Enterprise DLP
Strata Cloud Manager
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
-
- About Enterprise DLP
- What’s Supported with Enterprise DLP?
- Data Patterns, Document Types, and Data Profiles
- Enable Role Based Access
- Edit the Cloud Content Settings
- Edit the Enterprise DLP Data Filtering Settings
- Edit the Enterprise DLP Snippet Settings
- Configure Syslog Forwarding for Enterprise DLP Incidents
- Request a New Feature
-
-
- Enable Existing Data Patterns and Filtering Profiles
- Modify a DLP Rule on Strata Cloud Manager
- Create a SaaS Security Policy Recommendation to Leverage Enterprise DLP
- Reduce False Positive Detections
- Data Dictionaries
- Recommendations for Security Policy Rules
- Enterprise DLP Migrator
-
-
-
- Driver License - Australia
- Driver License - Austria
- Driver License - Belgium
- Driver License - Brazil
- Driver License - Bulgaria
- Driver License - Canada
- Driver License - China
- Driver License - Croatia
- Driver License - Cyprus
- Driver License - Czech Republic
- Driver License - Denmark
- Driver License - Estonia
- Driver License - Finland
- Driver License - France
- Driver License - Germany
- Driver License - Greece
- Driver License - Hungary
- Driver License - Iceland
- Driver License - Ireland
- Driver License - Italy
- Driver License - Japan
- Driver License - Latvia
- Driver License - Liechtenstein
- Driver License - Lithuania
- Driver License - Luxembourg
- Driver License - Malta
- Driver License - Netherlands
- Driver License - New Zealand
- Driver License - Norway
- Driver License - Poland
- Driver License - Portugal
- Driver License - Romania
- Driver License - Slovakia
- Driver License - Slovenia
- Driver License - South Africa
- Driver License - South Korea
- Driver License - Spain
- Driver License - Sweden
- Driver License - Switzerland
- Driver License - Taiwan
- Driver License - Turkey
- Driver License - UK
- Driver License - US
- Driver License - US - AK
- Driver License - US - AL
- Driver License - US - AR
- Driver License - US - AZ
- Driver License - US - CA
- Driver License - US - CO
- Driver License - US - CT
- Driver License - US - DC
- Driver License - US - DE
- Driver License - US - FL
- Driver License - US - GA
- Driver License - US - HI
- Driver License - US - IA
- Driver License - US - ID
- Driver License - US - IL
- Driver License - US - IN
- Driver License - US - KS
- Driver License - US - KY
- Driver License - US - LA
- Driver License - US - MA
- Driver License - US - ME
- Driver License - US - MI
- Driver License - US - MN
- Driver License - US - MO
- Driver License - US - MS
- Driver License - US - MT
- Driver License - US - NC
- Driver License - US - ND
- Driver License - US - NE
- Driver License - US - NH
- Driver License - US - NM
- Driver License - US - NV
- Driver License - US - NY
- Driver License - US - OH
- Driver License - US - OK
- Driver License - US - OR
- Driver License - US - PA
- Driver License - US - RI
- Driver License - US - SC
- Driver License - US - SD
- Driver License - US - TN
- Driver License - US - TX
- Driver License - US - UT
- Driver License - US - VA
- Driver License - US - VT
- Driver License - US - WA
- Driver License - US - WI
- Driver License - US - WV
- Driver License - US - WY
- National ID - Albania
- National Id - Argentina ID
- National ID - Australia
- National Id - Austria - Central Register of Residents
- National Id - Austria Social Security Card - e-card
- National ID - Bahrain
- National Id - Belgium - Citizen Service Number - BSN
- National Id - Belgium - National Registration Number
- National ID - Bosnia and Herzegovina
- National ID - Brazil
- National Id - Brazil - CNPJ
- National Id - Brazil - CPF
- National Id - Bulgaria - Uniform Civil Number
- National Id - Canada - Social Insurance Number - SIN
- National ID - Chile
- National Id - China ID
- National Id - Colombia National ID
- National ID - Costa Rica
- National Id - Croatia - Personal Identification Number
- National ID - Cuba
- National Id - Cyprus - Identity Card
- National Id - Czech - Birth Number
- National Id - Czech - National eID Card
- National Id - Denmark - CPR Number
- National ID - Dominican Republic
- National ID - Ecuador
- National ID - Egypt
- National Id - Estonia - Personal Identification Code
- National Id - Finland - Personal Identity Code - HETU
- National Id - France - INSEE
- National Id - France - Social Security Number - NIR
- National Id - Germany
- National Id - Greece
- National Id - Hong Kong ID
- National Id - Hungary - Personal Identification Number
- National Id - Iceland
- National ID - India
- National ID - Indonesia
- National ID - Iran
- National Id - Ireland - Personal Public Service Number - PPSN
- National ID - Israel
- National Id - Italy - Fiscal Code Card - Codice Fiscale
- National Id - Japan Corporate Number
- National Id - Japan My Number
- National ID - Kazakhstan
- National ID - Kuwait
- National Id - Latvia - Personal Public Service Number - PPSN
- National Id - Liechtenstein
- National Id - Lithuania
- National Id - Luxembourg
- National Id - Malaysia National ID
- National Id - Malta
- National ID - Mexico
- National ID - Moldova
- National ID - Montenegro
- National Id - Netherlands - Citizen Service Number - BSN
- National ID - North Macedonia
- National Id - Norway - Identification Number - Fødselsnummer
- National ID - Pakistan
- National ID - Paraguay
- National ID - Peru
- National ID - Philippines
- National Id - Poland
- National Id - Portugal
- National Id - Romania - Identity Card - CNP
- National ID - Russia
- National ID - Serbia
- National Id - Singapore NRIC
- National Id - Slovakia
- National Id - Slovenia
- National ID - South Africa
- National ID - South Korea
- National Id - Spain - National Identity Document - Documento Nacional de Identidad
- National ID - Sri Lanka
- National Id - Sweden - Personal Identity Number
- National ID - Switzerland
- National Id - Taiwan ID
- National Id - Thailand ID
- National Id - Turkey Identification Number
- National Id - UAE Emirates ID
- National Id - UK National Insurance Number - NINO
- National ID - Uruguay
- National Id - US Social Security Number - SSN
- National ID - Venezuela
- Passport - Australia
- Passport - Austria
- Passport - Belgium
- Passport - Brazil
- Passport - Bulgaria
- Passport - Canada
- Passport - Croatia
- Passport - Cyprus
- Passport - Czech Republic
- Passport - Denmark
- Passport - Estonia
- Passport - Finland
- Passport - France
- Passport - Germany
- Passport - Greece
- Passport - Hungary
- Passport - Iceland
- Passport - Ireland
- Passport - Italy
- Passport - Latvia
- Passport - Liechtenstein
- Passport - Lithuania
- Passport - Luxembourg
- Passport - Malta
- Passport - Netherlands
- Passport - New Zealand
- Passport - Norway
- Passport Number - China
- Passport Number - Singapore
- Passport Number - South Africa
- Passport number - South Korea
- Passport number - Taiwan
- Passport - Poland
- Passport - Portugal
- Passport - Romania
- Passport - Slovakia
- Passport - Slovenia
- Passport - Spain
- Passport - Sweden
- Passport - Switzerland
- Passport - Turkey
- Passport - UK
- Passport - US
- Tax Id - Australia
- Tax Id - Austria
- Tax Id - Belgium
- Tax Id - Brazil
- Tax Id - Bulgaria
- Tax ID - Canada
- Tax ID - China
- Tax ID - Costa Rica
- Tax Id - Cyprus
- Tax Id - Czech Republic
- Tax Id - Denmark
- Tax ID - Dominican Republic
- Tax Id - Estonia
- Tax Id - Finland
- Tax Id - France
- Tax Id - Germany
- Tax Id - Greece
- Tax Id - Hungary
- Tax Id - Iceland
- Tax Id - India - PAN
- Tax Id - Ireland
- Tax Id - Italy
- Tax ID - Japan
- Tax Id - Latvia
- Tax Id - Liechtenstein
- Tax Id - Lithuania
- Tax Id - Luxembourg
- Tax Id - Malta
- Tax Id - Netherlands
- Tax Id - New Zealand
- Tax Id - Norway
- Tax Id - Poland
- Tax Id - Portugal
- Tax Id - Romania
- Tax Id - Slovakia
- Tax Id - Slovenia
- Tax ID - South Africa
- Tax ID - South Korea
- Tax Id - Spain
- Tax Id - Sweden
- Tax Id - Switzerland
- Tax ID - Taiwan
- Tax Id - Turkey
- Tax Id - UK - UTR
- Tax Id - US - TIN
-
-
-
-
- March 2025
- February 2025
- January 2025
- December 2024
- November 2024
- October 2024
- September 2024
- August 2024
- July 2024
- June 2024
- April 2024
- March 2024
- January 2024
- December 2023
- November 2023
- October 2023
- August 2023
- July 2023
- June 2023
- May 2023
- March 2023
- February 2023
- January 2023
- November 2022
- October 2022
- August 2022
- July 2022
- June 2022
- May 2022
- April 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- September 2021
- July 2021
- New Features in Enterprise DLP Plugin 5.0
- New Features in Enterprise DLP Plugin 4.0
- New Features in Enterprise DLP Plugin 3.0
- New Features in Enterprise DLP Plugin 1.0
-
- Known Issues in the Enterprise DLP Cloud Service
- Known Issues in Endpoint DLP
-
- Known Issues in Enterprise DLP Plugin 5.0.6
- Known Issues in Enterprise DLP Plugin 5.0.5
- Known Issues in Enterprise DLP Plugin 5.0.4
- Known Issues in Enterprise DLP Plugin 5.0.3
- Known Issues in Enterprise DLP Plugin 5.0.2
- Known Issues in Enterprise DLP Plugin 5.0.1
- Known Issues in Enterprise DLP Plugin 5.0.0
-
- Known Issues in Enterprise DLP Plugin 3.0.10
- Known Issues in Enterprise DLP Plugin 3.0.9
- Known Issues in Enterprise DLP Plugin 3.0.8
- Known Issues in Enterprise DLP Plugin 3.0.7
- Known Issues in Enterprise DLP Plugin 3.0.6
- Known Issues in Enterprise DLP Plugin 3.0.5
- Known Issues in Enterprise DLP Plugin 3.0.4
- Known Issues in Enterprise DLP Plugin 3.0.3
- Known Issues in Enterprise DLP Plugin 3.0.2
- Known Issues in Enterprise DLP Plugin 3.0.1
- Known Issues in Enterprise DLP Plugin 3.0.0
-
- Known Issues in Enterprise DLP Plugin 1.0.8
- Known Issues in Enterprise DLP Plugin 1.0.7
- Known Issues in Enterprise DLP Plugin 1.0.6
- Known Issues in Enterprise DLP Plugin 1.0.5
- Known Issues in Enterprise DLP Plugin 1.0.4
- Known Issues in Enterprise DLP Plugin 1.0.3
- Known Issues in Enterprise DLP Plugin 1.0.2
- Known Issues in Enterprise DLP Plugin 1.0.1
- Enterprise DLP Limitations
- Changes to Default Behavior
-
Strata Cloud Manager
View the log details for traffic that matches your Enterprise Data Loss Prevention (E-DLP) data profiles
on Strata Cloud Manager.
- Log in to Strata Cloud Manager.
- Select ManageConfigurationData Loss PreventionDLP Incidents.
- Select a Scan Date and Region to filter the DLP Incidents.Enterprise DLP Incidents are generated in the Region where the Public Cloud Server is located.For Prisma Access (Managed by Strata Cloud Manager) and NGFW (Managed by Strata Cloud Manager), Enterprise DLP automatically resolves to the closest Public Cloud Server to where the inspected traffic originated.When a new Public Cloud Server is introduced, Enterprise DLP automatically resolve to it if it’s closer to where the inspected traffic originated.This might mean that new DLP Incidents generated after the release of a new Public Cloud Server are generated in a different Region.
- Review the DLP Incidents summary information to help focus your incident investigation.These lists are updated hourly.
- Top Data Profiles to Investigate—Lists up to seven data profiles with the highest number of incidents in descending order.
- Top Sources to Investigate—Lists up to seven source IP addresses and Fully Qualified Domain Names (FQDN) with the highest number of incidents in descending order.
- Sensitive Files by Action—Lists the number of incidents based on the Action taken by Enterprise DLP in descending order.
- Review the Incidents and click the File name to review detailed information for a specific incident.You can Add New Filter to filter the DLP incidents by Action, Channel, Data Profile or Response Status to search for a specific incident you want to review.
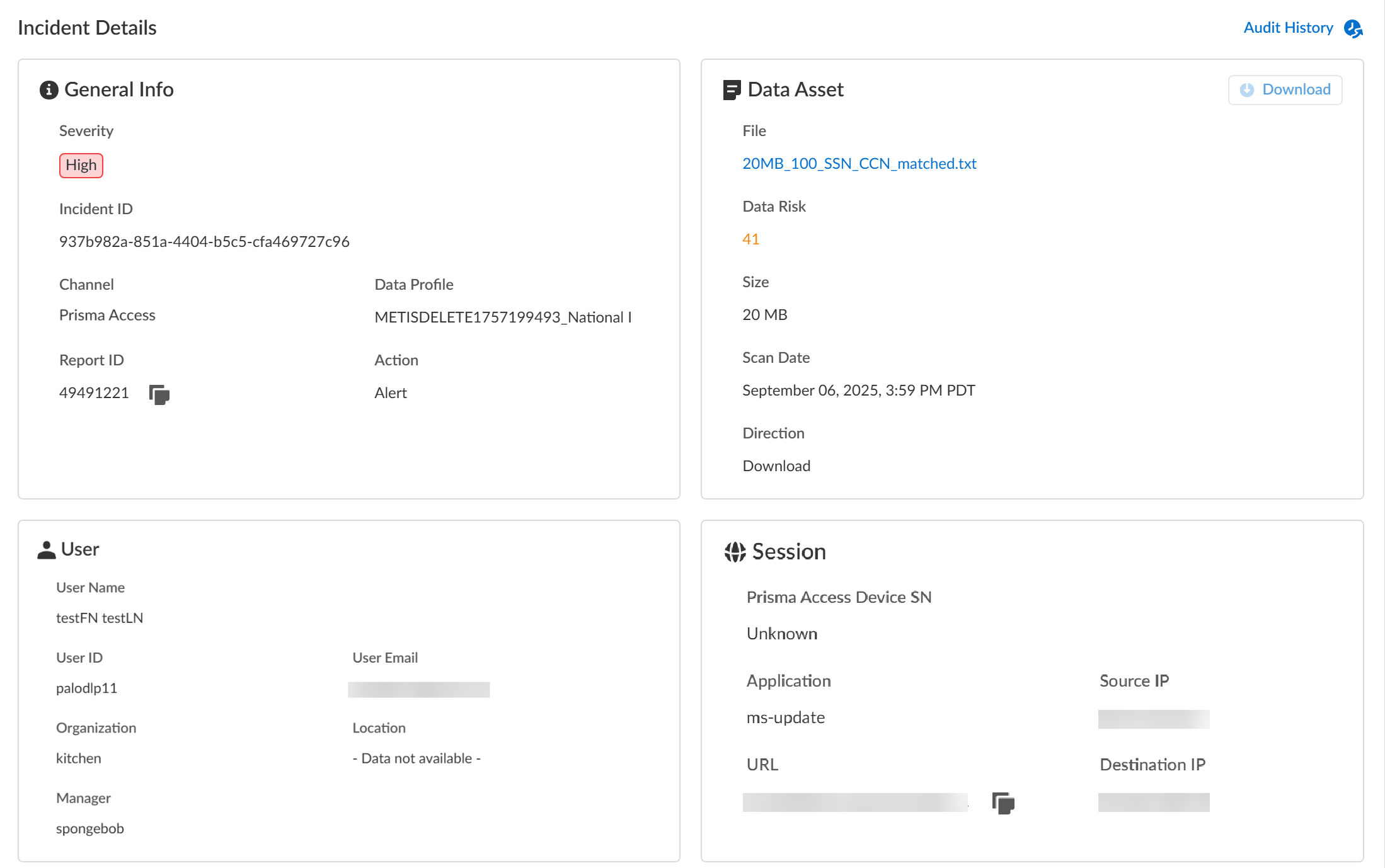
- Review the Incident Details to review specific file upload details.Make note of the Report ID for the DLP incident if you haven’t already done so. The Report ID is used to view additional Traffic log details regarding the DLP incident.
- InfoThe Info panel displays general information about the DLP incident.
- Channel/Source—The security endpoint using Enterprise DLP through which the incident occurred.
- Incident ID—Unique ID for the DLP incident.
- Report ID—Unique ID used to view additional Traffic log details regarding the DLP incident.
- Action—The action Enterprise DLP took on the traffic that matched your DLP rule.
- Data Profile—Data profile that traffic matched against that generated the incident.
- Assign To—Select an admin to review and manage the DLP incident.
- Status—Select the resolution status of the DLP incident.
- Priority—Specify the DLP incident priority. You can select P1, P2, P3, P4, or P5.
- Data
- Asset—Name of the file containing sensitive data that generated the incident. For non-file inspection, the asset name is http-post-put.
- Type—File type for the file that generated the incident. For non-file inspection, the type is non-file.
- Direction—Indicates whether the matched traffic was a Download or an Upload when the incident occurred.
- Scan Date—Date and time the matched traffic was scanned and the DLP incident was generated.
- UserUser data requires integration with Cloud Identity Engine (CIE) to display. The User data displayed correspond to Palo Alto Networks Attributes that correlate to specific directory provider fields in CIE.
- User ID—ID of the user that generated the DLP incident.The User ID field does not require CIE integration. However, the corresponding Palo Alto Networks Attribute is User Principal Name.
- Role—Role of the user that generated the DLP incident.Corresponding Palo Alto Networks Attribute is Title.
- Organization—Organization the user that generated the DLP incident is associated with.Corresponding Palo Alto Networks Attribute is Department.
- Location—Location of the user that generated the DLP incident.Corresponding Palo Alto Networks Attribute is Location.
- Manager—Manager of the user that generated the DLP incident.Corresponding Palo Alto Networks Attribute is Manager.
- Session
- Device—Serial number of the firewall that blocked a file or generated an alert.
- Destination IP—Target upload or download IP address of the application or user.
- App—App ID for the target application.
- URL—Fully Qualified Domain Name (FQDN) of the target application or user.
- AnnotationsThe Annotations sections allows you to add notes and details regarding the DLP incident. Save any annotations regarding the DLP incident so other administrators can view.
Expand allCollapse all
- Review the Matches within Data Profiles to review snippets of matching traffic and the data patterns that matched the traffic to better understand what data was detected.For nested data profiles, Enterprise DLP displays the name of the nested data profile and not the specific data profile containing the match criteria that matched inspected traffic. For example, you create a DataProfile, with the nested profiles Profile1, Profile2, and Profile3. Enterprise DLP inspects traffic that match Profile2 and blocks it. In this scenario, the Matches within Data Profile displays DataProfile.Additionally, you can filter the Matches within Data Profile for a nested data profile to display traffic matches against specific associated data profiles.


- Review the file log to learn about the traffic data for the DLP incident.
- Select Incidents & AlertsLog Viewer.
- From the Firewall drop-down, select File.
- Filter to view the file log for the DLP incident using the Report ID.Report ID = <report-id>
- Review the file log to learn more about the traffic data for the DLP incident.