SD-WAN
PAN-OS & Panorama
Table of Contents
Expand All
|
Collapse All
SD-WAN Docs
-
-
-
-
- 3.4
- 3.3
- 3.2
- 3.1
- 3.0
- 2.2
- 2.1
- 2.0
- 1.0
-
PAN-OS & Panorama
In PAN-OS, create a Traffic Distribution profile to distribute sessions
and to fail over to a better path when path quality deteriorates.
- Log in to the Panorama Web Interface.Ensure you already configured the Link Tags in an SD-WAN interface profile and committed and pushed them. The Link Tags must be pushed to your hubs and branches in order for Panorama™ to successfully associate the Link Tags you specify in this Traffic Distribution profile to an SD-WAN interface profile.Select a Device Group.Create a Traffic Distribution profile.
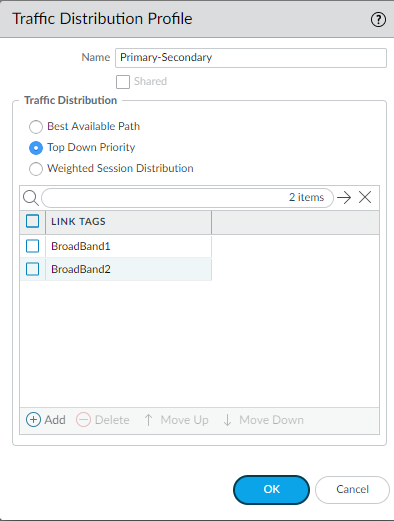
- Select ObjectsSD-WAN Link ManagementTraffic Distribution Profile.Add a Traffic Distribution profile by Name using a maximum of 31 alphanumeric characters.
![]() Select Shared only if you want to use this traffic distribution profile across all Device Groups (both hubs and branches).Select one traffic distribution method and add a maximum of four Link Tags that use this method for this profile.
Select Shared only if you want to use this traffic distribution profile across all Device Groups (both hubs and branches).Select one traffic distribution method and add a maximum of four Link Tags that use this method for this profile.- Best Available
Path—Add one or more
Link Tags. During the initial packet
exchanges, before App-ID has classified the application in the
packet, the firewall uses the path in the tag that has the best
health metrics (based on the order of tags). After the firewall
identifies the application, it compares the health (path
quality) of the path it was using to the health of the first
path (interface) in the first Link Tag. If the original path’s
health is better, it remains the selected path; otherwise, the
firewall replaces the original path. The firewall repeats this
process until it has evaluated all the paths in the Link Tag.
The final path is the path the firewall selects when a packet
arrives that meets the match criteria.When a link becomes unqualified and must fail over to the next best path, the firewall can migrate a maximum of 1,000 sessions per minute from the unqualified link to the next best path. For example, suppose tunnel.901 has 3,000 sessions; 2,000 of those sessions match SD-WAN policy rule A and 1,000 sessions match SD-WAN policy rule B (both rules have a traffic distribution policy configured with Best Path Available). If tunnel.901 becomes unqualified, it takes three minutes to migrate the 3,000 sessions from the unqualified link to the next best path.
- Top Down
Priority—Add one or more
Link Tags. The firewall distributes
new sessions (that meet the match criteria) to links using the
top-to-bottom order of the Link Tags you
added. The firewall examines the first tag configured for this
profile, and examines the paths that use that tag, selecting the
first path it finds that is qualified (that is at or below the
Path Quality thresholds for this rule). If no qualified path is
found from that Link Tag, firewall examines the paths that use
the next Link Tag. If the firewall finds no path after examining
all paths in all of the Link Tags, the firewall uses the
Best Available Path method. The first
path selected is the preferred path until one of the Path
Quality thresholds for that path is exceeded, at which point the
firewall again starts at the top of the Link Tag list to find
the new preferred path.If you have only one link at the hub, that link supports all of the virtual interfaces and DIA traffic. If you want to use the link types in a specific order, you must apply a Traffic Distribution profile to the hub that specifies Top Down Priority, and then order the Link Tags to specify the preferred order. If you apply a Traffic Distribution profile that instead specifies Best Available Path, the firewall will use the link, regardless of cost, to choose the best performing path to the branch. In summary, Link Tags in a Traffic Distribution profile, the Link Tag applied to a hub virtual interface, and a VPN Failover Metric in an SD-WAN Interface Profile work only when the Traffic Distribution profile specifies Top Down Priority.
- Weighted Session Distribution—Add one or more Link Tags and then enter the Weight percentage for each Link Tag so that the weights total 100%. The firewall performs session load distribution between Link Tags until their percentage maximums are reached. If there is more than one path in the Link Tag, the firewall distributes equally using round-robin until the path health metrics are reached, and then distributes sessions to the other member(s) that are not at the limit.
If multiple physical interfaces have the same tag, the firewall distributes matching sessions evenly among them. If all paths fail a health (path quality) threshold, the firewall selects the path that has the best health statistics. If no SD-WAN links are available (perhaps due to a blackout), the firewall uses static or dynamic routing to route the matching packets.If a packet is routed to a virtual SD-WAN interface, but the firewall cannot find a preferred path for the session based on the SD-WAN policy’s Traffic Distribution profile, the firewall implicitly uses the Best Available Path method to find the preferred path. The firewall distributes any application sessions that don’t match an SD-WAN policy rule based on the firewall’s implicit, final rule, which distributes the sessions in round-robin order among all available links, regardless of the Traffic Distribution profile.If you prefer to control how the firewall distributes unmatched sessions, create a final catch-all rule to distribute unmatched sessions to specific links in the order you specify.(Optional) After adding Link Tags, use the Move Up or Move Down arrows to change the order of tags in the list, so they reflect the order in which you want the firewall to use links for this profile and for the selected applications in the SD-WAN policy rule.Click OK.Commit and Commit and Push your configuration changes.Commit your changes.