Advanced WildFire Powered by Precision AI™
Verify File Forwarding
Table of Contents
Verify File Forwarding
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
After the firewall is set up to Forward Files for Advanced WildFire Analysis, use the following
options to verify the connection between the firewall and the Advanced
WildFire public or WildFire private cloud, and to monitor file forwarding.
Several
of the options to verify that a firewall is forwarding samples for
analysis are CLI commands; for details on getting started with and
using the CLI, refer to the PAN-OS CLI Quick Start Guide.
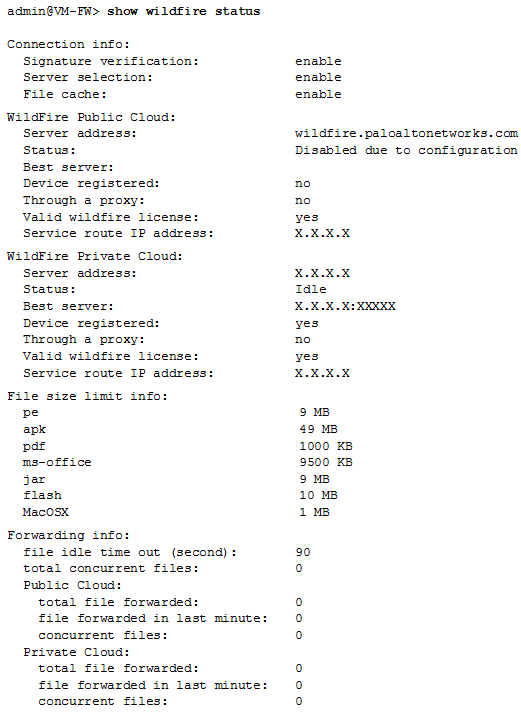
- Verify the status of the firewall connection to the Advanced WildFire public and/or WildFire private cloud, including the total number of files forwarded by the firewall for analysis.Use the show wildfire status command to:
- Check the status of the Advanced WildFire public and/or WildFire private cloud to which the firewall is connected. The status Idle indicates that the Advanced WildFire cloud (public or private) is ready to receive files for analysis.
- Confirm the configured size limits for files forwarded by the firewall (DeviceSetupWildFire).
- Monitor file forwarding, including how the total count of files forwarded by the firewall for analysis. If the firewall is in a WildFire hybrid cloud deployment, the number of files forwarded to the WildFire public cloud and the WildFire private cloud are also displayed.
The following example shows the show wildfire status output for a firewall in a WildFire private cloud deployment:![]() To view forwarding information for only the Advanced WildFire public cloud or WildFire private cloud, use the following commands:
To view forwarding information for only the Advanced WildFire public cloud or WildFire private cloud, use the following commands:- show wildfire status channel public
- show wildfire status channel private
View samples forwarded by the firewall according to file type (including email links).Use this option to confirm that email links are being forwarded for analysis, since only email links that receive a malicious or phishing verdict are logged as WildFire Submissions entries on the firewall, even if logging for benign and grayware samples is enabled. This is due to the sheer number of WildFire Submissions entries that would be logged for benign email links.Use the show wildfire statistics command to confirm the file types being forwarded to the Advanced WildFire public or WildFire private cloud:- The command displays the output of a working firewall and shows counters for each file type that the firewall forwards for analysis. If a counter field shows 0, the firewall is not forwarding that file type.
- Confirm that email links are being forwarded for analysis by checking that the following counters do not show zero:
- FWD_CNT_APPENDED_BATCH—Indicates the number of email links added to a batch waiting for upload to an Advanced WildFire public or WildFire private cloud.
- FWD_CNT_LOCAL_FILE— Indicates the total number of email links uploaded to an Advanced WildFire public or WildFire private cloud.
Verify that a specific sample was forwarded by the firewall and check that status of that sample.This option can be helpful when troubleshooting to:- Confirm that samples that have not yet received a verdict were correctly forwarded by the firewall. Because WildFire Submissions are logged on the firewall only when analysis is complete and the sample has received a verdict, use this option to verify the firewall forwarded a sample that is currently undergoing analysis.
- Track the status for a single file or email link that was allowed according to your security policy, matched to a WildFire Analysis profile, and then forwarded for analysis.
- Check that a firewall in a hybrid cloud deployment is forwarding the correct file types and email links to either the Advanced WildFire public cloud or a WildFire private cloud.
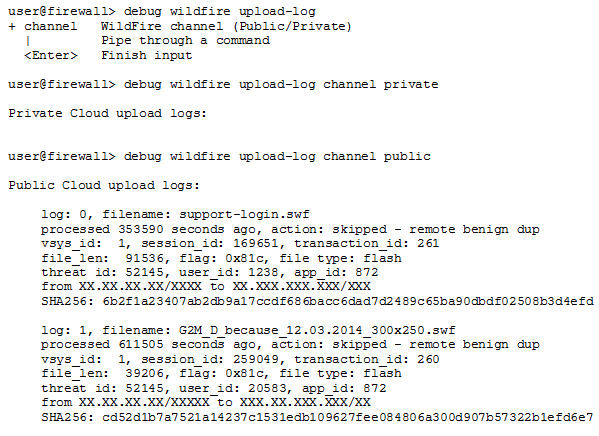
Execute the following CLI commands on the firewall to view samples the firewall has forwarded for analysis:- View all samples forwarded by the firewall with the CLI command debug wildfire upload-log.
- View only samples forwarded to the Advanced WildFire public cloud with the CLI command debug wildfire upload-log channel public.
- View only samples forwarded to the WildFire private cloud with the CLI command debug wildfire upload-log channel private.
The following example shows the output for the three commands listed above when issued on a firewall in an Advanced WildFire public cloud deployment:![]() Monitor samples successfully submitted for analysis.Using the firewall web interface, select MonitorLogsWildFire Submissions. All files forwarded by a firewall to the Advanced WildFire public or WildFire private cloud for analysis are logged on the WildFire Submissions page.
Monitor samples successfully submitted for analysis.Using the firewall web interface, select MonitorLogsWildFire Submissions. All files forwarded by a firewall to the Advanced WildFire public or WildFire private cloud for analysis are logged on the WildFire Submissions page.- Check the verdict for a sample:By default, only samples that receive malicious or phishing verdicts are displayed as WildFire Submissions entries. To enable logging for benign and/or grayware samples, select DeviceSetupWildFireReport Benign Files/ Report Grayware Files.Enable logging for benign files as a quick troubleshooting step to verify that the firewall is forwarding files. Check the WildFire Submissions logs to verify that files are being submitted for analysis and receiving verdicts (in this case, a benign verdict).
- Confirm the analysis location for a sample:The WildFire Cloud column displays the location to which the file was forwarded and where it was analyzed. This is useful when deploying a hybrid cloud.