Best Practices for Content Updates—Mission-Critical
Table of Contents
11.0 (EoL)
Expand all | Collapse all
-
-
- Upgrade Panorama with an Internet Connection
- Upgrade Panorama Without an Internet Connection
- Install Content Updates Automatically for Panorama without an Internet Connection
- Upgrade Panorama in an HA Configuration
- Migrate Panorama Logs to the New Log Format
- Upgrade Panorama for Increased Device Management Capacity
- Upgrade Panorama and Managed Devices in FIPS-CC Mode
- Downgrade from Panorama 11.0
- Troubleshoot Your Panorama Upgrade
-
- What Updates Can Panorama Push to Other Devices?
- Schedule a Content Update Using Panorama
- Panorama, Log Collector, Firewall, and WildFire Version Compatibility
- Upgrade Log Collectors When Panorama Is Internet-Connected
- Upgrade Log Collectors When Panorama Is Not Internet-Connected
- Upgrade a WildFire Cluster from Panorama with an Internet Connection
- Upgrade a WildFire Cluster from Panorama without an Internet Connection
- Upgrade Firewalls When Panorama Is Internet-Connected
- Upgrade Firewalls When Panorama Is Not Internet-Connected
- Upgrade a ZTP Firewall
- Revert Content Updates from Panorama
-
End-of-Life (EoL)
Best Practices for Content Updates—Mission-Critical
Follow these best practices to deploying content updates
in a mission-critical network, where application availability is
top priority.
The Best Practices for Applications and Threats Content Updates help to
ensure seamless policy enforcement as new application and threat
signatures are released. Follow these best practices to deploy content
updates in a mission-critical network, where you have zero
tolerance for application downtime.
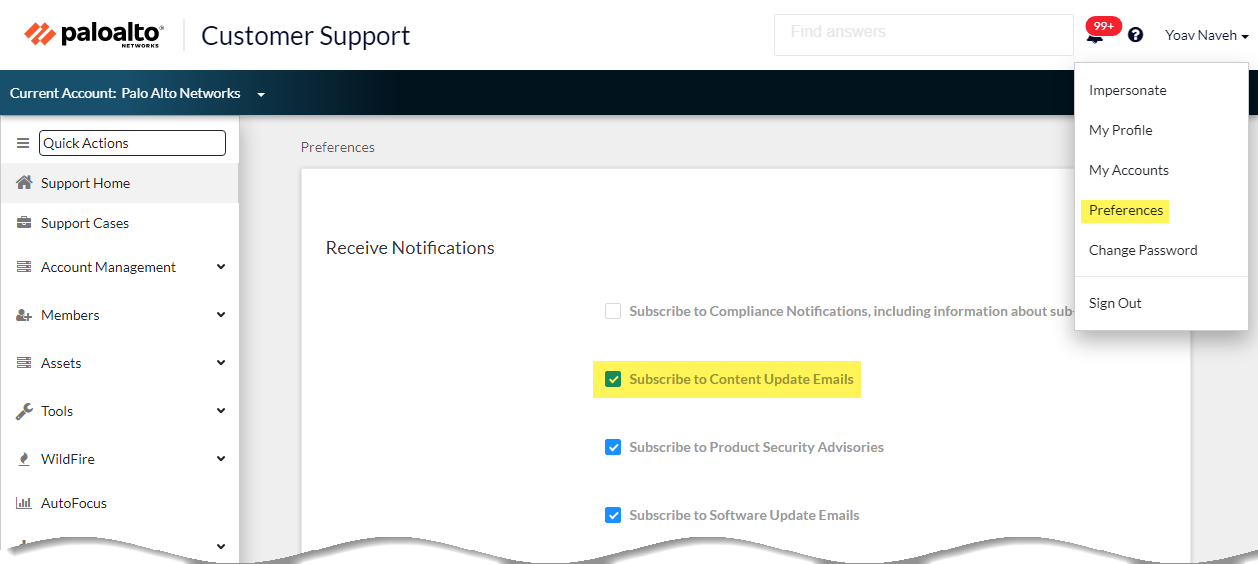
- Always review Content Release Notes for the list of newly-identified and modified application and threat signatures that the content release introduces. Content Release Notes also describe how the update might impact existing security policy enforcement and provides recommendations on how you can modify your security policy to best leverage what’s new.To subscribe to get notifications for new content updates, visit the Customer Support Portal, edit your Preferences, and select Subscribe to Content Update Emails.
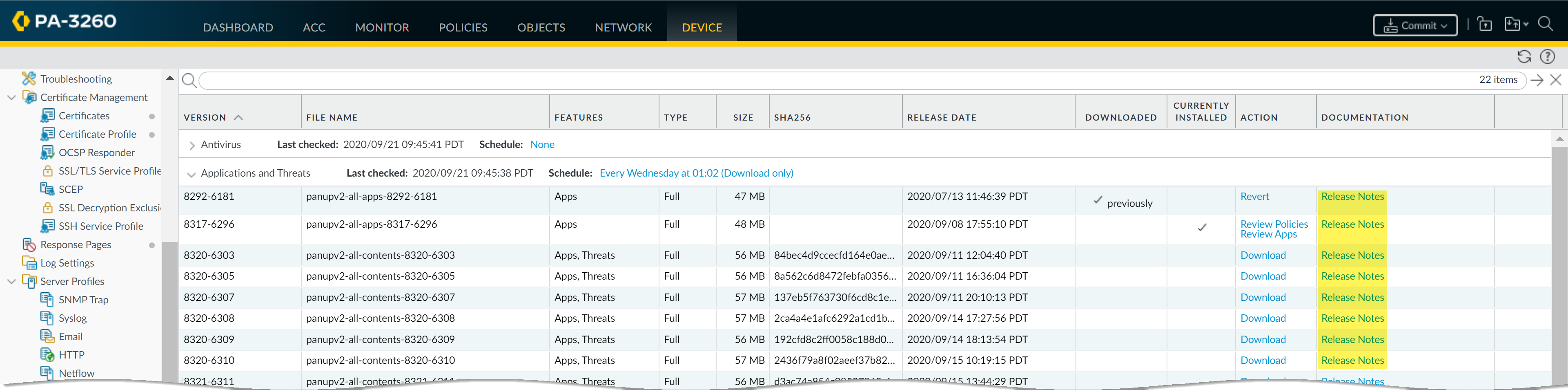
![]() You can also review Content Release Notes for apps and threats on the Palo Alto Networks Support Portal or directly in the firewall web interface: select DeviceDynamic Updates and open the Release Note for a specific content release version.
You can also review Content Release Notes for apps and threats on the Palo Alto Networks Support Portal or directly in the firewall web interface: select DeviceDynamic Updates and open the Release Note for a specific content release version.![]() The Notes section of Content Release Notes highlights future updates that Palo Alto Networks has identified as possibly significantly impacting coverage: for example, new App-IDs or decoders. Check for these future updates, so that you can account for any policy impact in advance of the release.
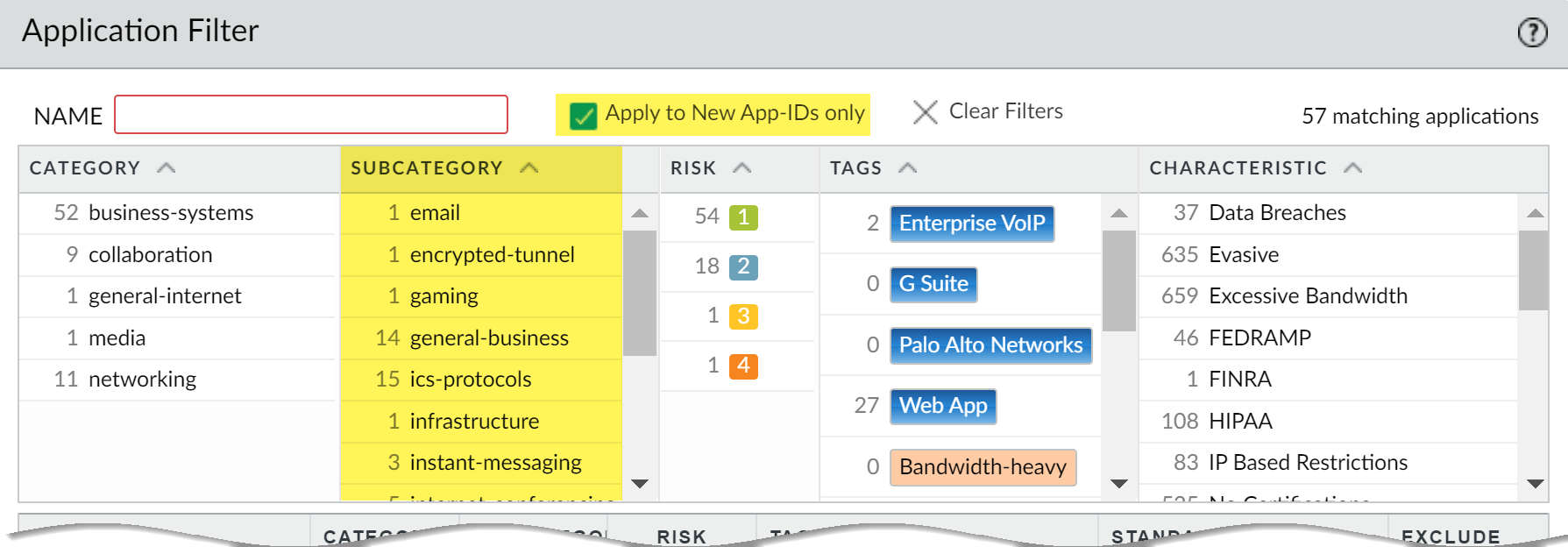
The Notes section of Content Release Notes highlights future updates that Palo Alto Networks has identified as possibly significantly impacting coverage: for example, new App-IDs or decoders. Check for these future updates, so that you can account for any policy impact in advance of the release. - Create a security policy rule to always allow certain categories of new App-IDs, like authentication or software development applications on which critical business functions rely. This means that when a content release introduces or changes coverage for an important business application, the firewall continues to seamlessly allow the application without requiring you to update your security policy. This eliminates any potential availability impact for App-IDs in critical categories, and gives you thirty days (new App-IDs are released on a monthly basis) to adjust your security policy to allow the mission-critical App-ID(s).To do this, create an application filter for new App-IDs in critical categories(Objects > Application Filters), and add the application filter to a security policy rule.
![]()
- To mitigate any impact to security policy enforcement that is associated with enabling new application and threat signatures, stagger the roll-out of new content. Provide new content to locations with less business risk (fewer users in satellite offices) before deploying them to locations with more business risk (such as locations with critical applications). Confining the latest content updates to certain firewalls before deploying them across your network also makes it easier to troubleshoot any issues that arise. You can use Panorama to push staggered schedules and installation thresholds to firewalls and device groups based on organization or location (Use Panorama to Deploy Updates to Firewalls).
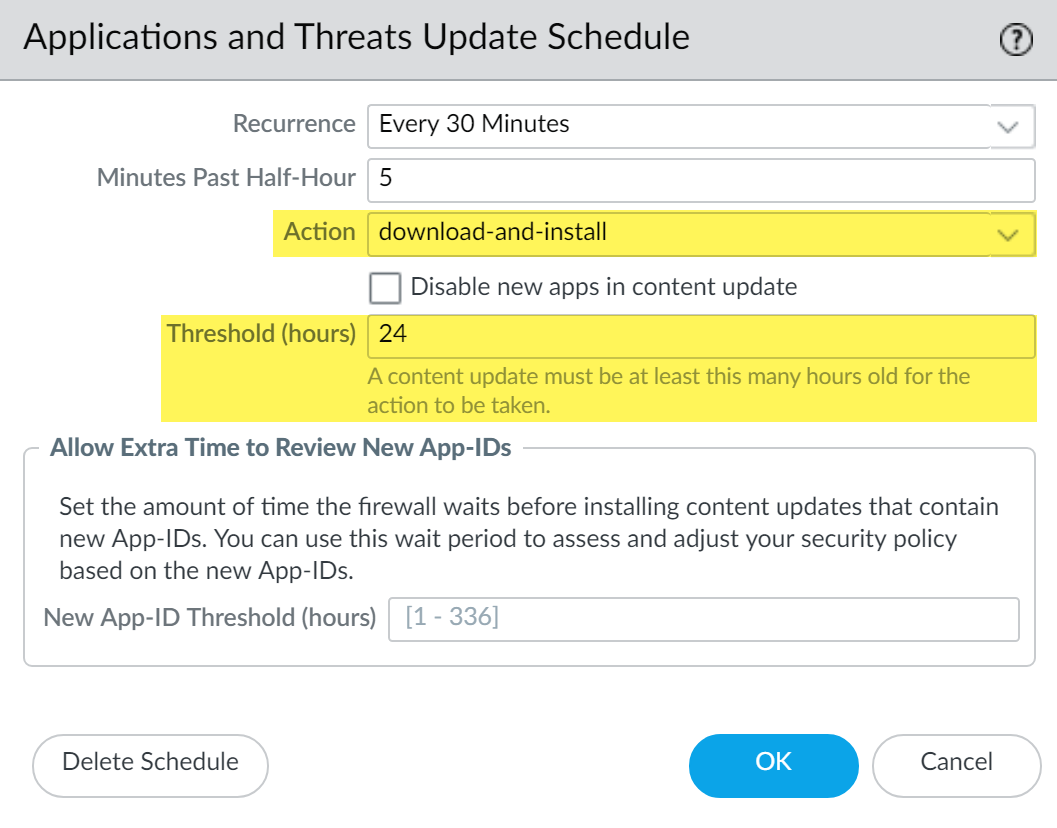
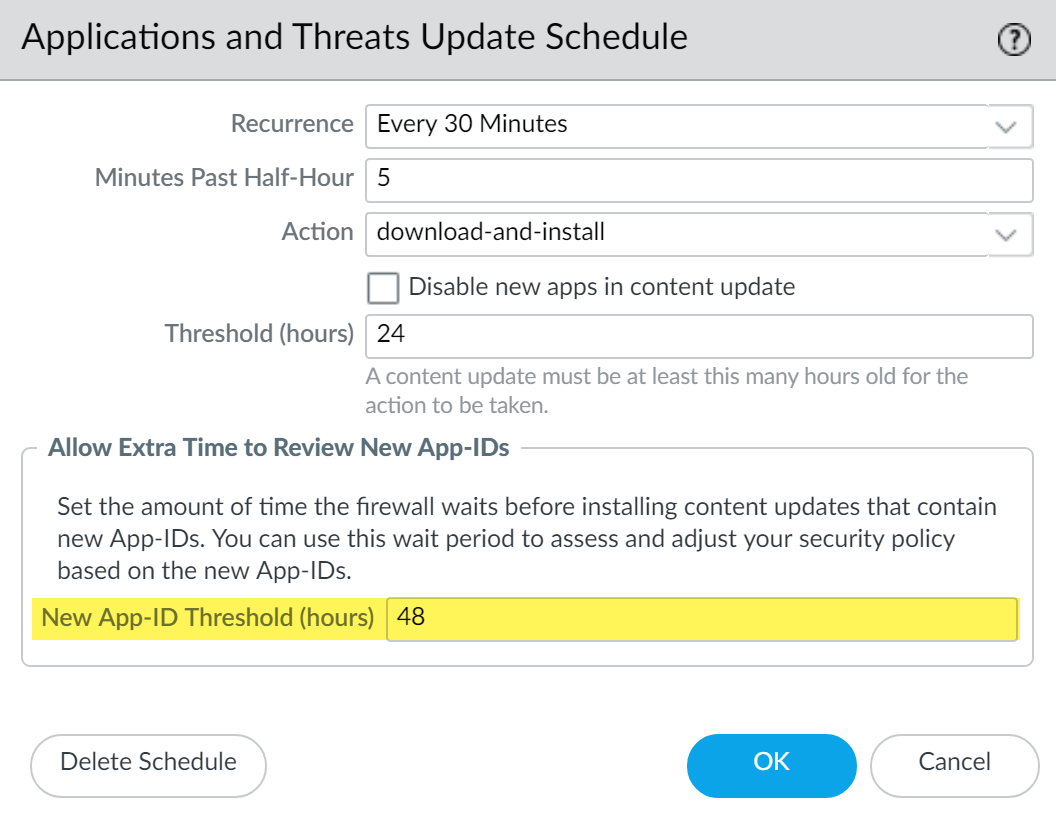
- Schedule content updates so that they download-and-install automatically. Then, set a Threshold that determines the amount of time the firewall waits before installing the latest content. In a mission-critical network, schedule up to a 48 hour threshold.
![]() The installation delay ensures that the firewall only installs content that has been available and functioning in customer environments for the specified amount of time. To schedule content updates, select DeviceDynamic UpdatesSchedule.
The installation delay ensures that the firewall only installs content that has been available and functioning in customer environments for the specified amount of time. To schedule content updates, select DeviceDynamic UpdatesSchedule. - Give yourself additional time to adjust your security policy based on new App-IDs before you install them. To do this, set an installation threshold that applies only to content updates that contain new App-IDs. Content updates with new App-IDs are released only once a month, and installation threshold triggers only at that time. Schedule content updates to configure a New App-ID Threshold (DeviceDynamic UpdatesSchedule).
![]()
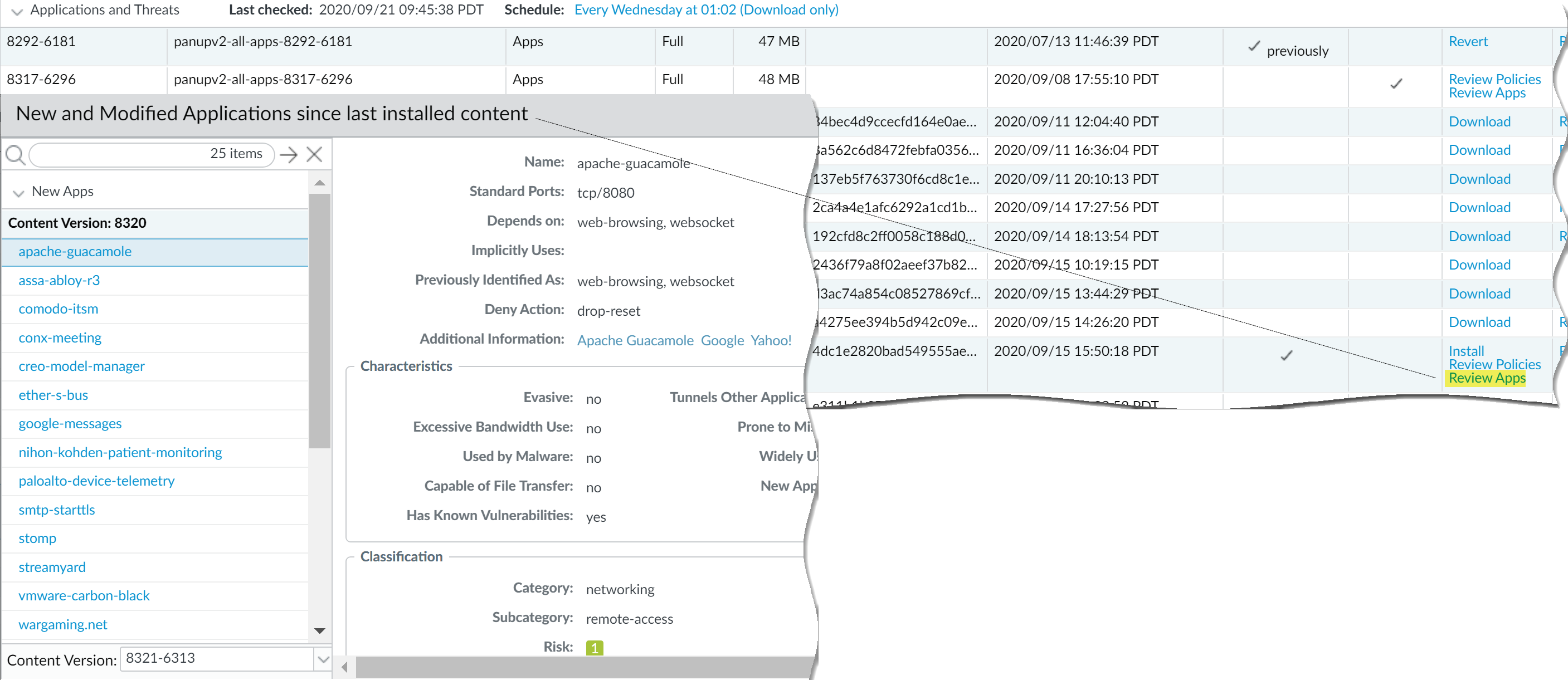
- Always review the new and modified App-IDs that a content release introduces, in order to assess how the changes might impact your security policy. The following topic describes the options you can use to update your security policy both before and after installing new App-IDs: Manage New and Modified App-IDs.
![]()
- Set up log forwarding to send Palo Alto Networks critical content alerts to external services that you use for monitoring network and firewall activity. This allows you to ensure that the appropriate personnel is notified about critical content issues, so that they can take action as needed. Critical content alerts are logged as system log entries with the following Type and Event: (subtype eq dynamic-updates) and (eventid eq palo-alto-networks-message).
![]() PAN-OS 8.1.2 changed the log type for critical content alerts from general to dynamic-updates. If you’re using PAN-OS 8.1.0 or PAN-OS 8.1.1, critical content are logged as system log entries with the following Type and Event, and you should set up forwarding for these alerts using the following filter: (subtype eq general) and (eventid eq palo-alto-networks-message).
PAN-OS 8.1.2 changed the log type for critical content alerts from general to dynamic-updates. If you’re using PAN-OS 8.1.0 or PAN-OS 8.1.1, critical content are logged as system log entries with the following Type and Event, and you should set up forwarding for these alerts using the following filter: (subtype eq general) and (eventid eq palo-alto-networks-message). - Test new Applications and Threats content updates in a dedicated staging environment before enabling them in your production environment. The easiest way to test new applications and threats is to use a test firewall to tap into production traffic. Install the latest content on the test firewall and monitor the firewall as it processes the traffic copied from your production environment. You can also use test clients and a test firewall or packet captures (PCAPs) to simulate production traffic. Using PCAPs works well to simulate traffic for diverse deployments where firewall security policy varies depending on location.