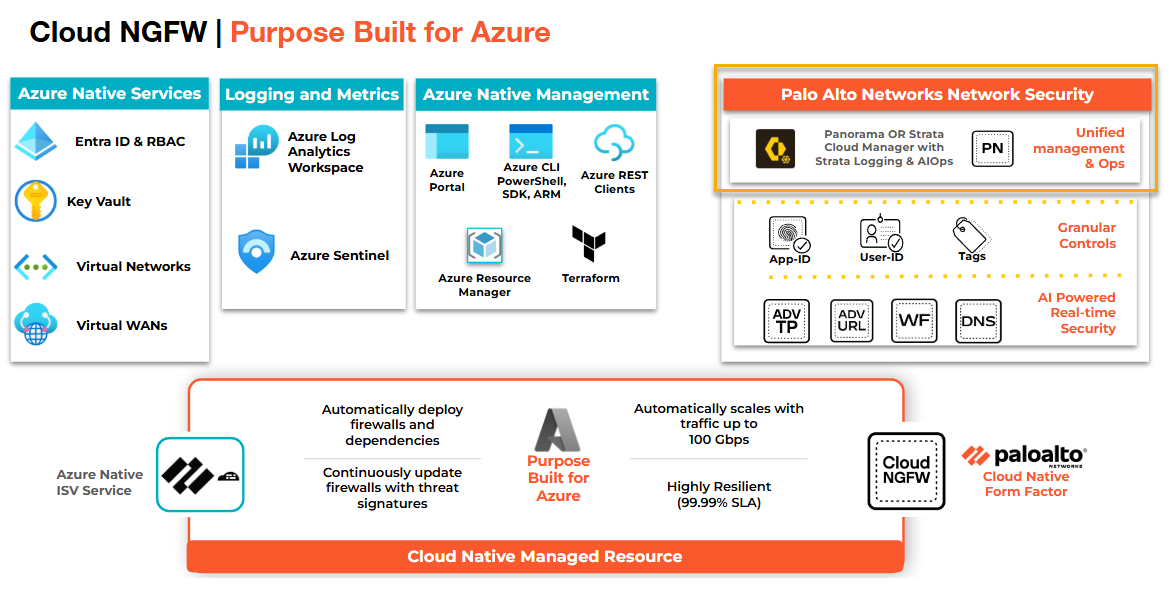
Cloud NGFW for Azure
Strata Cloud Manager Policy Management
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for Azure Docs
Strata Cloud Manager Policy Management
Learn how to link your Cloud NGFW for Azure with Strata Log Manager for policy
management.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can integrate your Cloud NGFW resources with Strata Cloud Manager (SCM) for policy management. With
this integration, you can now use a single Strata Cloud Manager to centrally manage
a shared set of security rules on Cloud NGFW resources alongside your physical and
virtual firewall appliances. You can also manage all aspects of shared policy
configurations, gain comprehensive visibility with actionable insights, and generate
reports on traffic patterns or security incidents of your Cloud NGFW resources, all
from a single console.
You can register your Cloud NGFW resources with an existing Strata Cloud Manager,
which you had previously activated based on your AIOps for NGFW, Prisma Access, or
Strata Cloud Manager Pro licenses. You
currently do not have to create a Strata Cloud Manager to use with Cloud NGFW.
![]()
Prerequisites
To use SCM for policy management:
- If you're deploying the firewall for the first time and your policy management choice is Strata Cloud Manager, first deploy the local rulestack and register it in the Customer Support Portal. Once the rulestack is registered with your Customer Support Portal account, you can deploy the firewall, and it will show existing Strata Cloud Manager tenants associated with the Customer Support Account.
- Ensure that your Cloud NGFW for Azure tenant and Strata Cloud Manager are registered to the same Customer Support Portal (CSP) account.
Create a Cloud NGFW Resource for SCM Policy Management
To must create a new Cloud NGFW resource to use SCM for policy management:
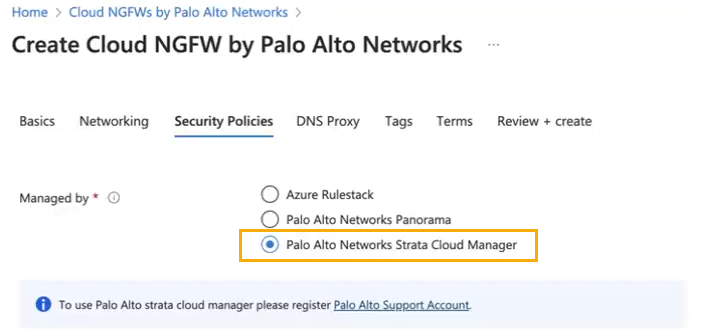
- Log in to the Azure portal and search for Cloud NGFWs by Palo Alto Networks. This displays the Cloud NGFWs you have registered with Azure. For more information, see Start with Cloud NGFW for Azure.Create a new NGFW resource.For more information on creating a new Cloud NGFW for Azure, see Deploy the Cloud NGFW in a vNET or Deploy the Cloud NGFW in a vWAN.In the Settings section, select Security Policies.You can choose Strata Cloud Manager under Security Policies when you deploy the Cloud NGFW resource.In the Security Policies tab, select Managed by Palo Alto Networks Strata Cloud Manager.
![]() If the SCM option does not appear, ensure you have registered with the Customer Support Portal. See the Prerequisites section.Use the drop-down to select the SCM Tenant.
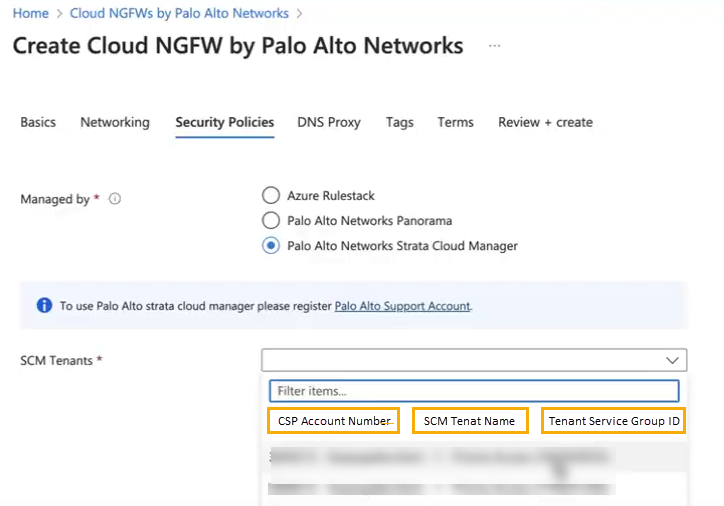
If the SCM option does not appear, ensure you have registered with the Customer Support Portal. See the Prerequisites section.Use the drop-down to select the SCM Tenant.![]() You can filter SCM tenant names to locate the appropriate tenant. For example, enter a portion of the tenant name, or the tenant ID to locate the SCM tenant you want to use for policy management.
You can filter SCM tenant names to locate the appropriate tenant. For example, enter a portion of the tenant name, or the tenant ID to locate the SCM tenant you want to use for policy management.View the Firewall in Strata Cloud Manager
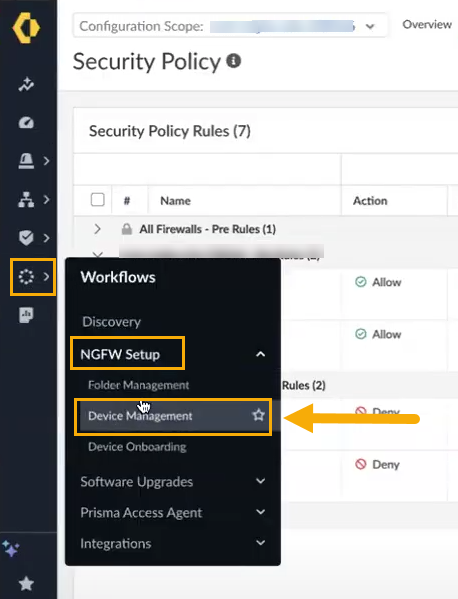
After creating your Cloud NGFW resource, you can use SCM to manage the policy.When you log into Strata Cloud Manager, the dashboard may fail to display the Cloud NGFW count under NGFW > Software. Refresh your browser to view the newly linked firewall.- Log in to the Strata Cloud Manager app from the Palo Alto Networks hub directly at stratacloudmanager.paloaltonetworks.com.Select Workflows > NGFW Setup > Device Management:
![]() The Device Management screen displays the NGFWs and Cloud NGFWs. Click Cloud NGFWs to display the firewalls associated with the SCM tenant:
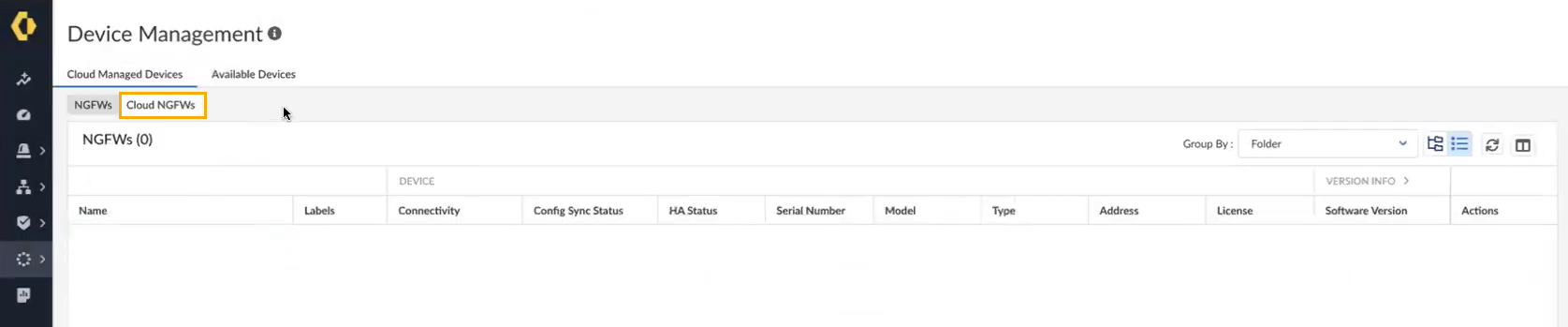
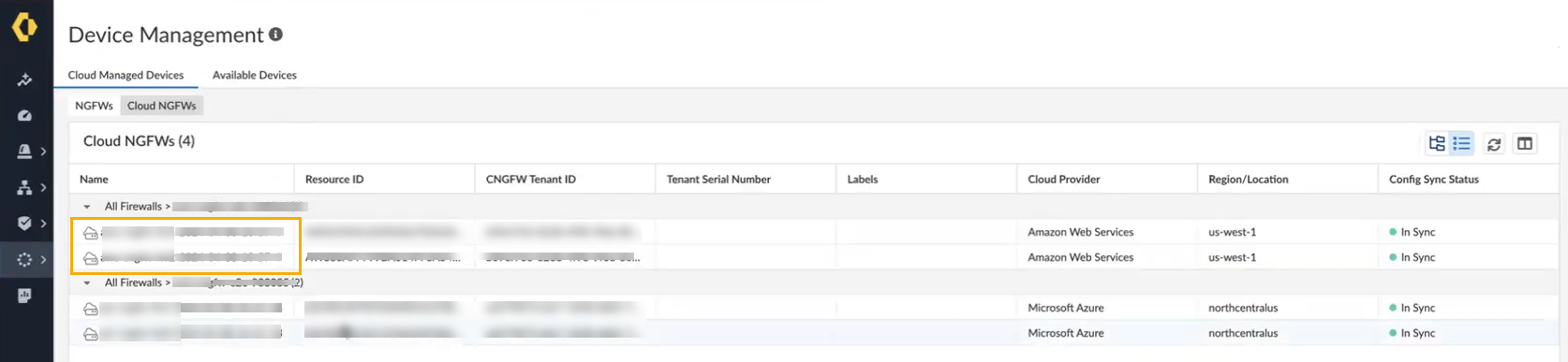
The Device Management screen displays the NGFWs and Cloud NGFWs. Click Cloud NGFWs to display the firewalls associated with the SCM tenant:![]() The Device Management screen displays the Cloud NGFW resources that are currently managed by SCM:
The Device Management screen displays the Cloud NGFW resources that are currently managed by SCM:![]() If you don't see Cloud NGFW resources, refresh your screen.The Device Management screen displays the following fields:
If you don't see Cloud NGFW resources, refresh your screen.The Device Management screen displays the following fields:- Name. Represents the name of the Cloud NGFW resource.
- Resource ID. Represents the Cloud NGFW name as it appears in the Azure.
- CNGFW tenant ID. Indicates the Azure tenant ID associated with the subscription for the CNGFW service.
- CNGFW Tenant Serial Number. The serial number associated with the Cloud NGFW tenant.
- Labels. An arbitrary label assigned to the Cloud NGFW.
- Region and Location. The region in which the Cloud NGFW resource is located.
- Config sync Status. The status of the Cloud NGFW resource.When using SCM policy management for the first time, the Config sync status appears Out of Sync; after manually pushing configuration changes the status changes to reflect In sync.
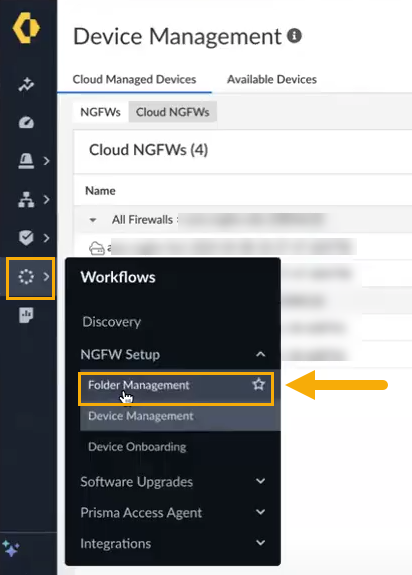
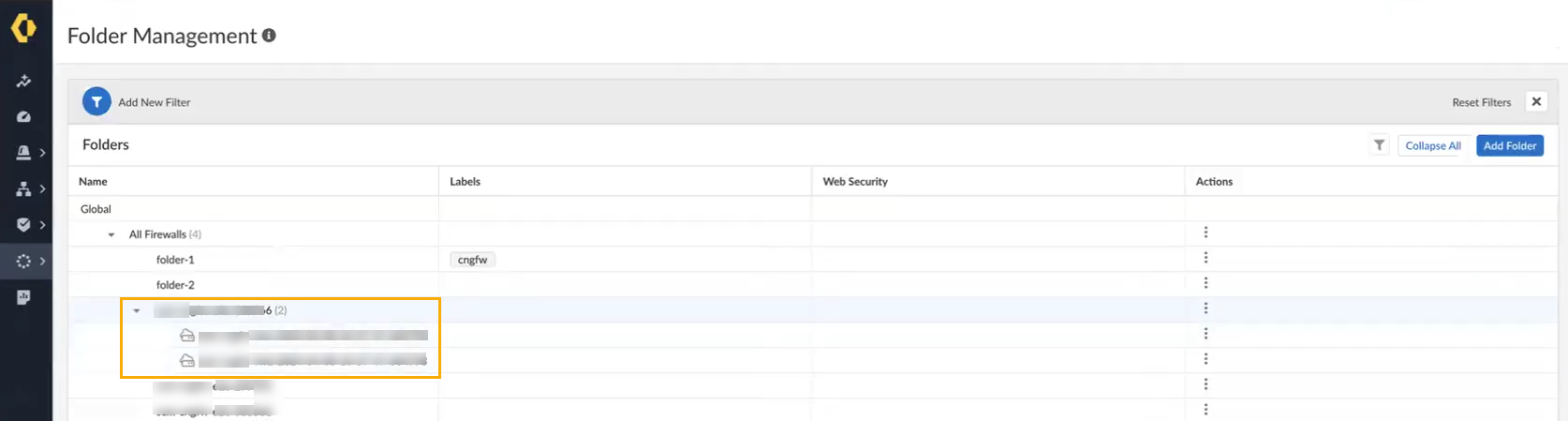
The Device Management screen groups your Cloud NGFW resources into folders. To view the structure of these folders, select Workflows > Folder Management.![]() The Folder Management screen displays the Cloud NGFW resources associated with the SCM tenant:
The Folder Management screen displays the Cloud NGFW resources associated with the SCM tenant:![]()
Create or Move a Folder for Your Cloud NGFW Resource Using Strata Cloud Manager
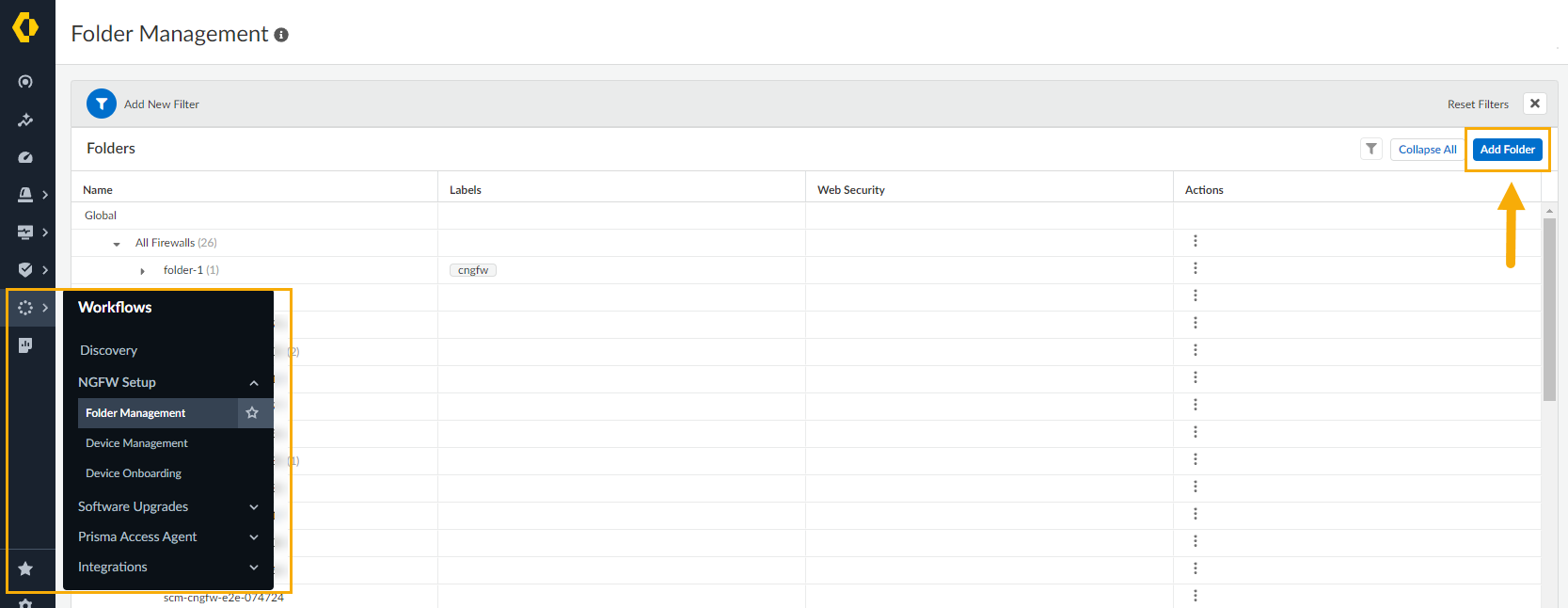
After configuring the appropriate subscription to use the Strata Cloud Manager service for your Cloud NGFW resources, you create a folder to view data associated with your firewall. SCM folders are used to group your Cloud NGFW resources logically to simplify policy management. You can create a folder that contains multiple nested folders to group firewalls and deployments that require similar configurations. Folders that are already nested can have multiple nested folders as well. By default, firewalls linked to SCM are placed in the All Firewalls folder.Folders for other Palo Alto Networks applications, like Prisma Access, and your NGFWs are separate; you can't group NGFWs in a folder with Prisma Access deployments. However, you can easily apply shared settings globally across all folders or use Manage: Snippets to easily apply standard settings and policy requirements across multiple folders.To create a folder for your Cloud NGFW resource:- Log in to the Strata Cloud Manager app from the Palo Alto Networks hub directly at stratacloudmanager.paloaltonetworks.com.In the Strata Cloud Manager console, select Workflows > NGFW Setup > Folder Management and click Add Folder.
![]() In the Create Folder screen:
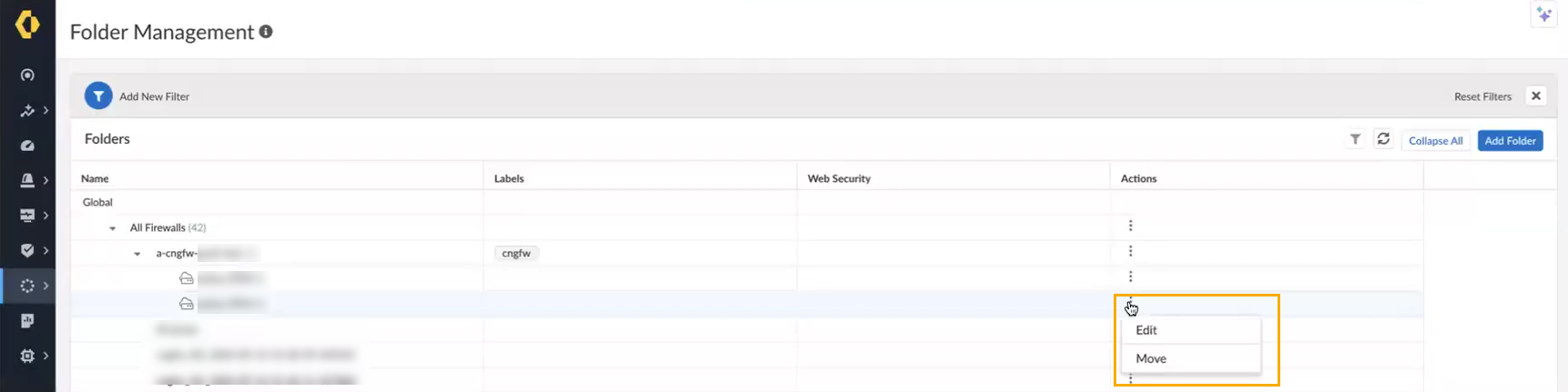
In the Create Folder screen:- Enter a descriptive name for the folder.Optionally provide a description for the folder.Optionally assign one or more labels. You can select an existing label or create a new label by typing the label you want to create. For example, use the Labels drop-down to select cngfw.Specify where to create the folder using the drop-down menu. You can select All Firewalls, or select an existing folder to nest the folder under it. This is a required field.Click Create.To move or edit the folder containing your Cloud NGFW resources to another folder:In the Folder Management screen, select the folder you want to move or edit.In the Actions column, select the vertical ellipsis to Edit or Move a folder:
![]() To move your folder to a different location, in the Move to Different Location screen, select the new Destination from the drop-down menuAfter making changes to the structure of your folder, you can use SCM for policy management and push the configuration changes.For information about pushing changes using SCM policy management, see Manage: Push Config.
To move your folder to a different location, in the Move to Different Location screen, select the new Destination from the drop-down menuAfter making changes to the structure of your folder, you can use SCM for policy management and push the configuration changes.For information about pushing changes using SCM policy management, see Manage: Push Config.Use Strata Cloud Manager for Cloud NGFW Policy Management
At this release, you can use Strata Cloud Manager to globally apply a security rule to the Cloud NGFW resources comprising a folder. All NAT policy rules (including DNS proxy) are applied using the Azure portal.You can optionally forward logs to Azure, which requires you to configure the Azure portal.Important ConsiderationsWhen using SCM for Cloud NGFW as a policy management, consider the following:- When you first connect to SCM, Cloud NGFW resources (for example, the resource ID) may fail to display. These resources will appear after a few moments if there are no underlying connection issues.
- Best practices for Cloud NGFW SCM policy management differ from those using Panorama policy management with your Cloud NGFW resource. For example, some pass-through traffic in a Panorama managed environment may be dropped in an SCM managed Cloud NGFW resource.
- X-Forwarded-For (XFF) functionality isn't supported in an SCM policy management for your Cloud NGFW resource.
- Cloud certificate isn't supported.
- Data loss prevention (DLP) isn't supported.
- When configuring security rules for your SCM-managed Cloud NGFW resource, you must specify ANY for the security rule. However, from/to zone appears as public/private in the Strata Logging Service.
- User-ID and tag-based policy rules are not yet supported.
- Operational visibility and metrics are not supported.
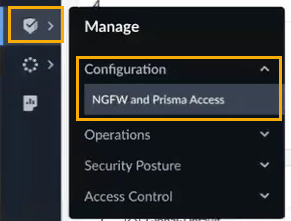
To use SCM for Cloud NGFW policy management:- In Strata Cloud Manager, select Manage > Configuration > NGFW and Prisma Access.
![]() Select Configuration Scope.
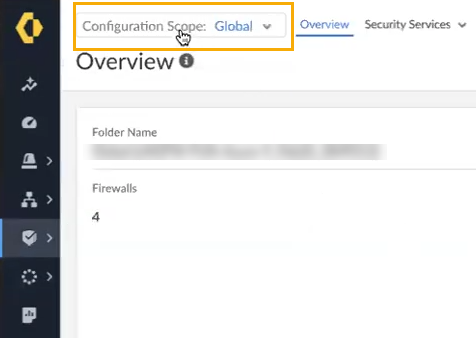
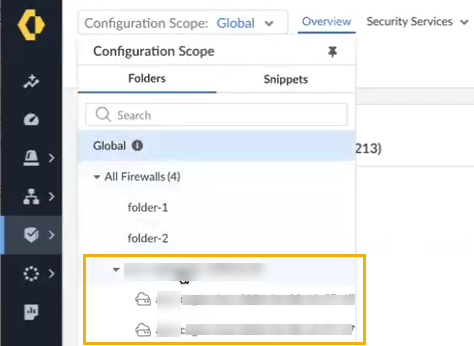
Select Configuration Scope.![]() By default, the Configuration Scope displays Global firewall resources. The scope may represent the Cloud NGFW (rather than a folder). The configuration menu changes automatically to reflect available options. Ensure that device scope configuration is enabled; device scope can't support Cloud NGFW names greater than 30 characters.In the drop-down list, locate the folder containing the Cloud NGFW Azure resources:
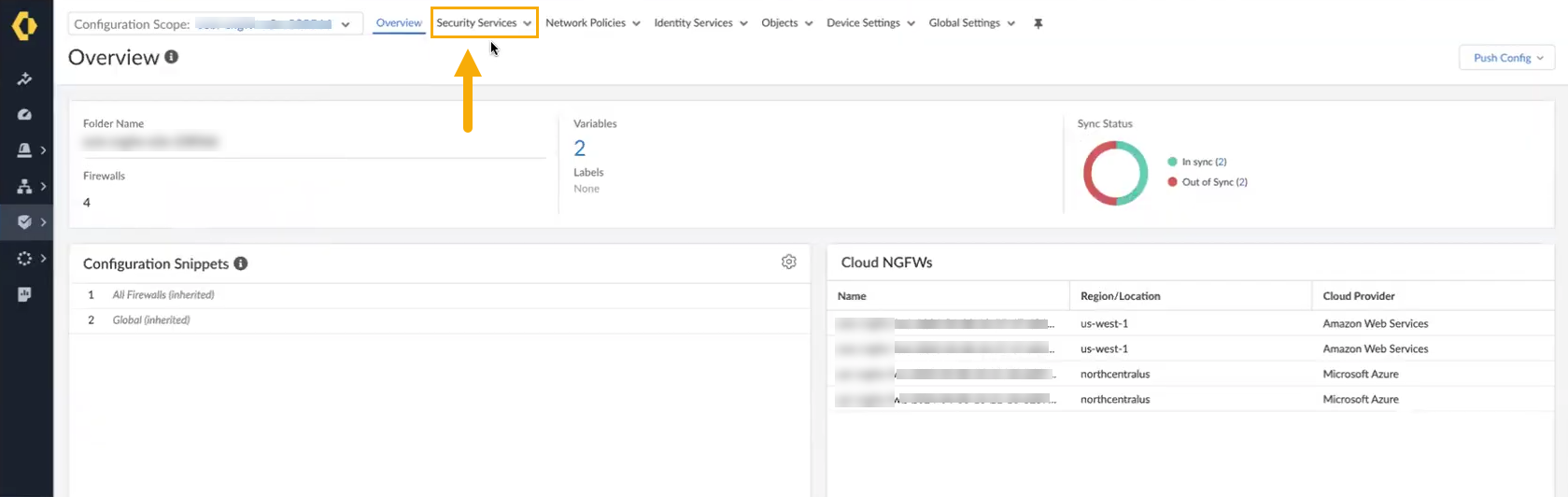
By default, the Configuration Scope displays Global firewall resources. The scope may represent the Cloud NGFW (rather than a folder). The configuration menu changes automatically to reflect available options. Ensure that device scope configuration is enabled; device scope can't support Cloud NGFW names greater than 30 characters.In the drop-down list, locate the folder containing the Cloud NGFW Azure resources:![]() In the Overview page, select Security Services:
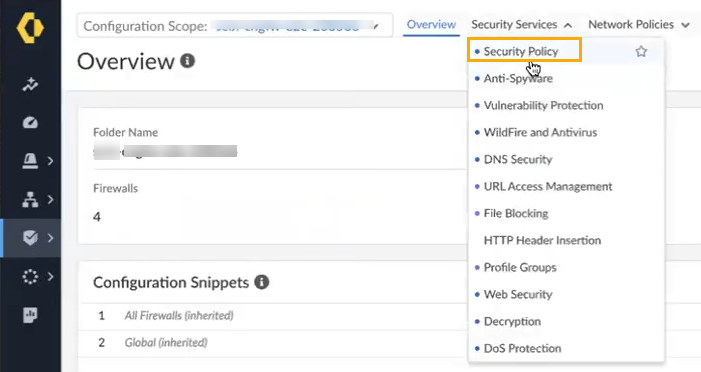
In the Overview page, select Security Services:![]() In the Security Services drop-down list, select Security Policy:
In the Security Services drop-down list, select Security Policy:![]() For more information about configuring Security policy using Strata Cloud Manager, see Manage Security Policy.
For more information about configuring Security policy using Strata Cloud Manager, see Manage Security Policy.Use the Strata Logging Service
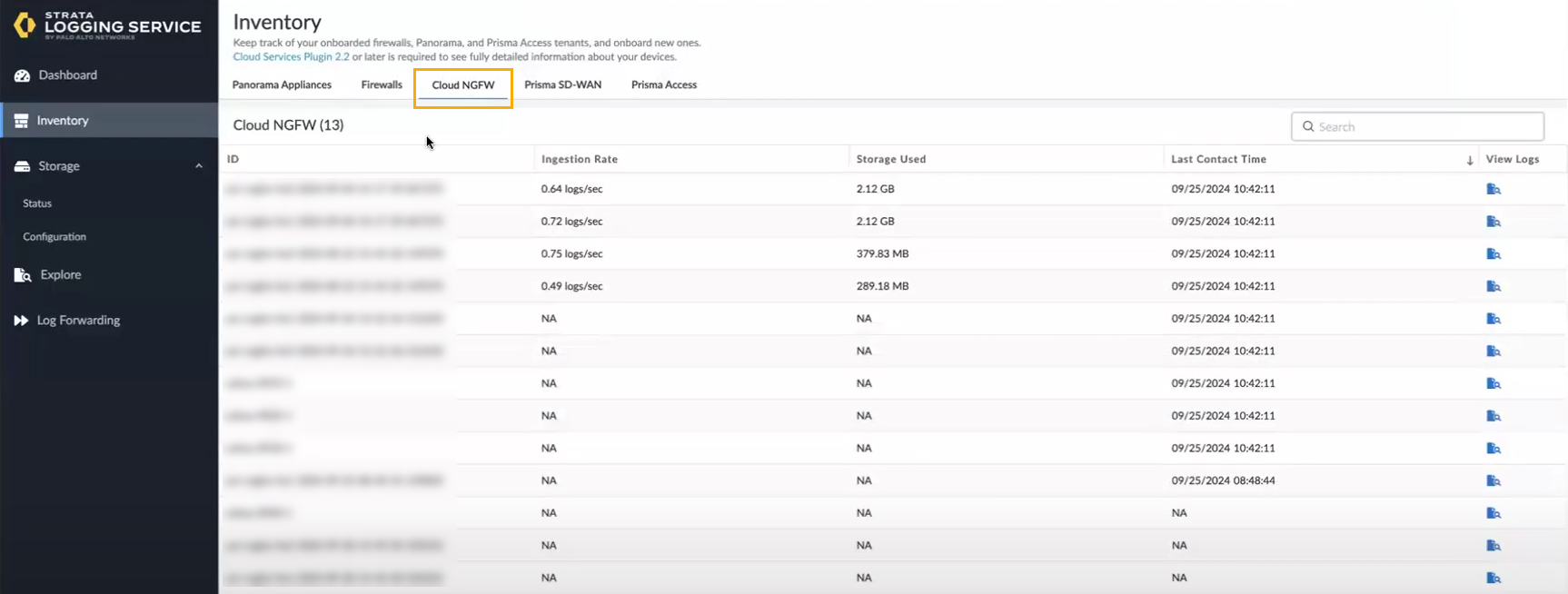
Cloud NGFW supports Strata Logging Service (formerly Cortex Data Lake), a cloud-based logging system that stores context-rich enhanced network logs generated by our security products, including our NGFWs, Prisma Access, and Cloud NGFW for AWS. With Strata Logging Service, you can collect ever-expanding volumes of data without needing to plan for local compute and storage, and it's ready to scale from the start. Learn how to activate and deploy Strata Logging Service in your product.In addition to using the Strata Logging Service, you can also use the Strata Cloud Manager Incidents and Alerts log viewer.- Launch the Strata Logging Service from the SCM console; log in to the SCM app from the Palo Alto Networks hub. In the lower left portion of the SCM interface, select the Tenant icon.Select Strata Logging Service.In the Strata Logging Service Dashboard, click Inventory. Your Cloud NGFW resource should appear.Select the Cloud NGFW tab:
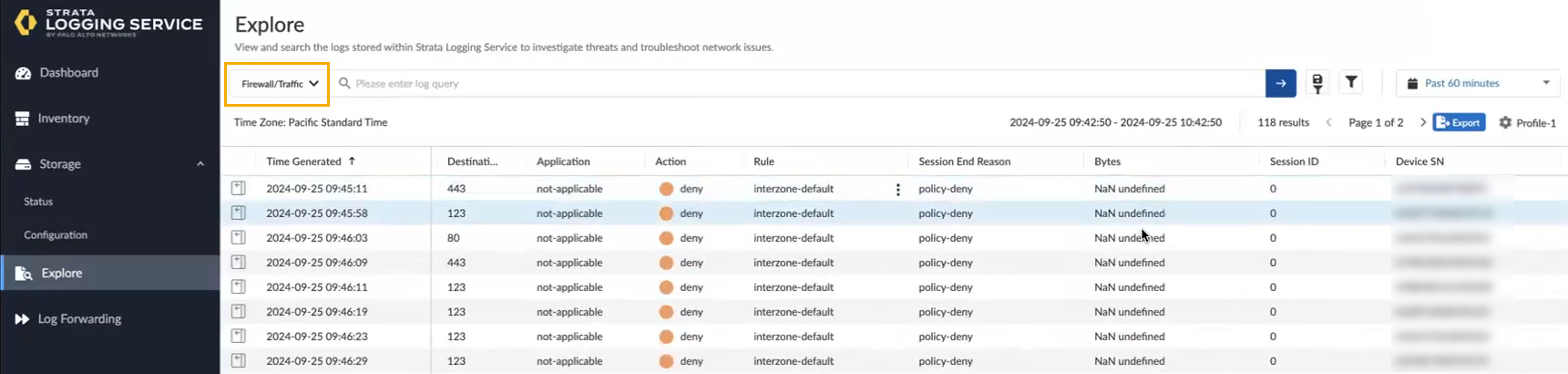
![]() Click Explore to view and interact with logs stored in your Strata Logging Service. The Query Builder along with time range preferences help you narrow down the specific logs that are of interest to you. You can view the log details and also export all log types to a compressed CSV file in GZ format.Select Firewall/Threat from the explore drop-down to select the log you want to view.You can filter logs for your Cloud NGFW resource. For example, enter sub_typevalue=WildFire® or wildFire®virus to filter for WildFire logs. For more information, see View Strata Logging Service Logs in Explore. You can also use the filter to query the log for a specific Cloud NGFW, for example, log source group ID = your Cloud NGFW name.
Click Explore to view and interact with logs stored in your Strata Logging Service. The Query Builder along with time range preferences help you narrow down the specific logs that are of interest to you. You can view the log details and also export all log types to a compressed CSV file in GZ format.Select Firewall/Threat from the explore drop-down to select the log you want to view.You can filter logs for your Cloud NGFW resource. For example, enter sub_typevalue=WildFire® or wildFire®virus to filter for WildFire logs. For more information, see View Strata Logging Service Logs in Explore. You can also use the filter to query the log for a specific Cloud NGFW, for example, log source group ID = your Cloud NGFW name.![]()