Enterprise DLP
Connect Microsoft Exchange and Enterprise DLP
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Connect Microsoft Exchange and Enterprise DLP
After you create the email transport rules, you must connect Microsoft Exchange and
Enterprise Data Loss Prevention (E-DLP) to complete onboarding.
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Connect Microsoft Exchange to Enterprise Data Loss Prevention (E-DLP) through SaaS Security on Strata Cloud Manager to complete the onboarding.
Before you begin connecting Microsoft Exchange to Enterprise DLP, ensure
that the admin performing the connection has at least Email
Administrator access for Microsoft Exchange. Microsoft
Exchange requires this minimum access privilege to enable Enterprise DLP
API access to Microsoft Exchange.
- Contact your email domain provider to update your SPF record to add the required Enterprise DLP service IP addresses.Add the IP addresses for the region where you host your email domain. You can update your SPF record with multiple regional IP addresses if you have email domains hosted in multiple regions.
- APAC35.186.151.226 and 34.87.43.120
- Australia35.197.179.113 and 35.244.122.65
- Europe34.141.90.172 and 34.107.47.119
- India34.93.185.212 and 35.200.159.173
- Japan34.84.8.170 and 35.221.111.27
- United Kingdom34.105.128.121 and 34.89.40.221
- United States34.168.197.200 and 34.83.143.116
Add a DNS TXT record to your email domain to validate email domain ownership when onboarding the domain to Email DLP.Enterprise DLP validates email domain ownership by requiring you to add a unique, system-generated token to your email domain's DNS TXT records. Enterprise DLP then performs a DNS lookup to verify this token, ensuring only authorized administrators can onboard email domains to Email DLP to prevent domain spoofing.You can add a DNS TXT record for a Microsoft Exchange email domain or you can connect a DNS TXT record at any third party domain provider.Repeat this step for all email domains you plan to onboard to Email DLP.Enterprise DLP doesn't require domain validation if:- The parent domain of a subdomain was already verified.For example, you have already onboarded the parent domain acme.com and Enterprise DLP successfully validated it. In this case, validation of the support.acme.com subdomain isn't required.
- You removed and re-added an onboarded domain within the last 90 days. Enterprise DLP stores domain validation records for all onboarded domains for up to 90 days.For example, you onboarded the acme.com domain and Enterprise DLP successfully validated it. On August 1st, you removed the domain from Email DLP. On September 19th, you added it back to Email DLP. In this case, Enterprise DLP doesn't need to validate the domain again because the domain validation records for the acme.com domain are still stored.
(Best Practices) Confirm you configured Active Directory correctly so that email senders have a manager to approve or reject quarantined emails.Email DLP requires Microsoft Exchange Active Directory to assign a manager to a sender. You can create a transport rule to quarantine and send the email for approval by the sender's manager. A sender must have a manager assigned to successfully quarantine a sender's email if Enterprise DLP detects sensitive data.If you did not assign a manager to a user, then Microsoft Exchange sends the quarantined email to the intended recipient. Microsoft Exchange requires that you assign a user a manager to approve or reject the email.(Best Practices) Save Evidence for Investigative Analysis with Enterprise DLP.Palo Alto Networks recommends configuring evidence storage so you can download emails for investigative analysis when your review Email DLP incidents.Set up the Cloud Identity Engine (CIE).Palo Alto Networks recommends using CIE so you can create targeted Email DLP policy rules.Create the Microsoft Exchange connectors and transport rules, and create the Email DLP Policy.Palo Alto Networks recommends setting up all connectors, transport rules, and Email DLP policy rules to ensure enforcement begins as soon as you successfully connect Microsoft Exchange Online to Enterprise DLP.- The outbound connector controls the flow of emails forwarded from Microsoft Exchange to Enterprise DLP.
- The inbound connector controls the flow of emails forwarded to Enterprise DLP back to Microsoft Exchange.
- Transport rules allow Microsoft Exchange to forward emails to Enterprise DLP and specify the actions Microsoft Exchange takes based on the hosted quarantine, admin approval, manager approval, encrypt, or block transport rules verdicts rendered by Enterprise DLP.
- The Email DLP policy specifies the incident severity and the action Enterprise DLP takes when matching traffic is inspected and sensitive data is detected.
Obtain Your Microsoft Exchange Domain and Relay Host.Log in to Strata Cloud Manager.Select ConfigurationSaaS SecuritySettingsApps Onboarding.Search for Exchange and click Microsoft Exchange.![]() In the Email DLP Instance, click Add Instance.In the Setup Connectors and Rules page, click Continue to Next Section since you have already configured the outbound connector, inbound connector, and transport rules.Configure one or more email domains.Enterprise DLP requires adding one or more email domains and relay hosts to ensure Enterprise DLP can successfully forward inspect emails back to Microsoft Exchange.
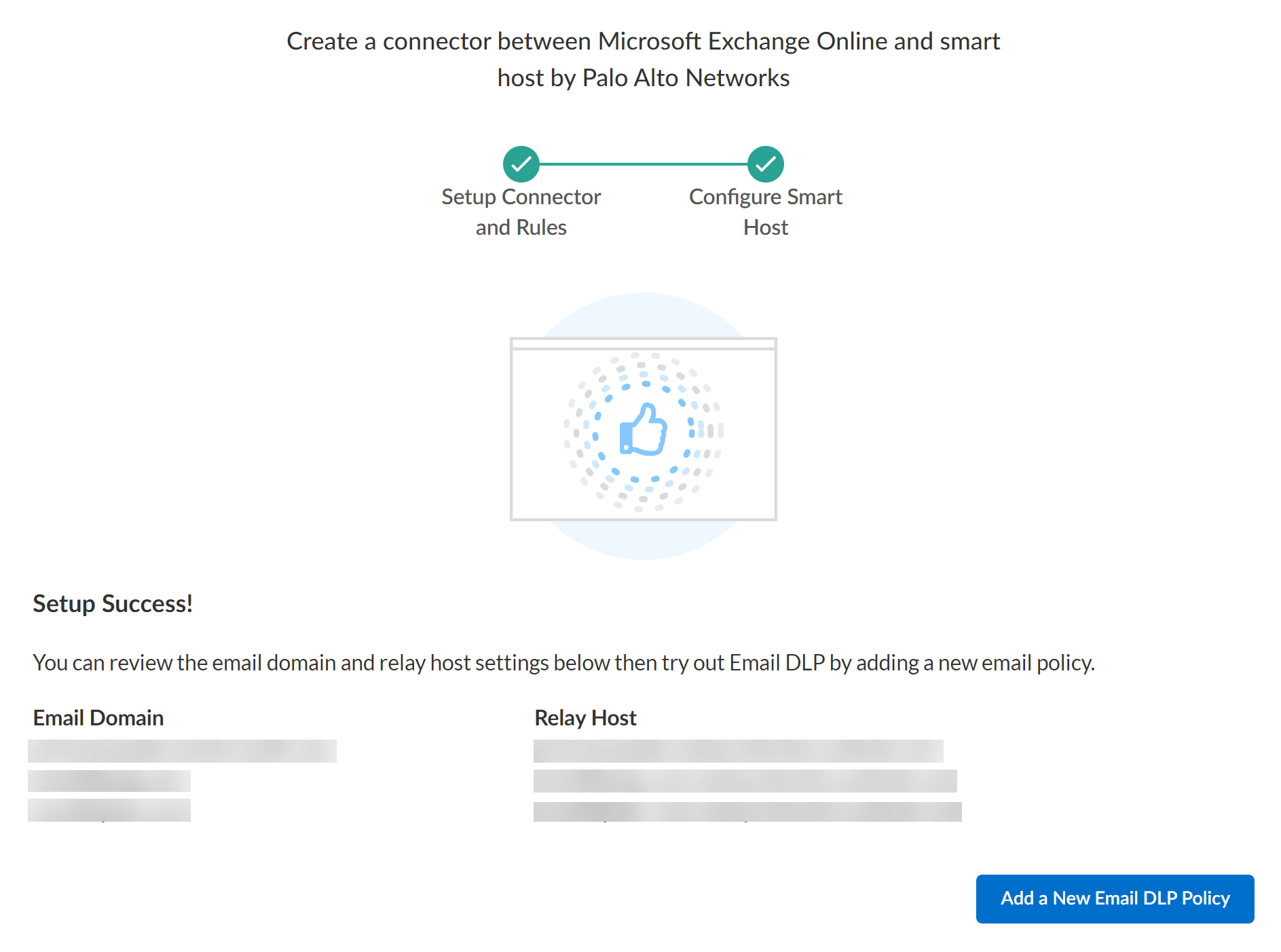
In the Email DLP Instance, click Add Instance.In the Setup Connectors and Rules page, click Continue to Next Section since you have already configured the outbound connector, inbound connector, and transport rules.Configure one or more email domains.Enterprise DLP requires adding one or more email domains and relay hosts to ensure Enterprise DLP can successfully forward inspect emails back to Microsoft Exchange.- (Optional) Enable Custom Routing.If you have a complex multivendor email security chain, enabling custom routing enables Email DLP to scan emails within complex multivendor email security chains while maintaining your existing infrastructure. Custom routing also helps prevent sender spoofing through IP validation.Enter an Email Domain, its corresponding Relay Host, and the networking Port.Obtain Your Microsoft Exchange Domain and Relay Host if you don't have the Microsoft Exchange email domain and relay host immediately available.(Custom Routing) If you enabled custom routing, enter the relay domain of the next hop server.(Optional) Click Add Domain any additional email domains.Connect.(Custom Routing only) For the Source IP Allow List, enter a trusted SMTP traffic source forwarding emails to Enterprise DLP.Enterprise DLP supports static IPv4 addresses and Classless Inter-Domain Routing (CIDR) IP ranges. It takes up to 2 minutes for Email DLP to add domains and IP addresses to the email inspection flow when connecting Email DLP for the first time or editing an existing configuration.The Source IP Allow List restricts Enterprise DLP email acceptance to only those emails originating from your specified IP addresses or address ranges. This prevents spoofing attacks by rejecting emails that claim to be from your organization's domain but come from unauthorized mail servers.Click Add Source IP to add more trusted STMP traffic sources. Email DLP supports up to 20 unique IP addresses and CIDR ranges.Microsoft Exchange is now successfully connected and onboarded.
![]()
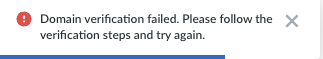
- Domain Validation ErrorThis error message appears if the DNS TXT record for your email domain is missing or incorrect
![]()
Configure the Email DLP settings.- Edit the snippet settings to configure if and how Enterprise DLP stores and masks snippets of sensitive data that match your data pattern match criteria.
- Edit the policy evaluation timeout settings to configure what Enterprise DLP does when Email DLP policy evaluation exceeds the configured timeout.
- Configure evidence storage to save evidence for investigative analysis.