Download PDF
GlobalProtect
Set Up Cloud Identity Engine Authentication
Table of Contents
Expand All
|
Collapse All
GlobalProtect Docs
-
-
-
-
- 6.3
- 6.2
- 6.1
- 6.0
-
- 6.3
- 6.2
- 6.1
- 6.0
Set Up Cloud Identity Engine Authentication
Cloud Identity Engine authentication for GlobalProtect.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Cloud Identity Engine supports the following authentication methods for
GlobalProtect:
- SAML
- Client Certificate
- OIDC
- Set Up an Authentication Profile.In your environment, navigate to the Add Authentication screen for GlobalProtect.Select Cloud Identity Engine as the authentication method and the profile you created in step 1.Follow the on-screen prompts to set up the desired Cloud Identity authentication.
Cloud Identity Engine SAML Authentication with Embedded Web-View
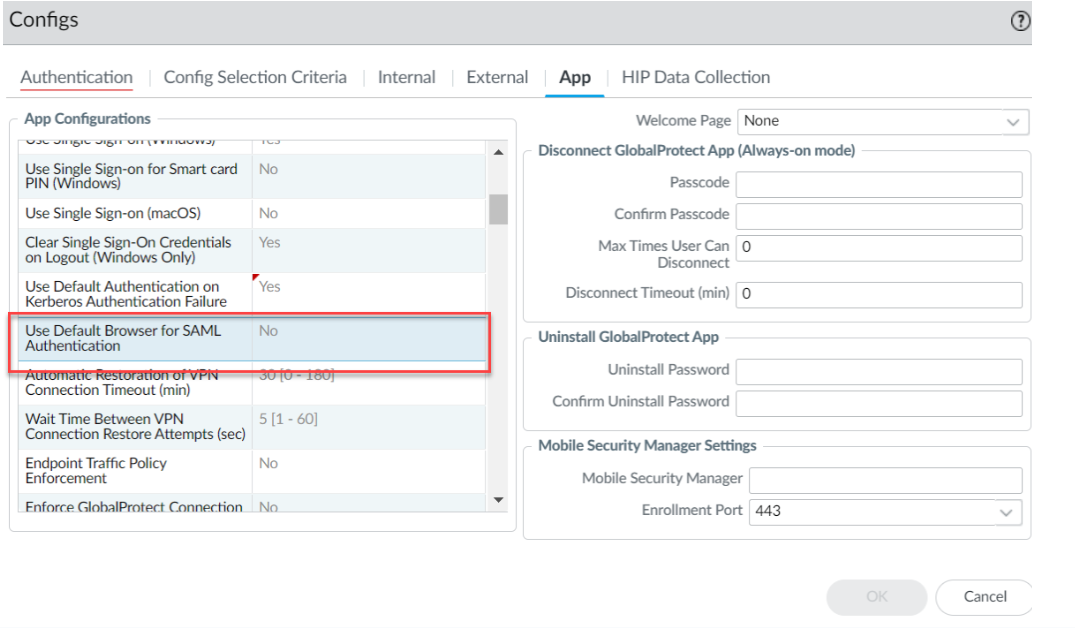
The system browser is the default browser for Cloud Identity Engine SAML Authentication. Follow the steps below to use the embedded web-view: - Disable the Use Default Browser for SAML Authentication
option in the app settings of the portal configuration.
- Select NetworkGlobalProtectPortals<portal-config>Agent<agent-config>App.
- In the App Configurations area, set Use Default Browser
for SAML Authentication option to
No to enable the GlobalProtect app to
open the embedded browser for CIE authentication. After you set the
option as No and when the GlobalProtect app
tries to reconnect, the app prompts the end users to reauthenticate
using CIE as the authentication method.
![]()
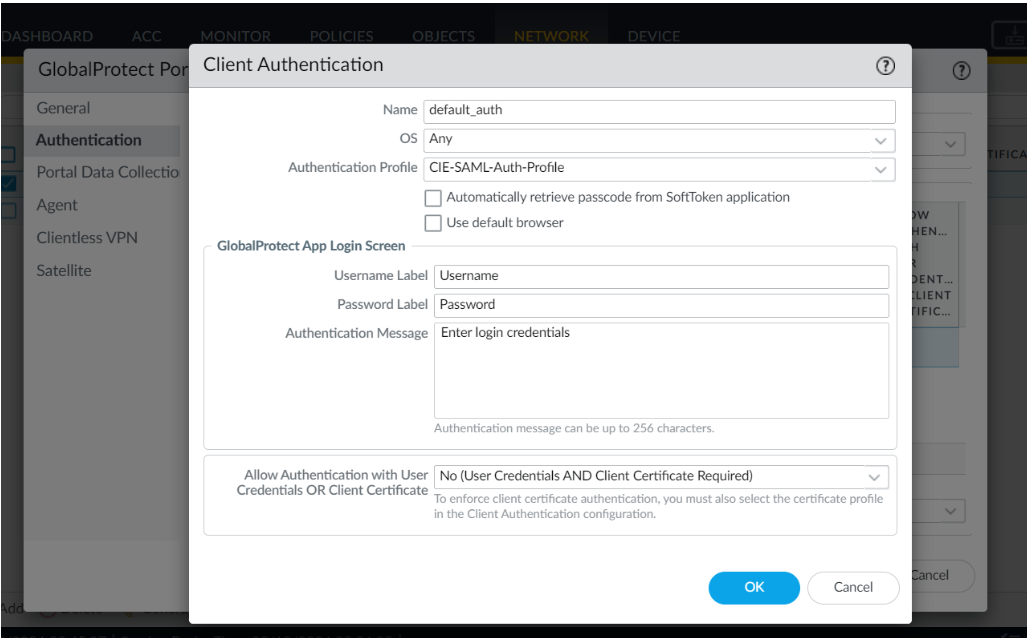
- Set the browser option in the Client Authentication settings of the portal
configuration.
- Select NetworkGlobalProtectPortals<portal-config>Authentication<client-authentication-config> .
- Uncheck the Use default browser option in the
Client Authentication window to use the
embedded browser for CIE authentication.
![]()
- Click OK.
- Commit the configuration.
Cloud Identity Engine Multi-Authentication
You can create an authentication profile that redirects users to the authentication type (either a client certificate or a SAML 2.0-compliant identity provider) you configure for authentication. For more information, see Configure Cloud Identity Engine Authentication on the Firewall or Panorama.With Cloud Identity Engine multi-authentication, you can enable the end user to bypass the SSO hub page (which prompts the user for their SAML username) on Windows endpoints by pre-deploying the following registry key:CASSKIPHUBPAGE using the following syntax:msiexec.exe /i globalprotect64.msi CASSKIPHUBPAGE=yesThe registry key is displayed in the Windows registry path \HKEY_LOCAL_MACHINE\SOFTWARE\Palo Alto Networks\GlobalProtect\Settings.This feature is supported on the default browser and embedded web-view for the following actions:- User unlocks the device
- Device wakes up from sleep mode
- After a system reboot
For the GlobalProtect app with Connect Before Logon (CBL) installed on Windows endpoints, you must use the default browser for Cloud Identity Engine SAML authentication.Before enabling this feature, ensure the following:- Username is configured in UPN format in CIE or the Windows endpoints are joined to Azure domain (AAD or Active Directory).
- The cloud identity engine is configured without the Force authentication option in the authentication profile.
- IDP/SAML session is active.