Equipment ID Security in a 5G Network
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- Automatic Content Updates Through Offline Panorama
- Enhanced Authentication for Dedicated Log Collectors and WildFire Appliances
- Syslog Forwarding Using Ethernet Interfaces
- Increased Configuration Size for Panorama
- Access Domain Enhancements for Multi-Tenancy
- Enhanced Performance for Panorama Query and Reporting
- Log Query Debugging
- Configurable Key Limits in Scheduled Reports
- Multiple Plugin Support for Panorama
End-of-Life (EoL)
Equipment ID Security in a 5G Network
Secure your 5G traffic with Security policy rules that
specify source equipment identifiers.
Detection of threats in 5G mobile networks
requires identification of compromised equipment and devices. Prevention
requires the ability to apply network security based on equipment
ID, which is a Permanent Equipment Identifier (PEI) including
International Mobile Equipment Identity (IMEI).
You can now
apply network security based on the equipment identity of any device
or equipment that is trying to access your 5G network. Security
policy rules and correlation based on 5G PEI including IMEI are
supported on:
- PA-7000 Series firewalls that use the PA-7000-100G-NPC-A, the PA-7050-SMC-B or PA-7080-SMC-B card, and the PA-7000-LFC card (the firewall must use all three cards)
- PA-5200 Series firewalls
- VM-700, VM-500, VM-300, and VM-100 firewalls
When
deciding which firewall model to purchase, consider the total number
of 3G, 4G, and 5G network identifiers (Subscriber IDs and Equipment
IDs) you need to include as external dynamic list (EDL) entries
or static entries. Each firewall model supports a number of EDL entries and static
entries.
- Enable GTP Security, commit your changes, and reboot.Enable inspection of 5G HTTP/2 control packets and content inspection of GTP-U packets; create a Mobile Network Protection profile.
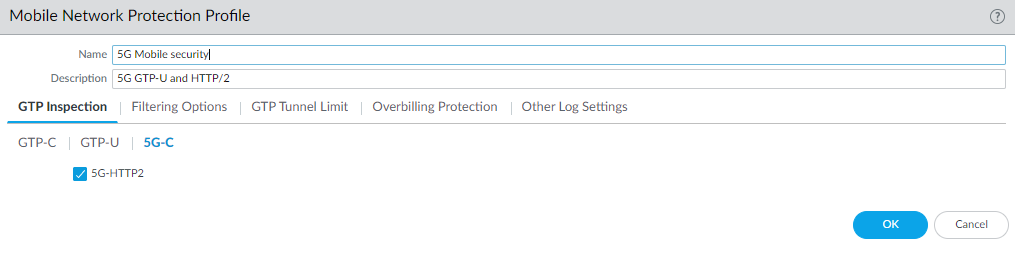
- Select ObjectsSecurity ProfilesMobile Network Protection.Add a profile by Name, such as 5G Mobile security.On the GTP Inspection tab, select 5G-C.Enable 5G-HTTP2 to enable inspection of 5G HTTP/2 control packets.
![]() Select GTP-U and enable GTP-U Content Inspection.Click OK.Create address objects for the IP addresses assigned to the network elements in your topology, such as the AMF on the N11 interface, the gNB on the N3 interface, the SMF on the N11 interface, and the UPF on the N3 interface.(Optional) Create an External Dynamic List (EDL) of Type Equipment Identity List; the Source of the list provides access to a server that provides identifiers of devices connected to the 5G network for which you want to allow (or deny) traffic.Create a Security policy rule that applies your Mobile Network Protection profile to application traffic.
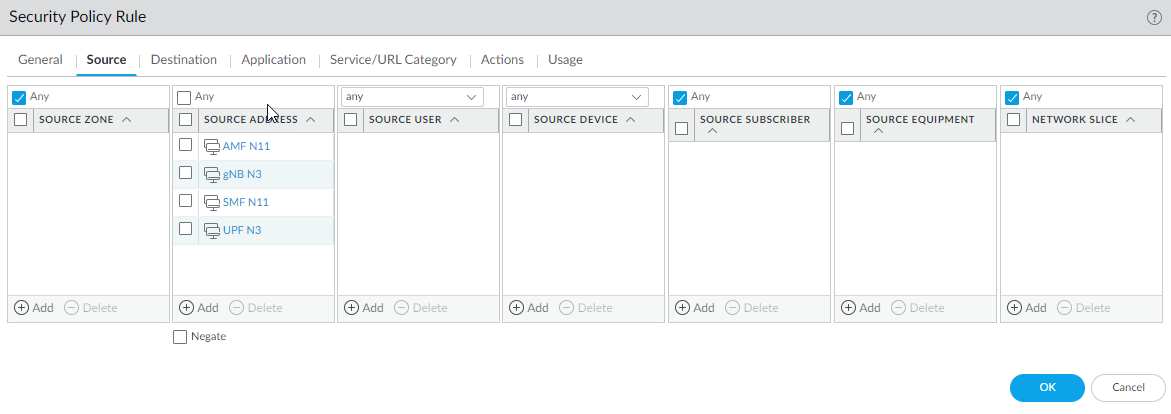
Select GTP-U and enable GTP-U Content Inspection.Click OK.Create address objects for the IP addresses assigned to the network elements in your topology, such as the AMF on the N11 interface, the gNB on the N3 interface, the SMF on the N11 interface, and the UPF on the N3 interface.(Optional) Create an External Dynamic List (EDL) of Type Equipment Identity List; the Source of the list provides access to a server that provides identifiers of devices connected to the 5G network for which you want to allow (or deny) traffic.Create a Security policy rule that applies your Mobile Network Protection profile to application traffic.- Select PoliciesSecurity and Add a Security policy rule.For Source Address, Add the address objects for the 5G element endpoints on the N3 and N11 interfaces that you want to allow.
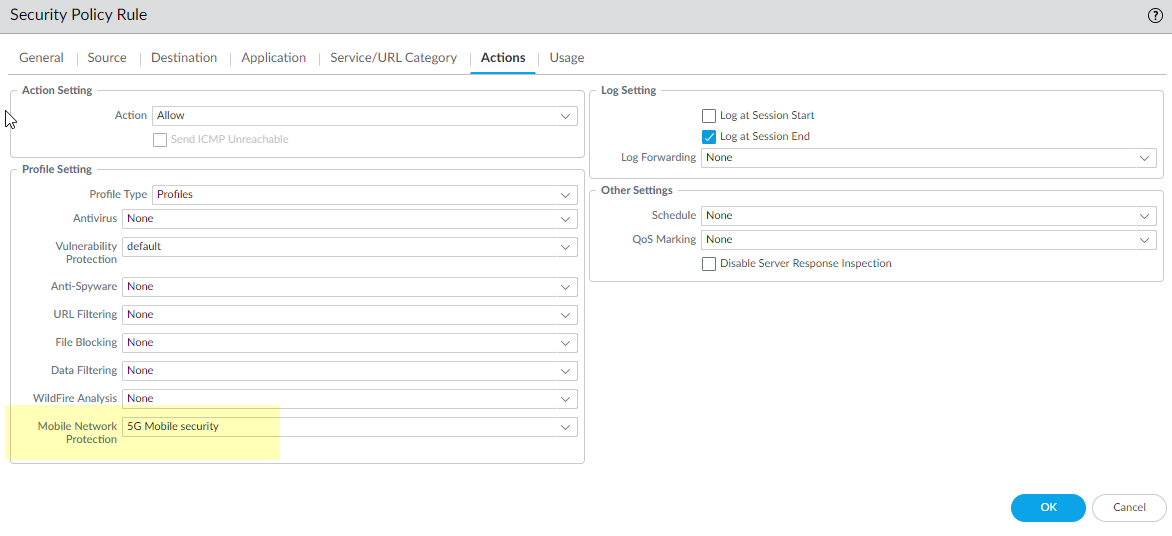
![]() For Destination, Add the Destination Address address objects for the 5G element endpoints on the N3 and N11 interfaces that you want to allow.Add the Applications to allow, such as the user plane, which is gtp-u, and web-browsing, which has HTTP/2.On the Actions tab, select the Action, such as Allow.Select the Mobile Network Protection profile you created.
For Destination, Add the Destination Address address objects for the 5G element endpoints on the N3 and N11 interfaces that you want to allow.Add the Applications to allow, such as the user plane, which is gtp-u, and web-browsing, which has HTTP/2.On the Actions tab, select the Action, such as Allow.Select the Mobile Network Protection profile you created.![]() Click OK.Create another Security policy rule based on Equipment ID.
Click OK.Create another Security policy rule based on Equipment ID.- Select PoliciesSecurity and Add a Security policy rule by Name, such as Equipment ID Security.Select Source tab and Add a Source Zone or select Any zone.Add one or more Source Equipment IDs in any of the following formats (if you configured an EDL, specify that EDL in this step):
- 5G Permanent Equipment Identifier (PEI) including IMEI
- IMEI (15 or 16 digits)
- IMEI prefix of eight digits for Type Allocation Code (TAC)
- EDL that specifies IMEIs
![]() Specify destinations.Add the Applications to allow, such as ssh, ssl, radmin, and telnet.On the Actions tab, select the Action, such as Allow.Click OK.Commit your changes.
Specify destinations.Add the Applications to allow, such as ssh, ssl, radmin, and telnet.On the Actions tab, select the Action, such as Allow.Click OK.Commit your changes.