GlobalProtect
Tunnel Connections Over Proxies
Table of Contents
End-of-Life (EoL)
Tunnel Connections Over Proxies
You can now configure the GlobalProtect app to use proxies
or bypass proxies.
On Windows and macOS platforms, you can configure GlobalProtect to bypass proxies so
that all HTTP/HTTPS traffic that matches the proxy/PAC file rules is required to
traverse the GlobalProtect VPN tunnel before reaching the intended destination. When
you configure the option to bypass proxies, you can prevent users from setting up a
personal proxy to access web resources without going through the VPN tunnel for
inspection and policy enforcement.
If you enable GlobalProtect to use proxies on Windows endpoints, only the HTTP/HTTPS
traffic that matches the proxy/PAC file rules goes through the proxy directly after
users establish the GlobalProtect connection. All other traffic that matches the
access routes configured on the GlobalProtect gateway goes through the tunnel
established over the proxy. On macOS endpoints, proxies are disabled after users
establish the GlobalProtect connection. This occurs because proxy settings are not
copied from the physical network adapter of the endpoint to the virtual network
adapter of the endpoint, and the virtual network adapter becomes the primary adapter
from which the macOS endpoint receives proxy settings.
The following tables describe network traffic behavior based on the endpoint OS,
tunnel type, and GlobalProtect proxy use.
|
Tunnel Type
|
GlobalProtect Uses Proxies
|
GlobalProtect Bypasses Proxies
|
|---|---|---|
|
SSL
|
|
|
|
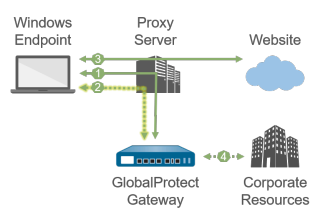
1—All login requests go through the proxy.
|
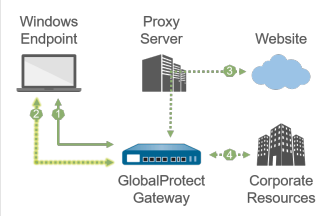
1—All login requests bypass the proxy and go directly
to the gateway.
| |
|
2—SSL tunnel setup goes through the proxy.
|
2—SSL tunnel setup bypasses the proxy and goes
directly to the gateway.
| |
|
3—HTTP/HTTPS traffic that matches the proxy/PAC file
rules goes through the proxy and bypasses the SSL
tunnel.
|
3—HTTP/HTTPS traffic that matches the proxy/PAC file
rules goes through the SSL tunnel and then through the
proxy.
If the proxy is unreachable from the gateway, HTTP/HTTPS
traffic is dropped, and users cannot access the intended
destination.
| |
|
4—Other traffic that matches the access routes
configured on the gateway goes through the SSL tunnel built
over the proxy.
|
4—Other traffic that matches the access routes
configured on the gateway bypasses the proxy and goes
through the SSL tunnel.
| |
|
IPSec
|
You cannot set up an IPSec tunnel through a proxy because
proxies do not support UDP traffic.
|
|
|
1—All login requests go through the proxy.
|
1—All login requests bypass the proxy and go directly
to the gateway.
| |
|
2—IPSec tunnel setup bypasses the proxy and goes
directly to the gateway.
|
2—IPSec tunnel setup bypasses the proxy and goes
directly to the gateway.
| |
|
3—HTTP/HTTPS traffic that matches the proxy/PAC file
rules goes through the proxy and bypasses the IPSec
tunnel.
|
3—HTTP/HTTPS traffic that matches the proxy/PAC file
rules goes through the IPSec tunnel and then through the
proxy.
If the proxy is unreachable from the gateway, HTTP/HTTPS
traffic is dropped, and users cannot access the intended
destination.
| |
|
4—Other traffic that matches the access routes
configured on the gateway bypasses the proxy and goes
through the IPSec tunnel.
|
4—Other traffic that matches the access routes
configured on the gateway bypasses the proxy and goes
through the IPSec tunnel.
|
|
Tunnel Type
|
GlobalProtect Uses Proxies
|
GlobalProtect Bypasses Proxies
|
|---|---|---|
|
SSL
|
|
|
|
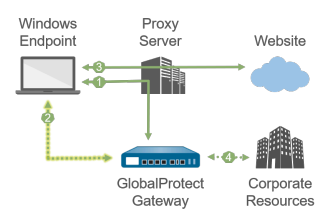
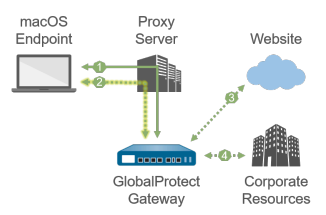
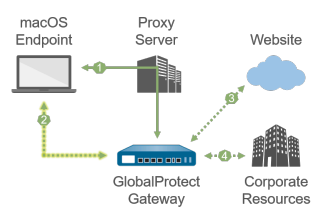
1—All login requests go through the proxy.
|
1—All login requests go through the proxy.
| |
|
2—SSL tunnel setup goes through the proxy.
|
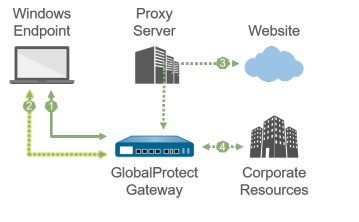
2—SSL tunnel setup bypasses the proxy and goes
directly to the gateway.
| |
|
3—HTTP/HTTPS traffic that matches the proxy/PAC file
rules goes through the SSL tunnel built over the proxy.
|
3—HTTP/HTTPS traffic that matches the proxy/PAC file
rules bypasses the proxy and goes through the SSL
tunnel.
| |
|
4—Other traffic that matches the access routes
configured on the gateway goes through the SSL tunnel built
over the proxy.
|
4—Other traffic that matches the access routes
configured on the gateway bypasses the proxy and goes
through the SSL tunnel.
| |
|
IPSec
|
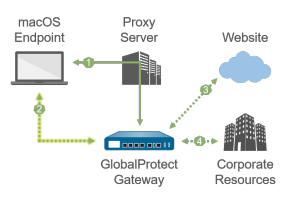
You cannot set up an IPSec tunnel through a proxy because
proxies do not support UDP traffic.
| |
|
1—All login requests go through the proxy.
| ||
|
3—IPSec tunnel setup bypasses the proxy and goes
directly to the gateway.
| ||
|
3—HTTP/HTTPS traffic that matches the proxy/PAC file
rules bypasses the proxy and goes through the IPSec
tunnel.
| ||
|
4—Other traffic that matches the access routes
configured on the gateway bypasses the proxy and goes
through the IPSec tunnel.
| ||
