Ethernet SGT Protection
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- Automatic Content Updates Through Offline Panorama
- Enhanced Authentication for Dedicated Log Collectors and WildFire Appliances
- Syslog Forwarding Using Ethernet Interfaces
- Increased Configuration Size for Panorama
- Access Domain Enhancements for Multi-Tenancy
- Enhanced Performance for Panorama Query and Reporting
- Log Query Debugging
- Configurable Key Limits in Scheduled Reports
- Multiple Plugin Support for Panorama
End-of-Life (EoL)
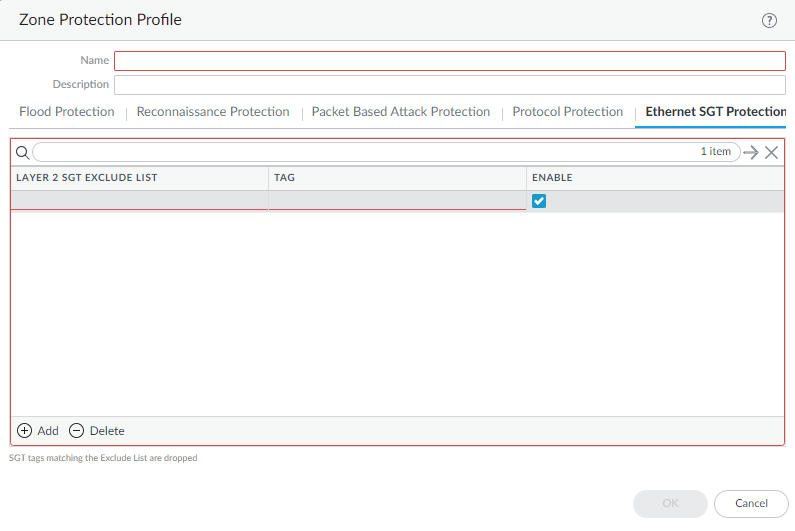
Ethernet SGT Protection
In a Cisco TrustSec network, employ Zone Protection based
on dropping packets that contain specific security group tags (SGT)
in the 802.1Q header.
In a Cisco TrustSec network, a Cisco Identity
Services Engine (ISE) assigns a Layer 2 Security Group Tag (SGT)
of 16 bits to a user’s or endpoint’s session. When your firewall
is part of a Cisco TrustSec network, the firewall needs to support
the TrustSec 802.1Q header to do content inspection. Without such
support, in a virtual wire topology the firewall can only pass SGT-tagged
packets without being able to inspect content. The firewall can
now inspect headers with 802.1Q (Ethertype 0x8909) for specified
SGT values and drop the packet if the SGT matches the list you configure
in the Zone Protection profile attached to a Layer2, virtual wire,
or tap interface.
- Create a Zone Protection profile to provide Ethernet SGT Protection.
- Select NetworkNetwork ProfilesZone Protection.Add a Zone Protection profile by Name.Select Ethernet SGT Protection.Add a Layer 2 SGT Exclude List by name.Enter one or more Tag values for the list; range is 0 to 65,535. You can enter individual entries that are a contiguous range of tag values (for example, 100-500). You can add up to 100 (individual or range) tag entries in an Exclude List.Enable the Layer 2 SGT Exclude List. You can disable the list at any time.Click OK.
![]() Apply the Zone Protection profile to the security zone to which the Layer 2, virtual wire, or tap interfaces belong.
Apply the Zone Protection profile to the security zone to which the Layer 2, virtual wire, or tap interfaces belong.- Select NetworkZones.Add a zone.Enter the Name of the zone.For Location, select the virtual system where the zone applies.For Type, select Layer2, Virtual Wire, or Tap.Add an Interface that belongs to the zone.For Zone Protection Profile, select the profile you created.Click OK.Commit.View the global counter of packets that the firewall dropped as a result of all Zone Protection profiles that employ Ethernet SGT Protection.
- Access the CLI.> show counter global name pan_flow_dos_l2_sec_tag_drop