Enterprise DLP
DLP App
Table of Contents
DLP App
Create an advanced Enterprise Data Loss Prevention (E-DLP) data profile containing any combination
of custom and file property data patterns, and advanced detection methods on the DLP app on
the Hub.
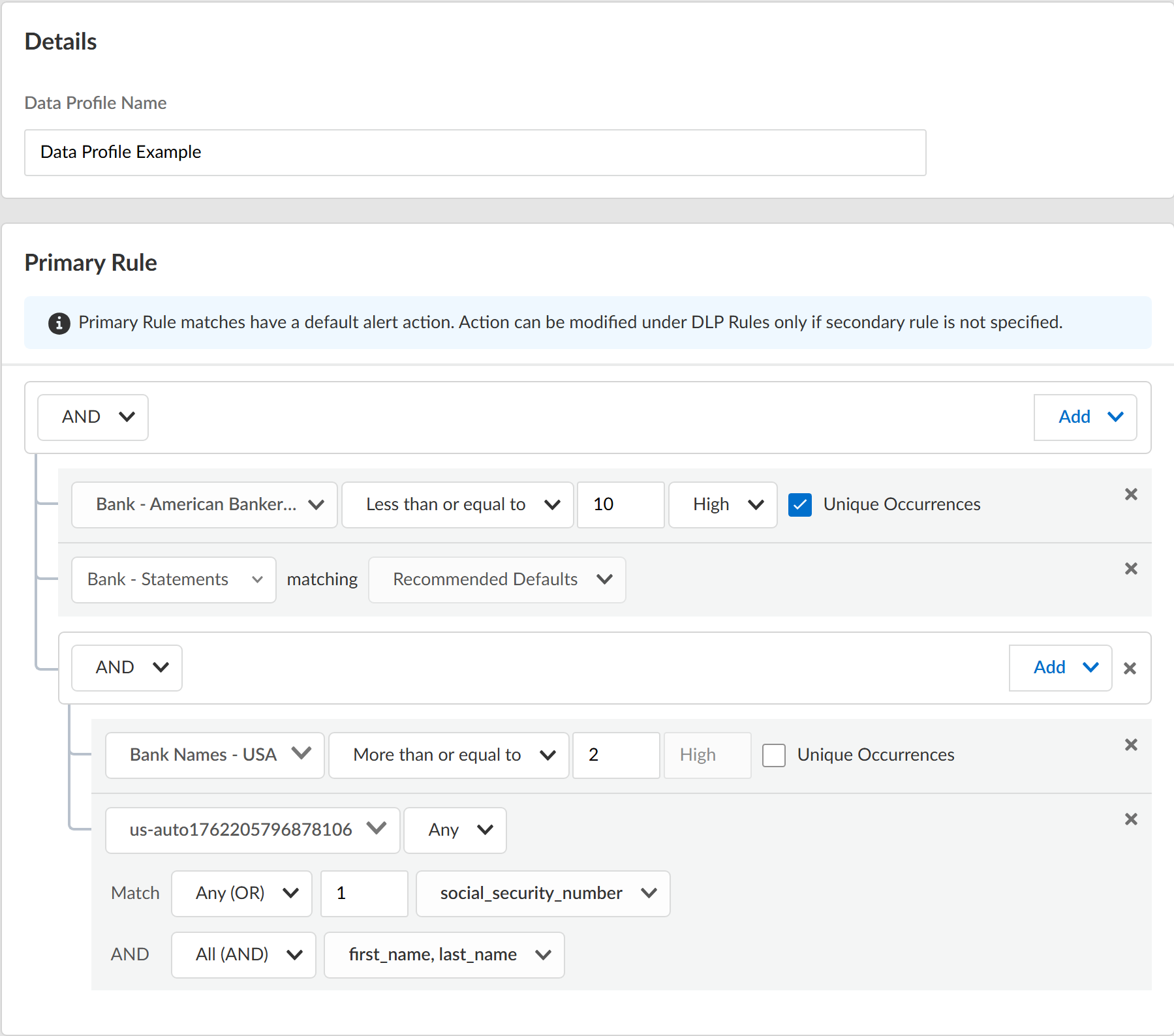
- Log in to the DLP app on the hub.If you don’t already have access to the DLP app on the hub, see the hub Getting Started Guide. Only Superusers can access the hub.Select Data ProfilesAdd Data ProfileAdvanced Data Profile.You can also create a new data profile by copying an existing data profile. This allows you to quickly modify an existing data profile with additional match criteria while preserving the original data profile from which the new data profile was copied.Data profiles created by copying an existing data profile are appended with Copy - <name_of_original_data_profile>. This name can be edited as needed.Adding an EDM data set to a copied data profile is supported only if the original data profile had an EDM data set to begin with. Adding an EDM data set to a data profile that doesn’t already have an EDM data set isn’t supported.Configure the Primary Rule for the data profile.Data pattern match criteria for traffic that you want to allow must be added to the Primary Rule. Data pattern match criteria for traffic that you want to block can be added to either Primary Rule or Secondary Rule.
- Enter a descriptive Data Profile Name.Select the data pattern operator (AND or OR).Add Data Pattern.Define the data profile match criteria
- Data PatternsSelect AddData Pattern and define the data pattern match criteria.
- Data Pattern—Select a custom or predefined data pattern.
- Occurrence Condition—Specify the occurrences condition required to trigger a Security policy rule action.
- Any—Security policy rule action triggered if Enterprise DLP detects at least one instance of matched traffic.
- Less than or equal to—Security policy rule action triggered if Enterprise DLP detects instances of matched traffic, with the maximum being the specified Count.
- More than or equal to—Security policy rule action triggered if Enterprise DLP detects instances of matched traffic, with a minimum being the specified Count.
- Between (inclusive)—Security policy rule action triggered if Enterprise DLP detects any number of instances of matched traffic between the specific Count range.
- Count—Specify the number of instances of matched traffic required to trigger a Security policy rule action. Range is 1 - 500.For example, to match a pattern that appears three or more times in a file, select More than or equal to as the Occurrence Condition and specify 3 as the Threshold.
- Confidence—Specify the confidence level required for a Security policy rule action to be taken (High or Low).
- Unique Occurrences—Check (enable) to detect only unique instances of traffic matches. Only unique occurrences of traffic matches are counted toward the specified Count.This setting is disabled by default. Keep Unique Occurrences disabled if you want all instances of traffic matches to count toward the specified Count.
- Data DictionarySelect AddDictionary and define the data dictionary match criteria.
- Dictionary—Select a custom or predefined data pattern.
- Occurrence Condition—Specify the occurrences condition required to trigger a Security policy rule action.
- Any—Security policy rule action triggered if Enterprise DLP detects at least one instance of matched traffic.
- Less than or equal to—Security policy rule action triggered if Enterprise DLP detects instances of matched traffic, with the maximum being the specified Count.
- More than or equal to—Security policy rule action triggered if Enterprise DLP detects instances of matched traffic, with a minimum being the specified Count.
- Between (inclusive)—Security policy rule action triggered if Enterprise DLP detects any number of instances of matched traffic between the specific Count range.
- Count—Specify the number of instances of matched traffic required to trigger a Security policy rule action. Range is 1 - 500.For example, to match a pattern that appears three or more times in a file, select More than or equal to as the Occurrence Condition and specify 3 as the Threshold.
- Confidence—Specify the confidence level required for a Security policy rule action to be taken (High or Low).
- Unique Occurrences—Check (enable) to detect only unique instances of traffic matches. Only unique occurrences of traffic matches are counted toward the specified Count.This setting is disabled by default. Keep Unique Occurrences disabled if you want all instances of traffic matches to count toward the specified Count.
- Custom Document TypesSelect AddDocument Types and define the custom document type match criteria.
- Overlapping Score Condition—Specify the custom document overlapping score required to trigger a Security policy rule action.
- Greater Than or Equal To—Security policy rule triggered if Enterprise DLP detects an instance of matched traffic with the specified minimum overlapping score.
- Between (Inclusive)—Security policy rule action triggered if Enterprise DLP detects an instance of matched traffic with an overlapping score between the specified min and max overlapping scores.
- EDMSelect AddEDM Dataset and define the EDM match criteria.
- EDM Dataset—Select an EDM data set uploaded to the DLP cloud service.
- Occurrence Condition—Specify the occurrences condition required to trigger a Security policy rule action.
- Count—Specify the number of instances of matched traffic required to trigger a Security policy rule action. Range is 1 - 500.
- Configure EDM data set Primary Fields values to specify whether a Security policy rule action is taken if Any (OR) or All (AND) primary fields are matched and if Any (OR) or All (AND) secondary fields are matched.
- (Any(OR) only) Enter the Count to specify the number of instances of matched traffic required to trigger a Security policy rule action. Range is 1 - 500.When you select Any (OR), the maximum Count setting is one less than the total number of fields included in the Primary Field or Secondary Field.
- Select the Primary Fields values.The list of available values is populated from the selected EDM data set. You must select at least one primary field value.You’re required to add at least one column where the column values occurs up to 12 times in the selected EDM data set for the Primary Field. For example, if the EDM data set contains columns for first name, last name, social security number, and credit card number, add social security number and credit card in the primary field.
- GroupSelect AddGroup to nest and group additional match criteria so you can more accurately define your compliance rules.When you click add a new Group, the new match criteria group is nested under the most recently added data pattern or EDM data set. You can’t nest a new match criteria group between existing data patterns or EDM data sets. If multiple data patterns or EDM data sets are added, you must remove the data patterns or EDM data sets that follow the data pattern or EDM data set for which you want to add the nested match criteria. For example, you added EDM_Dataset1, Data_Pattern2, and EDM_Dataset3 to the Primary Rule. If you wanted to added nested match criteria to Data_Pattern2, you must first remove EDM_Dataset3 from the Primary Rule.You can select the same data pattern or EDM data set or a different data pattern EDM data set to more accurately define your compliance rules. Nesting match criteria is supported only when the data profile includes an EDM data set. Enterprise DLP supports up to three level of additional nesting groups for each data pattern or EDM data set. You can nest additional data patterns or EDM data sets under a data pattern or EDM data set added to the Primary or Secondary Rule.Nested match criteria support the AND, OR, and NOT operators. Refer to the descriptions above to configure the nested match criteria.
(Optional) Configure a Secondary Rule.Data pattern match criteria added to the Secondary Rule block all traffic that meets the match criteria for the data patterns by default and can’t be modified. If you want to allow traffic that matches a data pattern match criteria, add it to the Primary Rule.Review the Data Profile Preview to verify the data profile match criteria.Save the data profile.![]() Verify that the data profile you created.
Verify that the data profile you created.- DLP App on the hub—Log in to the DLP app on the hub as a Superuser and select Data Profiles to view the data profile you created.
- Strata Cloud Manager—Log in to Strata Cloud Manager and select ManageConfigurationSecurity ServicesData Loss Prevention and search for the data profile you created.
- Panorama and Prisma Access (Managed by Panorama)See Update a Data Profile for more information on which data profile settings are editable on Panorama for a data profile created on Strata Cloud Manager.
- Log in to the Panorama web interface.Select ObjectsDLPData Filtering Profiles and navigate to the data profile you created.(Optional) Edit the data profile Action to block traffic.The Action for a data profile created on Strata Cloud Manager is configured to Alert by default.If the data profile has both Primary and Secondary Patterns, changing the data profile Action on Panorama deletes all Secondary Pattern match criteria.
- Select the data profile created on Strata Cloud Manager.
- Set the data profile Action to Block traffic that matches the data profile match criteria.
- Select CommitCommit to Panorama and Commit.
- Click OK.
- Select CommitPush to Devices and Edit Selections.
- Select Device Groups and Include Device and Network Templates.
- Push your configuration changes to your managed firewalls that are using Enterprise DLP.
Attach the data profile to a Security policy rule.- Strata Cloud Manager—Modify a DLP Rule on Strata Cloud Manager
- Panorama and Panorama™ management server
- Log in to the Panorama web interface.Select PoliciesSecurity and specify the Device Group.Select the Security policy rule to which you want to add the data profile.Select Actions and set the Profile Type to Profiles.Select the Data Filtering profile you created.Click OK.Select Commit and Commit and Push.