Remote Browser Isolation
Remote Browser Isolation
Table of Contents
Remote Browser Isolation
Remote Browser Isolation (RBI) can help secure your endpoints and networks from ever
evolving browser and web-based zero day attacks.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Browser and web-based attacks are continuously evolving, resulting in security challenges
for many enterprises. Web browsers, being a major entry point for malware to penetrate
networks, pose a significant security risk to enterprises, prompting the increasing need
to protect networks and devices from zero day attacks. Highly regulated industries, such
as government and financial institutions, also require browser traffic isolation as a
mandatory compliance requirement.
While most enterprises want to block 100% of attacks by using network security and
endpoint security methods, such a goal might not be realistic. Most attacks start with
the compromise of an endpoint that connects to malicious or compromised sites or by
opening malicious content from those sites. An attacker only needs one miss to take over
an endpoint and compromise the network. When this happens, the consequences of that
compromise and the impact to your organization can be damaging.
Remote Browser Isolation (RBI) creates a no-code execution isolation environment for a user's
local browser, so that no website code and files are executed on their local browser.
Unlike other isolation solutions, RBI uses next-generation
isolation technologies to deliver near-native experiences for users accessing websites
without compromising on security.
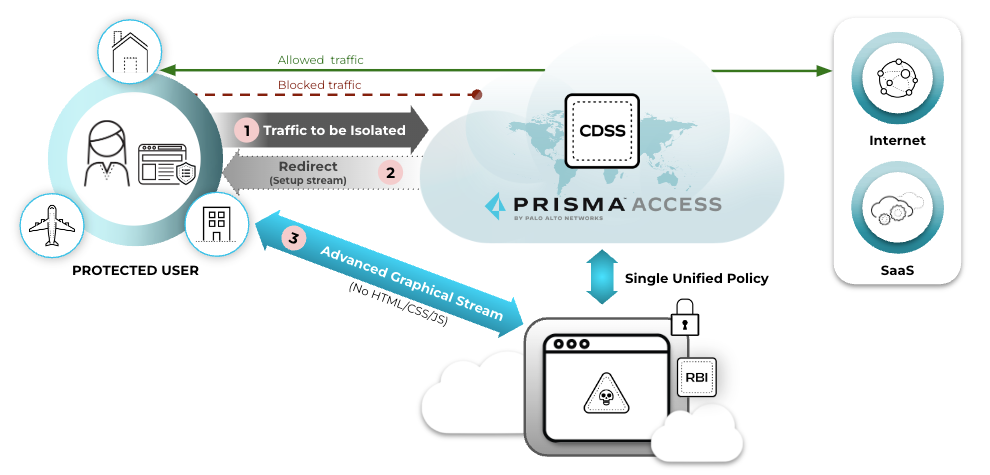
RBI is a service that isolates and transfers all browsing activity
away from the user's managed devices and corporate networks to an outside entity such as
Prisma Access. The outside entity then secures and isolates potentially
malicious code and content within their platform, and separates any threats from direct
connections to end-user devices and networks.
Natively integrated with Prisma Access, RBI allows you to apply
isolation profiles easily to existing security policies. Isolation profiles can restrict
many user controls such as copy and paste actions, keyboard inputs, and sharing options
like uploading, downloading, and printing files to keep sensitive data and information
secure. All traffic in isolation undergoes analysis and threat prevention provided by
Cloud-Delivered Security Services (CDSS) such as Advanced Threat Prevention, Advanced
WildFire, Advanced URL Filtering, DNS Security, and SaaS Security.
You and your users can benefit from the following features:
- Near-native browsing experience—When users browse websites in isolation, the websites load in a protected air-gapped environment that looks and feels as if they were accessed directly from a local web browser, including all web technologies that a standard web browser supports. This enables you and your users to access internet websites in isolation without sacrificing web browser functionality or performance.RBI supports most web technologies, including JavaScript, modern frameworks, HTML5, HTTP protocol, and rich media support such as video, audio, and animated GIFs. URLs shown on the remote browser will look the same as the original native URLs, with no prefixes added to the addresses.
- Security policy driven—You can specify URL categories whose website content you want to redirect to RBI using isolation profiles, which you attach to Prisma Access security policy rules that protect your users. You can also create isolation profiles that control what browser actions are allowed during isolated browsing. RBI is integrated with Prisma Access so that you can apply additional internet security services to traffic from isolated browsing sessions.In combination with Prisma Access, RBI provides the following security benefits:
- Isolated sessions, cookies, and user data
- Safe previews of documents such as PDFs
- Credential phishing protection (provided by the disabling the keyboard in an isolation profile)
- Cloud-delivered security services such as:
- XSS prevention
- Advanced URL Filtering
- Advanced Threat Protection
- Advanced WildFire
- SaaS Inline Security (provided by SaaS Security)
- DNS Security
As a result, RBI can help prevent your users from compromising any enterprise or personal information on managed devices while accessing the internet. This also includes data loss prevention (DLP) of sensitive or critical data while accessing web applications or the internet. - Simple onboarding and configuration—Managed users who have onboarded to Prisma Access using GlobalProtect, Explicit Proxy, or Remote Networks connections can browse in isolation. No extra authentication step is required for RBI.Because RBI conforms to the existing security policy framework of Prisma Access, you can easily onboard and configure RBI for your end users. This reduces the overhead for you, because you can easily set up isolation profiles and attach them to existing security rules.
- Monitoring and troubleshooting—By using either Strata Cloud Manager or the Panorama Managed Prisma Access management interface, you can monitor the health of the RBI deployment, the security outcomes achieved, and any user experience issues without having to use multiple management tools. You can monitor the health of the RBI deployment (such as RBI usage, health, and license information), and troubleshoot and resolve common end-user issues.
