Prisma Access
Integrate Prisma Access with Cisco Catalyst SD-WAN (Manual Integration) (Strata Cloud Manager)
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Integrate Prisma Access with Cisco Catalyst SD-WAN (Manual Integration) (Strata Cloud Manager)
Integrate Prisma Access with Cisco Catalyst SD-WAN (Manual Integration).
- Connect a remote network site to Prisma Access.
- Choose a Prisma Access Location that is close to the remote network location that you want to onboard.
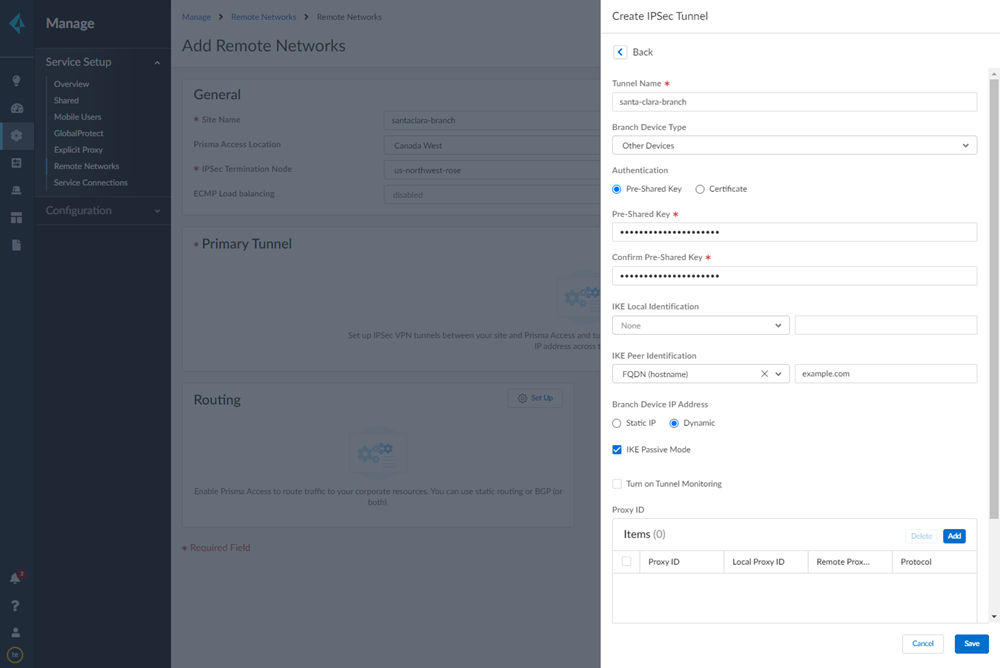
- When creating the IPSec tunnel, use a Branch Device Type of Other Devices.
![]() Select IPSec Advanced Options and Create New to create a new IPSec crypto profile for the remote network tunnel using the recommended settings.
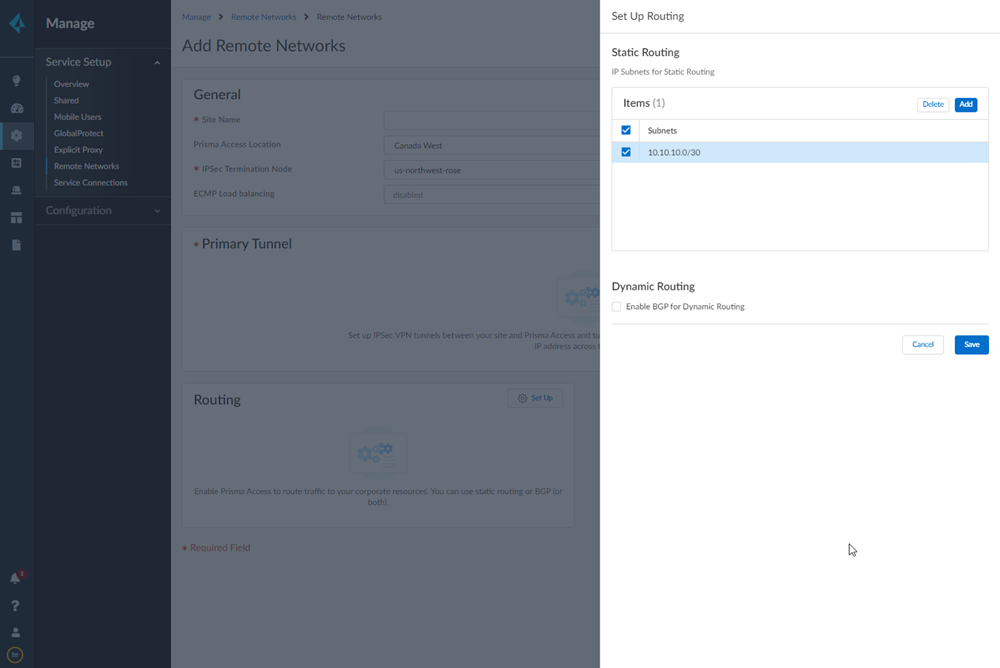
Select IPSec Advanced Options and Create New to create a new IPSec crypto profile for the remote network tunnel using the recommended settings.![]() Select IKE Advanced Options and Create New to create a new IKE cryptographic profile for the remote network tunnel.Be sure to use crypto values that are supported with Viptela and make a note of the values you use.Set up routing for the remote network.Set Up Routing and Add the IP subnets for Static Routing.Choose Static Routing and Add a subnet. A /30 subnet is sufficient for a Viptela-Prisma Access SD-WAN integration, because you need only two IP addresses for this configuration:
Select IKE Advanced Options and Create New to create a new IKE cryptographic profile for the remote network tunnel.Be sure to use crypto values that are supported with Viptela and make a note of the values you use.Set up routing for the remote network.Set Up Routing and Add the IP subnets for Static Routing.Choose Static Routing and Add a subnet. A /30 subnet is sufficient for a Viptela-Prisma Access SD-WAN integration, because you need only two IP addresses for this configuration:- 10.10.10.1, which you specified as the IP address for the ge0/4 interface.
- 10.10.10.2, for which you specify a default route when you configure the remote network connection in Viptela.
![]() Push your configuration changes.
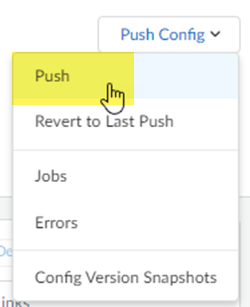
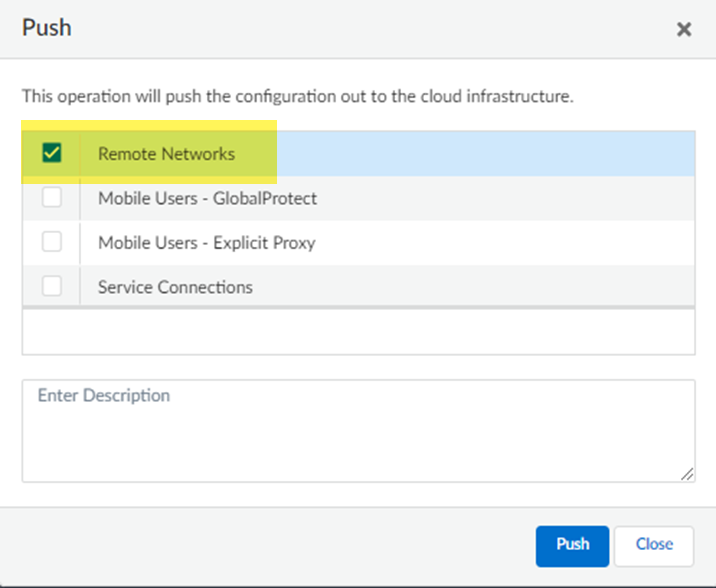
Push your configuration changes.- Return to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote Networks and select Push ConfigPush.
![]() Select Remote Networks.
Select Remote Networks.![]() Push your changes.Make a note of the Service IP of the Prisma Access side of the tunnel. To find this address in Prisma Access (Managed by Strata Cloud Manager), select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote Networks, click the Remote Networks. Look for the Service IP field corresponding to the remote network configuration you created.Complete configuration of the IPSec tunnel.
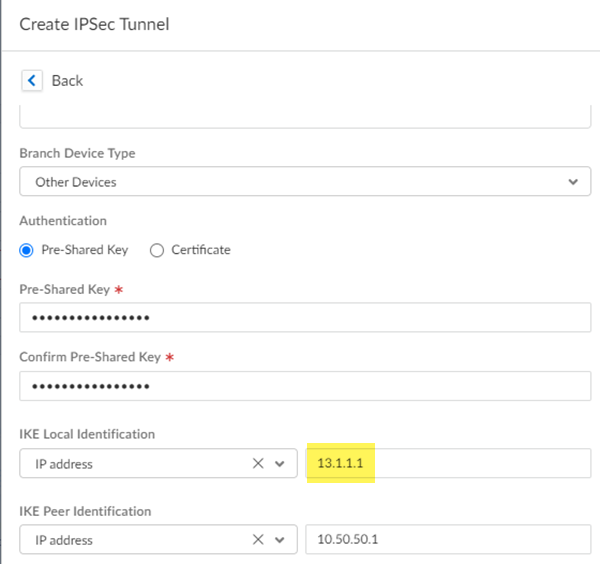
Push your changes.Make a note of the Service IP of the Prisma Access side of the tunnel. To find this address in Prisma Access (Managed by Strata Cloud Manager), select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote Networks, click the Remote Networks. Look for the Service IP field corresponding to the remote network configuration you created.Complete configuration of the IPSec tunnel.- Return to the IPSec tunnel configuration.Change Local Identification to IP address and add the Service IP you just retrieved (13.1.1.1 in this example).Be sure to make a note of the Service IP; you configure this as the peer IP address for the IPSec tunnel between the Viptela SD-WAN device and Prisma Access.
![]()
Create a Remote Network Connection in Viptela
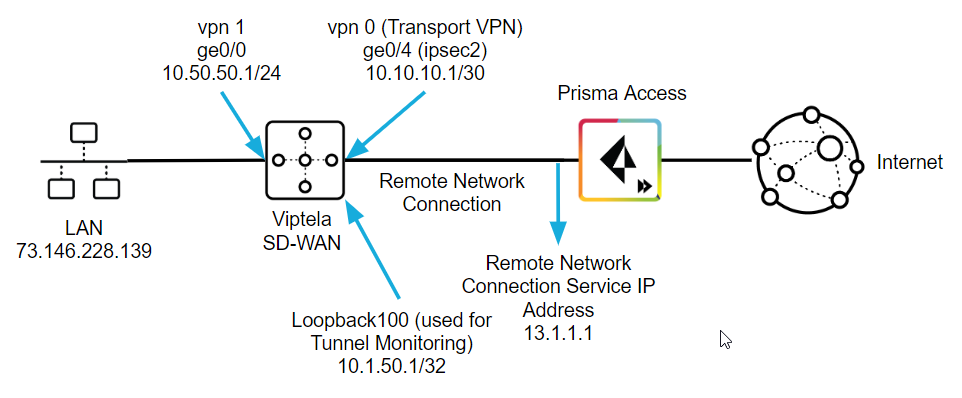
Use the following steps to configure the IPSec tunnel in Viptela. The examples in this section use command-line interface (CLI) commands.This configuration completes the remote network connection between Prisma Access and the Viptela SD-WAN. The following figure shows what you define in the Viptela side:- On the LAN side of the Viptela SD-WAN device, create a ge0/0 interface with an IP address of 10.50.50.1. This matches the IP address you specified when you configured the IKE Gateway in Prisma Access.The Viptela SD-WAN performs NAT on the source IP address for the LAN (73.146.228.139).
- On the remote network tunnel (WAN) side, create an interface named ipsec2 with a type, slot, and port of ge0/4 whose IP address is 10.10.10.1/30.This address must be within the subnet range you specified for the Branch IP Subnet when you onboarded your remote network in Prisma Access. In this example, the administrator specified a Branch IP Subnet of 10.10.10.0/30 in Prisma Access, and you use the other available IP address (10.10.10.1/30) on the Viptela side of the remote network connection.
- Specify a tunnel-destination IP address that matches the Prisma Access Service IP. This example uses 13.1.1.1.
- Specify a loopback IP address that Prisma Access can use for tunnel monitoring.In this example, the administrator configured a loopback100 interface with an IP address of 10.1.50.1/32. This value matches the Tunnel Monitor Destination IP address you specified in the IPSec Tunnel configuration that you configured in Prisma Access.
![]()
- Open a CLI session with the Viptela SD-WAN device and enter the following commands to define the control plane for the Viptela Overlay Management Protocol (OMP).The following commands enable a graceful restart for the OMP and advertise static and connected routes.
omp no shutdown graceful-restart advertise connected advertise static
Define the security types for the IPSec tunnel.The following commands enable the AH-SHA1 HMAC and ESP HMAC-SHA1 authentication types.security ipsec authentication-type sha1-hmac ah-sha1-hmac
Configure VPNs to segment the Viptela overlay network.The following commands create a VPN VPN 0 named Transport VPN and associates the ge0/4 interface with this VPN. You use this interface and VPN for the Viptela SD-WAN side of the remote network tunnel (IPSec tunnel) between Viptela and Prisma Access.vpn 0 name "Transport VPN" interface ge0/4 ip dhcp-client tunnel-interface encapsulation ipsec color biz-internet allow-service all no allow-service bgp allow-service dhcp allow-service dns allow-service icmp no allow-service sshd no allow-service netconf no allow-service ntp no allow-service ospf no allow-service stun
Enter the no shutdown command to enable the ge0/4 interface.Create another VPN named VPN 1, associate the ge0/0 interface with this VPN, then define parameters for it.The following example defines the parameters to allow the Viptela SD-WAN to route traffic from the LAN to its ge0/0 interface.vpn 1 interface ge0/0 ip address 10.50.50.1/24 no shutdown dhcp-server address-pool 10.50.50.0/24 exclude 10.50.50.1 offer-time 600 lease-time 86400 admin-state up options default-gateway 10.50.50.1 dns-servers 8.8.8.8 8.8.4.4Create an interface named ipsec2 and apply it to the ge0/4 interface. These commands define the parameters for the remote network tunnel between the Viptela SD-WAN and Prisma Access.Enter the following values:- Enter an ip address to allow the Viptela SD-WAN to route traffic to Prisma Access.This address must be within the subnet range you specified for the Branch Subnet when you onboarded your remote network in Prisma Access. A /30 address is sufficient to allow routing to Prisma Access.
- Specify the same tunnel-source-interface that you used for VPN 0 (ge0/4 in this example).
- Specify a tunnel-destination using the Service IP from Prisma Access. This example uses 13.1.1.1 as the Service IP.
- Make sure that the ike and ipsec parameters that you specify match the parameters you specified in Prisma Access.
- Enter a pre-shared-secret that matches the Pre-shared key (PSK) that you entered in Prisma Access. This example uses a PSK of secretkey.
interface ipsec2 ip address 10.10.10.1/30 tunnel-source-interface ge0/4 tunnel-destination 13.1.1.1 ike version 1 mode main rekey 14400 cipher-suite aes128-cbc-sha1 group 2 authentication-type pre-shared-key pre-shared-secret secretkey ! ! ! ipsec rekey 3600 replay-window 512 cipher-suite aes256-cbc-sha1Enter the no shutdown command on the ipsec2 interface to enable it.Create a loopback interface to be used for tunnel monitoring.interface loopback100 ip address 10.1.50.1/32 no shutdown
Create a default route for the network.This route uses the second IP address (10.10.10.2 in this example) of the /30 subnet you used when you onboarded your remote network in Prisma Access. The Viptela side of the network can route to this IP address and uses it as a next hop for routing.ip route 0.0.0.0/0 10.10.10.2
Enter a VPN and give it a name.vpn 512 name "Transport VPN"
Apply policies for the network.policy app-visibility flow-visibility
Troubleshoot the Viptela Remote Network
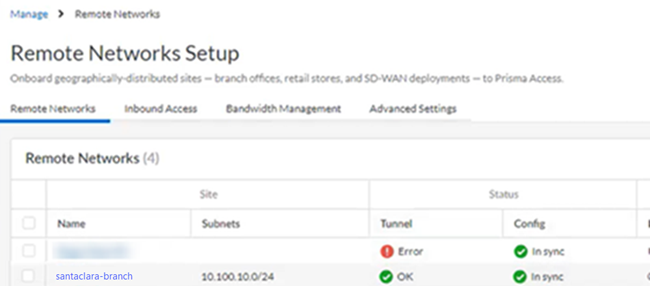
To troubleshoot problems related to SD-WAN tunnels in Viptela, refer to the Viptela documentation for configuring IPSec tunnels at the following URL: https://www.cisco.com/c/en/us/support/routers/sd-wan/tsd-products-support-series-home.html.Prisma Access provides logs and widgets that provide you with the status of remote tunnels and the status of each tunnel.- Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote Networks and check the Status of the tunnel.
![]()
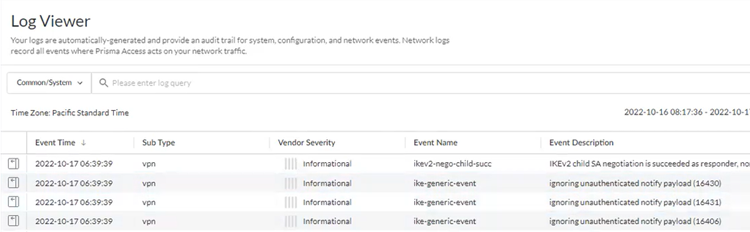
- Go to ActivityLog Viewer and check the Common/System logs for IPSec- and IKE-related messages.To view VPN-relates messages, set the filter to sub_type.value = vpn.The message ignoring unauthenticated notify payload indicates that the route has not been added in the crypto map on the other side of the IPSec tunnel after the IPSec negotiation has already occurred.
![]()
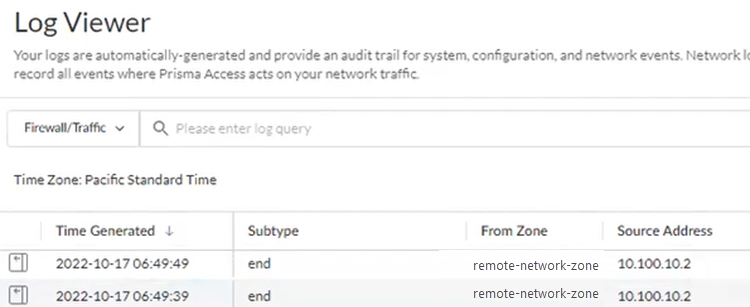
- Check the Firewall/Traffic logs and view the messages that are coming from the zone that has the same name as the remote network.In the logs, the remote network name is used as the source zone.
![]()