Enterprise DLP
Review Email DLP Incidents
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Review Email DLP Incidents
Review your Enterprise Data Loss Prevention (E-DLP) Email DLP incidents for outbound
emails.
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
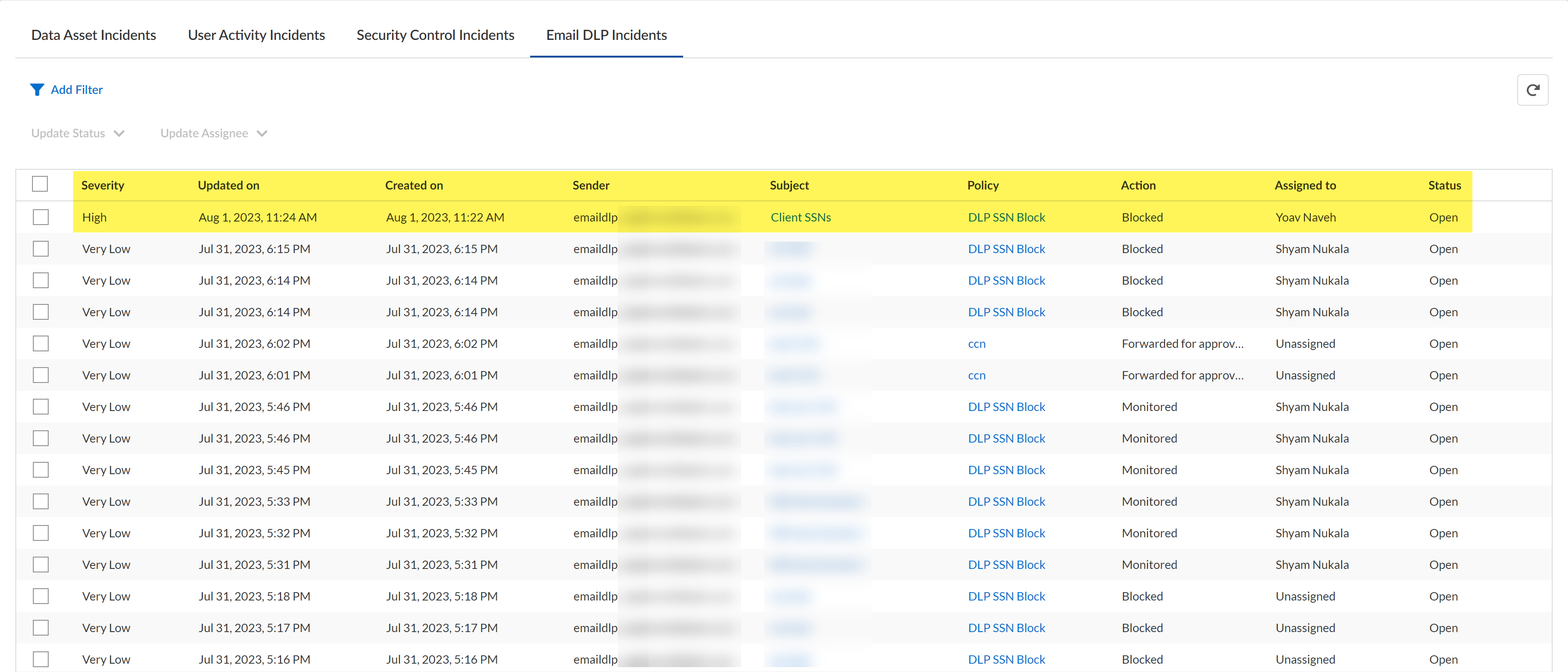
Review your Enterprise Data Loss Prevention (E-DLP) Email DLP incidents to understand which outbound
emails were inspected, review which were blocked, quarantined, or sent for approval,
and to download files inspected by Enterprise DLP.
- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityData SecurityIncidentsEmail DLP Incidents.Review your Email DLP incidents.
- Severity—Severity of the DLP incident specified in the Email DLP policy.
- Updated On—Date the Email DLP incident status or assignee was updated.
- Created On—Date the Email DLP incident occurred.
- Sender—Email of the sender who generated the Email DLP incident.
- Subject—Subject line for the email that generated the Email DLP incident.
- Policy—Email DLP policy rule that the email matched against.
- Action—Action taken by Enterprise DLP based on the Email DLP policy rule the outbound email matched against.
- Assigned to—Incident assignee responsible to review and address the Email DLP incident.
- Status—Resolution status of the Email DLP incident.
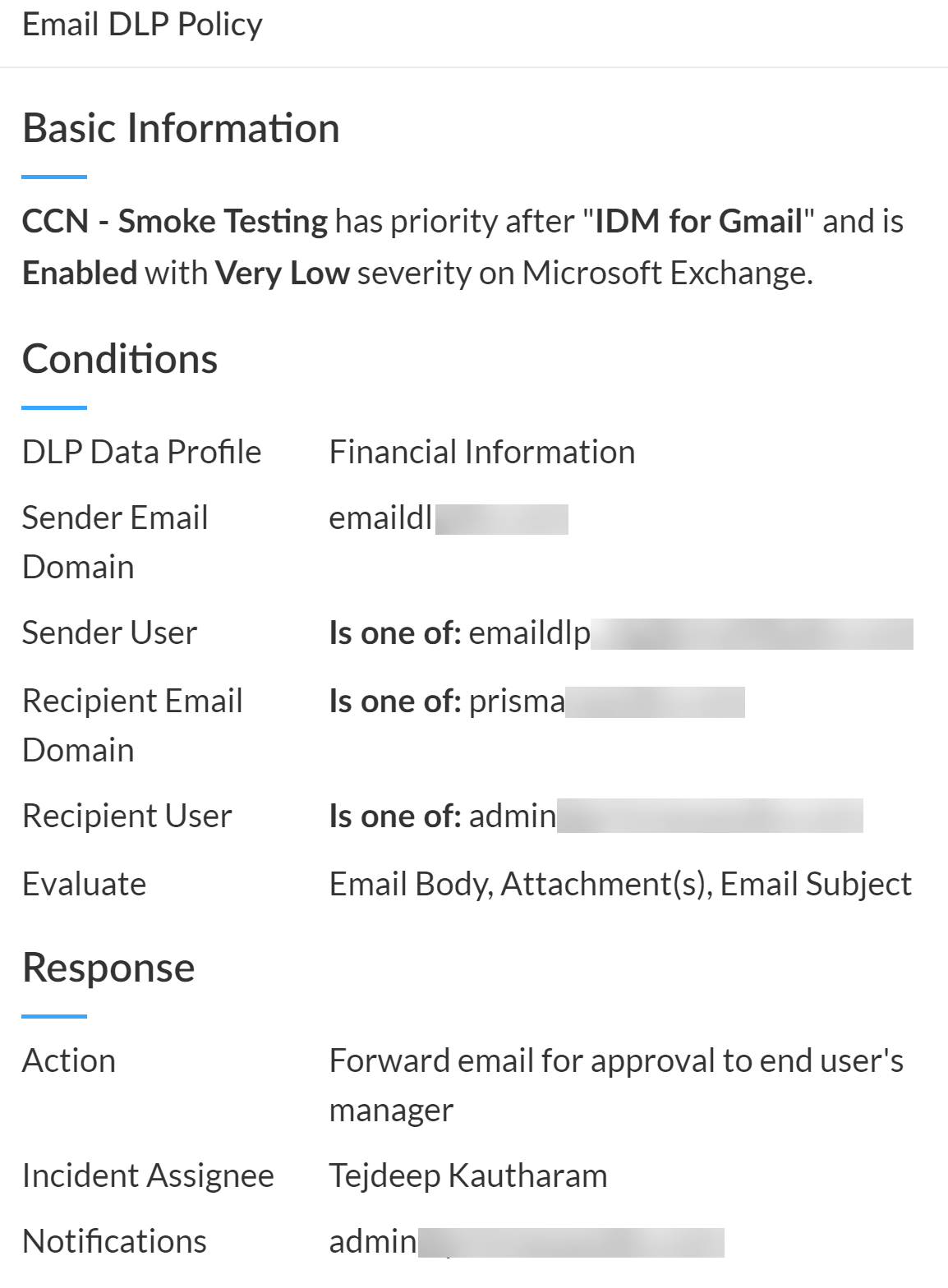
![]() Click the Email DLP Policy to view a summary of the Email DLP policy rule the email matched against.
Click the Email DLP Policy to view a summary of the Email DLP policy rule the email matched against.- Basic Information—Email DLP policy rule priority, whether the rule is Enabled or Disabled, the incident severity, and the email service provider.
- Conditions—Data profile associated with the Email DLP policy rule, the sender and recipient information, and the email components the Email DLP policy rule is configured to evaluate.
- Response— Action configured in the Email DLP policy rule, the primary Incident Assignee specified in the Email DLP policy rule, and the email address that notifications are sent to when an Email DLP incident is generated against this Email DLP policy rule.
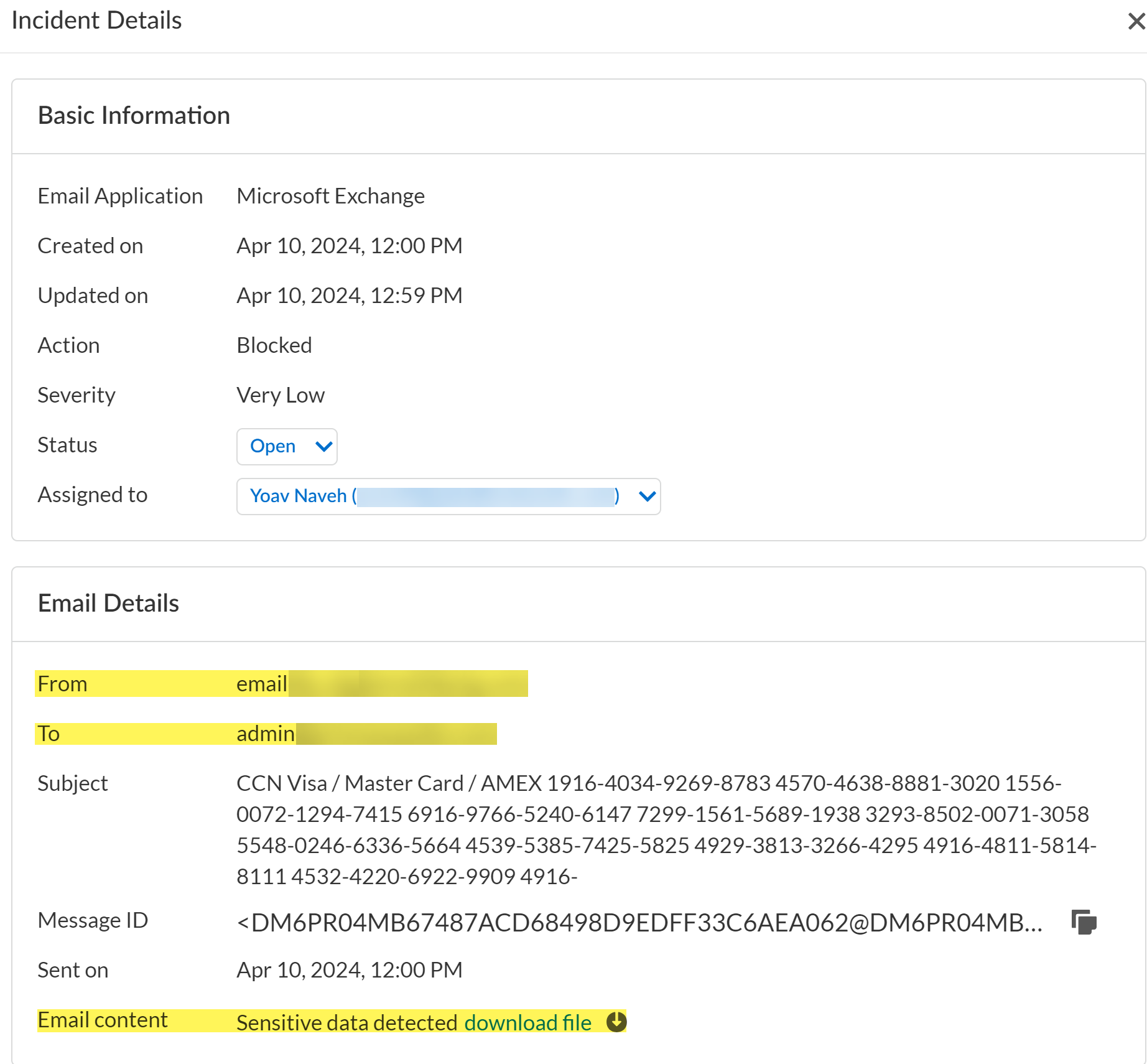
![]() Click the Email DLP incident Subject to view the Incident Details.
Click the Email DLP incident Subject to view the Incident Details.- The From and To fields display the email sender and recipient for the email that generated the DLP incident.
- The Email content field allows you to download the email in .eml format.To successfully download an email, you must have configured evidence storage before the outbound email was inspected by Enterprise DLP. Emails of existing Email DLP incidents cannot be downloaded if you configure evidence storage after the Email DLP incident occurred.
- The Message ID can be used to create a message trace on Microsoft Exchange Online or a custom Email Log Search on Gmail.
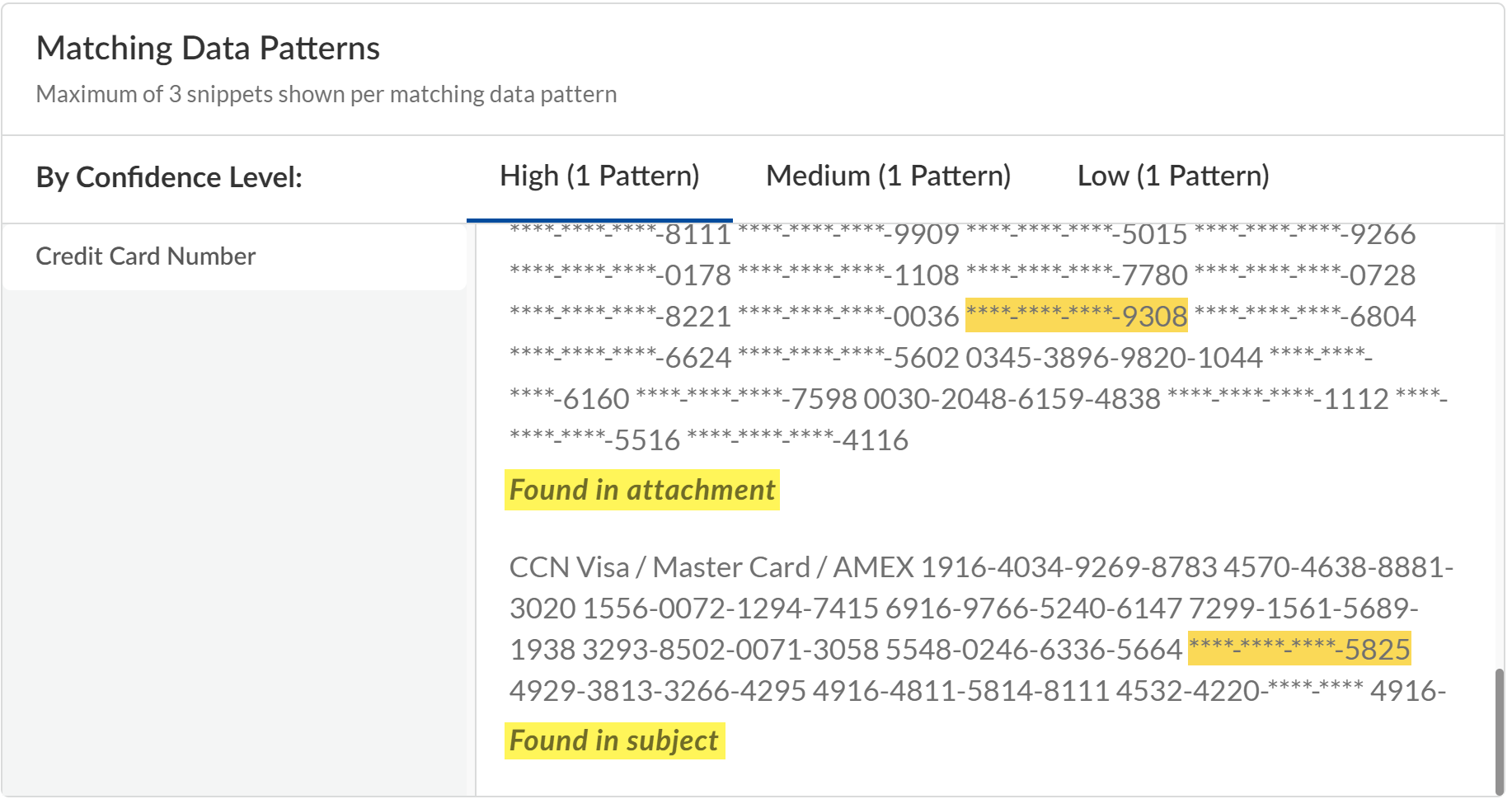
![]() Review the Matching Data Patterns.The Matching Data Patterns shows snippets of the sensitive data Enterprise DLP detected and the data pattern that it matched against. All data patterns added to the data profile are listed in the left-hand side. All traffic matches are grouped by match confidence (High, Medium, and Low) and list the total number of patterns against which traffic matches were detected.Additionally, Enterprise DLP provides the location each snippet was detected in. Enterprise DLPonly inspects the parts of the email configured in the Email DLP policy rule evaluation criteria. Possible values are found in body, found in attachment, or found in subject.
Review the Matching Data Patterns.The Matching Data Patterns shows snippets of the sensitive data Enterprise DLP detected and the data pattern that it matched against. All data patterns added to the data profile are listed in the left-hand side. All traffic matches are grouped by match confidence (High, Medium, and Low) and list the total number of patterns against which traffic matches were detected.Additionally, Enterprise DLP provides the location each snippet was detected in. Enterprise DLPonly inspects the parts of the email configured in the Email DLP policy rule evaluation criteria. Possible values are found in body, found in attachment, or found in subject.![]() (Quarantine only) If an outbound email was quarantined, an email administrator must review and approve these emails before they can continue to their intended recipient.
(Quarantine only) If an outbound email was quarantined, an email administrator must review and approve these emails before they can continue to their intended recipient.- Due to a Gmail limitation, SaaS Security generates two Email DLP logs (ConfigurationSaaS SecurityData SecurityLogsEmail DLP Logs) when a quarantined email is allowed. The first Email DLP log describes the initial outbound email blocked by Email DLP. The second Email DLP log describes the allowed outbound email that is sent back to Enterprise DLP to add x-panw-inspected: true and x-panw-action: monitor to the email header before it continues on its path to the intended recipient.