Android on Chromebooks. Only IPv4 routes are supported on Chromebooks.
- Click OK to save the tunnel settings.
- Alternatively, configure split tunnel settings based on Domain and Application.
- Click Panorama > Network > GlobalProtect > Gateways and select the gateway you want to customize.
- Click Agent > Client Settings and select the config.
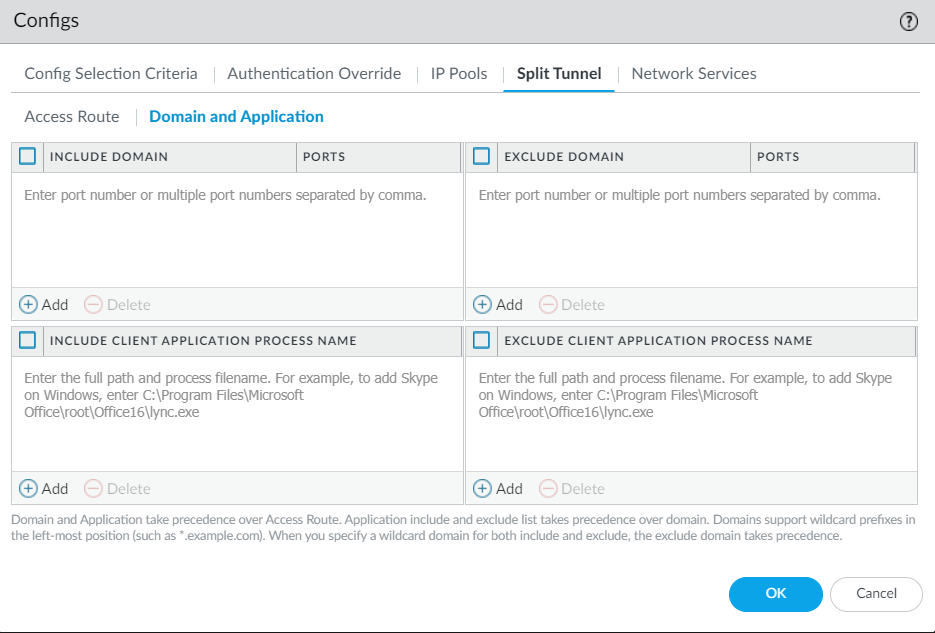
- Click Split Tunnel > Domain and Application tab to configure
split tunnel settings based on the destination domain. You might experience some incompatibility issues when using a third-party endpoint security product such as Sophos on macOS endpoints.
![]()
- (Optional) Select Include Domain and Add the SaaS or public cloud applications that you want to route to GlobalProtect through the VPN connection using the destination domain and port. You can add up to 200 entries to the list. For example, add *.gmail.com to allow all Gmail traffic to go through the VPN tunnel.
- (Optional) Select Exclude Domain and Add the SaaS or public cloud applications that you want to exclude from the VPN tunnel using the destination domain and port. You can add up to 200 entries to the list. For example, add *.target.com to exclude all Target traffic from the VPN tunnel.
- Configure split tunnel settings based on the application.Safari traffic cannot be added to the application-based split tunnel rule on macOS endpoints.You can use environment variables to configure a split tunnel based on the application on Windows and macOS endpoints.
- (Optional) Select Include Client Application Process Name and Add the SaaS or public cloud applications that you want to route to GlobalProtect through the VPN connection using the application process name. You can add up to 200 entries to the list.
- (Optional) Select Exclude Client Application Process Name and Add the SaaS or public cloud applications that you want to exclude from the VPN tunnel using the application process name. You can add up to 200 entries to the list.
- Save the tunnel settings.