Network Security
Security Profile Groups
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Security Profile Groups
A Security profile group is a set of security profiles that can be treated as a unit and
then easily added to Security policies.
A Security profile group is a set of security profiles that can be treated as a unit and then
easily added to Security policies. Profiles that are often assigned together can be
added to profile groups to simplify the creation of Security policies. For example, you
can create a Security profile group for threats that includes profiles for Antivirus,
Anti-Spyware, and Vulnerability Protection and then create a Security rule that includes
the threats profile. Similarly, Antivirus, Anti-Spyware, Vulnerability Protection, URL
filtering, and file blocking profiles that are often assigned together can be combined
into profile groups to simplify the creation of Security policies. You can also setup a
default security profile group—new security policies will use the settings defined in
the default profile group to check and control traffic that matches the Security policy.
Name a security profile group default to allow the profiles in that group to be added to
new Security policies by default. This allows you to consistently include your
organization’s preferred profile settings in new policies automatically, without having
to manually add security profiles each time you create new rules.
Here are the Security Profile settings:
Security Profile
Group Settings | Description |
|---|---|
Name | The profile group name (up to 31 characters). This
name appears in the profiles list when defining Security policies.
The name is case-sensitive and must be unique. Use only letters,
numbers, spaces, hyphens, and underscores. |
Shared (Panorama only) | When a profile group is Shared, the profile group
to be available to:
|
Disable override (Panorama only) | Prevents administrators from overriding
the settings of this Security Profile group object in device groups
that inherit the object. By default, the administrators can override
the settings for any device group that inherits the object. |
Profiles | Profiles to be included in this group, for example,
Antivirus, Anti-Spyware, Vulnerability Protection, URL filtering,
and/or file blocking. Data filtering profiles can also be specified
in Security Profile groups. |
Create a Security Profile Group
While Security rules enable you to allow or block traffic on your network, Security
profiles help you define an allow but scan rule, which scans allowed
applications for threats, such as viruses, malware, spyware, and DDOS attacks. When
traffic matches the allow rule defined in the Security policy, the Security
profile(s) that are attached to the rule are applied for further content inspection
rules such as antivirus checks and data filtering.
Security profiles are the only profiles that attach to security rules.
Profiles and the security rules that they attach to must be of the same type.
- Security profiles are not used in the match criteria of a traffic flow. The Security profile is applied to scan traffic after the application or category is allowed by the Security policy.
- You must create a security profile group to add security profiles to policy rule in Strata Cloud Manager, but PAN-OS and Panorama do not have this requirement.
You can use out of the box default Security profiles to begin protecting your network
from threats. See Set Up a Basic Security Policy for
information on using the default profiles in your Security policy.
For recommendations on the best-practice settings for Security profiles, see
Create Best Practice Security Profiles for
the Internet Gateway.
Security Profile Groups streamline the management and
application of security settings, allowing you to apply a set of predefined profiles
to traffic based on their security requirements.
Create a Security Profile Group (Strata Cloud Manager)
Create a security profile group and add it to a Security policy.
In Strata Cloud Manager, a Security profile is only active when these two things are
in place:
- The Security profile is in a profile groupA profile group is a set of profiles—it can contain one profile from each profile type.
- A Security rule is referencing the profile groupWhen a Security rule is referencing a profile group, you can make updates to the individual profiles and the group without editing the Security rule. The Security rule automatically enforces your changes, without requiring you to make a policy commit.To get started, you’ll need to:
- Add a profile groupWhen adding a Security Profile Group to your configuration, begin by providing a descriptive name and optional description to identify the purpose and functionality of the group.
- Choose your Security Profiles Select the security profiles you wish to include within the group. These profiles can encompass various security aspects such as antivirus, antispyware, vulnerability protection, URL Filtering, and more. Customize each selected profile based on specific security rules and threat prevention needs.After configuring the profiles, associate the profile group with security rules to ensure consistent and comprehensive threat prevention. Implement this association by editing existing security rules or creating new ones, referencing the Security Profile Group accordingly.
- Review your Security Profile GroupRegularly reviewing and updating your Security Profile Groups is crucial to adapt to evolving threats and security requirements. This iterative process involves fine-tuning profile settings and incorporating new threat intelligence to optimize security efficacy. By effectively utilizing security profile groups, you can streamline security policy management, achieve granular threat prevention, and fortify your network against a wide array of cyberthreats.
Use the following steps to create a security profile group and add it to a Security policy. - Add a profile group
- Create a security profile group.If you name the group default, it'll be automatically attached to any new rules you create. This is a time saver if you have a preferred set of security profiles that you want to make sure get attached to every new rule.
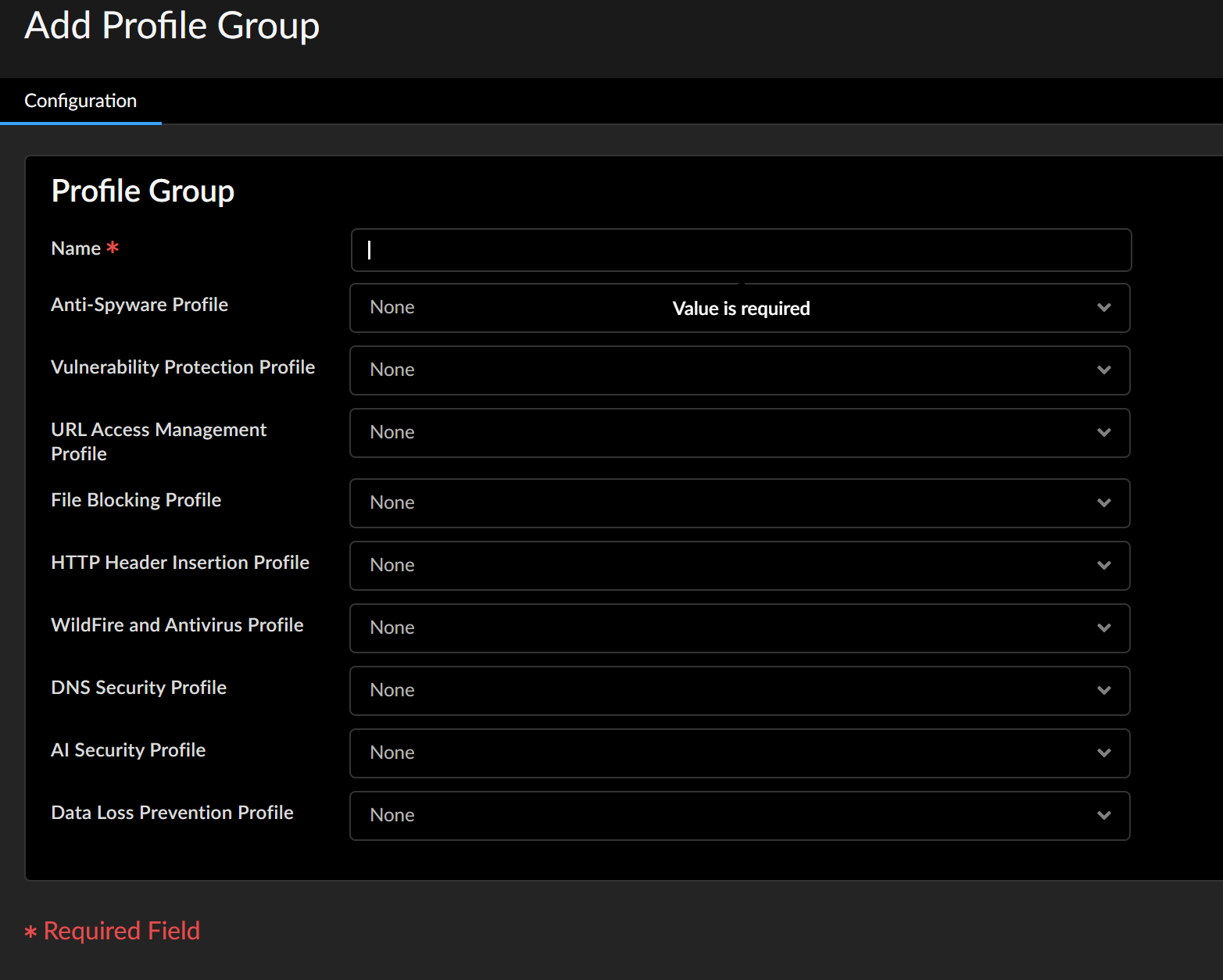
- Select ConfigurationNGFW and Prisma AccessSecurity ServicesProfile Groups and Add Profile Group.Give the profile group a descriptive Name, for example, Threats.Add existing profiles to the group.
![]() Select Save to save the profile group.Add your security profile group to a Security policy.
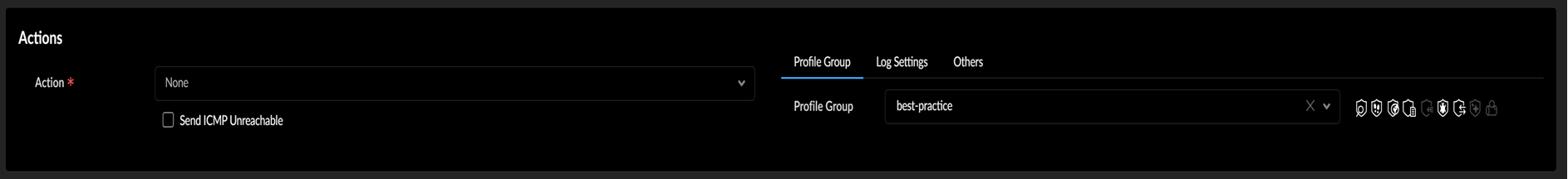
Select Save to save the profile group.Add your security profile group to a Security policy.- Select ConfigurationNGFW and Prisma AccessSecurity ServicesSecurity Policy and Add Rule or modify a security security rule.In the Profile Group drop-down in the Actions tab, select the group you created (for example, select the best-practice group):
![]() Select Save to save the security rule.Select Push Config to push your configuration changes to your network.
Select Save to save the security rule.Select Push Config to push your configuration changes to your network.Set Up or Override a Default Security Profile Group
A Security Profile Group streamlines the management and application of security settings, allowing you to apply a set of predefined profiles to traffic based on their security requirements.Additionally, you can set up a default Security Profile Group to be used in new security rules, or to override an existing default group. When you create a new Security policy, the default profile group is automatically selected as the policy’s profile settings, and traffic matching the policy are checked according to the settings defined in the profile group (you can choose to manually select different profile settings if desired).If you have an existing default Security Profile Group, and you don't want that set of profiles to be attached to a new security rule, you can override the default Security Profile Group and select a different profile group.Use the following options to set up a default Security Profile Group or to override your default settings.- Set up a default security profile group.
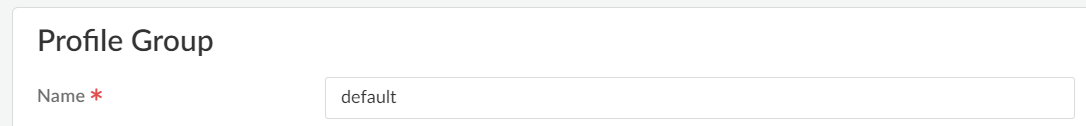
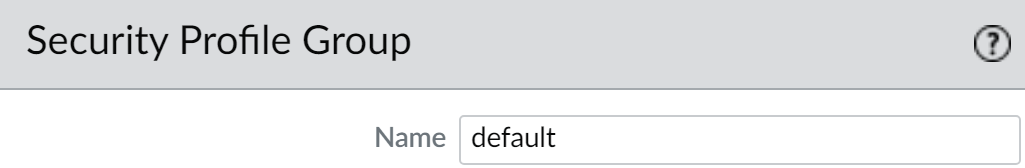
- Select ConfigurationNGFW and Prisma AccessSecurity ServicesProfile Groups and add a new security profile group or modify an existing security profile group.Name the security profile group default:
![]() Select Save and Push Config.Confirm that the default security profile group is included in new security rules by default:
Select Save and Push Config.Confirm that the default security profile group is included in new security rules by default:- Select ManageConfigurationNGFW and Prisma AccessSecurity ServicesSecurity Policy and Add Rule.
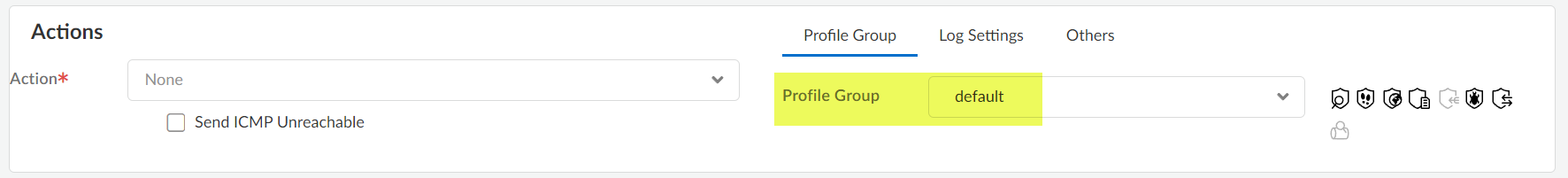
- Select the Actions tab and view the Profile Setting fields:
![]() The new Security policy has the default Profile Group selected.
The new Security policy has the default Profile Group selected.
Override a default security profile group.If you have an existing default security profile group, and you do not want that set of profiles to be attached to a new security rule, you can select a different Profile Group.
Create a Security Profile Group (PAN-OS & Panorama)
Create a security profile group and add it to a Security policy.To get started, you’ll need to:- Add a profile groupWhen adding a Security Profile Group to your configuration, begin by providing a descriptive name and optional description to identify the purpose and functionality of the group.
- Choose your Security Profiles Select the security profiles you wish to include within the group. These profiles can encompass various security aspects such as antivirus, antispyware, vulnerability protection, URL Filtering, and more. Customize each selected profile based on specific security rules and threat prevention needs.After configuring the profiles, associate the profile group with Security policy rules to ensure consistent and comprehensive threat prevention. Implement this association by editing existing security rules or creating new ones, referencing the Security Profile Group accordingly.
- Review your Security Profile GroupRegularly reviewing and updating your Security Profile Groups is crucial to adapt to evolving threats and security requirements. This iterative process involves fine-tuning profile settings and incorporating new threat intelligence to optimize security efficacy. By effectively utilizing security profile groups, you can streamline Security policy management, achieve granular threat prevention, and fortify your network against a wide array of cyberthreats.
Use the following steps to create a security profile group and add it to a security policy.- Create a security profile group.If you name the group default, the firewall will automatically attach it to any new rules you create. This is a time saver if you have a preferred set of security profiles that you want to make sure get attached to every new rule.
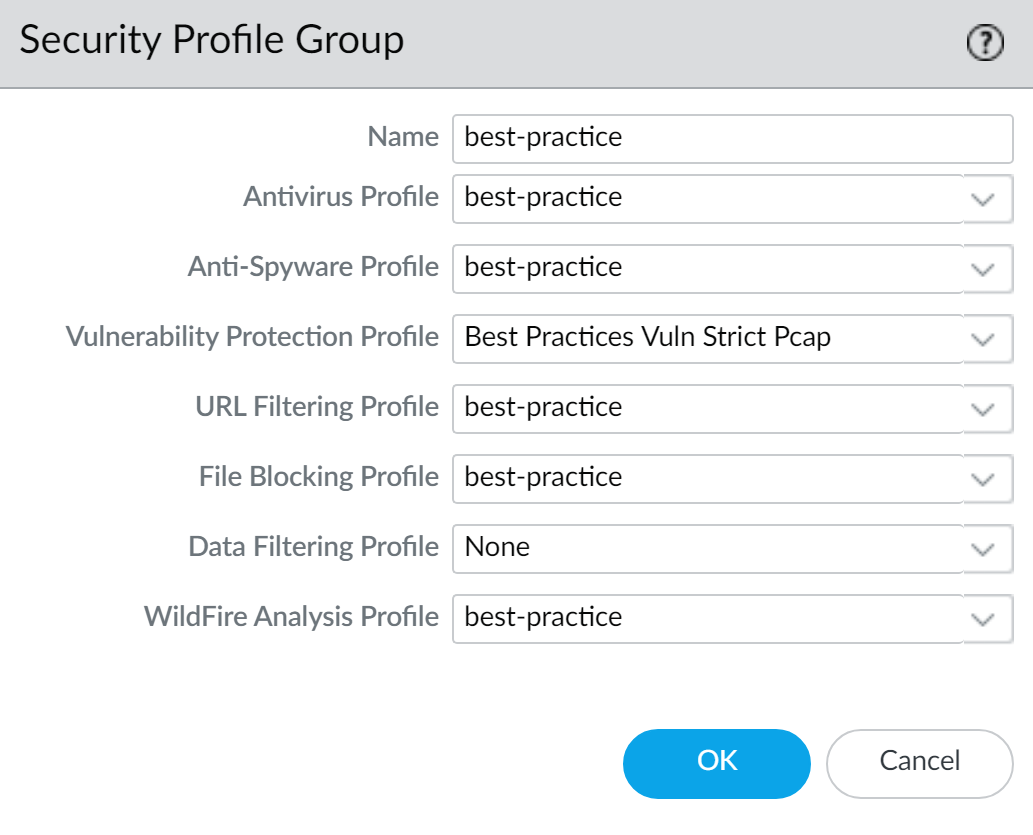
- Select ObjectsSecurity Profile Groups and Add a new security profile group.Give the profile group a descriptive Name, for example, Threats.If the firewall is in Multiple Virtual System Mode, enable the profile to be Shared by all virtual systems.Add existing profiles to the group.
![]() Click OK to save the profile group.Add your security profile to a Security policy.
Click OK to save the profile group.Add your security profile to a Security policy.- Select PoliciesSecurity and Add or modify a security security rule.Select the Actions tab.In the Profile Setting section, select Profiles for the Profile Type.Select the profiles you want to add to your security rule.
![]() Click OK to save the security rule and Commit your changes.
Click OK to save the security rule and Commit your changes.Set Up or Override a Default Security Profile Group
A Security Profile Group streamlines the management and application of security settings, allowing you to apply a set of predefined profiles to traffic based on their security requirements.Additionally, you can set up a default Security Profile Group to be used in new security rules, or to override an existing default group. When you create a new Security policy, the default profile group is automatically selected as the policy’s profile settings, and traffic matching the policy are checked according to the settings defined in the profile group (you can choose to manually select different profile settings if desired).If you have an existing default Security Profile Group, and you don't want that set of profiles to be attached to a new security rule, you can override the default Security Profile Group and select a different profile group.Use the following options to set up a default Security Profile Group or to override your default settings.- Set up a default security profile group.
- Select ObjectsSecurity Profile Groups and add a new security profile group or modify an existing security profile group.Name the security profile group default:
![]() Click OK and Commit.Confirm that the default security profile group is included in new Security policies by default:
Click OK and Commit.Confirm that the default security profile group is included in new Security policies by default:- Select PoliciesSecurity and Add a new Security policy.
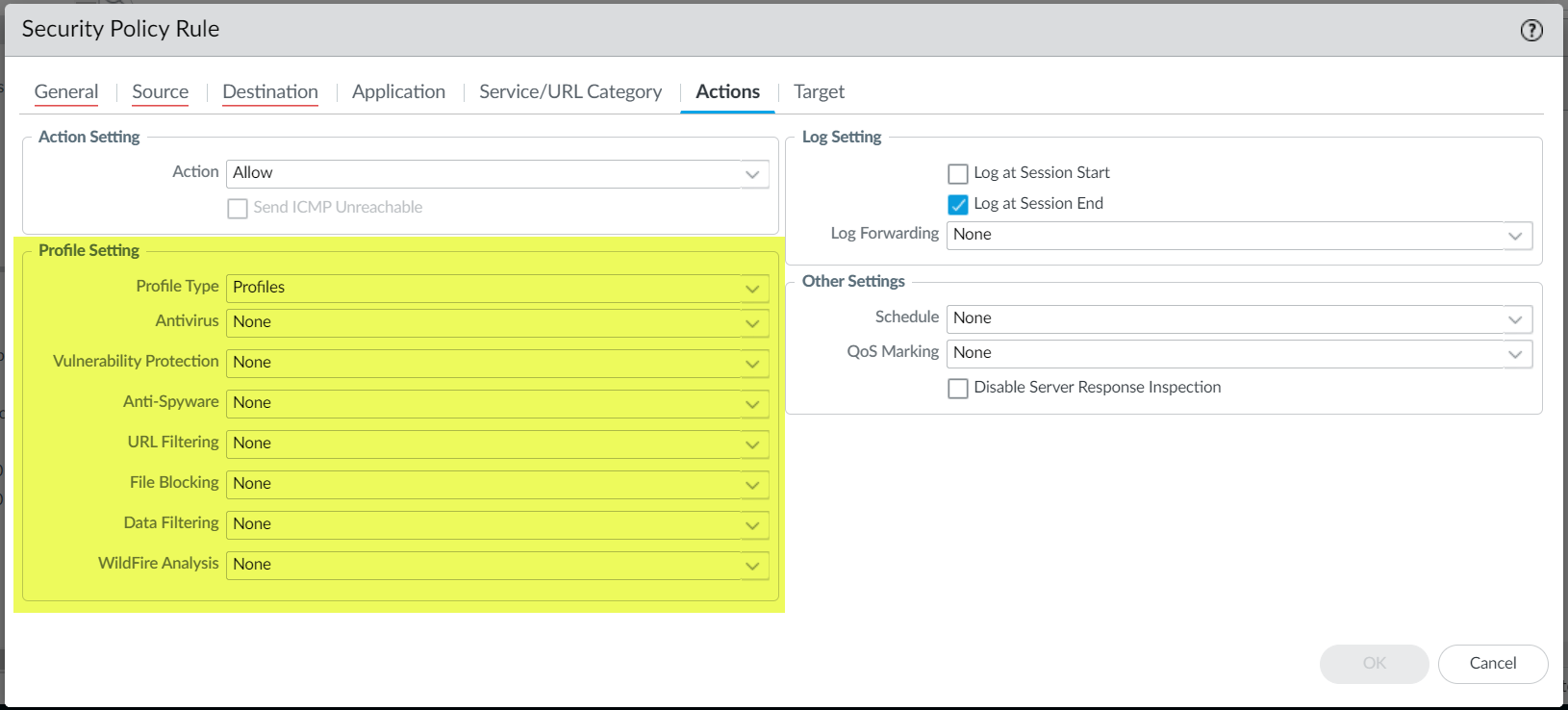
- Select the Actions tab and view the Profile Setting fields:
![]() By default, the new Security policy correctly shows the Profile Type set to Group and the default Group Profile is selected.
By default, the new Security policy correctly shows the Profile Type set to Group and the default Group Profile is selected.
Override a default security profile group.If you have an existing default security profile group, and you do not want that set of profiles to be attached to a new Security policy, you can continue to modify the Profile Setting fields according to your preference. Begin by selecting a different Profile Type for your policy (PoliciesSecuritySecurity Policy RuleActions).