Download PDF
GlobalProtect
Deploy the GlobalProtect App for Android on Managed Chromebooks Using the Google Admin Console
Table of Contents
Deploy the GlobalProtect App for Android on Managed Chromebooks Using the Google Admin Console
Deploy GlobalProtect for Android
The Google Admin console enables you to manage Chromebook
settings and apps from a central, web-based location. You can deploy the
GlobalProtect app for Android on managed Chromebooks and configure
the associated VPN settings from the console.
To set up the
app for the user automatically, you can optionally use the Google Chromebook
Management Console to configure and deploy settings to managed Chrome
OS devices. You can use the Google Admin console to manage Chromebook settings
and apps.
Follow these recommendations to deploy the
GlobalProtect app for Android on managed Chromebooks:
- You cannot push a unique certificate for authentication to the device using the Google Admin console.
- From your Chromebook, press CTRL+ALT+T to open the terminal command line. Use the route command to display the routes that are installed on the device. You can determine whether to include the access routes for split tunneling.
- Because applications often use different file formats, you can use OpenSSL to convert the certificates from PKCS #12 format to Base64 format. Use the openssl base64 -A -in <certificate-in-p12-format> -out <cert.txt> command.
Use
the following steps to deploy the GlobalProtect app for Android
on managed Chromebooks using the Google Admin console:
- Before you begin:
- Configure the GlobalProtect gateways to support the GlobalProtect app for Android on managed Chromebooks. Refer to Configure a GlobalProtect Gateway.
- Configure the portal and customize the GlobalProtect app for Android on managed Chromebooks. You must configure one or more gateways to which the GlobalProtect app can connect. Refer to Set Up Access to the GlobalProtect Portal. Refer to the Palo Alto Networks Compatibility Matrix for a list of features supported for Android on Chrome OS.
- (Recommended) Enable SAML SSO for the GlobalProtect app for Android on Chromebooks for seamless authentication. We recommend that you set up SAML SSO to allow users to connect automatically after they log in to Chromebook without having to re-enter their credentials on the GlobalProtect app. This ensures that users have access to always on security. Refer to Set Up SAML Authentication.
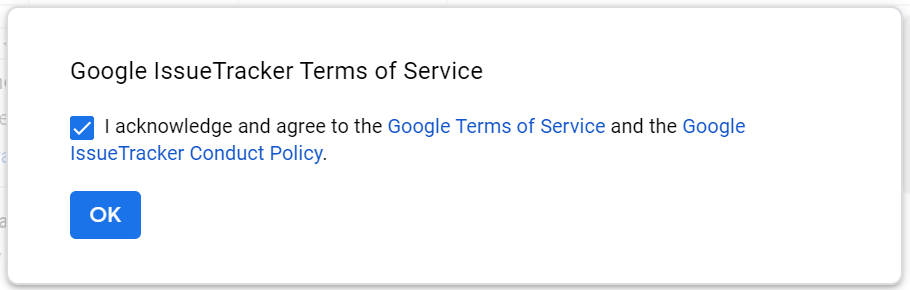
- When users connect to GlobalProtect for the first time on Android on managed Chromebooks, the following suppress VPN notification message must be acknowledged before the tunnel is set up:
![]()
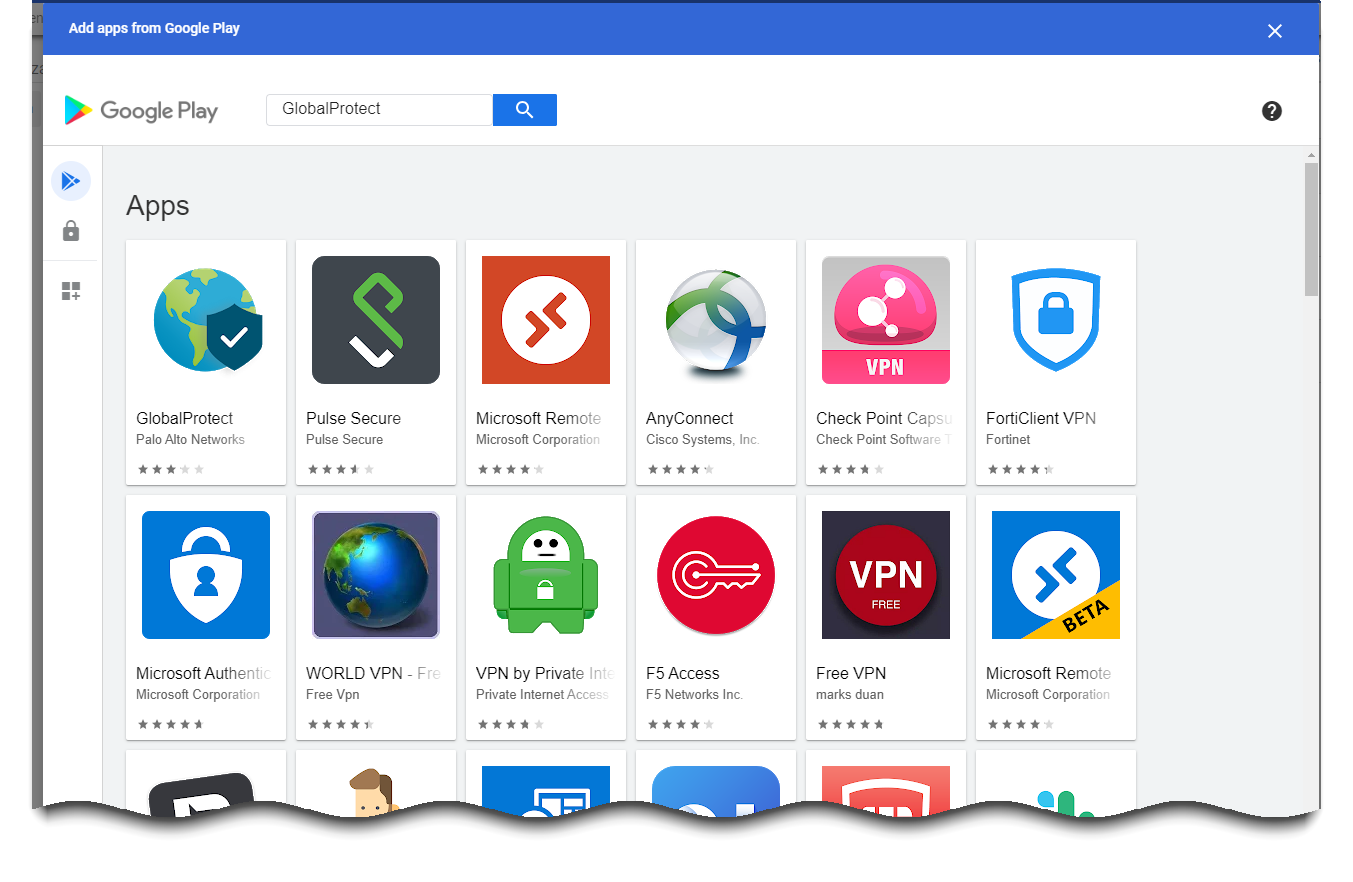
Approve the GlobalProtect app for Chromebook users.- Log in to the Google Admin console as an administrator.From the Admin console, select DevicesChrome management to view and modify the Chrome management settings.Select Apps & extensions.In the Apps and extensions area, click the application settings page link.Click the add () button to add GlobalProtect to the list of approved Android apps from the Google Playstore.
![]() When the Google Play store launches, search for GlobalProtect and then click the GlobalProtect app icon.
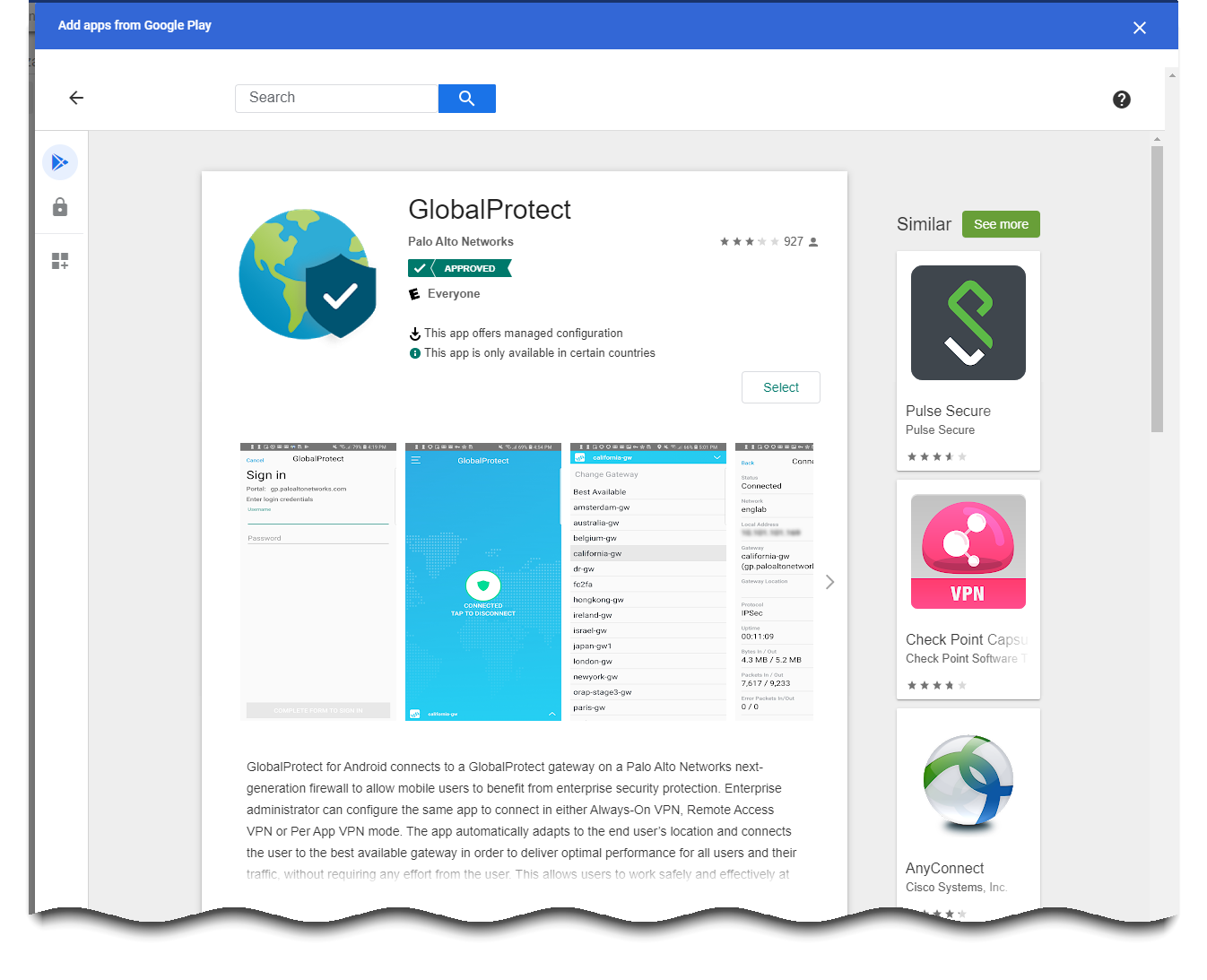
When the Google Play store launches, search for GlobalProtect and then click the GlobalProtect app icon.![]() Click Select to add the GlobalProtect app.A message appears if the GlobalProtect app is successfully added as a result.
Click Select to add the GlobalProtect app.A message appears if the GlobalProtect app is successfully added as a result.![]() Determine how the GlobalProtect app is installed on Chromebooks.After you approve the GlobalProtect app, you must specify how the app is installed on Chromebooks. To prevent users from bypassing GlobalProtect by uninstalling the app, force all Chromebooks to install the GlobalProtect app automatically when users log in to their Chromebook.
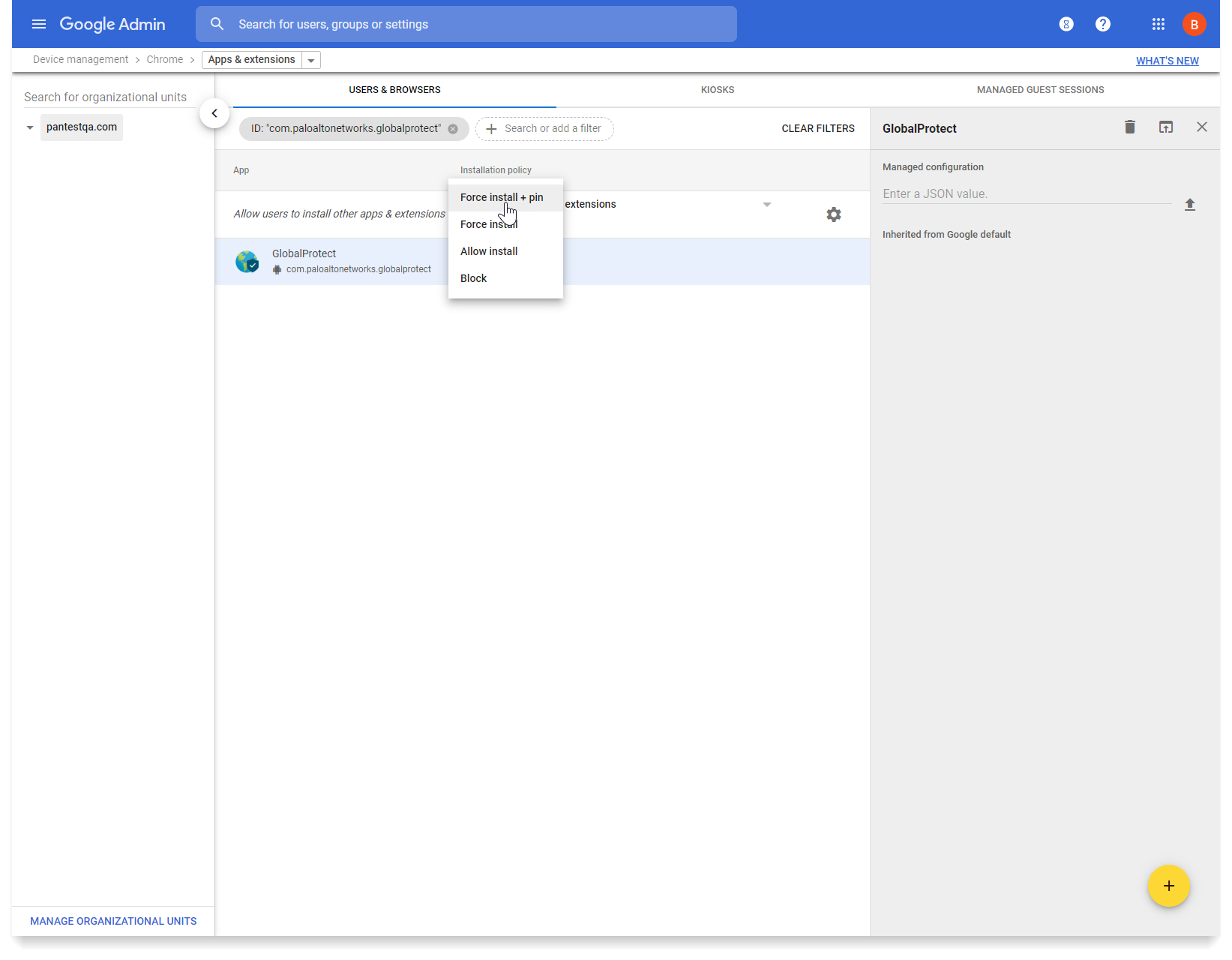
Determine how the GlobalProtect app is installed on Chromebooks.After you approve the GlobalProtect app, you must specify how the app is installed on Chromebooks. To prevent users from bypassing GlobalProtect by uninstalling the app, force all Chromebooks to install the GlobalProtect app automatically when users log in to their Chromebook.- From the app extension management settings (Device managementChrome Apps & extensions), select GlobalProtect from the Apps list.Select your organizational unit from the list on the left edge of the page.Select any of the following options:
- (Recommended) Force install + pin—Enable and pin the force-installed GlobalProtect app to the taskbar. If you selected this option, users will not have the option to Sign Out of the app.
- Force install—Use this option if you want to ensure that the GlobalProtect app is automatically installed on each Chromebook when users log in to their Chromebooks. To prevent users from uninstalling the GlobalProtect app and getting around the security and compliance requirements you want to enforce the Force install option. If you selected this option, users will not have the option to Sign Out of the app.
- Allow install—Install this app manually from the Google Playstore. This option also allows users to uninstall the GlobalProtect app from their Chromebooks.
- Block—Block users from installing this app.
![]() SAVE your changes.Apply a managed configuration to the GlobalProtect app.If you have enabled the GlobalProtect app to force install, you can apply a managed configuration file to the app. The managed configuration file contains values for configurable app settings.
SAVE your changes.Apply a managed configuration to the GlobalProtect app.If you have enabled the GlobalProtect app to force install, you can apply a managed configuration file to the app. The managed configuration file contains values for configurable app settings.- From the App Management settings (Device ManagementChrome managementApps & Extensions), select GlobalProtect from the Apps list.Select your organizational unit from the list on the left edge of the page.Click the Upload from file icon on the right edge of the page to select and upload your managed configuration file. Or enter the name of the key value in JSON format, as shown in the following sample configuration.
{ "portal": "acme.portal.com", "username": "user123" }The following table displays an example of the settings in the managed configuration file. For the settings that are relevant for your company, please contact your IT administrator.SettingDescriptionValue TypeExampleportalIP address or fully qualified domain name (FQDN) of the portal.Stringacme.portal.com usernameUsername for portal authentication.Stringuser123 passwordPassword for portal authentication.Stringpassword123 client_certificateClient certificate for portal authentication.String (in Base64)DAFDSaweEWQ23wDSAFD… client_certificate_passphraseClient certificate passphrase for portal authentication.StringPA$$W0RD$123 app_listBegin the string with either the allowlist keyword or blocklist keyword followed by a colon, and follow it with an array of app names separated by semicolons. The block list or allow list enables you to control which application traffic can go through the VPN tunnel in a per-app VPN configuration.Stringallowlist| blocklist: com.google.calendar; com.android.email; com.android.chrome connect_methodVPN connection method.Stringuser-logon | on-demand mobile_idUnique identifier used to identify mobile endpoints, as configured in a third-party MDM system.String5188a8193be43f42d332 dde5cb2c941e remove_vpn_config_via_restrictionFlag to remove the VPN configuration.Booleantrue | false allow_vpn_bypassFlag to allow application traffic to bypass the VPN tunnel.Booleantrue | false cert_aliasUnique name used to identify the client certificate during portal or gateway authentication.StringCompany User client managedFlag to indicate whether the device is enrolled with an MDM server.Booleantrue | false ownershipOwnership category of the device (for example, Employee Owned).Stringbyod complianceCompliance status that indicates whether the device is compliant with the compliance policies that you have defined.Stringyes tagTags to enable you to identify devices. Each tag must be separated by a comma.StringGuestAccount,SatelliteOffice SAVE your changes.Enforce policies on the GlobalProtect app for Android on managed Chromebooks.- Create HIP objects using Host Info that is specific to Android on managed Chromebooks. Then use it as match conditions in any Host Information Profile (HIP) profiles.
- Enforce the corresponding security policy using a HIP profile as a match condition in a policy rule. By default, the app collects data categories of information to help identify the security state of the host.