AI Access Security
Tag GenAI Apps
Table of Contents
Expand All
|
Collapse All
AI Access Security Docs
Tag GenAI Apps
Apply tags to the application to reflect whether the application is approved within
your organization.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
And one of the following:
|
Based on a GenAI apps
risk score and other considerations, you can apply tags to
the application to reflect whether the application is approved within your
organization. The following tags are available:
| Tag | Description |
|---|---|
|
Sanctioned
|
The application is approved by your organization, and is being
used by members of your organization.
|
|
Unsanctioned
|
The application isn't approved by your organization. For example,
the application might be unsanctioned due to security risks
associated with the application.
Because members of your organization should not be using the
application, you should take action to block the application.
You can use a policy rule to block the application.
|
|
Tolerated
|
The application isn't trusted like a sanctioned application.
However, your organization allows its use until your
organization can identify a more secure application. The
application is tolerated so as not to inhibit your
organization's productivity.
Because the application is allowed despite potential security
risks, you might take steps to restrict certain actions. For
example, you might create a policy rule to block upload or
download operations for the application.
|
Palo Alto Networks groups the child App-IDs for app functionality in a container
App-ID. However, tagging an App-ID container isn’t supported. You must
individually tag the specific child App-ID that are sanctioned, unsanctioned, or
tolerated within your organization.
For example, consider the claude container App-ID
that contains the following child App-IDs:
claude-base,
claude-upload,
claude-edit,
claude-post, and
claude-delete.
You create an application filter to enforce the same
data exfiltration controls for Sanctioned applications.
In this case, you must tag all the child App-IDs of the
claude App-ID container to apply the policy rule action for all
sub-processes of the Sanctioned
claude GenAI app.
In September 2024, Palo Alto Networks updated the way app tagging is
implemented. Starting in September 2024, tags are written to, and read from, a
new predefined Application-Tagging snippet. After
this update is released to your tenant, it takes effect the first time you tag
an app. The tags are written to the snippet and AI Access Security, the Activity Insights Applications page, and the
Strata Cloud Manager Command Center start displaying tag information from the
snippet. If you tagged apps prior to this update, you will no longer see those
tag changes reflected in AI Access Security and Activity Insights
Applications. The Application-Tagging snippet
tracks which apps are tagged as Sanctioned or
Tolerated. Apps not explicitly tagged as
Sanctioned or Tolerated are
considered Unsanctioned. For this reason, only the tags
you add after this update will be shown in Strata Cloud Manager. All other apps
are shown as Unsanctioned.
The tags that you applied prior to this update still affect tag-based policy
enforcement on the NGFW or Prisma Access deployment as long
as you associate the Application-Tagging
snippet and apply tags while in the
Application-Tagging configuration scope.
Tag GenAI Apps in the Application Config
Apply tags to the application to reflect whether a GenAI app is approved within your
organization from the Application config in Strata Cloud Manager.
- Log in to Strata Cloud Manager.Associate the predefined Application-Tagging snippet with appropriate Configuration Scope to support tag-based policy enforcement.Obtain the child App-IDs you want to tag.You can obtain the child App-IDs for a GenAI app using one of the following ways.
- Use the AI Access Security Insights dashboard to discover risks posed by GenAI apps. AI Access Security Insights shows you the detected child App-IDs used across your organization.
- Review the list of supported GenAI apps.
- Use Applipedia to search for the child App-IDs of supported GenAI apps delivered through a dynamic content update.Applipedia only displays App-IDs for apps delivered through a dynamic content, and doesn't display apps delivered through App-ID Cloud Engine (ACE).
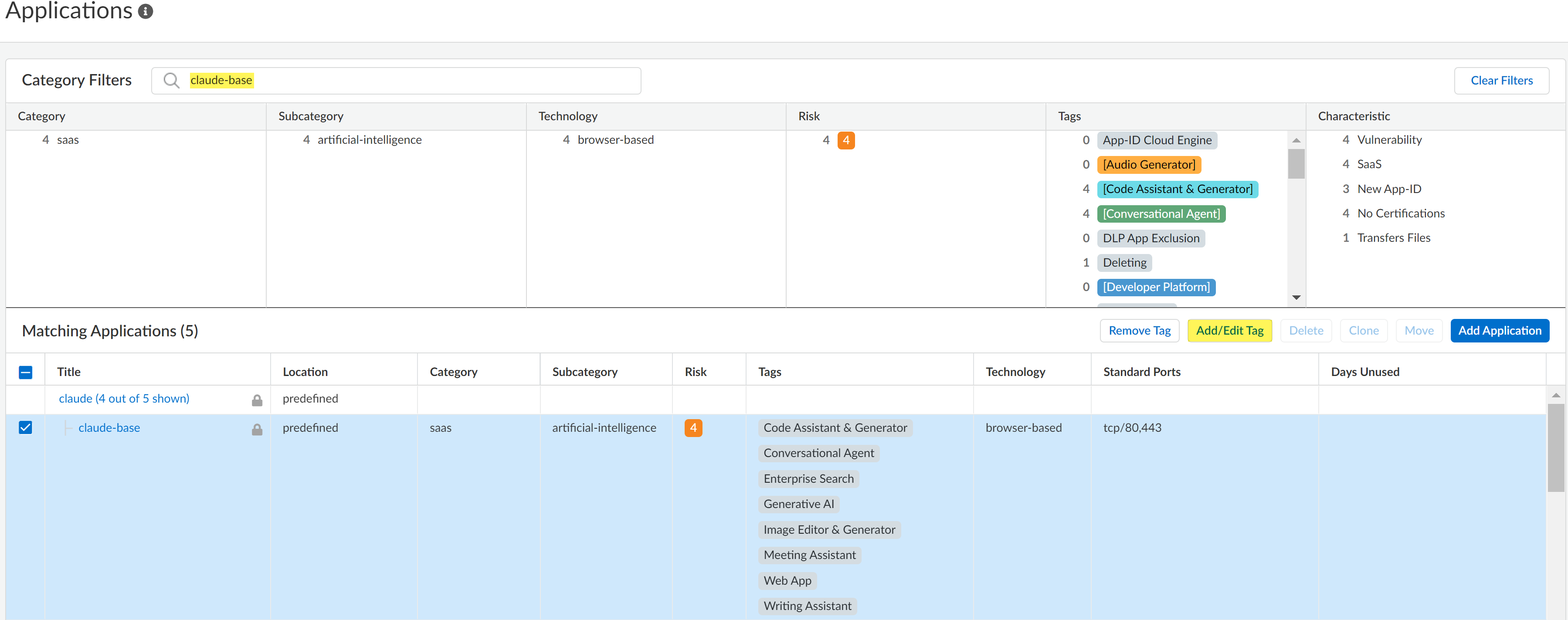
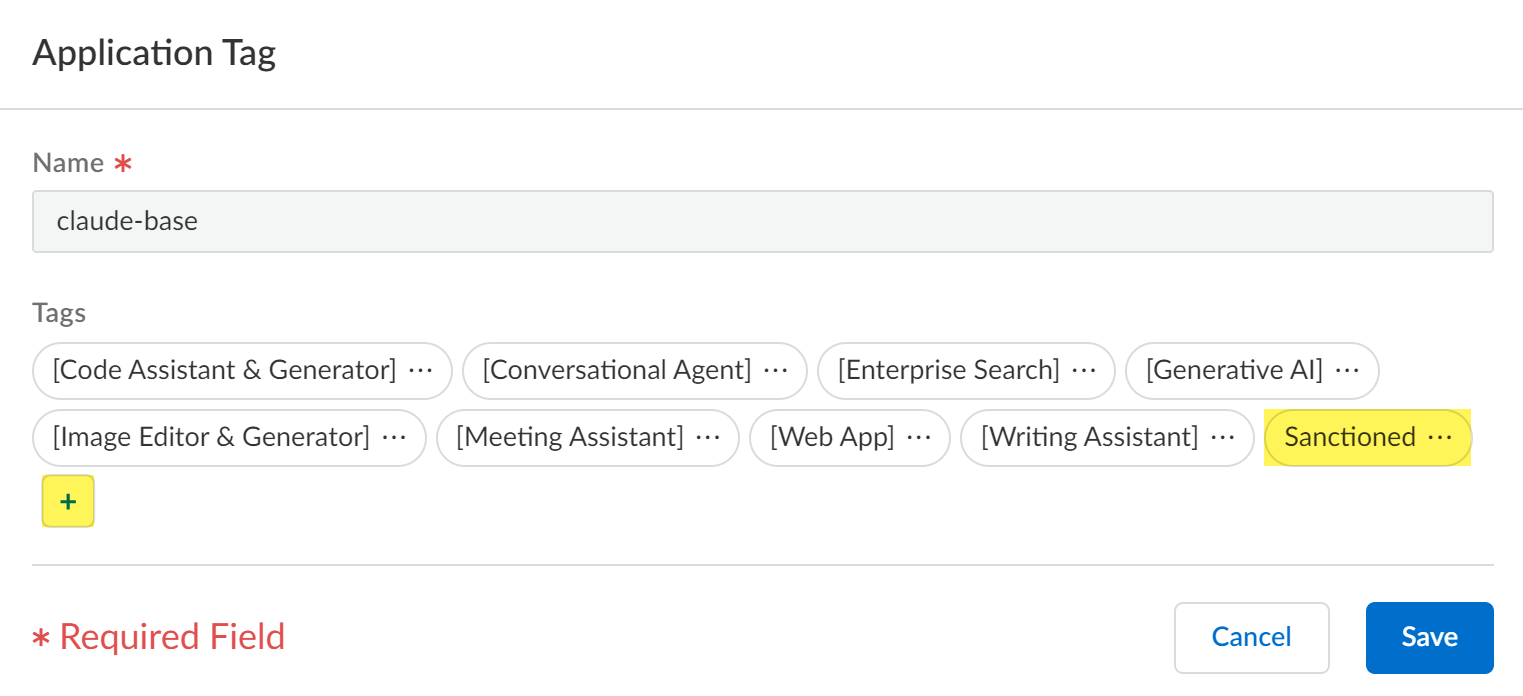
Select ConfigurationNGFW and Prisma AccessObjectsApplicationApplications.In the Configuration Scope, select the Application-Tagging snippet.If you are tagging an App-ID delivered through App-ID Cloud Engine (ACE), then all NGFW or Prisma Access tenants associated with the selected folder must be configured to receive App-ID updates from ACE.ACE is enabled by default for a NGFW or Prisma Access tenant when they have an active SaaS Security Inline or AI Access Security license. You can also manually enable ACE for your NGFW.The configuration push fails if you tag an App-ID delivered from ACE and at least one NGFW or Prisma Access tenant associated with the selected folder isn't configured to receive App-IDs from ACE.For this reason, Palo Alto Networks doesn't recommend selecting the Global Configuration Scope.In the Category Filters search field, enter the App-ID you want to tag and select it.You can only tag one App-ID at a time.Add/Edit Tag.![]() Click + to apply a predefined Sanctioned or Tolerated application tag.In this example, the claude-base App-ID is tagged with the Sanctioned tag.An app is assumed as Unsanctioned in the absence of the Sanctioned or Tolerated tags if tagging from Applications.If you want to change the app tag from Sanctioned or Tolerated to Unsanctioned, you need to remove the existing tag. You can't manually tag an app as Unsanctioned from Applications.Save.
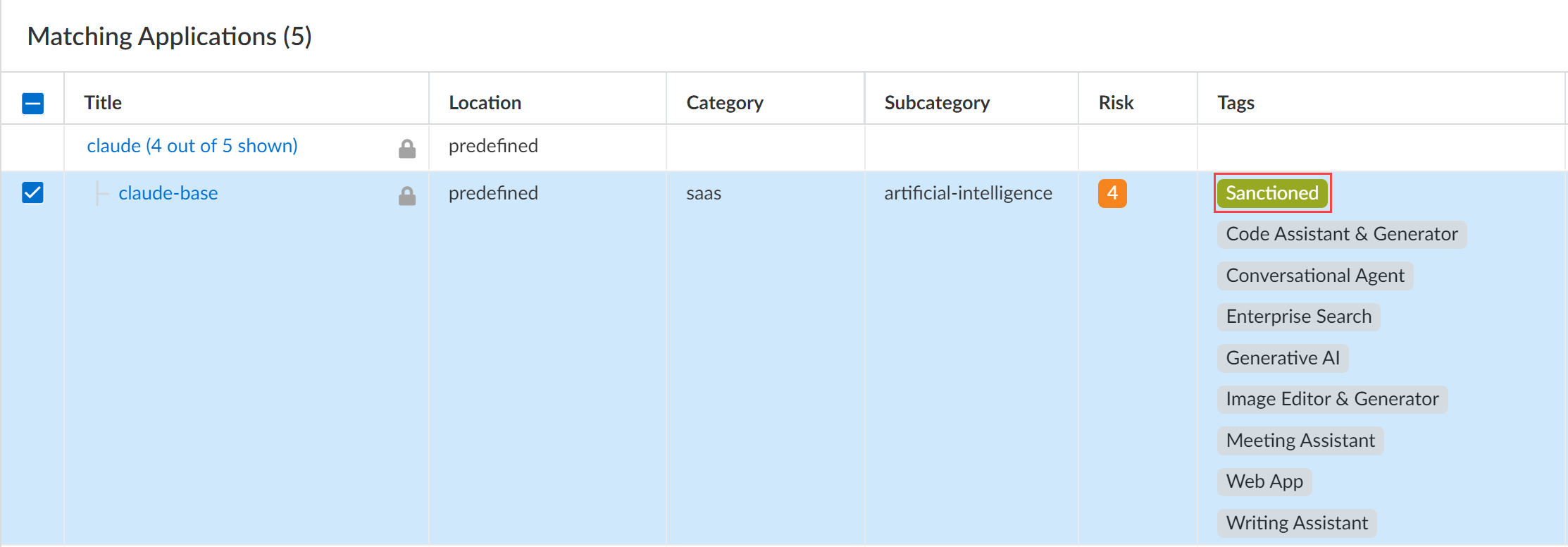
Click + to apply a predefined Sanctioned or Tolerated application tag.In this example, the claude-base App-ID is tagged with the Sanctioned tag.An app is assumed as Unsanctioned in the absence of the Sanctioned or Tolerated tags if tagging from Applications.If you want to change the app tag from Sanctioned or Tolerated to Unsanctioned, you need to remove the existing tag. You can't manually tag an app as Unsanctioned from Applications.Save.![]() Review the values in the Tag column to verify you successfully applied the application tag.
Review the values in the Tag column to verify you successfully applied the application tag.![]() Click Overview.Push Config and Push your configuration changes.
Click Overview.Push Config and Push your configuration changes.Tag GenAI Apps in the Insights Dashboard
Apply tags to the application to reflect whether the GenAI app is approved within your organization from the Insights dashboard in Strata Cloud Manager.- Log in to Strata Cloud Manager.Associate the predefined Application-Tagging snippet with appropriate Configuration Scope to support tag-based policy enforcement.Obtain the child App-IDs you want to tag.You can obtain the child App-IDs for a GenAI app using one of the following ways.
- Use the AI Access Security Insights dashboard to discover risks posed by GenAI apps. AI Access Security Insights shows you the detected child App-IDs used across your organization.
- Review the list of supported GenAI apps.
- Use Applipedia to search for the child App-IDs of supported GenAI apps delivered through a dynamic content update.Applipedia only displays App-IDs for apps delivered through a dynamic content, and doesn't display apps delivered through App-ID Cloud Engine (ACE).
Select InsightsActivity InsightsApplications.Locate the GenAI child App-ID you want to tag. If necessary, you can filter the table to show only the GenAI applications.- Add Filter and add the GenAI Application filter.Set the GenAI Application filter to TRUE.To review the tags that are applied to the GenAI App-ID, examine the values in the Tag column.Apply a different tag to the child GenAI App-ID.
- In the Actions column, select the tag icon and choose the Sanctioned, Tolerated, or Unsanctioned tag.Apply the new tag.