Advanced DNS Security Powered by Precision AI®
Create Domain Exceptions and Allow | Block Lists
Table of Contents
Create Domain Exceptions and Allow | Block Lists
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
DNS Security creates threat signatures for domains that have been analyzed by the
DNS Security service. For these known domains, the signatures are referenced when a DNS
query is received. In some cases, it might be possible that the signature has
incorrectly categorized a domain as a threat, due to certain features or qualities
present in the domain. In such circumstances, you can add signature exceptions to bypass
these false-positives.
If there are known safe domains that are categorized as malicious, such as
internal domains, you can add a list of domains that will bypass any DNS analysis. If
your organization uses third party threat feeds as part of a comprehensive threat
intelligence solution, you can also reference those in the form of external dynamic
lists (EDLs) in your DNS Security profile.
- You can specify up to a maximum of 100 DNS signature exceptions and 100 DNS domain/FQDN entries in an allow list. If you require an allow list with more than 100 domain/FQDN entries, you can reference an external dynamic list (EDL) in your DNS signature source set with a policy action of allow.
- Do not add UTIDs from 109,000,000 to 109,029,999 to the DNS Signature Exception list. These Universal Threat IDs represent malicious categories, not individual domains, unlike other threat signatures. The UTID number (seen as ID in the Threat logs) identifies the specific DNS detection method DNS Security uses for domain classification.
Create Domain Exceptions and Allow | Block Lists (Strata Cloud Manager)
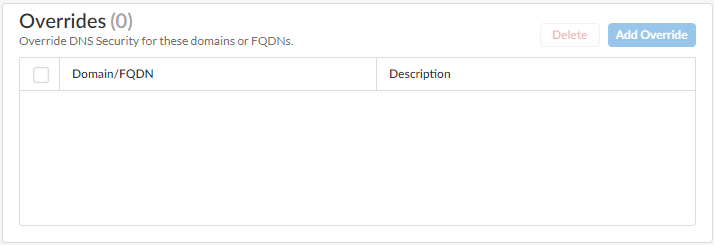
- Use the credentials associated with your Palo Alto Networks support account and log in to the Strata Cloud Manager on the hub.Add domain overrides in cases where false-positives occur.
- Select ConfigurationNGFW and Prisma AccessSecurity ServicesDNS Security and select a DNS Security profile to modify.Add Override or Delete to modify the domain list entries as necessary. Each additional entry requires the domain and a description.
![]() Click OK to save your modified DNS Security profile.Reference an external dynamic list (EDL) as part of your DNS Security profile to import third party threat feeds.
Click OK to save your modified DNS Security profile.Reference an external dynamic list (EDL) as part of your DNS Security profile to import third party threat feeds.- Create an domain-based external dynamic list (ConfigurationNGFW and Prisma AccessObjectsExternal Dynamic Lists). For more information about EDLs, see External Dynamic List.Select ConfigurationNGFW and Prisma AccessSecurity ServicesDNS Security.In the External Dynamic Lists panel, select a domain list EDL and provide the Policy Action and Packet Capture settings. In Apply to Profiles, select the DNS Security profile for which you want the EDL domain list to apply to.Save your changes when you have finished making your updates.
Create Domain Exceptions and Allow | Block Lists (NGFW (Managed by PAN-OS or Panorama))
PAN-OS 10.0 and later releases provide an additional option to explicitly add allowable domains through the Anti-Spyware security profile. You can add domain/FQDN entries for approved domain sources if they trigger a false-positive response from DNS Security.Create Domain Exceptions and Allow | Block Lists (PAN-OS 10.0 and later)
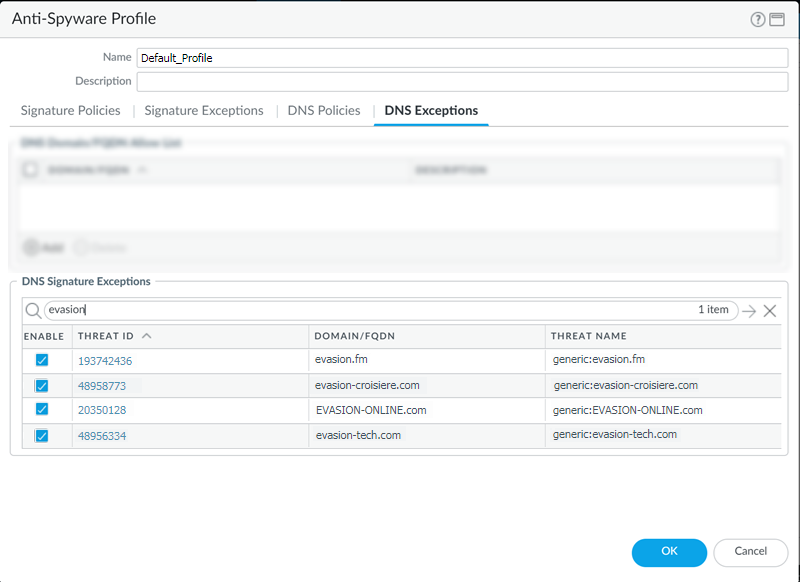
- Log in to the NGFW.Add domain signature exceptions in cases where false-positives occur.
- Select ObjectsSecurity ProfilesAnti-Spyware.Select a profile to modify.Add or modify the Anti-Spyware profile from which you want to exclude the threat signature, and select DNS Exceptions.Search for a DNS signature to exclude by entering the name or FQDN.Select the checkbox for each Threat ID of the DNS signature that you want to exclude from enforcement.
![]() Click OK to save your new or modified Anti-Spyware profile.Add an allow list to specify a list of DNS domains / FQDNs to be explicitly allowed.
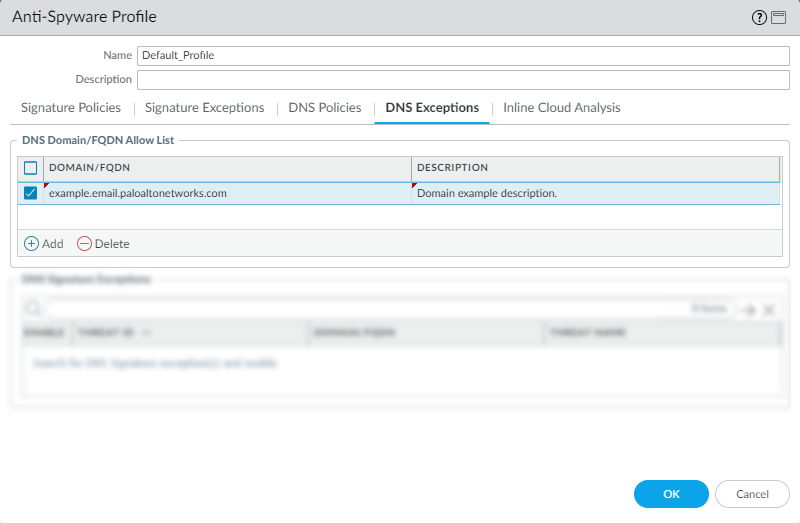
Click OK to save your new or modified Anti-Spyware profile.Add an allow list to specify a list of DNS domains / FQDNs to be explicitly allowed.- Select ObjectsSecurity ProfilesAnti-Spyware.Select a profile to modify.Add or modify the Anti-Spyware profile from which you want to exclude the threat signature, and select DNS Exceptions.To Add a new FQDN allow list entry, provide the DNS domain or FQDN location and a description.
![]() Click OK to save your new or modified Anti-Spyware profile.
Click OK to save your new or modified Anti-Spyware profile.Create Domain Exceptions and Allow | Block Lists (PAN-OS 9.1)
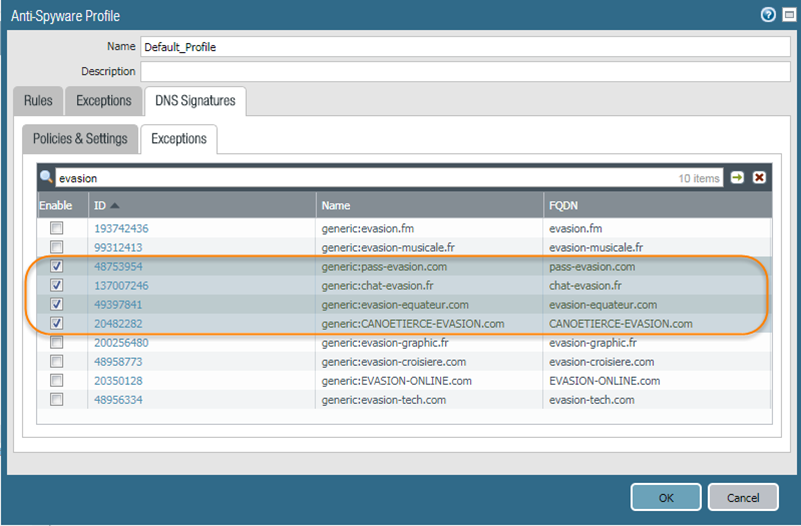
Allow and block lists are not available in PAN-OS 9.1.- Log in to the NGFW.Add domain signature exceptions in cases where false-positives occur.
- Select ObjectsSecurity ProfilesAnti-Spyware.Select a profile to modify.Add or modify the Anti-Spyware profile from which you want to exclude the threat signature, and select DNS Signatures > Exceptions.Search for a DNS signature to exclude by entering the name or FQDN.Select the DNS Threat ID for the DNS signature that you want to exclude from enforcement.
![]() Click OK to save your new or modified Anti-Spyware profile.
Click OK to save your new or modified Anti-Spyware profile.