Network Slice Security in a 5G Network
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- Automatic Content Updates Through Offline Panorama
- Enhanced Authentication for Dedicated Log Collectors and WildFire Appliances
- Syslog Forwarding Using Ethernet Interfaces
- Increased Configuration Size for Panorama
- Access Domain Enhancements for Multi-Tenancy
- Enhanced Performance for Panorama Query and Reporting
- Log Query Debugging
- Configurable Key Limits in Scheduled Reports
- Multiple Plugin Support for Panorama
End-of-Life (EoL)
Network Slice Security in a 5G Network
Secure a 5G network slice by configuring Security policy
rules with source network slice SST names (standardized or operator-specific).
Network operators need tools to investigate
security events related to enterprises and industry verticals served
by network slices in a fifth generation (5G) cellular wireless network.
A network slice comprises dedicated, shared, or both types of resources
(for example, processing power, storage, and bandwidth), and has
isolation from other network slices.
You can now apply network
security based on network Slice/Service Type (SST). 5G network functions
communicate with each other using the HTTP/2 protocol over service-based
interfaces. Traffic from User Equipment (UE) and IoT devices is
carried in GTP-U tunnels in the 5G network.
The Security policy
rules for 5G network slice are based
on Network SST in two categories—standardized and operator-specific:
- Network Slice SST - Standardized—Three predefined slices,
which PAN-OS® delivers to you in dynamic content updates:
- eMBB (enhanced Mobile Broadband)—For faster speeds and high data rates, such as video streaming.
- URLLC (Ultra-Reliable Low-Latency Communication)—For mission-critical applications that are sensitive to latency, such as applications for health care, wireless payments, home control, and vehicle communication.
- MIoT (Massive Internet of Things)—For IoT traffic, such as smart metering, smart waste management, anti-theft, asset management, and location tracking.
- Network Slice SST—Operator-specific—You determine the name for and specify the slice.
You can apply the following security
per network slice or per group of network slices: application control,
Antivirus, Anti-Spyware, URL filtering, intrusion prevention, and
advanced threat prevention with WildFire®. You can see
the Network Slice ID SST in traffic, threat, URL filtering, and
WildFire submissions as well as in data filtering, GTP, and unified
logs; and you can see the Network Slice ID SD in traffic, GTP, and
unified logs to help you investigate a security event related to
the enterprise or customer.
Security policy rules and correlation
based on 5G Network Slice are supported on the following firewalls:
- PA-7000 Series firewalls that use the following three cards:
- The PA-7000-100G-NPC
- The PA-7050-SMC-B card or the PA-7080-SMC-B card
- The PA-7000-LFC card
- PA-5200 Series firewalls
- VM-700, VM-500, VM-300, and VM-100 firewalls
- Enable GTP Security, Commit, and reboot.Enable inspection of 5G HTTP/2 control packets; create a Mobile Network Protection profile.
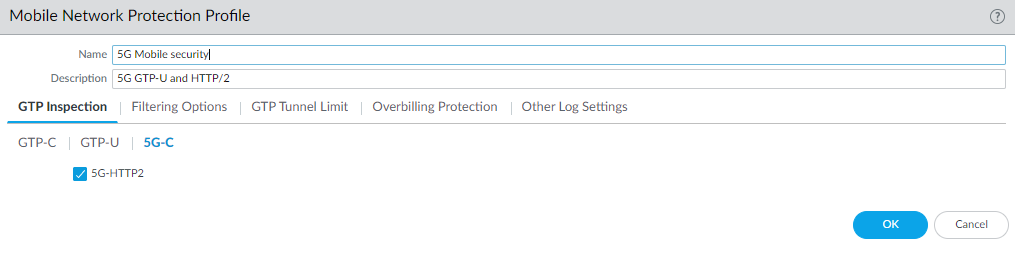
- Select ObjectsSecurity ProfilesMobile Network Protection and add a profile by Name.On the GTP Inspection tab, select 5G-C.Enable 5G-HTTP2 to enable inspection of 5G HTTP/2 control packets.
![]() Select GTP-U and enable GTP-U Content Inspection.Click OK.Create address objects for the IP addresses assigned to the network elements in your topology, such as the AMF on the N11 interface, the gNB on the N3 interface, the SMF on the N11 interface, and the UPF on the N3 interface.Create a Security policy rule that applies your Mobile Network Protection profile to application traffic.
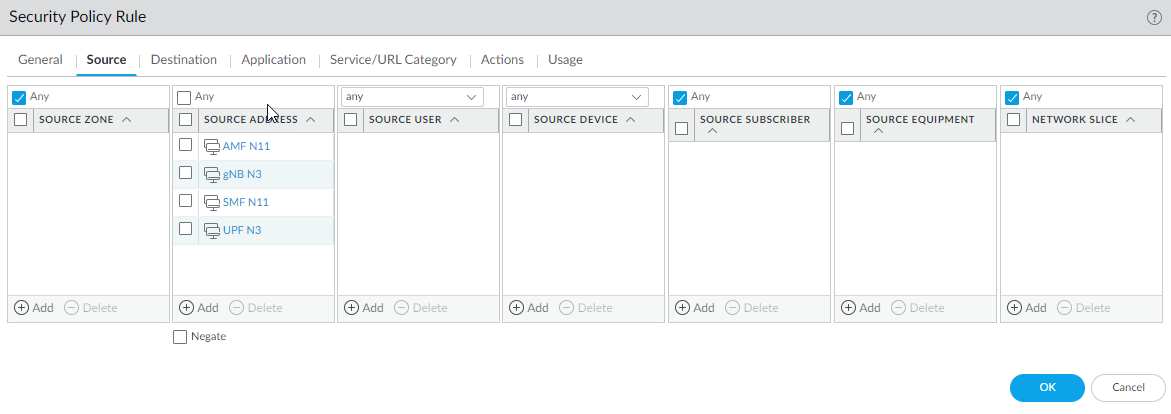
Select GTP-U and enable GTP-U Content Inspection.Click OK.Create address objects for the IP addresses assigned to the network elements in your topology, such as the AMF on the N11 interface, the gNB on the N3 interface, the SMF on the N11 interface, and the UPF on the N3 interface.Create a Security policy rule that applies your Mobile Network Protection profile to application traffic.- Select PoliciesSecurity and Add a Security policy rule.For Source Address, Add the address objects for the 5G element endpoints on the N3 and N11 interfaces that you want to allow.
![]() For Destination, Add the Destination Address objects for the 5G element endpoints on the N3 and N11 interfaces that you want to allow.Add the Applications to allow, such as the user plane, which is gtp-u, and web-browsing, which has HTTP/2.On the Actions tab, select the Action, such as Allow.Select the Mobile Network Protection profile you created.
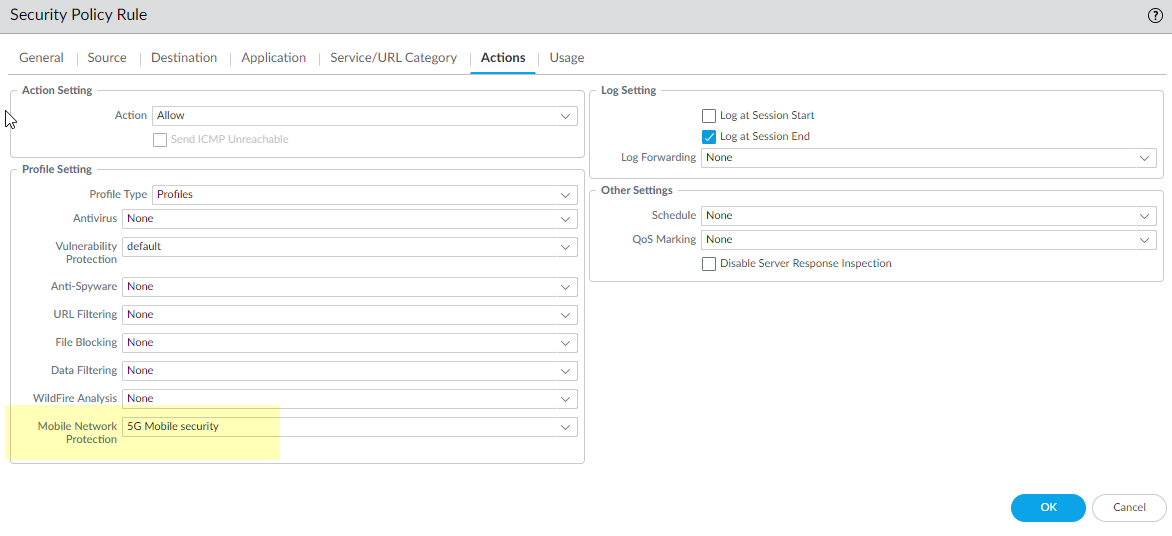
For Destination, Add the Destination Address objects for the 5G element endpoints on the N3 and N11 interfaces that you want to allow.Add the Applications to allow, such as the user plane, which is gtp-u, and web-browsing, which has HTTP/2.On the Actions tab, select the Action, such as Allow.Select the Mobile Network Protection profile you created.![]() Click OK.Create another Security policy rule based on Network Slices to allow, for example, applications for a standardized or operator-specific SST.
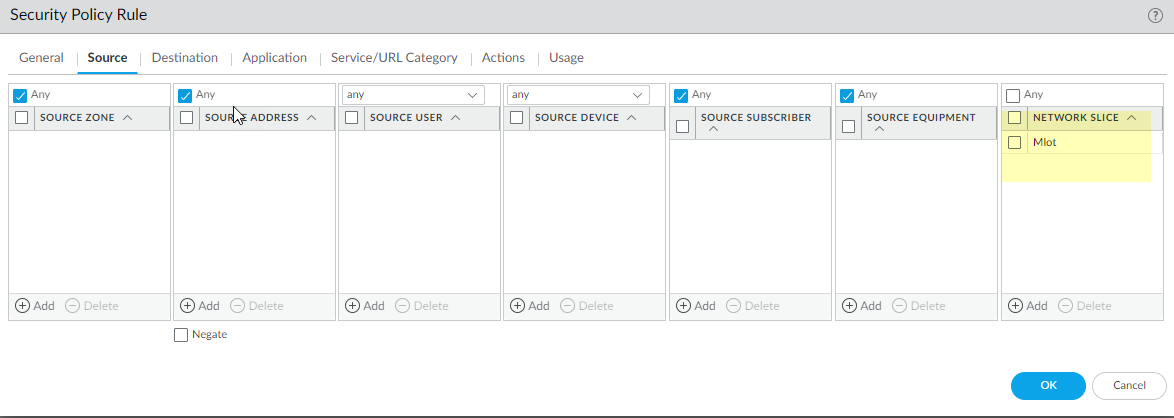
Click OK.Create another Security policy rule based on Network Slices to allow, for example, applications for a standardized or operator-specific SST.- Select PoliciesSecurity and Add a Security policy rule by Name.Select Source and Add one or more Network Slices in either of the following formats:
- Standardized SST (select eMBB, MIoT, or URLLC).
- Operator-specific SSTs in the format of text,number (number range is 128 to 255 in decimal).
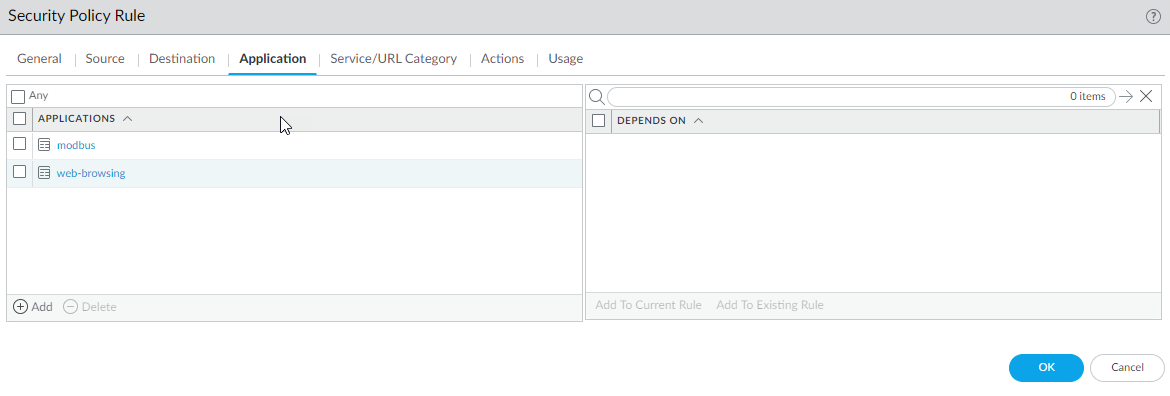
![]() Specify Source Zone, Source Address, Source User, and Source Device or use the default Any setting for each.Specify Destination Zone, Destination Address, and Destination Device or use the default Any setting for each.For Applications, select, for example, modbus and web-browsing.
Specify Source Zone, Source Address, Source User, and Source Device or use the default Any setting for each.Specify Destination Zone, Destination Address, and Destination Device or use the default Any setting for each.For Applications, select, for example, modbus and web-browsing.![]() On the Actions tab, select the Action, such as Allow.Select profiles you want to apply, such as Antivirus, Vulnerability Protection, Anti-Spyware, URL Filtering, File Blocking, and WildFire Analysis.Click OK.Commit your changes.
On the Actions tab, select the Action, such as Allow.Select profiles you want to apply, such as Antivirus, Vulnerability Protection, Anti-Spyware, URL Filtering, File Blocking, and WildFire Analysis.Click OK.Commit your changes.