Remote Browser Isolation
Configure Remote Browser Isolation (Strata Cloud Manager)
Table of Contents
Configure Remote Browser Isolation (Strata Cloud Manager)
Learn how to configure Remote Browser Isolation using Strata Cloud Manager.
You can secure your end users' browsing experience by configuring Remote Browser Isolation (RBI) to isolate their browser traffic.
Configure RBI by completing the following steps:
- Before you can begin to configure RBI, ensure that you:
- Purchase a valid Prisma Access license with a Mobile Users or Remote Networks license subscription.
- Purchase and activate the Remote Browser Isolation license.
- Configure at least one Prisma Access connection method, such as GlobalProtect, Explicit Proxy, or Remote Networks, otherwise you won't be able to enable RBI.
- Enable decryption so that Prisma Access can decrypt and inspect traffic to determine what needs to be isolated according to the policies that you configured.
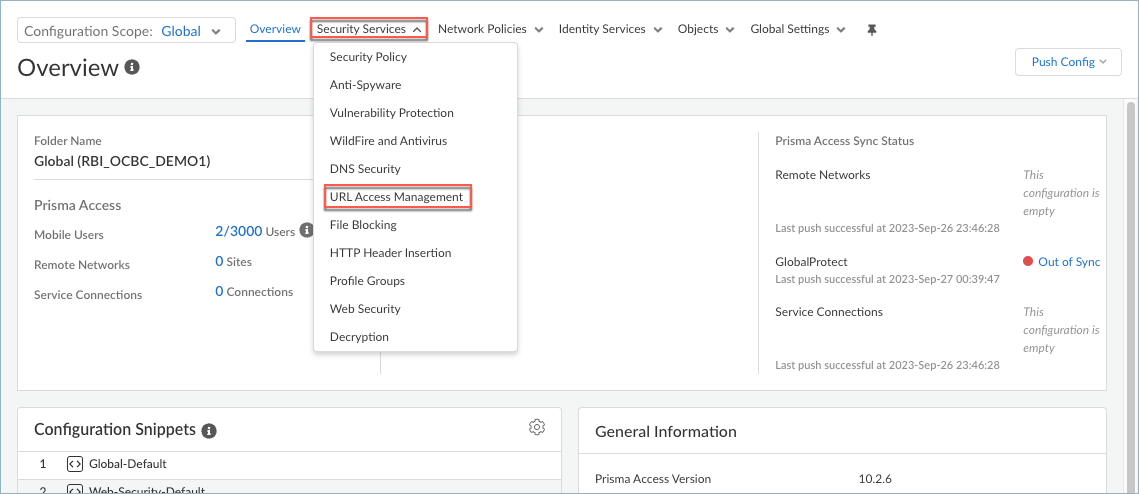
In Strata Cloud Manager, select ConfigurationNGFW and Prisma AccessConfiguration ScopeGlobalSetup and select the Remote Browser Isolation settings.![]() Alternatively, you can select ConfigurationNGFW and Prisma AccessConfiguration ScopeGlobalSecurity ServicesURL Access Management. Then, click Settings, open the Third Party Remote Browser Isolation Settings, and click Configure Remote Browser Isolation.The Configure Remote Browser Isolation button is available only if you purchased and activated the Remote Browser Isolation license.Set up the infrastructure settings for RBI that will define the browser behavior and appearance during isolated browsing sessions.
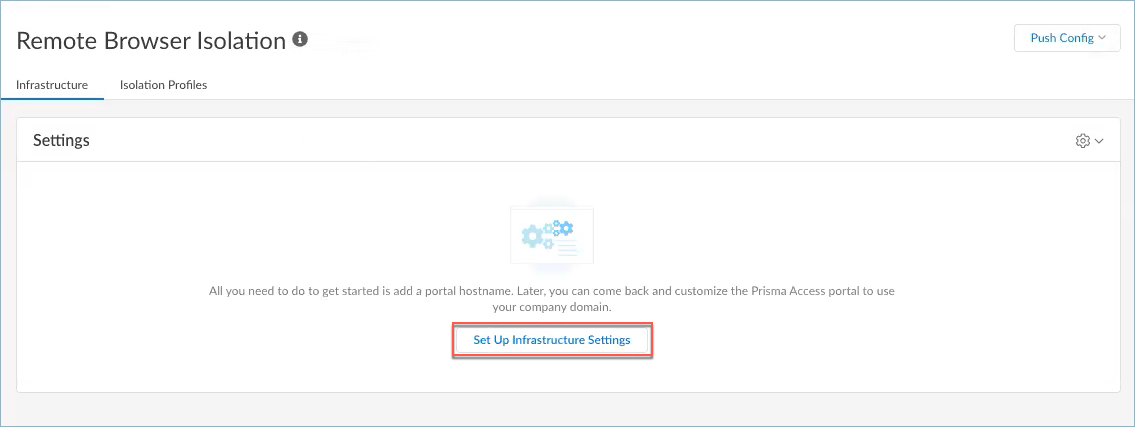
Alternatively, you can select ConfigurationNGFW and Prisma AccessConfiguration ScopeGlobalSecurity ServicesURL Access Management. Then, click Settings, open the Third Party Remote Browser Isolation Settings, and click Configure Remote Browser Isolation.The Configure Remote Browser Isolation button is available only if you purchased and activated the Remote Browser Isolation license.Set up the infrastructure settings for RBI that will define the browser behavior and appearance during isolated browsing sessions.- If you're setting up RBI for the first time, select InfrastructureSet Up Infrastructure Settings.
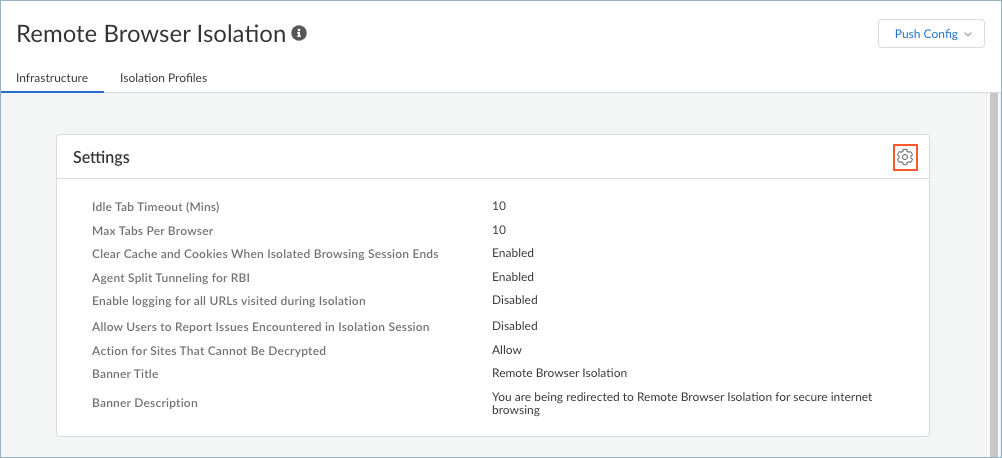
![]() Otherwise, edit the Settings.
Otherwise, edit the Settings.![]() Define the browser behavior during an isolated browsing session.
Define the browser behavior during an isolated browsing session.![]()
-
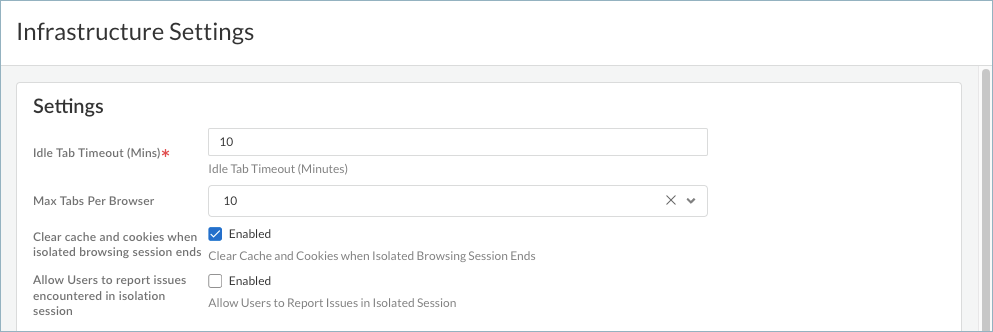
Idle Tab Timeout (Mins)—Specify the duration that elapses before a browser tab will time out due to user inactivity. The default timeout value is 10 minutes. The range is 5-20 minutes.The inactivity timer starts from the user's last action, such as mouse click, scrolling, navigation, file upload or download, and stopping video or audio. Just moving the cursor isn't considered an activity.
-
Max Tabs Per Browser—Select the maximum number of tabs that the user can open per browser. You can choose either 5, 10, or 15 maximum tabs. The default is 10.When the number of tabs exceeds the maximum, the users will be prompted to close existing tabs if they want to open more tabs for browsing.
-
Clear cache and cookies when isolated browsing session ends—Enable this setting to clear the browser's cache and cookies when the user ends the isolated browsing session (by closing the browser). Clearing the cache and cookies can potentially help resolve some browser issues by speeding page loads or removing website tracking data.
- Allow users to report issues encountered in isolation sessions—When this setting is Enabled, mobile users can report issues that they encountered during isolated browsing. The users can click the floating action button and select Report an issue.
![]()
Set up advanced settings for isolated browsing, such as split tunnel settings.![]()
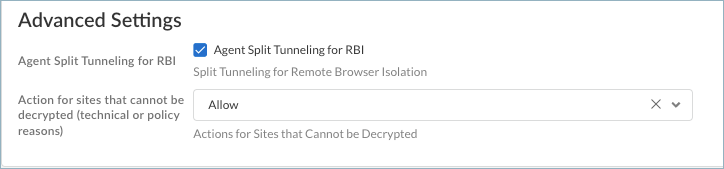
- Agent Split Tunneling for RBI—To further improve the user experience while in isolation, enable split tunneling, which enables the remote browser to connect directly to endpoints for quicker access.This setting is enabled by default and applies only to mobile user connections such as GlobalProtect and Explicit Proxy. For Remote Networks, all traffic goes through the tunnel to Prisma Access. For Explicit Proxy, you need to exclude the RBI domain in the PAC file by adding the following statements:
if (shExpMatch(host, "*.rbi.io")) return "DIRECT";
The RBI split tunnel configuration isn’t viewable in the split tunnel configuration area of GlobalProtect. RBI uses split tunneling based on the domain and application, and the configuration is FQDN-based. For split tunneling to work, you must enable Split DNS to enable mobile users to direct their DNS queries for applications and resources over the tunnel or outside the tunnel in addition to network traffic. - Action for sites that cannot be decrypted (technical or policy reason)—Prisma Access needs to decrypt encrypted websites so that it can inspect traffic to determine which websites to isolate according to the policies that you configured.Choose whether to Allow or Block access to websites that can't be decrypted due to technical or policy reasons. You can also select Force Isolate to isolate the traffic from these websites if Prisma Access is unable to decrypt the traffic.
Set up theme settings for the isolated browsing session. When a user enters an isolated browsing session, a notification banner appears for about five seconds in the browser to let them know that they are entering isolation. You can customize this notification to align with your organization's look and feel.The following is an example of a notification banner:![]() Here's where you set up the isolation theme:
Here's where you set up the isolation theme:![]()
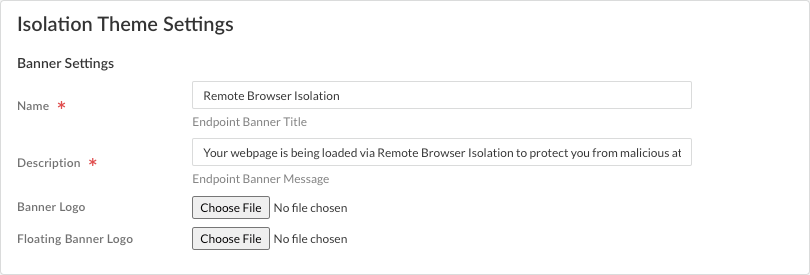
- Name—Enter the name that will appear on the notification banner when the user enters an isolated session on their browser. (Required field)
- Description—Enter the text that goes on the notification banner. (Required field)
- Banner Logo—Select Choose File to upload a graphics file that will appear as the logo for the banner. If you do not upload a file, the Palo Alto Networks logo will be used by default. You can upload only one file. The valid file formats are JPG and PNG.
- Floating Banner Logo—Select Choose File to upload a graphics file that will appear in the floating action button that users can click to invoke an action such as reporting an issue. If you do not upload a file, the Palo Alto Networks logo will be used by default. You can upload only one file. The valid file formats are JPG and PNG. The image should be 42x42 pixels in size to render well in RBI.
![]()
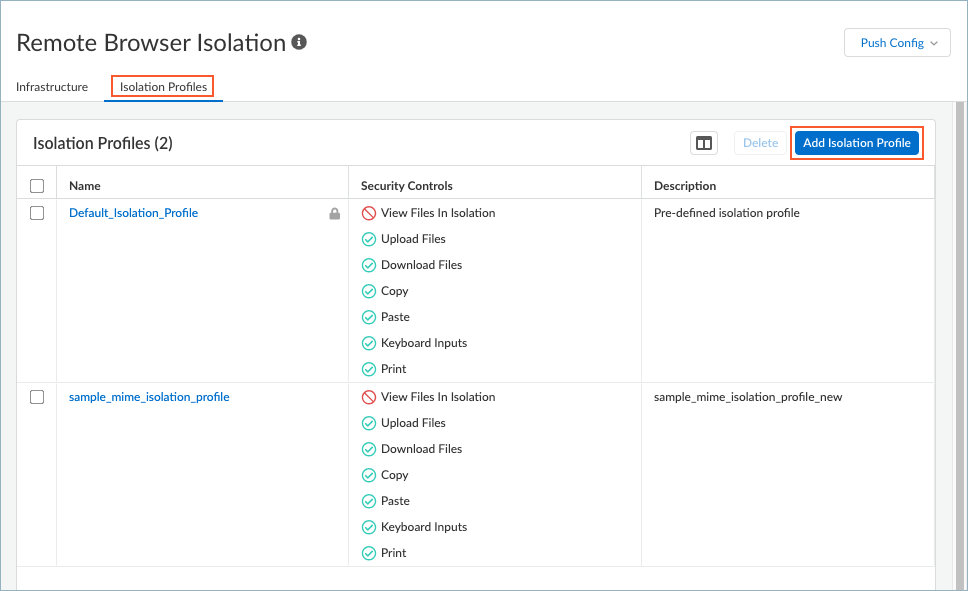
Save your infrastructure settings.Set up one or more isolation profiles that define what browser actions users can perform during an isolated session.- From the Remote Browser Isolation Setup page, select Isolation Profiles.A default isolation profile is provided for you. You can create custom isolation profiles when you Add Isolation Profile.
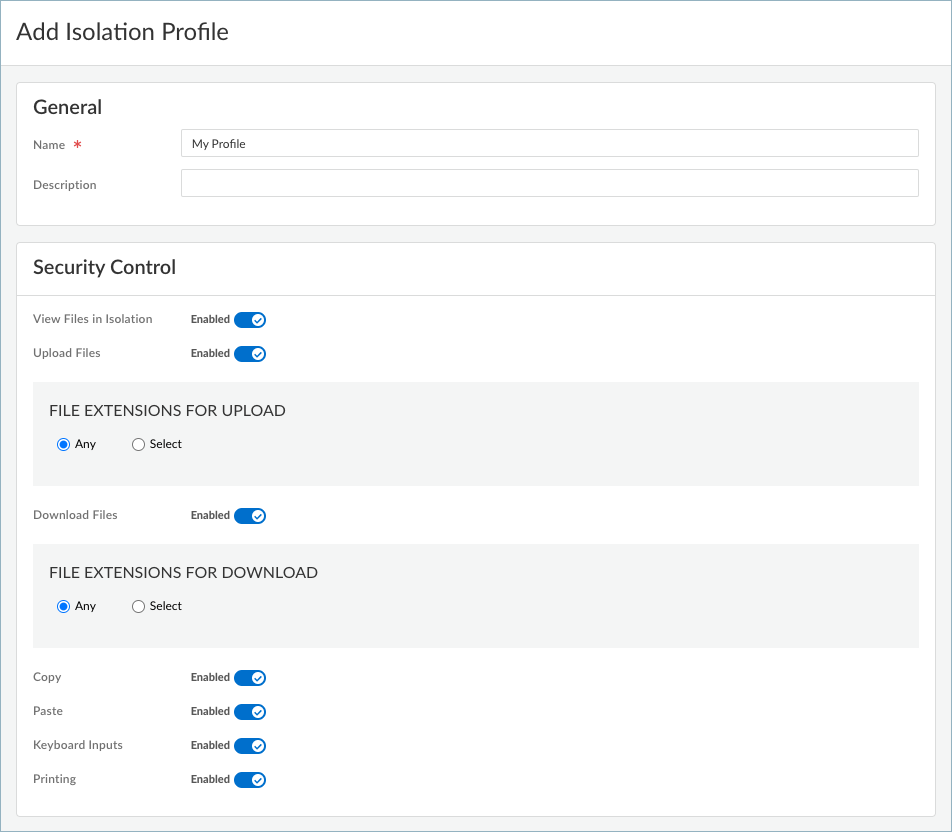
![]() Enter a Name and Description for the isolation profile.Select the security controls that you want to put in place for the browser. You can allow or prohibit a user from doing the following actions:
Enter a Name and Description for the isolation profile.Select the security controls that you want to put in place for the browser. You can allow or prohibit a user from doing the following actions:- View files in isolation
- Upload files
- Download files
- Copy content
- Paste content
- Use the keyboard for input
- Print content
By enabling an action, you will permit the user to perform that action in isolation.For file uploads and downloads, you can restrict which types of files users can transfer during isolated browsing sessions.![]() Save your isolation profile settings.Create or update a URL Access Management profile and attach the isolation profile to it.
Save your isolation profile settings.Create or update a URL Access Management profile and attach the isolation profile to it.- From Strata Cloud Manager, select ConfigurationNGFW and Prisma Access.Select Security ServicesURL Access Management.
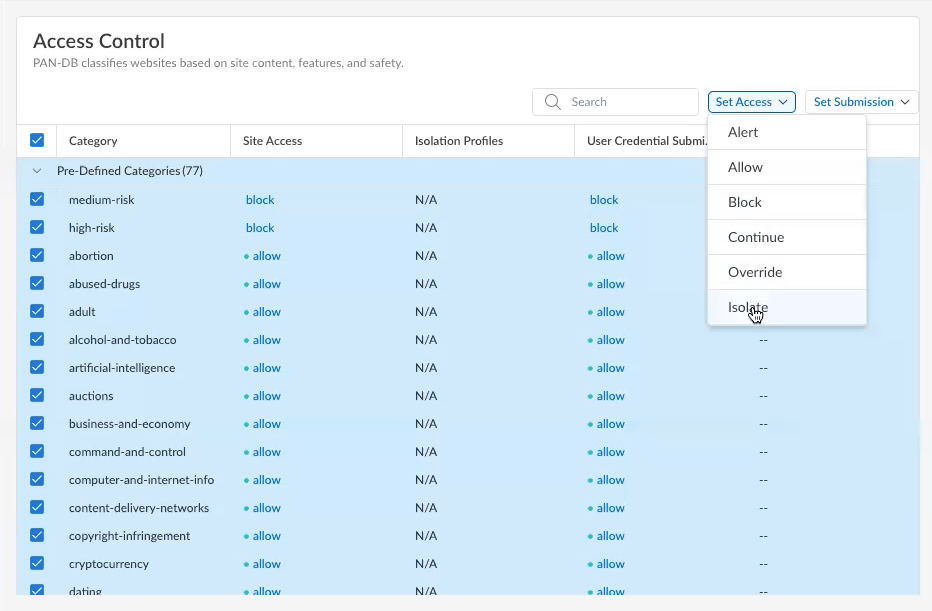
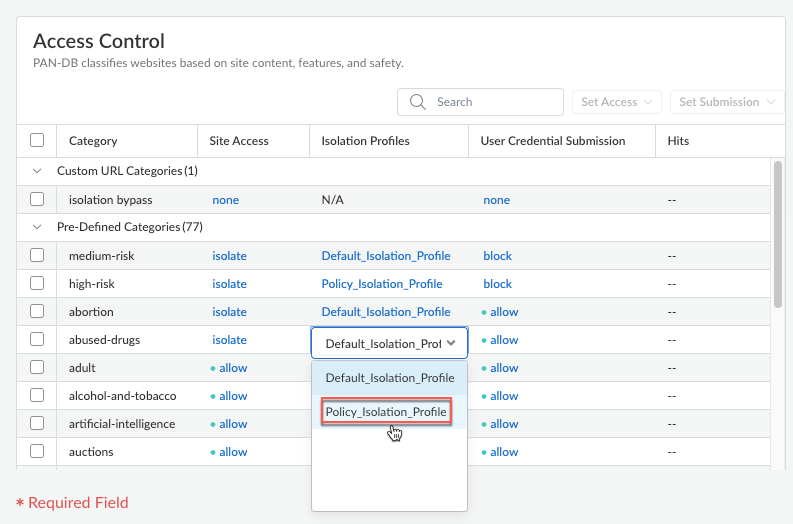
![]() Edit an existing URL Access Management profile by selecting the profile name or Add Profile to create a new one.If you are adding a profile, enter a Name and Description for the profile, select the check box next to the Category column heading, and select Set AccessIsolate.This action automatically sets the Site Access to isolate, and associates the Default_Isolation_Profile to all the URL categories.
Edit an existing URL Access Management profile by selecting the profile name or Add Profile to create a new one.If you are adding a profile, enter a Name and Description for the profile, select the check box next to the Category column heading, and select Set AccessIsolate.This action automatically sets the Site Access to isolate, and associates the Default_Isolation_Profile to all the URL categories.![]() If necessary, change the Access Control for specific website categories.
If necessary, change the Access Control for specific website categories.- Search for a URL category or scroll to a category.
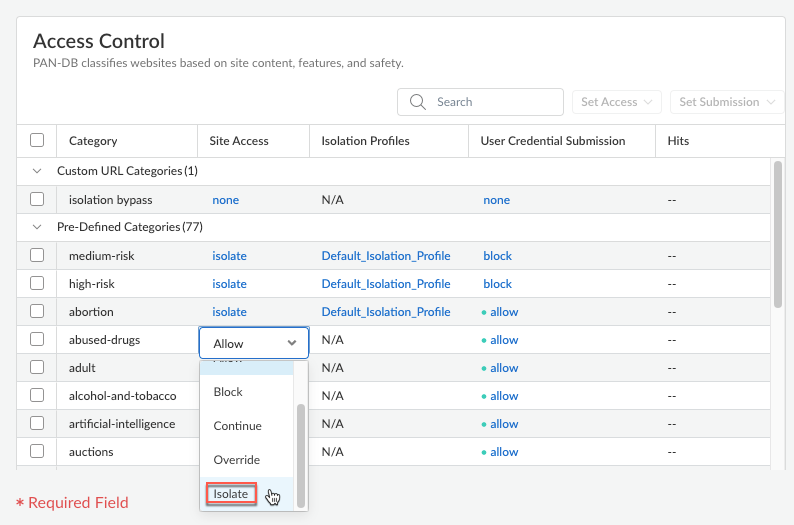
- If you are editing an existing URL management profile, click the Site Access drop-down for a URL category and select Isolate to permit isolated browsing of websites in that category.
![]() For websites that belong in multiple URL categories, the effective URL category action is the highest priority match action across all these categories. The priority in descending order is as follows: BlockIsolateOverrideContinueAlertAllow. Therefore, for RBI to work, you need to set the action to Isolate for all categories that match a website.For example, cnn.com belongs in both the news and low-risk categories. If the news category is set to Block and the low-risk category is set to Isolate, the cnn.com website will be blocked because the Block action overrides the Isolate action. For isolated browsing to work for cnn.com, you must set both categories to the Isolate action.
For websites that belong in multiple URL categories, the effective URL category action is the highest priority match action across all these categories. The priority in descending order is as follows: BlockIsolateOverrideContinueAlertAllow. Therefore, for RBI to work, you need to set the action to Isolate for all categories that match a website.For example, cnn.com belongs in both the news and low-risk categories. If the news category is set to Block and the low-risk category is set to Isolate, the cnn.com website will be blocked because the Block action overrides the Isolate action. For isolated browsing to work for cnn.com, you must set both categories to the Isolate action. - After you select the site access, the Default_Isolation_Profile is automatically attached to the URL category. If you created additional isolation profiles that control the browser actions in isolation mode, you can attach a different profile by clicking the Isolation Profile drop-down and selecting an available profile.
![]()
Save your settings.Create a security policy rule that uses the URL Access Management profile that you set up for isolation.You need to complete this step because for the URL Access Management profile to be active, it must be included in a profile group that is referenced by a security policy rule.- From Strata Cloud Manager, select ConfigurationNGFW and Prisma Access.If you have not done so already, create a profile group.
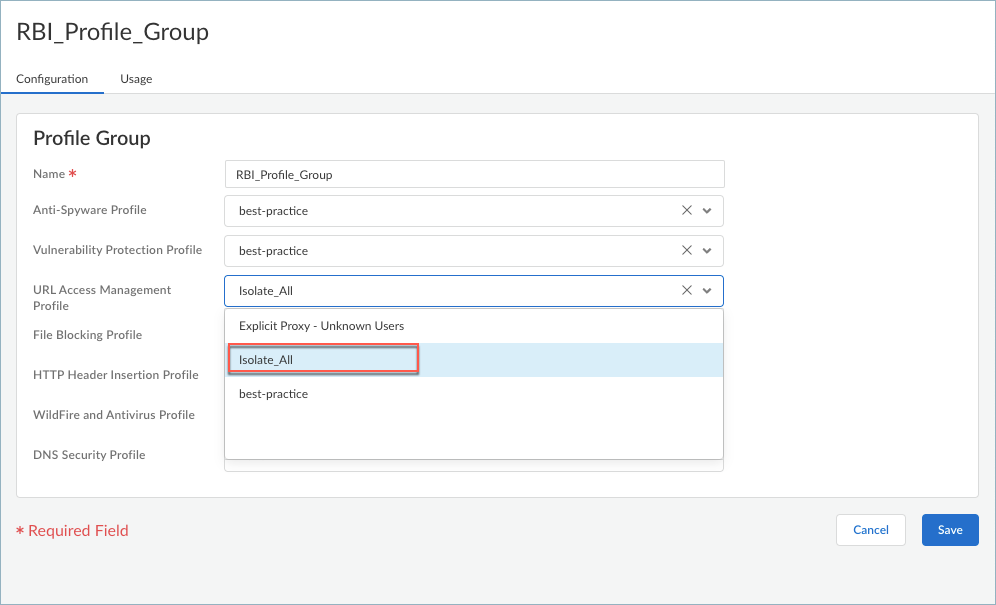
- Select Security ServicesProfile Groups and Add Profile Group.
- Enter the Name of the profile group.
- Select the security profiles that you want to use, and ensure that you select the URL Access Management Profile that you want to use for isolation.
![]()
- Save your changes.
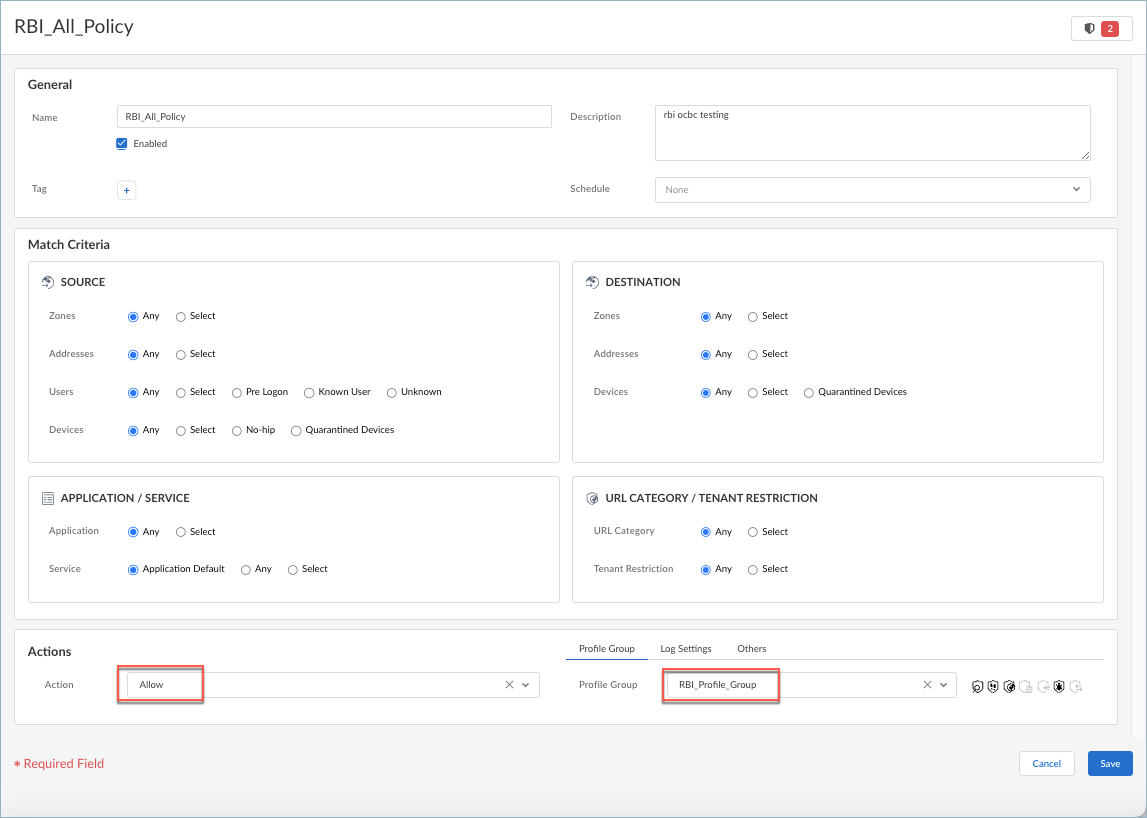
Associate the profile group to a security rule. If you have not done so already, create a security rule.- Select Security ServicesSecurity PolicyAdd RulePre RuleSecurity Rule.Select Pre Rule to evaluate the security rule first, and Post Rule to evaluate the rule lat, at the end of the rule processing order.
- Enter the Name for the security rule.
- Select a source zone for the Match Criteria.
- Select a destination zone and address for the Match Criteria.
- Select an Application.
- Select the Allow action and select the Profile Group that you created for isolation.You can use the groups that you created or populated in Cloud Identity Engine for user and user group mapping for RBI.
![]()
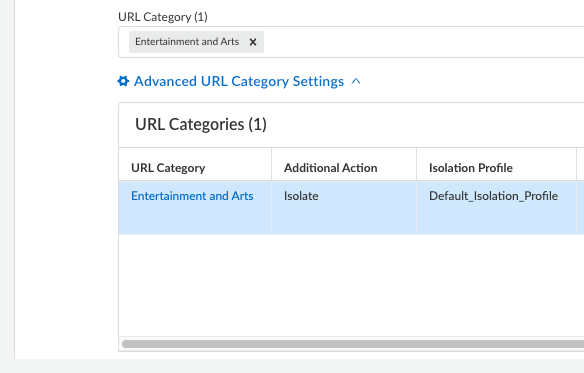
You can also create a web security rule where you can control the access for websites in URL categories based on the isolation profile that you set up previously.- From Strata Cloud Manager, select ConfigurationNGFW and Prisma Access.Select Security ServicesSecurity PolicySecurity Policy RulesAdd RulePre RuleInternet Access Rule.Select Pre Rule to evaluate the security rule first, and Post Rule to evaluate the rule lat, at the end of the rule processing order.Enter the Name for the custom web access policy and select the Allow action.Specify the URL Category that you want to explicitly allow for isolated browsing. For example, to allow websites in the Entertainment and Arts category for isolated browsing, search for entertainment and arts and select entertainment-and-arts.Expand Advanced URL Category Settings and select the URL category that you added, such as Entertainment and Arts.In the panel that slides open on the right, select Additional ActionIsolate, and select the Isolation Profile that you created or use the default isolation profile.Update the URL category settings and Save your internet access rule.
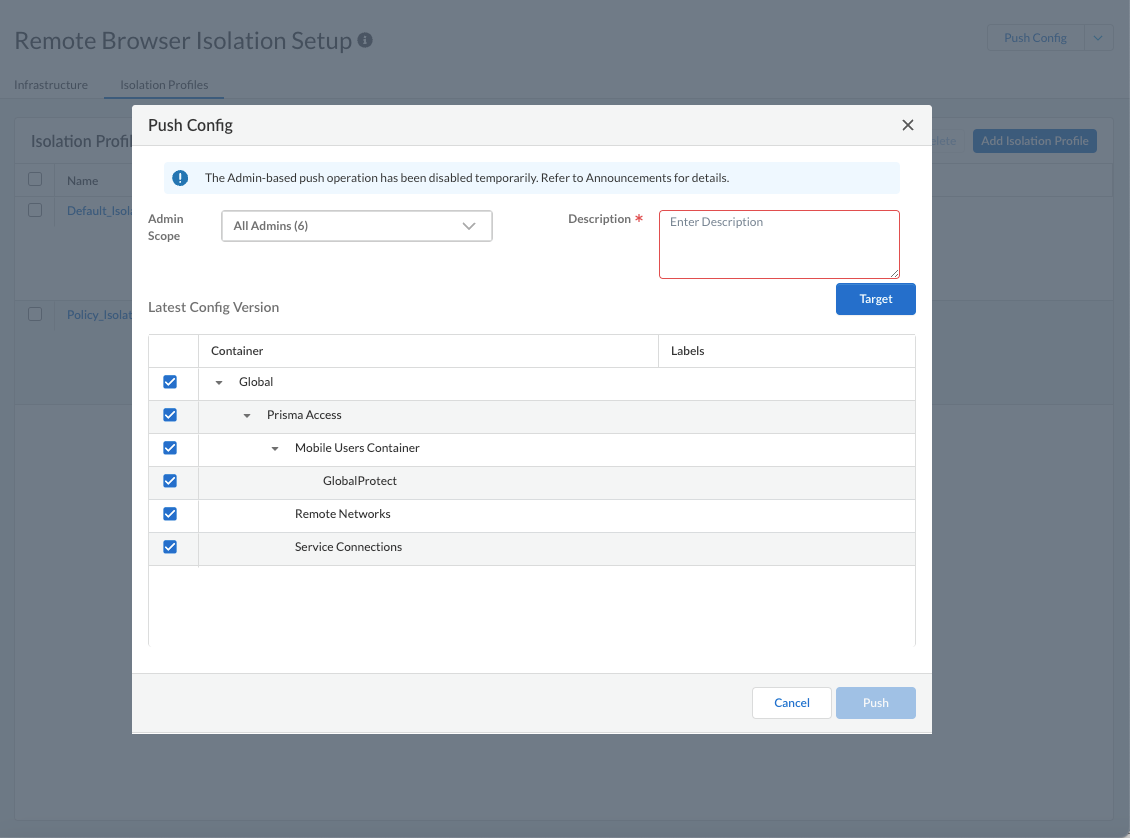
![]() Push the configuration to your mobile users or remote networks by selecting Push ConfigPush, selecting the Target for the configuration, and Push.
Push the configuration to your mobile users or remote networks by selecting Push ConfigPush, selecting the Target for the configuration, and Push.![]()