Enterprise DLP
Connect Gmail and Enterprise DLP
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Connect Gmail and Enterprise DLP
After you create you set up the Email DLP Host and create the transport rules, you
must connect Gmail and Enterprise Data Loss Prevention (E-DLP) to complete onboarding.
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Connect Gmail to Enterprise Data Loss Prevention (E-DLP) through SaaS Security on Strata Cloud Manager to complete the onboarding.
- Contact your email domain provider to update your SPF record to add the required Enterprise DLP service IP addresses.Add the IP addresses for the region where your email domain is hosted. You can update your SPF record with multiple regional IP addresses if you have email domains hosted in multiple regions.
- APAC35.186.151.226 and 34.87.43.120
- Australia35.197.179.113 and 35.244.122.65
- Europe34.141.90.172 and 34.107.47.119
- India34.93.185.212 and 35.200.159.173
- Japan34.84.8.170 and 35.221.111.27
- United Kingdom34.105.128.121 and 34.89.40.221
- United States34.168.197.200 and 34.83.143.116
Add a DNS TXT record to your email domain to validate email domain ownership when onboarding the domain to Email DLP.Enterprise DLP validates email domain ownership by requiring you to add a unique, system-generated token to your email domain's DNS TXT records. Enterprise DLP then performs a DNS lookup to verify this token, ensuring only authorized administrators can onboard email domains to Email DLP to prevent domain spoofing.You can add a DNS TXT record for a Google Workspace email domain or you can connect a DNS TXT record at any third party domain provider.Repeat this step for all email domains you plan to onboard to Email DLP.Enterprise DLP doesn't require domain validation if:- The parent domain of a subdomain was already verified.For example, you have already onboarded the parent domain acme.com and Enterprise DLP successfully validated it. In this case, validation of the support.acme.com subdomain isn't required.
- You removed and re-added an onboarded domain within the last 90 days. Enterprise DLP stores domain validation records for all onboarded domains for up to 90 days.For example, you onboarded the acme.com domain and Enterprise DLP successfully validated it. On August 1st, you removed the domain from Email DLP. On September 19th, you added it back to Email DLP. In this case, Enterprise DLP doesn't need to validate the domain again because the domain validation records for the acme.com domain are still stored.
Add an SMTP relay service entry to forward outbound emails to Enterprise DLP.- Log in to the Google Admin Console.Select AppsGoogle WorkspaceGmailRouting.For the SMTP relay service, Add Another Rule.In the Description, enter a descriptive name for the Enterprise DLP SMTP relay service.For Allowed Senders, verify Only addresses in my domains is selected.For Authentication, check (enable) Only accept mail from the specified IP addresses.Add a new SMTP relay serviceIn the Enter IP address/range field, enter the required IP addresses for the region where you host your email domain. You can add multiple sets of IP addresses if needed.
- APAC35.186.151.226 and 34.87.43.120
- Australia35.197.179.113 and 35.244.122.65
- Europe34.141.90.172 and 34.107.47.119
- India34.93.185.212 and 35.200.159.173
- Japan34.84.8.170 and 35.221.111.27
- United Kingdom34.105.128.121 and 34.89.40.221
- United States34.168.197.200 and 34.83.143.116
Verify that the SMTP relay service is Enabled.Save.Repeat this step to add both the required Enterprise DLP SMTP relay service IP addresses for the region where you host your email domain.For Encryption, check (enable) Require TLS Encryption.Save.Configure Gmail to enable the download of emails for investigative analysis when you review Email DLP incidents.- Log in to the Google Workspace Marketplace.Download the Email DLP app for your region.You can only download the Email DLP app for the region from which you're currently accessing the Google Workspace Marketplace.For example, if you access the Google Workspace Marketplace from California, click the United States link below to download the Email DLP app.Click Admin Install.You're prompted with a confirmation that you're about to install the Email DLP by Palo Alto Networks app. Click Continue.Select for which users you want to install the Email DLP app.
- Everyone at your organization—Select this option if you want to be able to download emails for everybody in your organization who generates an Email DLP incident.
- Certain groups or organizational units—Select this option if you want to be able to download emails for specific user groups and organizational units when they generate an Email DLP incident.For example, you have user groups Group1, Group2, and Group3 where your CEO and other executives are part of Group3. You don't want to give your security administrators the ability to download emails sent by the CEO and other executives. In this case, you would select the Certain groups or organizational units option and add Group1 and Group2 but not Group3.
Agree to the app Terms and Conditions.(Certain groups or organizational units) Select the user groups and organizational you want to install the app for.Click Finish.A notification is displayed notifying you the Email DLP by Palo Alto Networks app successfully installed.Click Done.Enter Email DLP in the search bar and select the Email DLP app for your region. Verify that the app tile displays InstalledSet Up a Proofpoint Server for Email Encryption.This is required to encrypt emails inspected by Enterprise DLP that match your encryption Email DLP policy rule.Create the Gmail transport rules, and create the Email DLP Policy.Palo Alto Networks recommends setting Email DLP Host, transport rules, and Email DLP policy rules to ensure enforcements begins as soon as you successfully connect Gmail to Enterprise DLP.- Setting up a routing to the Email DLP Host enables Gmail to forward emails to Enterprise DLP and for inspection and verdict rendering to prevent exfiltration of sensitive data.
- Transport rules instruct Gmail to forward emails to Enterprise DLP and establish the actions Gmail takes based on verdicts rendered by Enterprise DLP.A transport rule isn't required for emails that match your Email DLP policy where you set the action to Monitor. In this case, the x-panw-action - monitor email header is added, a DLP incident is created, and the email continues to its intended recipient.
- The Email DLP policy specifies the incident severity and the action Enterprise DLP takes when matching traffic is inspected and sensitive data is detected.
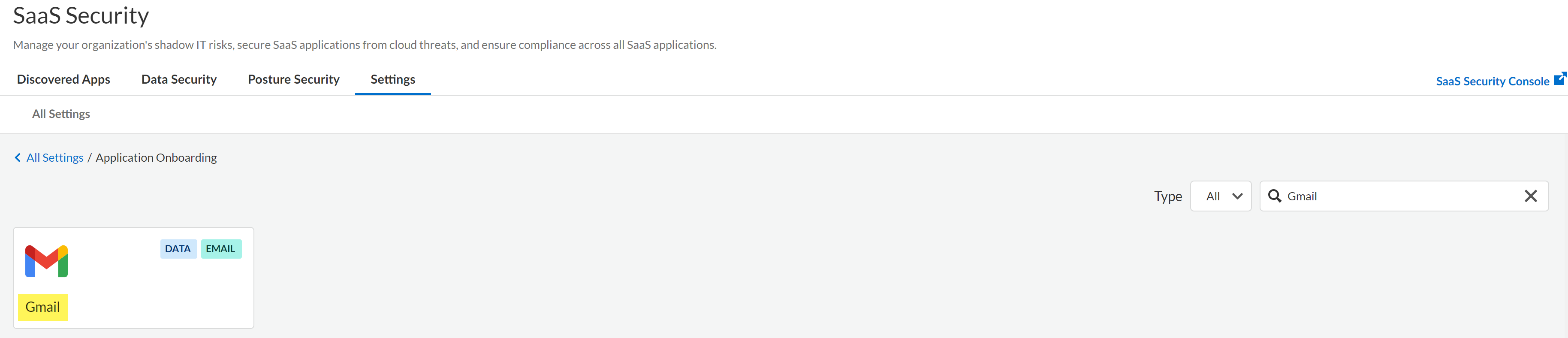
Log in to Strata Cloud Manager.Select ConfigurationSaaS SecuritySettingsApps Onboarding.Add the Gmail app to SaaS Security.- Search for Gmail and click the Gmail app.
![]() Add the Gmail app to SaaS Security.In the Email DLP Instance, click Add Instance.Configure one or more email domains.Enterprise DLP requires adding one or more email domains and relay hosts to ensure Enterprise DLP can successfully forward inspect emails back to Microsoft Exchange.
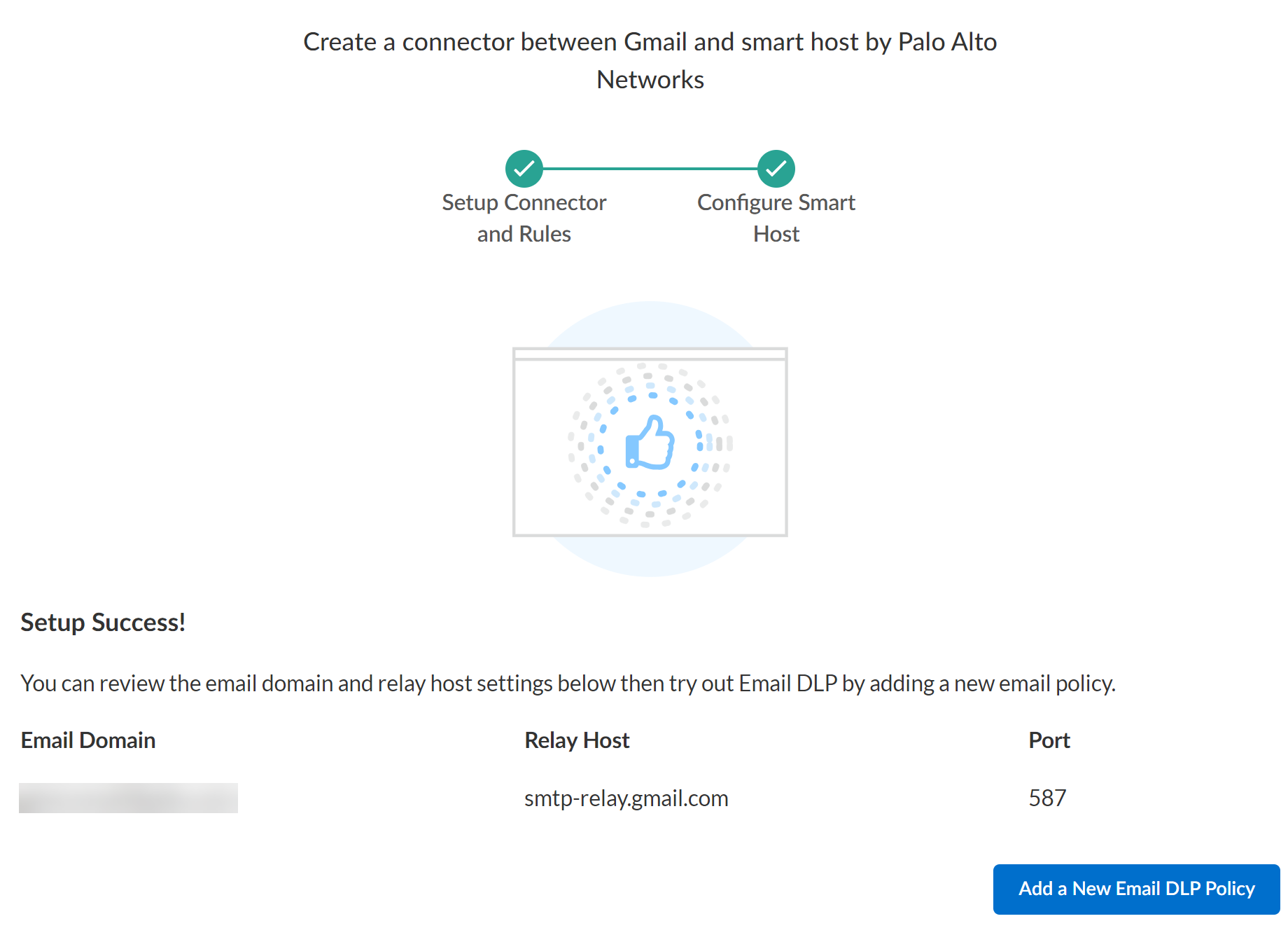
Add the Gmail app to SaaS Security.In the Email DLP Instance, click Add Instance.Configure one or more email domains.Enterprise DLP requires adding one or more email domains and relay hosts to ensure Enterprise DLP can successfully forward inspect emails back to Microsoft Exchange.- (Optional) Enable Custom Routing.If you have a complex multivendor email security chain, enabling custom routing allows Email DLP to scan emails within complex multivendor email security chains while maintaining your existing infrastructure. Custom routing also helps prevent sender spoofing through IP validation.Enter an Email Domain, its corresponding Relay Host, and the networking Port.Obtain Your Microsoft Exchange Domain and Relay Host if you don't have the Microsoft Exchange email domain and relay host immediately available.(Custom Routing) If you enabled custom routing, enter the relay domain of the next hop server.(Optional) Click Add Domain any additional email domains.Connect.(Custom Routing only) For the Source IP Allow List, enter a trusted SMTP traffic source forwarding emails to Enterprise DLP.Enterprise DLP supports static IPv4 addresses and Classless Inter-Domain Routing (CIDR) IP ranges. It takes up to 2 minutes for Email DLP to add domains and IP addresses to the email inspection flow when connecting Email DLP for the first time or editing an existing configuration.The Source IP Allow List restricts Enterprise DLP email acceptance to only those emails originating from your specified IP addresses or address ranges. This prevents spoofing attacks by rejecting emails that claim to be from your organization's domain but come from unauthorized mail servers.Click Add Source IP to add more trusted STMP traffic sources. Email DLP supports up to 20 unique IP addresses and CIDR ranges.Gmail is now successfully connected and onboarded.
![]()
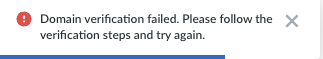
- Domain Validation ErrorThis error message appears if the DNS TXT record for your email domain is missing or incorrect
![]()
Configure the Email DLP settings.- Edit the snippet settings to configure if and how Enterprise DLP stores and masks snippets of sensitive data that match your data pattern match criteria.
- Edit the policy evaluation timeout settings to configure what Enterprise DLP does when Email DLP policy evaluation exceeds the configured timeout.
- Configure evidence storage to save evidence for investigative analysis.