Prisma Access
Integrate Prisma Access with Aryaka SD-WAN (Strata Cloud Manager)
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Integrate Prisma Access with Aryaka SD-WAN (Strata Cloud Manager)
set up Prisma Access for use with an Aryaka SD-WAN.
To set up Prisma Access for use with an Aryaka SD-WAN, complete the following
task.
- Configure the Prisma Access Service Infrastructure.Follow the steps to Connect a remote network to Prisma Access.When creating a new IPSec Tunnel during the onboarding procedure, make a note of the IPSec Tunnel name and the IKE Gateway and IPSec Crypto profile that you use.If you configure a pre-shared key (PSK) for the IKE Gateway, make a note of it; you enter this PSK when you configure the IPSec tunnel in Aryaka SmartConnect.Commit the configuration changes and push the configuration out to Prisma Access for remote networks.
- Click Push ConfigPushRemote NetworksPush.Make a note of the Service IP of the Prisma Access side of the tunnel. To find this address in Prisma Access (Managed by Strata Cloud Manager), select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote Networks. Look for the Service IP field corresponding to the remote network configuration you created.
Configure the IPSec Tunnel in Aryaka SmartConnect
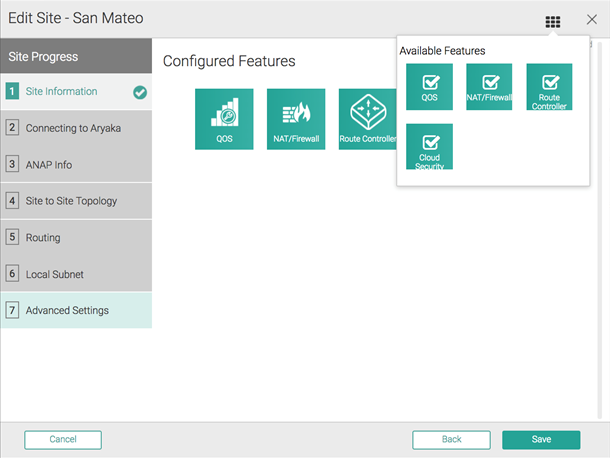
You configure Aryaka SmartConnect in the Cloud Security Connector section of the MyAryaka portal at https://my.aryaka.com/. Alternatively, you can contact the Aryaka support team to assist with the configuration.Your MyAryaka account must have write permission access to configure the Cloud Security Service. To verify that you have this access, log in to MyAryaka and select ConfigUser ManagementUsers.To complete the tunnel configuration for Aryaka SmartConnect, complete the following task.- Log in to MyAryaka and navigate to the SmartConnect site for which you want to deploy Prisma Access.Click Edit Site, then select Cloud Security from the list of Advanced Settings.
![]() Enter information for the remote network tunnel.Enter the following settings:
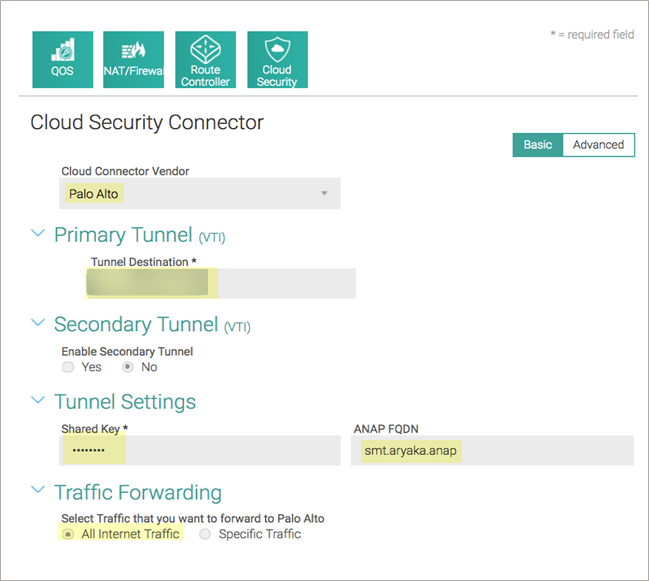
Enter information for the remote network tunnel.Enter the following settings:- Select Palo Alto in the Cloud Connector Vendor field.
- Enter the Service IP Address for the remote network tunnel from Prisma Access in the Primary TunnelTunnel Destination field.
- Enter the PSK value from the Prisma Access IKE gateway in the Tunnel SettingsShared Key field.
- Enter a FQDN for the Aryaka Network Access Point (ANAP), if the IP address of the M1/M2 interface is dynamic.
- Select All Internet Traffic in the Traffic Forwarding field.
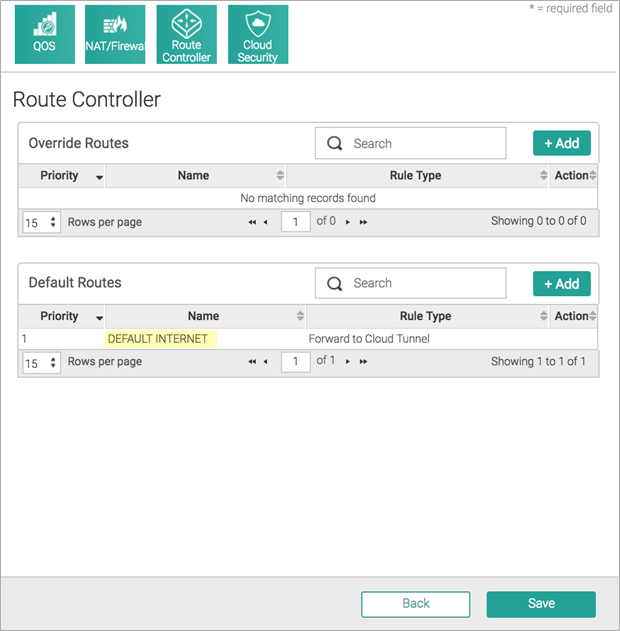
![]() After you choose to forward all internet traffic to Prisma Access, a default rule named DEFAULT INTERNET is inserted in the Route Controller, in the Default Routes section. The following screenshot shows the traffic forwarding settings.
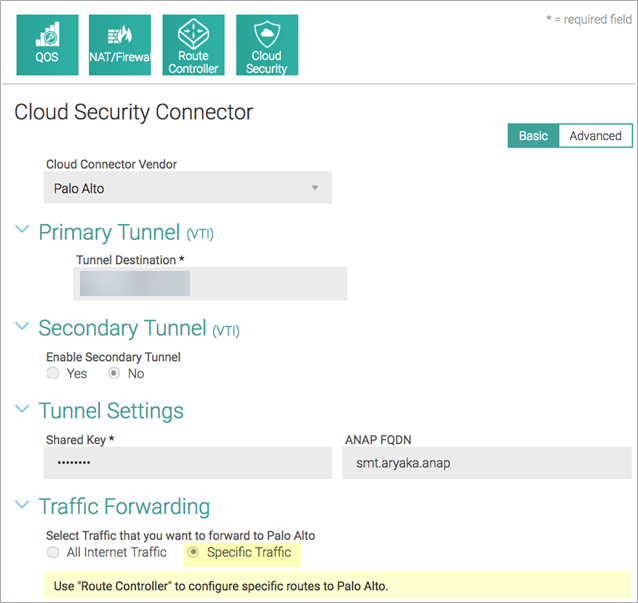
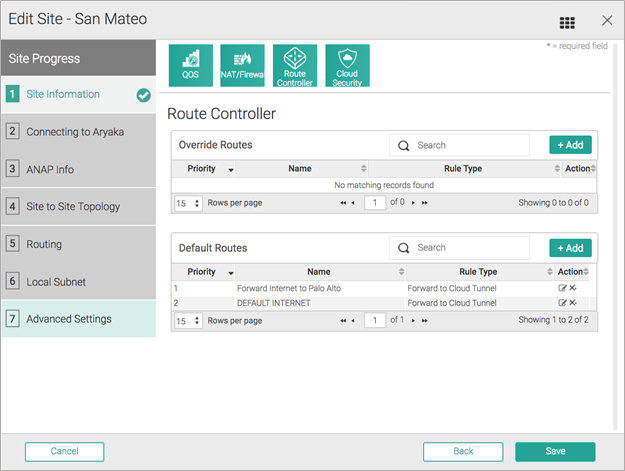
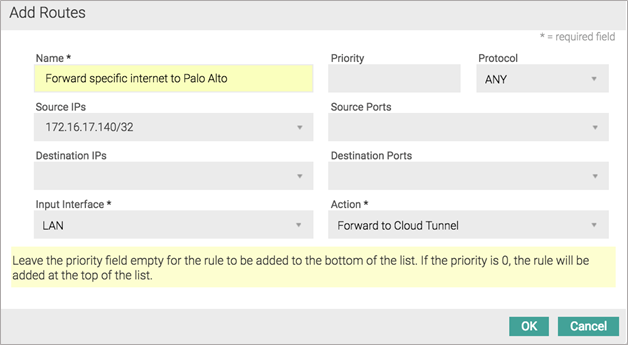
After you choose to forward all internet traffic to Prisma Access, a default rule named DEFAULT INTERNET is inserted in the Route Controller, in the Default Routes section. The following screenshot shows the traffic forwarding settings.![]() (Optional) If you choose to forward only specific internet traffic to Prisma Access, program appropriate routes in the Router Controller section.Aryaka recommends that you edit Default Routes and not override routes to control forwarding. Override routes take precedence over any Aryaka-destined traffic and may accidentally cause site-to-site traffic to be routed to Prisma Access.The following figures provide screenshots of the Route Controller feature.
(Optional) If you choose to forward only specific internet traffic to Prisma Access, program appropriate routes in the Router Controller section.Aryaka recommends that you edit Default Routes and not override routes to control forwarding. Override routes take precedence over any Aryaka-destined traffic and may accidentally cause site-to-site traffic to be routed to Prisma Access.The following figures provide screenshots of the Route Controller feature.![]()
![]()
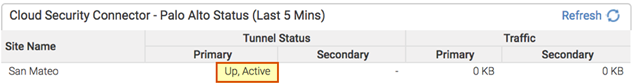
![]() Check the status of the tunnels.
Check the status of the tunnels.- To check the status from the Aryaka Cloud Security Connector, click the Status tab. Aryaka uses Dead Peer Detection (DPD) to determine the availability of the tunnel.
![]()
- To check the status from Prisma Access (Managed by Strata Cloud Manager), select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote NetworksRemote Networks Setup to verify that the remote network has been successfully deployed.
Monitor Remote Network Traffic
To monitor remote network tunnel traffic from the Aryaka SD-WAN, complete the following task.- Click the Monitor tab, then select Cloud Security Connector Traffic.Pick a reference site, select a time, and click Apply.To zoom in any of these graphs, click a graph and drag the cursor.
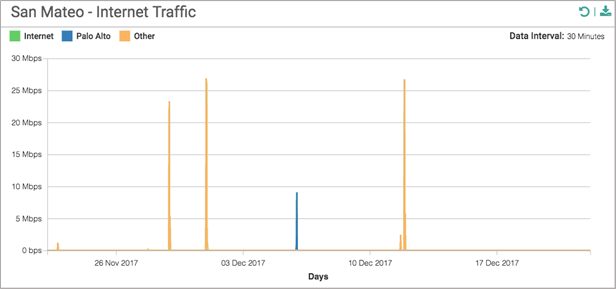
- The following information displays in the Internet Traffic graph:
- Total Internet—All traffic forwarded to the internet.
- Total Palo Alto —All internet traffic forwarded to Prisma Access.
- Total Other—All traffic forwarded to internet that isn't going to Prisma Access.
![]()
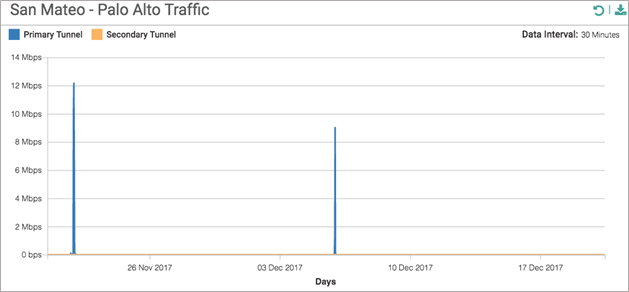
- The Palo Alto Traffic graph shows traffic data (in Mbps) over IPSec tunnels to Prisma Access for the time period that you select. This graph shows traffic flow in both directions to Prisma Access.
![]()
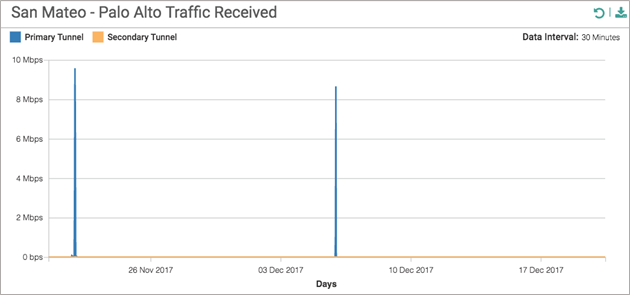
- The Palo Alto Received graph shows traffic received on the IPSec tunnels to Prisma Access. This graph shows all internet traffic inbound to the site from Prisma Access.
![]()
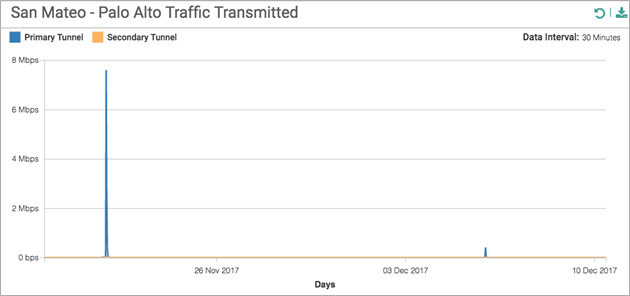
- The Palo Alto Transmitted graph shows all traffic that is transmitted on IPSec tunnels to Prisma Access. This graph shows all traffic outbound to Prisma Access from the site.
![]()
Troubleshoot the Aryaka Remote Network
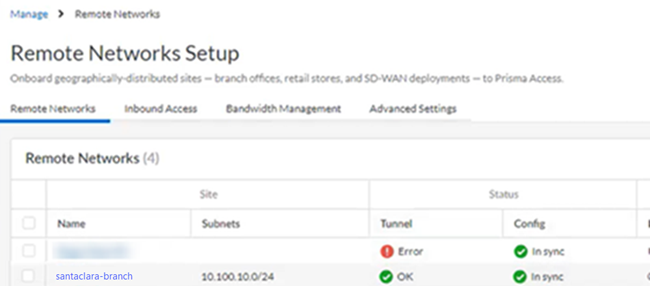
Prisma Access provides logs and widgets that provide you with the status of remote tunnels and the status of each tunnel.- Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote NetworksRemote Networks Setup and check the Status of the tunnel.
![]()
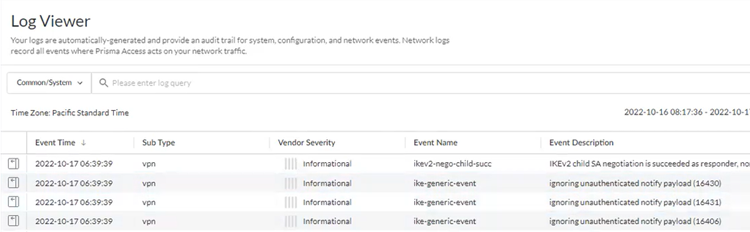
- Go to ActivityLog Viewer and check the Common/System logs for IPSec- and IKE-related messages.To view VPN-relates messages, set the filter to sub_type.value = vpn.The message ignoring unauthenticated notify payload indicates that the route has not been added in the crypto map on the other side of the IPSec tunnel after the IPSec negotiation has already occurred.
![]()
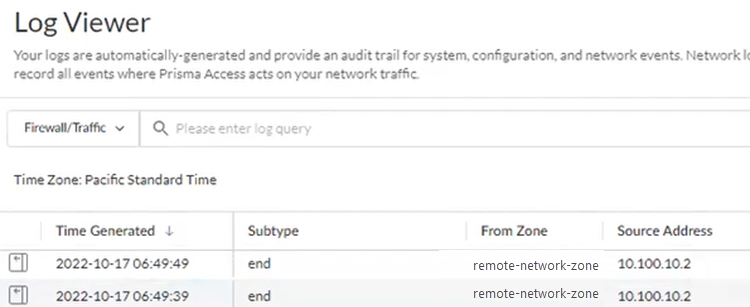
- Check the Firewall/Traffic logs and view the messages that are coming from the zone that has the same name as the remote network.In the logs, the remote network name is used as the source zone.
![]()