Enterprise DLP
Create Microsoft Exchange Transport Rules
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Create Microsoft Exchange Transport Rules
Create Microsoft Exchange transports rule to forward emails to Enterprise Data Loss Prevention (E-DLP) for inspection, and to specify what actions Microsoft Exchange takes based on the Enterprise DLP verdicts.
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Create Microsoft Exchange email transport rules to forward emails from Microsoft
Exchange to the Enterprise Data Loss Prevention (E-DLP) for inspection to prevent exfiltration of
sensitive data. Additionally, you must create transport rules to specify the actions
Microsoft Exchange takes based on the verdicts rendered by Enterprise DLP. The
following transport rules are required:
- Email TransportRequired to forward all outbound emails from Microsoft Exchange to the Enterprise Data Loss Prevention (E-DLP) for inline email inspection and verdict rendering. The email transport rule is required in all cases regardless of the verdict Enterprise DLP renders.Enterprise DLP adds x-panw-inspected: true and x-panw-action: monitor to the email header for all forwarded and inspected emails. If an outbound email already includes these two headers, it will not be forwarded to Enterprise DLP again. If Enterprise DLP already inspected and rendered a verdict, Microsoft Exchange automatically takes the action specified in the quarantine, or block transport rule.Enterprise DLP adds one of the following X-PANW-Processing-Status email headers based on the inspection status.
- X-PANW-Processing-Status: completed—Enterprise DLP successfully inspected the forwarded email.
- X-PANW-Processing-Status: limited—Enterprise DLP couldn't finish inspecting the forwarded email due to the Email DLP Max Timeout setting. This setting defines the amount of time allowed for Enterprise DLP to inspect the email.
- X-PANW-Processing-Status: failed—Enterprise DLP failed to inspect the forwarded email due to an error or unavailability of a dependent service. For example, the Enterprise DLP scanning service or Cloud Identity Engine being unavailable or returning an error.
These are informational headers designed to provide you with essential details regarding the Enterprise DLP inspection status and outcome for each forwarded email to facilitating better governance and operational transparency. If you write custom transport rules based on these headers, be sure they don't interfere with the transport rules required for Email DLP functionality. - Hosted QuarantineInstructs Microsoft Exchange to quarantine and forward the email to the spam quarantine mailbox hosted by Microsoft Exchange when Enterprise Data Loss Prevention (E-DLP) returns a Quarantine verdict for an email that contains sensitive data.Enterprise DLP adds x-panw-action: quarantine to the email header for inspected emails. The email is transported back to Microsoft Exchange and forwarded to the hosted quarantine spam inbox so an email administrator can review the email contents and decide whether to approve or block the email. Any future emails with this header already included will not be forwarded to Enterprise DLP again. Instead, Microsoft Exchange will take the action specified in the quarantine transport rule.
- Admin ApprovalInstructs Microsoft Exchange to forward the email to the specified email administrator when Enterprise Data Loss Prevention (E-DLP) returns a Forward email for approval admin verdict for an email that contains sensitive data.Enterprise DLP adds x-panw-action: fwd_to_admin to the email header for inspected emails. The email is transported back to Microsoft Exchange so an email administrator can review the email contents and decide whether to approve or block the email. Any future emails with this header already included will not be forwarded to Enterprise DLP again. Instead, Microsoft Exchange will take the action specified in the transport rule.
- Manager ApprovalInstructs Microsoft Exchange to forward the email to the sender's manager when Enterprise Data Loss Prevention (E-DLP) returns a Forward email for approval by end user's manager verdict for an email that contains sensitive data.Enterprise DLP adds x-panw-action: fwd_to_manager to the email header for inspected emails. The email is transported back to Microsoft Exchange so a manager can review the email contents and decide whether to approve or block the email. Any future emails with this header already included will not be forwarded to Enterprise DLP again. Instead, Microsoft Exchange will take the action specified in the transport rule.
- EncryptInstructs Microsoft Exchange on the action to take when Enterprise DLP returns a Encrypt verdict for an email that contains sensitive data.Enterprise DLP adds x-panw-action: encrypt to the email header for inspected emails. The email is either transported back to Microsoft Exchange or to your Proofpoint server for encryption based on the encryption settings you configure in the transport rule. Any future emails with this header already included will not be forwarded to Enterprise DLP again. Instead, Microsoft Exchange will take the action specified in the encrypt transport rule.Forwarding an email to both Microsoft Exchange and your Proofpoint server for encryption is not supported.
- BlockInstructs Microsoft Exchange on the action to take when Enterprise DLP returns a Block verdict for an email that contains sensitive data.Enterprise DLP adds x-panw-action: block to the email header for all inspected emails. Any future emails with this header already included will not be forwarded to Enterprise DLP for inspection. Instead, Microsoft Exchange takes the action specified in the Block transport rule.
(Custom Routing only) If using custom routing to forward
emails existing email infrastructure like Proofpoint or Mimecast, you must create
all the required Email DLP transport rules in the respective service's management
interface.
Create a Microsoft Exchange Email Transport Rule
Create a Microsoft Exchange email transport rule to forward traffic to the Enterprise Data Loss Prevention (E-DLP)cloud service for inline email inspection.
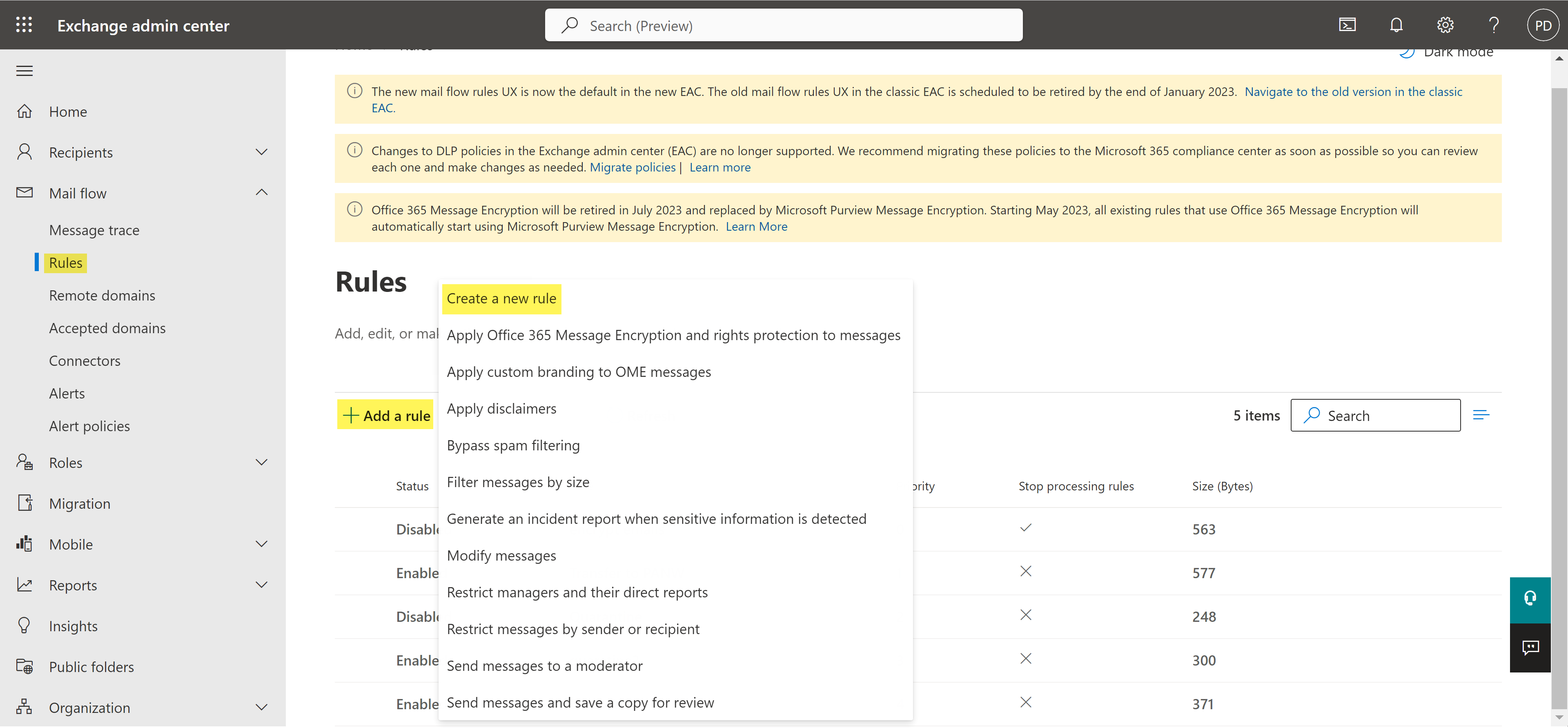
- Log in to the Microsoft Exchange Admin Center.Create the outbound and inbound connectors.Skip this step if you have already created both the outbound and inbound connectors.Select Mail flowRulesAdd a ruleCreate a new rule to create a new email transport rule.
![]() Configure the email transport rule conditions.
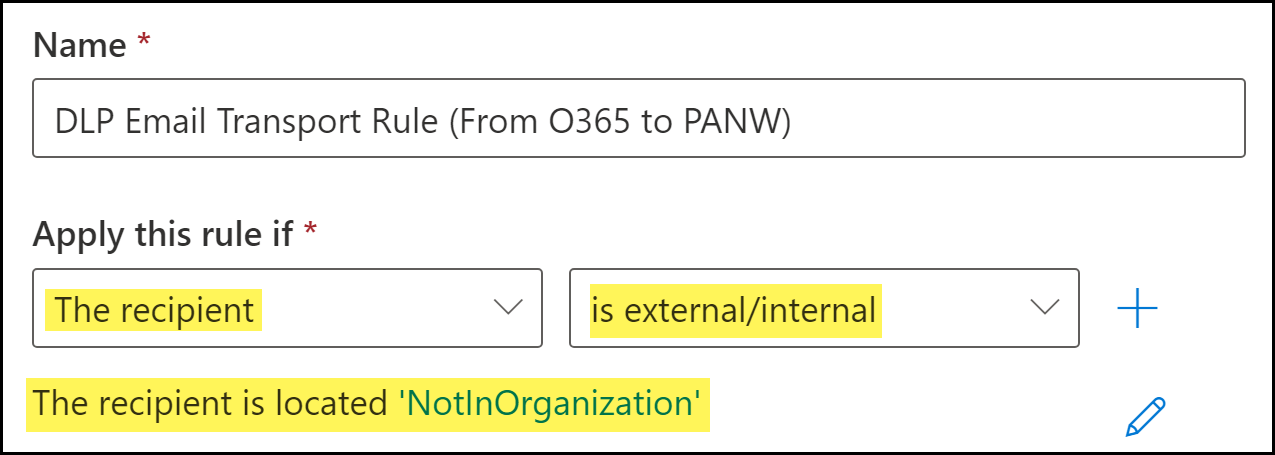
Configure the email transport rule conditions.- Enter a Name for the email transport rule.Specify the email recipient.This instructs Microsoft Exchange to forward the email to Enterprise DLP before it leaves your network when the email recipient is outside your organization.
- For Apply this rule if, select The recipient.
- For the recipient, select is external/internal. When prompted to select the recipient location, select Outside the organizationClick Save to continue.
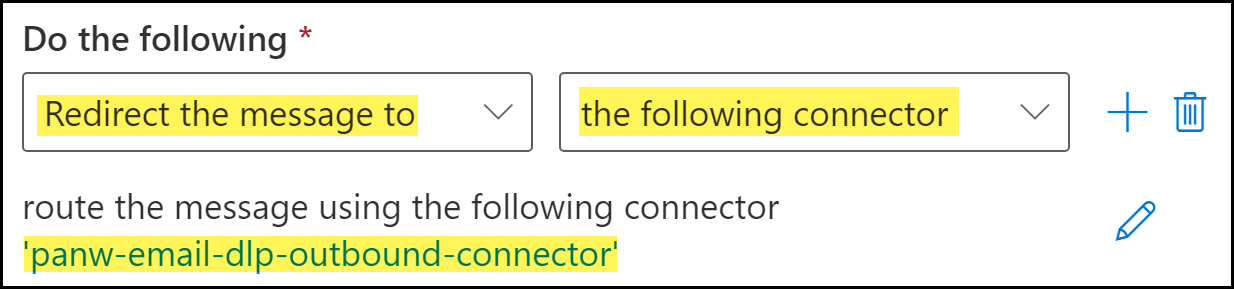
![]() Specify Microsoft Exchange Connector you created as the transport target for email inspection.
Specify Microsoft Exchange Connector you created as the transport target for email inspection.- For Do the following, select redirect the message to.
- For the transport target, select the following connector. When prompted, select the outbound connector.Click Save to continue.
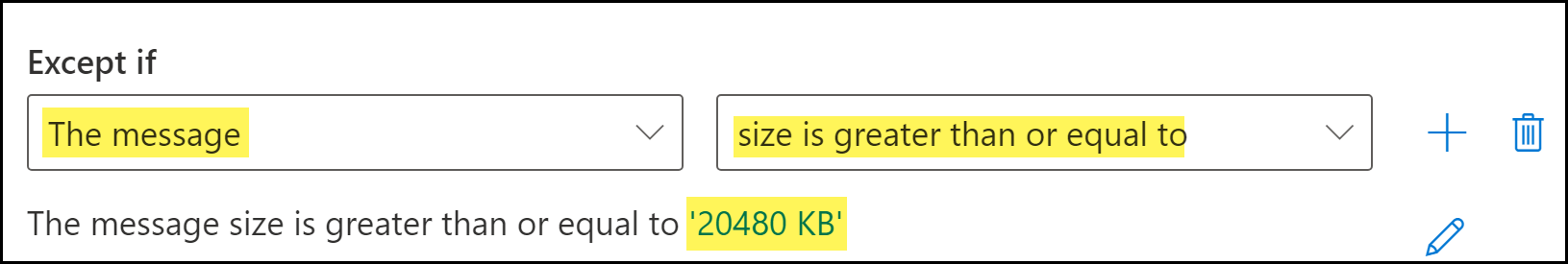
![]() Add an exception for emails that exceed the maximum message size supported by Enterprise DLP.Enterprise DLP supports inspection of email messages up to 20 MB in size. Larger email messages are not supported and should not be forwarded to Enterprise DLP.
Add an exception for emails that exceed the maximum message size supported by Enterprise DLP.Enterprise DLP supports inspection of email messages up to 20 MB in size. Larger email messages are not supported and should not be forwarded to Enterprise DLP.- In the s Except If field, select The message.
- Select size is greater than or equal to. When prompted, enter the following maximum-supported message size KB:20480
![]()
- Add an exception for emails that were already inspected by Enterprise DLP.
- In the Except if condition, click the add symbol () to add a new Or condition.
![]()
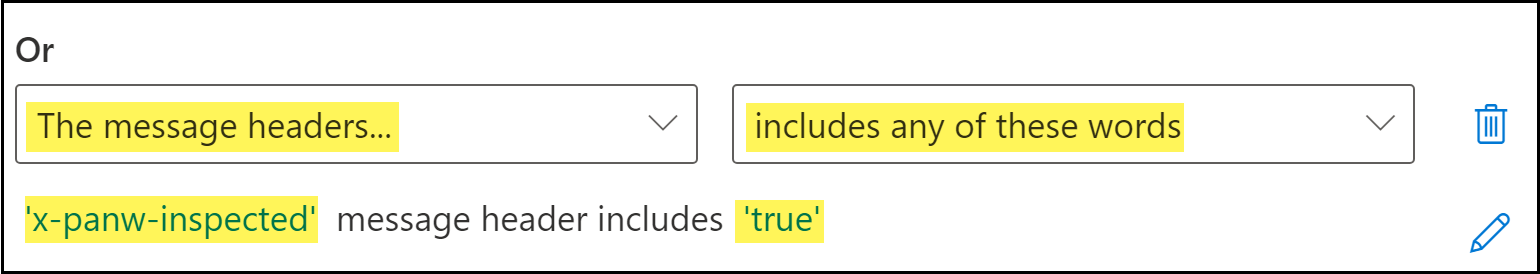
- Select the The message headers condition.
- For the Or condition action, select matches any of these words.
- Click Enter text to set the message header to x-panw-inspected.
- Click Enter words and enter true.Click Add and select the word you added. Click Save to continue.
![]() Add an exception for emails where the sender is blank or empty.
Add an exception for emails where the sender is blank or empty.- In the Except if condition, click the add symbol () to add a new Or condition.
![]()
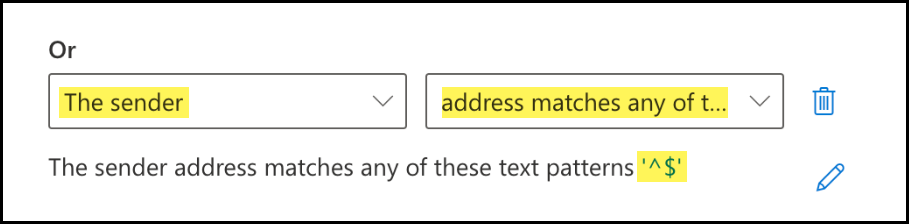
- Select the The sender condition.
- For the Or condition action, select address matches any of these text patterns.
- Click Enter text to configure the text pattern as ^$.
![]() Click Next to continue.Configure the email transport rule settings.
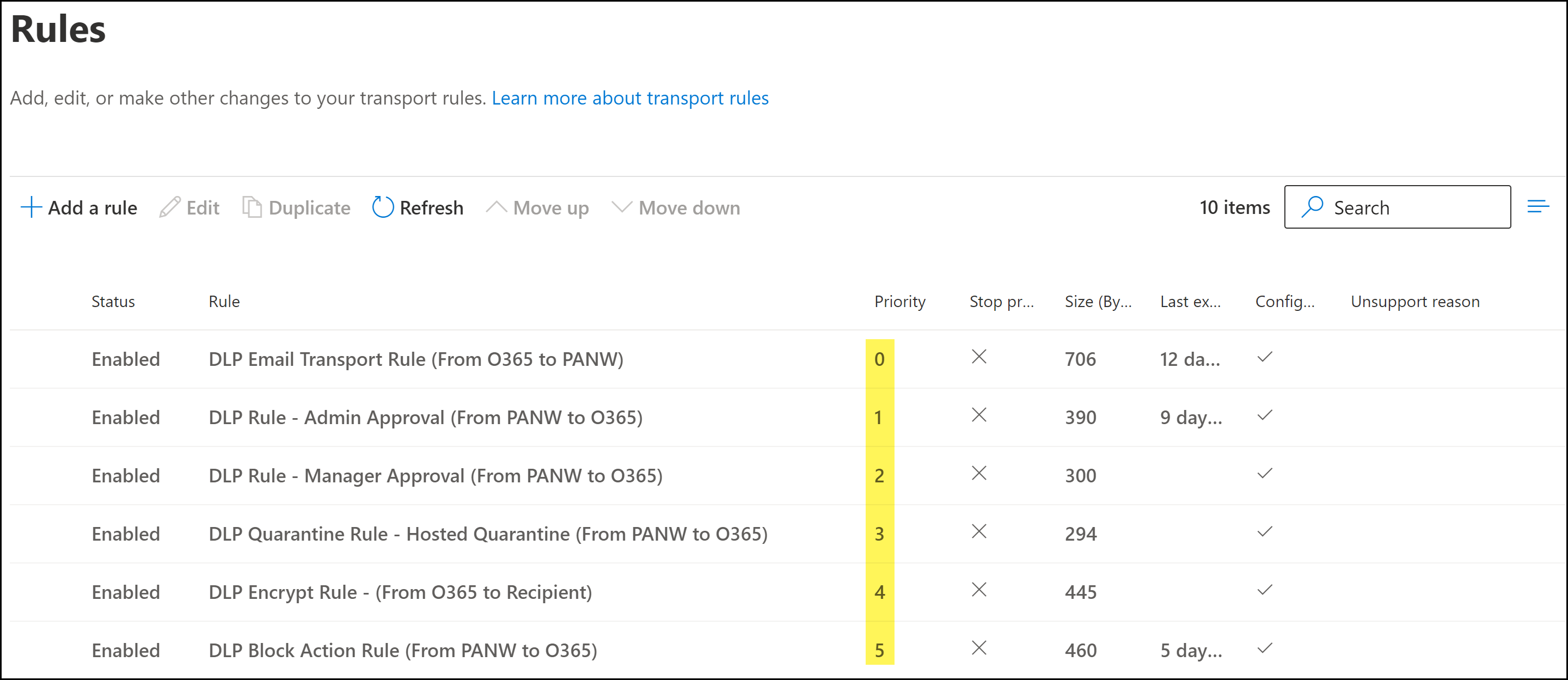
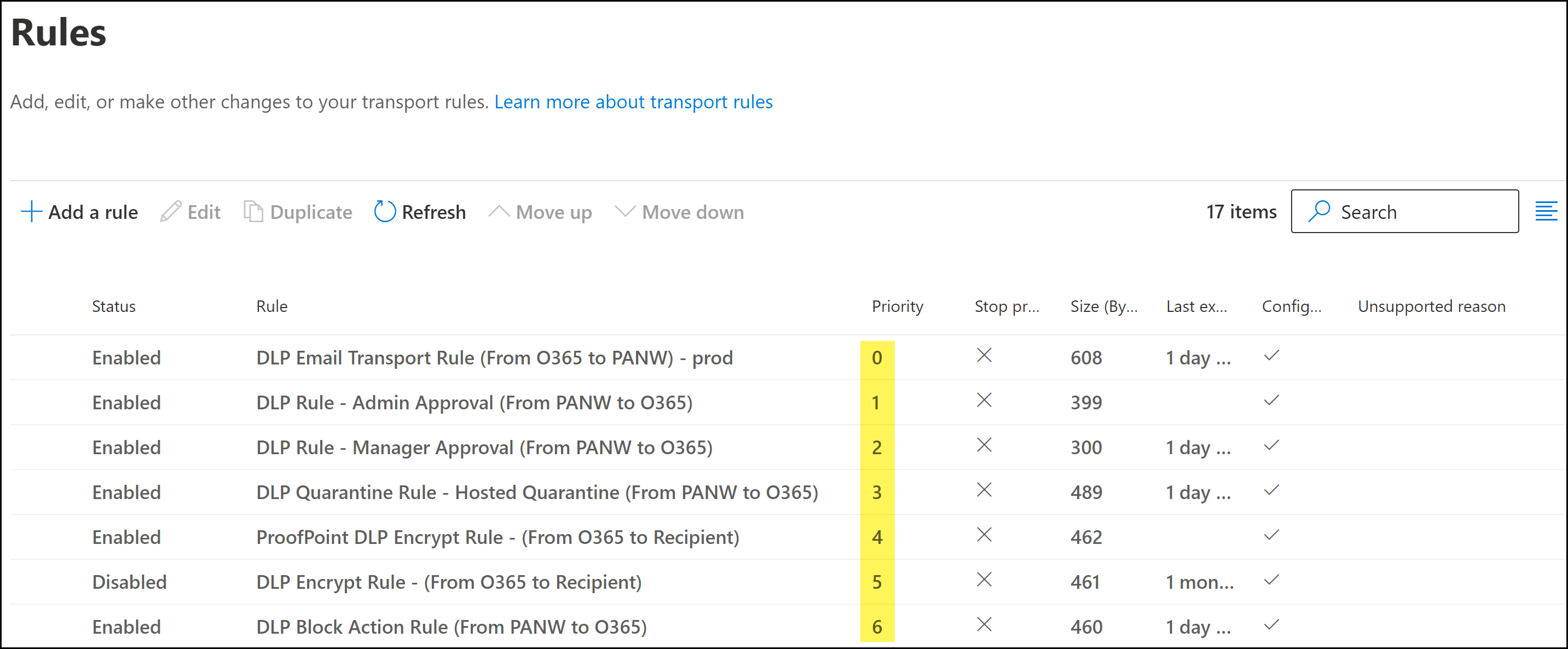
Click Next to continue.Configure the email transport rule settings.- For the Rule mode, ensure Enforce is selected.This setting is enabled by default when a new transport rule is created.(Optional) Configure the rest of the email transport rule settings as needed.Click Next to continue.Save.Review the email transport rule configuration and click Finish.Click Done when prompted that the email transport rule was successfully created. You are redirected back to the Microsoft Exchange Rules page.Modify the email transport rule priority as needed.To change the priority of a transport rule, select the transport rule and Move Up or Move Down as needed.A proper rule hierarchy is recommended to ensure emails successfully forward to Enterprise DLP.
- The email transport rule should always be the highest priority rule relative to the other transport rules required for Email DLP.
- Any email encryption rules not created as part of the Email DLP configuration must be ordered below the transport rules created for Email DLP. Enterprise DLP cannot inspect encrypted emails.
- There is no impact in regards to priority between the quarantine transport rules, block transport rule, encrypt transport rule, or any other transport rules that exist.After Enterprise DLP inspects and returns the email back to Microsoft Exchange, the appropriate transport rule action will occur based on the email header.
![]()
Create a Microsoft Exchange Hosted Quarantine Transport Rule
Create a Microsoft Exchange Quarantine transport rule to quarantine and forward a quarantined email to Microsoft Exchange hosted quarantine for approval after inspection by Enterprise Data Loss Prevention (E-DLP).Microsoft supports email approvals on the web browser-based Microsoft Exchange only. Approving or rejecting emails on the Microsoft Exchange mobile application or desktop client is not supported.- Log in to the Microsoft Exchange Admin Center.Create the outbound and inbound connectors.Skip this step if you have already created both the outbound and inbound connectors.Select Mail flowRulesAdd a ruleCreate a new rule to create a new email transport rule.
![]() Configure the quarantine transport rule conditions.
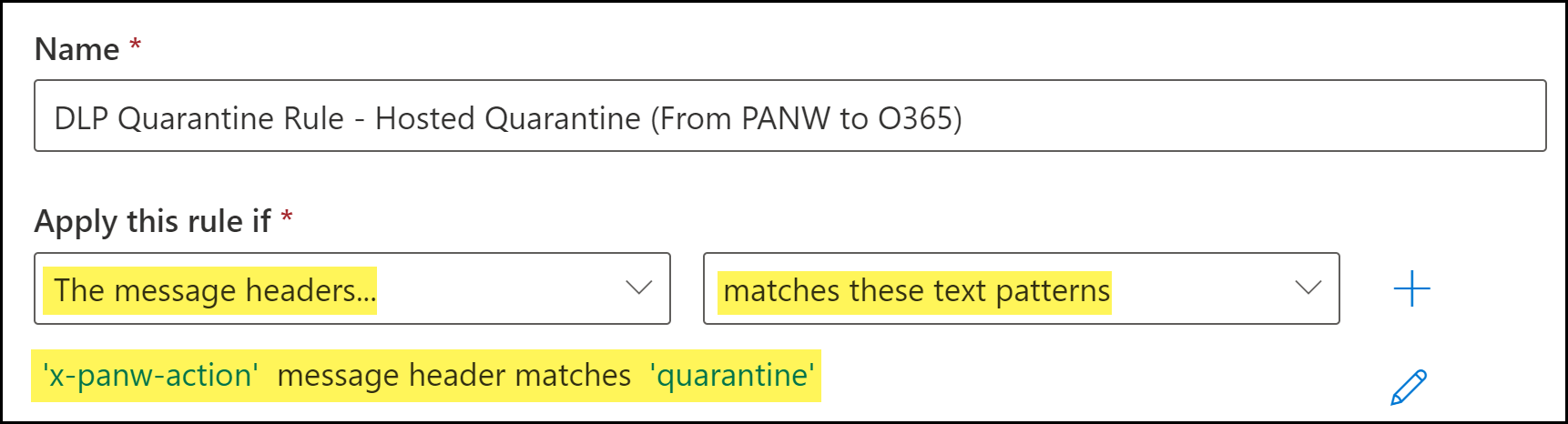
Configure the quarantine transport rule conditions.- Enter a Name for the quarantine transport rule.Add the quarantine email message header.The quarantine header is added by the DLP cloud service when an email contains sensitive information that needs to be approved by your email administrator.
- For Apply this rule if, select The message headers....
- Select match these text patterns.
- Click Enter Text. When promoted, enter the following.x-panw-actionClick Save to continue.Click Enter words. When prompted, enter the following and Add:quarantineSelect the word you added. Click Save to continue.
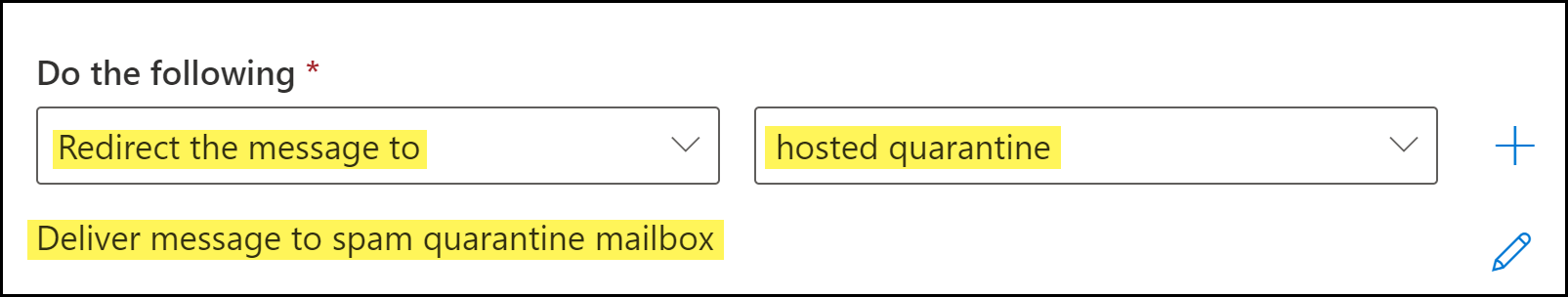
![]() Specify the action Microsoft Exchange takes when an email header includes the quarantine header added by Enterprise DLP.
Specify the action Microsoft Exchange takes when an email header includes the quarantine header added by Enterprise DLP.- For Do the following, select Redirect the message to.
- Select hosted quarantine.
![]()
Click Next to continue.Configure the quarantine transport rule settings.- For the Rule mode, ensure Enforce is selected.This setting is enabled by default when a new transport rule is created.(Optional) Configure the rest of the quarantine transport rule settings as needed.Click Next to continue.Review the quarantine transport rule configuration and click Finish.Click Done when prompted that the quarantine transport rule was successfully created. You are redirected back to the Microsoft Exchange Rules page.Modify the email transport rule priority as needed.To change the priority of a transport rule, select the transport rule and Move Up or Move Down as needed.A proper rule hierarchy is recommended to ensure emails successfully forward to Enterprise DLP.
- The email transport rule should always be the highest priority rule relative to the other transport rules required for Email DLP.
- Any email encryption rules not created as part of the Email DLP configuration must be ordered below the transport rules created for Email DLP. Enterprise DLP cannot inspect encrypted emails.
- There is no impact in regards to priority between the quarantine transport rules, block transport rule, encrypt transport rule, or any other transport rules that exist.After Enterprise DLP inspects and returns the email back to Microsoft Exchange, the appropriate transport rule action will occur based on the email header.
![]() An email administrator must review and approve or reject quarantined emails forwarded to the hosted quarantine mailbox.
An email administrator must review and approve or reject quarantined emails forwarded to the hosted quarantine mailbox.Create a Microsoft Exchange Admin Approval Transport Rule
Create a Microsoft Exchange transport rule to forward an email to the specified email administrator for approval after inspection by Enterprise Data Loss Prevention (E-DLP).Microsoft supports email approvals on the web browser-based Microsoft Exchange only. Approving or rejecting emails on the Microsoft Exchange mobile application or desktop client is not supported.- Log in to the Microsoft Exchange Admin Center.Create the outbound and inbound connectors.Skip this step if you have already created both the outbound and inbound connectors.Select Mail flowRulesAdd a ruleCreate a new rule to create a new email transport rule.
![]() Configure the transport rule conditions.
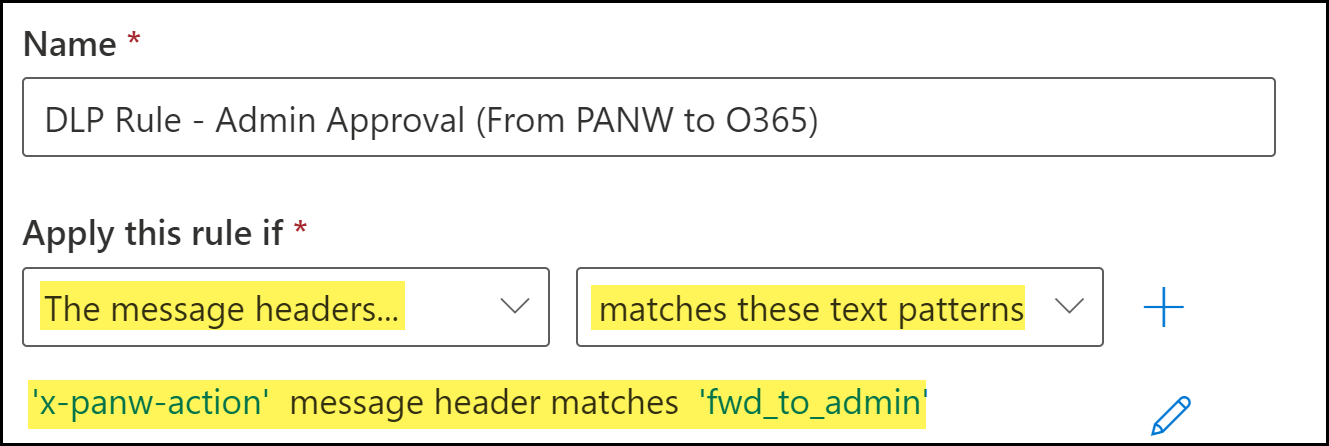
Configure the transport rule conditions.- Enter a Name for the transport rule.Add the email message header.The fwd_to_admin email header is added by the DLP cloud service when an email contains sensitive information requiring email administrator approval.
- For Apply this rule if, select The message headers....
- Select match these text patterns.
- Click Enter Text. When promoted, enter the following.x-panw-actionClick Save to continue.Click Enter words. When prompted, enter the following and Add:fwd_to_adminSelect the word you added. Click Save to continue.
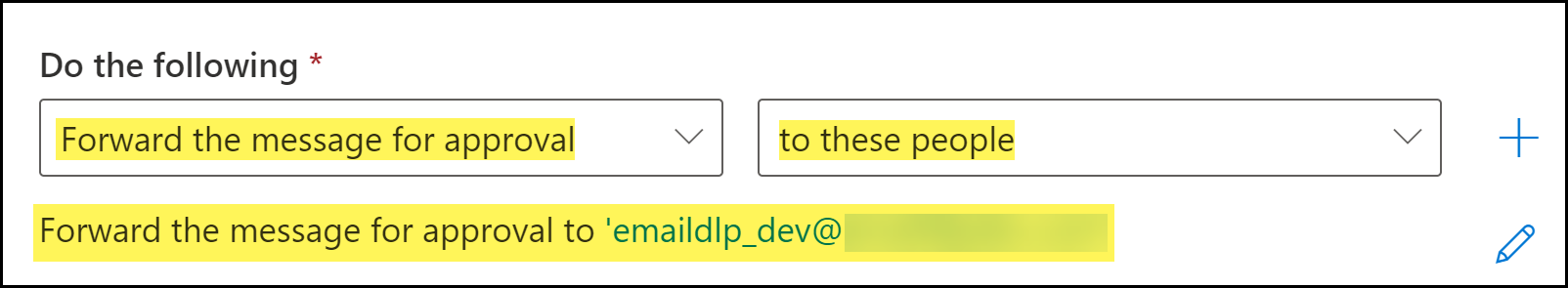
![]() Specify the action Microsoft Exchange takes when an email header includes the header added by Enterprise DLP.
Specify the action Microsoft Exchange takes when an email header includes the header added by Enterprise DLP.- For Do the following, select Forward the message for approval.
- Select to these people.
![]()
Click Next to continue.Configure the transport rule settings.- For the Rule mode, ensure Enforce is selected.This setting is enabled by default when a new transport rule is created.(Optional) Configure the rest of the transport rule settings as needed.Click Next to continue.Review the transport rule configuration and click Finish.Click Done when prompted that the transport rule was successfully created. You are redirected back to the Microsoft Exchange Rules page.Modify the transport rule priority as needed.To change the priority of a transport rule, select the transport rule and Move Up or Move Down as needed.A proper rule hierarchy is recommended to ensure emails successfully forward to Enterprise DLP.
- The email transport rule should always be the highest priority rule relative to the other transport rules required for Email DLP.
- Any email encryption rules not created as part of the Email DLP configuration must be ordered below the transport rules created for Email DLP. Enterprise DLP cannot inspect encrypted emails.
- There is no impact in regards to priority between the quarantine transport rules, block transport rule, encrypt transport rule, or any other transport rules that exist.After Enterprise DLP inspects and returns the email back to Microsoft Exchange, the appropriate transport rule action will occur based on the email header.
![]()
Create a Microsoft Exchange Manager Approval Transport Rule
Create a Microsoft Exchange email transport rule to forward an email to the sender's manager for approval after inspection by Enterprise Data Loss Prevention (E-DLP).Microsoft Exchange Active Directory is required to assign a manager to a user. To successfully send an email for manager approval if sensitive data is detected by Enterprise DLP, the sender must have a manager assigned.If no manager is assigned to the sender, then the email is sent to the recipient because no manager is assigned to approve or reject the email.Additionally, Microsoft supports email approvals on the web browser-based Microsoft Exchange only. Approving or rejecting emails on the Microsoft Exchange mobile application or desktop client is not supported.- Log in to the Microsoft Exchange Admin Center.Create the outbound and inbound connectors.Skip this step if you have already created both the outbound and inbound connectors.Select Mail flowRulesAdd a ruleCreate a new rule to create a new email transport rule.
![]() Configure the transport rule conditions.
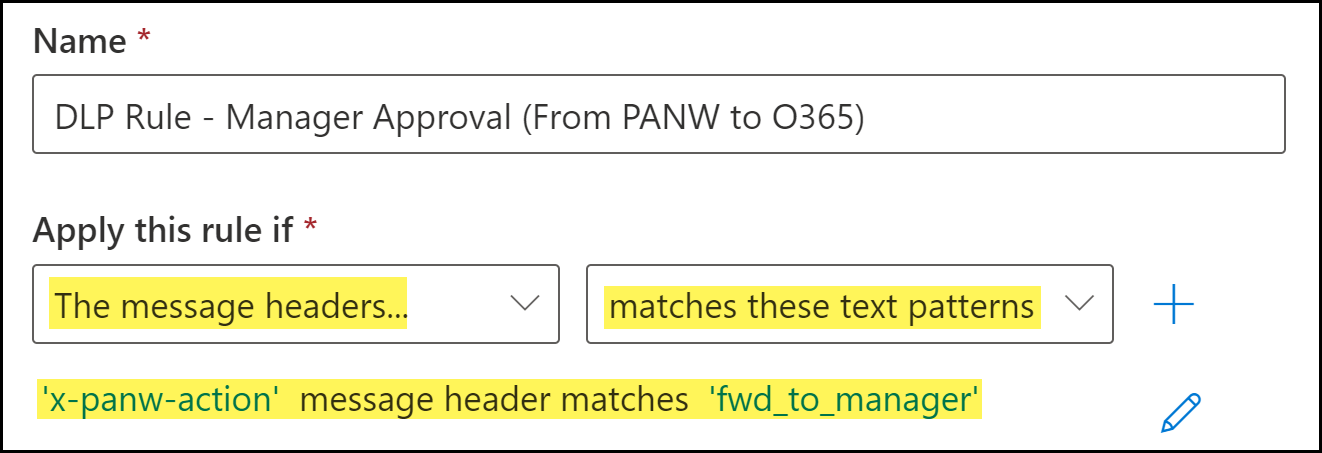
Configure the transport rule conditions.- Enter a Name for the transport rule.Add the email message header.The fw_to_manager header is added by the DLP cloud service when an email contains sensitive information requiring manager approval.
- For Apply this rule if, select The message headers....
- Select match these text patterns.
- Click Enter Text. When promoted, enter the following.x-panw-actionClick Save to continue.Click Enter words. When prompted, enter the following and Add:fwd_to_managerSelect the word you added. Click Save to continue.
![]() Specify the action Microsoft Exchange takes when an email header includes the header added by Enterprise DLP.Microsoft Exchange Active Directory is required to assign a manager to a user. To successfully forward a sender's email if sensitive data is detected by Enterprise DLP, a user must have a manager assigned.If no manager is assigned to a user, then the email is sent to the recipient because no manager is assigned to approve or reject the email.
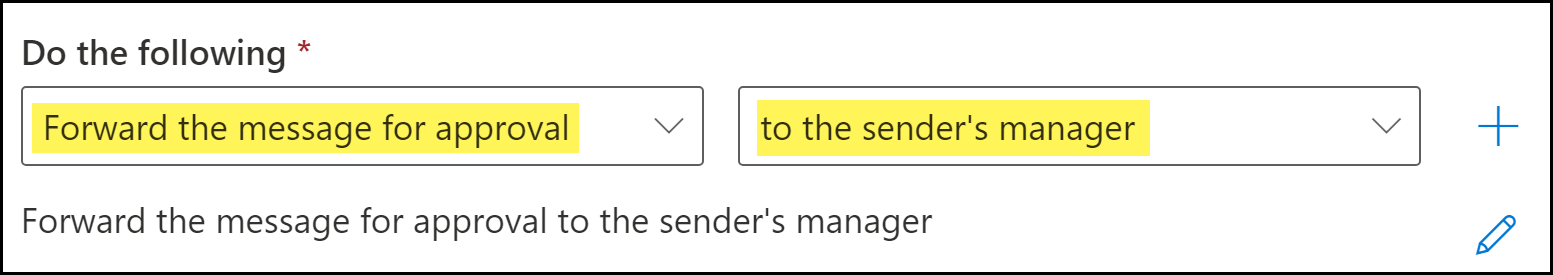
Specify the action Microsoft Exchange takes when an email header includes the header added by Enterprise DLP.Microsoft Exchange Active Directory is required to assign a manager to a user. To successfully forward a sender's email if sensitive data is detected by Enterprise DLP, a user must have a manager assigned.If no manager is assigned to a user, then the email is sent to the recipient because no manager is assigned to approve or reject the email.- For Do the following, select Forward the message for approval.
- Select to the sender's manager.
![]()
Click Next to continue.Configure the transport rule settings.- For the Rule mode, ensure Enforce is selected.This setting is enabled by default when a new transport rule is created.(Optional) Configure the rest of the transport rule settings as needed.Click Next to continue.Review the transport rule configuration and click Finish.Click Done when prompted that the transport rule was successfully created. You are redirected back to the Microsoft Exchange Rules page.Modify the email transport rule priority as needed.To change the priority of a transport rule, select the transport rule and Move Up or Move Down as needed.A proper rule hierarchy is recommended to ensure emails successfully forward to Enterprise DLP.
- The email transport rule should always be the highest priority rule relative to the other transport rules required for Email DLP.
- Any email encryption rules not created as part of the Email DLP configuration must be ordered below the transport rules created for Email DLP. Enterprise DLP cannot inspect encrypted emails.
- There is no impact in regards to priority between the quarantine transport rules, block transport rule, encrypt transport rule, or any other transport rules that exist.After Enterprise DLP inspects and returns the email back to Microsoft Exchange, the appropriate transport rule action will occur based on the email header.
![]()
Create a Microsoft Exchange Encrypt Transport Rule
Create a Microsoft Exchange Encrypt transport rule to encrypt an outbound email to Microsoft Exchange after inspection by Enterprise Data Loss Prevention (E-DLP).- Log in to the Microsoft Exchange Admin Center.Create the required Microsoft Exchange connectors.Skip this step if you have already created both the outbound, inbound, and Proofpoint server connectors.Select Mail flowRulesAdd a ruleCreate a new rule to create a new email transport rule.
![]() Configure the encrypt transport rule conditions.
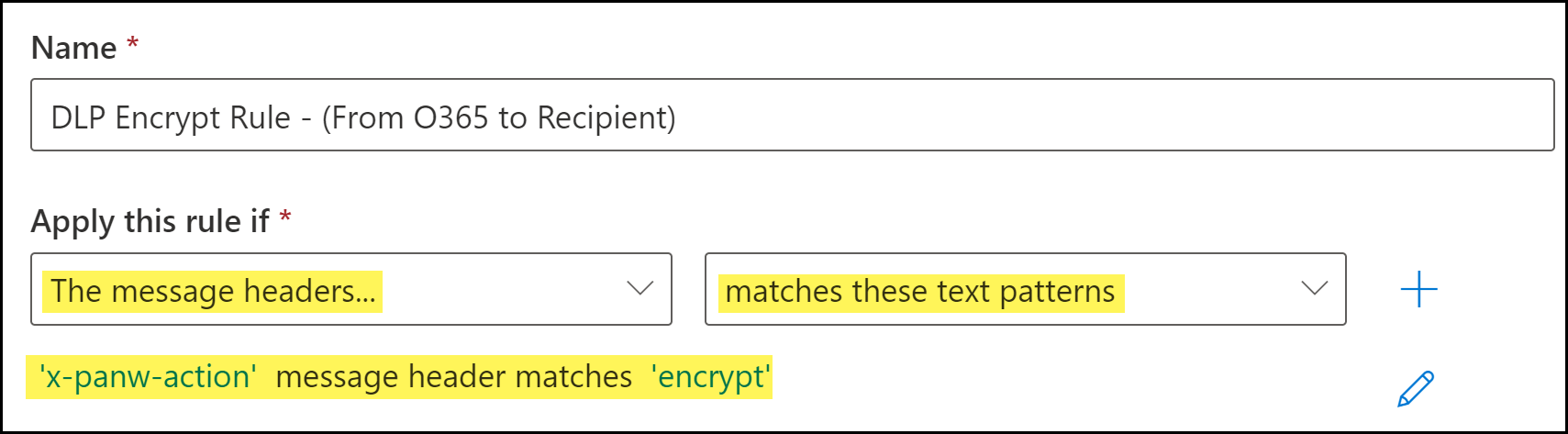
Configure the encrypt transport rule conditions.- Enter a Name for the encrypt transport rule.Add the encrypt email message header.The encrypt header is added by the DLP cloud service when an email contains sensitive information that should be encrypted.
- For Apply this rule if, select The message headers....
- Select match these text patterns.
- Click Enter Text. When promoted, enter the following.x-panw-actionClick Save to continue.Click Enter words. When prompted, enter the following and Add:encryptSelect the word you added. Click Save to continue.
![]() Specify the action Microsoft Exchange takes when an email header includes the encrypt header added by Enterprise DLP.
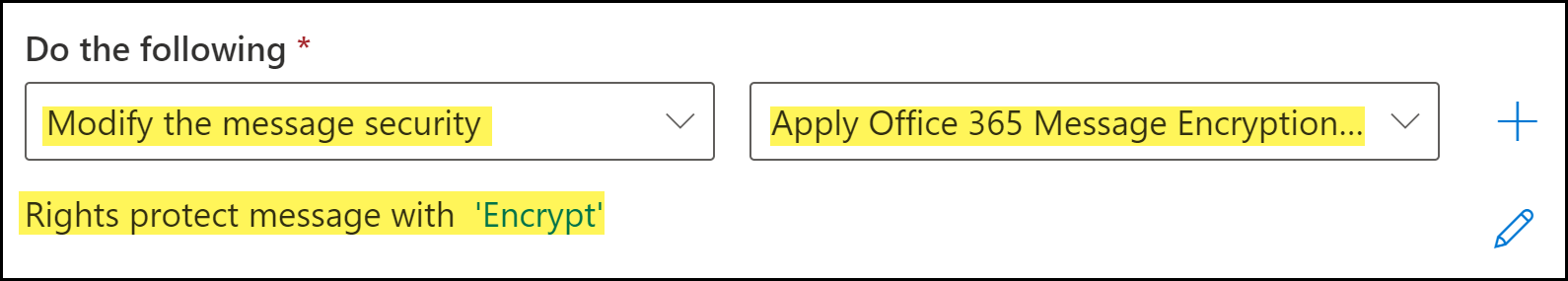
Specify the action Microsoft Exchange takes when an email header includes the encrypt header added by Enterprise DLP.- For Do the following, select Modify the message security.
- Select Apply Office 365 Message Encryption and rights protection.
- Select the RMS template you want to use for outbound email encryption and Save.
![]()
Click Next to continue.Configure the encrypt transport rule settings.- For the Rule mode, ensure Enforce is selected.This setting is enabled by default when a new transport rule is created.(Optional) Configure the rest of the encrypt transport rule settings as needed.Click Next to continue.Review the encrypt transport rule configuration and click Finish.Click Done when prompted that the encrypt transport rule was successfully created. You are redirected back to the Microsoft Exchange Rules page.Modify the email transport rule priority as needed.To change the priority of a transport rule, select the transport rule and Move Up or Move Down as needed.A proper rule hierarchy is recommended to ensure emails successfully forward to Enterprise DLP.
- The email transport rule should always be the highest priority rule relative to the other transport rules required for Email DLP.
- Any email encryption rules not created as part of the Email DLP configuration must be ordered below the transport rules created for Email DLP. Enterprise DLP cannot inspect encrypted emails.
- There is no impact in regards to priority between the quarantine transport rules, block transport rule, encrypt transport rule, or any other transport rules that exist.After Enterprise DLP inspects and returns the email back to Microsoft Exchange, the appropriate transport rule action will occur based on the email header.
![]()
Create a Microsoft Exchange Proofpoint Encrypt Transport Rule
Create a Microsoft Exchange Encrypt transport rule to forward an email to your Proofpoint server for encrypting after inspection by Enterprise Data Loss Prevention (E-DLP).This procedure assumes you have already setup your Proofpoint server and created the required Proofpoint connector.- Log in to the Microsoft Exchange Admin Center.Create the required Microsoft Exchange connectors.Skip this step if you have already created both the outbound, inbound, and Proofpoint server connectors.Select Mail flowRulesAdd a ruleCreate a new rule to create a new email transport rule.
![]() Configure the encrypt transport rule conditions.
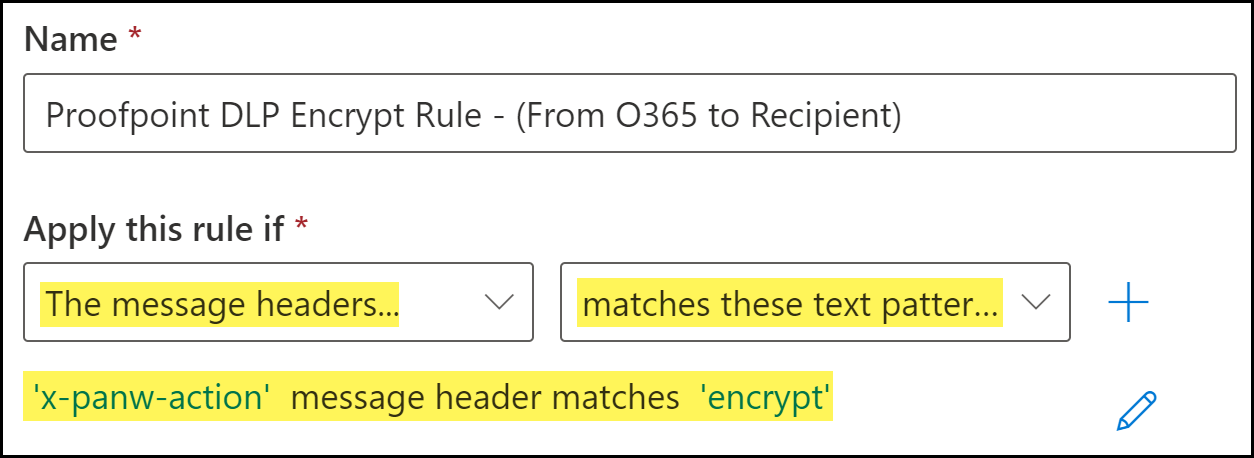
Configure the encrypt transport rule conditions.- Enter a Name for the Proofpoint encrypt transport rule.Add the encrypt email message header.The encrypt header is added by the DLP cloud service when an email contains sensitive information that should be encrypted.
- For Apply this rule if, select The message headers....
- Select match these text patterns.
- Click Enter Text. When promoted, enter the following.x-panw-actionClick Save to continue.Click Enter words. When prompted, enter the following and Add:encryptSelect the word you added. Click Save to continue.
![]() Specify the action Microsoft Exchange takes when an email header includes the encrypt header added by Enterprise DLP.
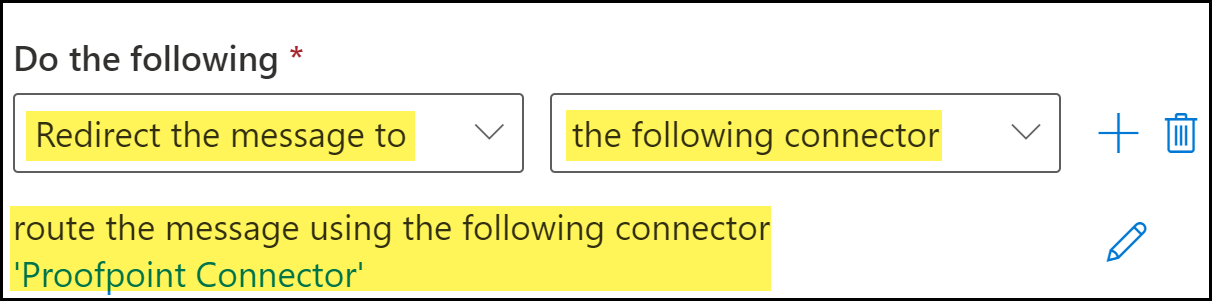
Specify the action Microsoft Exchange takes when an email header includes the encrypt header added by Enterprise DLP.- For Do the following, select Redirect the message to.
- Select the following connector.
- Select the Proofpoint connector and Save.
![]()
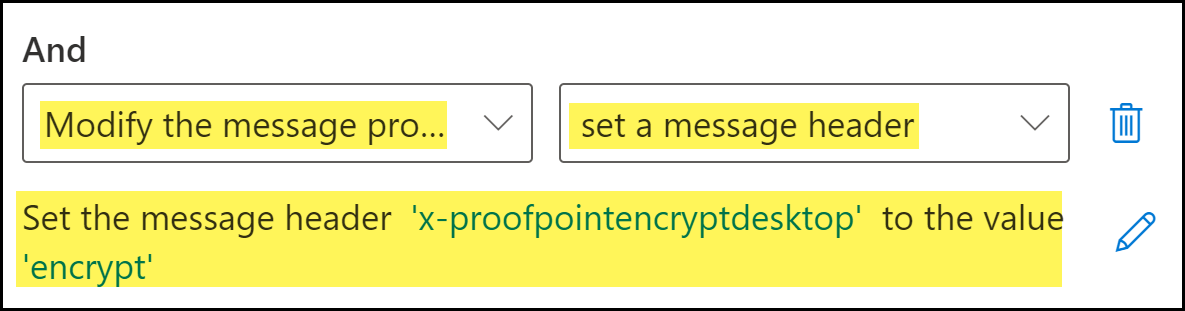
Click the Add Action icon (+) to add an additional rule condition.Instruct Microsoft Exchange to further modify the email header.- For Do the following, select Modify the message properties.
- Select set a message header.
- Click Enter Text. When promoted, enter the following.x-proofpointencryptdesktopClick Save to continue.Click Enter words. When prompted, enter the following and Add:encryptSelect the word you added. Click Save to continue.
![]() Click Next to continue.Configure the Proofpoint encrypt transport rule settings.
Click Next to continue.Configure the Proofpoint encrypt transport rule settings.- For the Rule mode, ensure Enforce is selected.This setting is enabled by default when a new transport rule is created.(Optional) Configure the rest of the encrypt transport rule settings as needed.Click Next to continue.Review the encrypt transport rule configuration and click Finish.Click Done when prompted that the encrypt transport rule was successfully created. You are redirected back to the Microsoft Exchange Rules page.Modify the email transport rule priority as needed.To change the priority of a transport rule, select the transport rule and Move Up or Move Down as needed.A proper rule hierarchy is recommended to ensure emails successfully forward to Enterprise DLP.
- The email transport rule should always be the highest priority rule relative to the other transport rules required for Email DLP.
- Any email encryption rules not created as part of the Email DLP configuration must be ordered below the transport rules created for Email DLP. Enterprise DLP cannot inspect encrypted emails.
- There is no impact in regards to priority between the quarantine transport rules, block transport rule, encrypt transport rule, or any other transport rules that exist.After Enterprise DLP inspects and returns the email back to Microsoft Exchange, the appropriate transport rule action will occur based on the email header.
- If you want to ensure emails are forwarded to your Proofpoint server for encryption, Palo Alto Networks recommends disabling your existing Encrypt or assigning a higher priority to the Proofpoint encrypt rule.You can forward an email for encryption to either your Proofpoint server or to Microsoft Exchange for encryption, but not both.
![]()
Create a Microsoft Exchange Block Transport Rule
Create a Microsoft Exchange Block transport rule to specify the action Microsoft Exchange takes when an email contains sensitive data and is blocked.- Log in to the Microsoft Exchange Admin Center.Create the outbound and inbound connectors.Skip this step if you have already created both the outbound and inbound connectors.Select Mail flowRulesAdd a ruleCreate a new rule to create a new email transport rule.
![]() Configure the Block transport rule conditions.
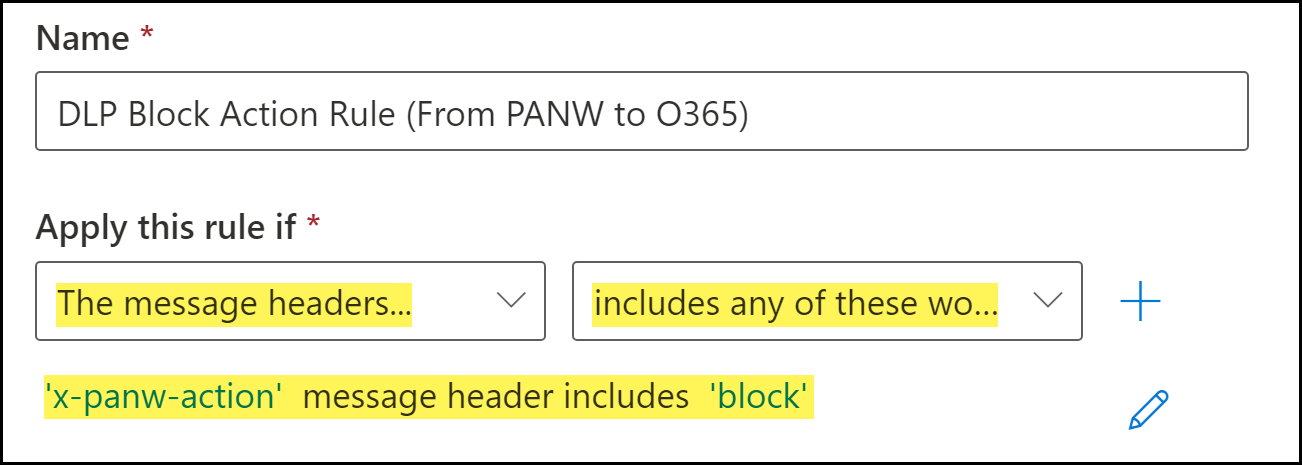
Configure the Block transport rule conditions.- Enter a Name for the Block transport rule.Add the Block email message header.The Block header is added by the DLP cloud service when an inspected email contains sensitive information that is blocked.
- For Apply this rule if, select The message headers....
- Select includes any of these words.
- Click Enter Text. When promoted, enter the following.x-panw-actionClick Save to continue.Click Enter words. When prompted, enter the following and Add:blockSelect the word you added. Click Save to continue.
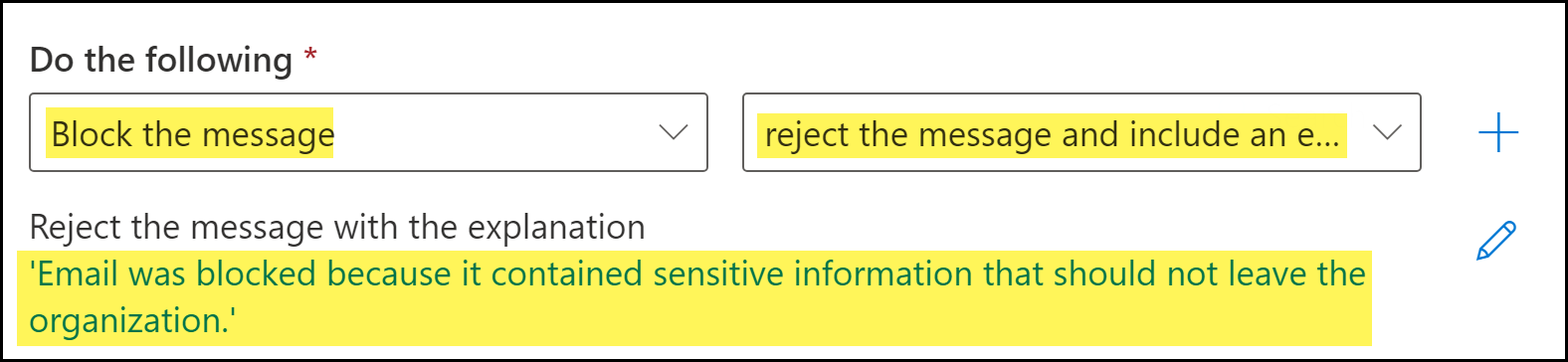
![]() Specify the action Microsoft Exchange takes when an email header includes the Block header added by Enterprise DLP.
Specify the action Microsoft Exchange takes when an email header includes the Block header added by Enterprise DLP.- For Do the following, select Block the message.
- Select reject the message and include an explanation. When prompted, enter the explanation for why the email was blocked.This is the response members of your organization receive when an outbound email is blocked.Click Save to continue.
![]() Click Next to continue.Configure the Block transport rule settings.
Click Next to continue.Configure the Block transport rule settings.- For the Rule mode, ensure Enforce is selected.