ECMP Strict Source Path
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- Automatic Content Updates Through Offline Panorama
- Enhanced Authentication for Dedicated Log Collectors and WildFire Appliances
- Syslog Forwarding Using Ethernet Interfaces
- Increased Configuration Size for Panorama
- Access Domain Enhancements for Multi-Tenancy
- Enhanced Performance for Panorama Query and Reporting
- Log Query Debugging
- Configurable Key Limits in Scheduled Reports
- Multiple Plugin Support for Panorama
End-of-Life (EoL)
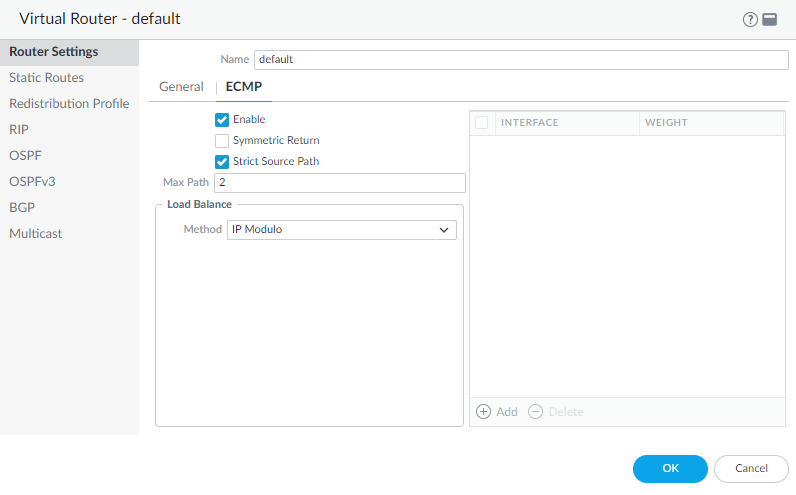
ECMP Strict Source Path
Enable ECMP Strict Source Path when ECMP load balancing
can interfere with an ISP verifying an expected source IP address.
When you Configure ECMP on a virtual router,
IKE and IPSec traffic originating at the firewall by
default egresses an interface that the ECMP load-balancing method
determines. This can be an issue when the firewall has more than
one ISP providing equal-cost paths to the same destination. ISPs
typically perform a Reverse Path Forwarding (RPF) check to confirm
that the traffic is egressing the same interface on which it arrived. Because
ECMP would choose an egress interface based on the load balancing
method, that wouldn’t be the interface that the ISP expects and
the ISP could block legitimate return traffic.
To avoid this
issue, you can now ensure that IKE and IPSec traffic originating
at the firewall always egresses the physical interface to which
the source IP address of the IPSec tunnel belongs by enabling Strict
Source Path.
- Select NetworkVirtual Routers and select a virtual router.Select Router SettingsECMP.Enable ECMP.Enable Strict Source Path.
![]() Click OK.Commit.
Click OK.Commit.