Push a Policy Rule to a Subset of Firewalls
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- Determine Panorama Log Storage Requirements
-
- Setup Prerequisites for the Panorama Virtual Appliance
- Perform Initial Configuration of the Panorama Virtual Appliance
- Set Up The Panorama Virtual Appliance as a Log Collector
- Set Up the Panorama Virtual Appliance with Local Log Collector
- Set up a Panorama Virtual Appliance in Panorama Mode
- Set up a Panorama Virtual Appliance in Management Only Mode
-
- Preserve Existing Logs When Adding Storage on Panorama Virtual Appliance in Legacy Mode
- Add a Virtual Disk to Panorama on an ESXi Server
- Add a Virtual Disk to Panorama on vCloud Air
- Add a Virtual Disk to Panorama on Alibaba Cloud
- Add a Virtual Disk to Panorama on AWS
- Add a Virtual Disk to Panorama on Azure
- Add a Virtual Disk to Panorama on Google Cloud Platform
- Add a Virtual Disk to Panorama on Hyper-V
- Add a Virtual Disk to Panorama on KVM
- Add a Virtual Disk to Panorama on Oracle Cloud Infrastructure (OCI)
- Mount the Panorama ESXi Server to an NFS Datastore
-
- Increase CPUs and Memory for Panorama on an ESXi Server
- Increase CPUs and Memory for Panorama on vCloud Air
- Increase CPUs and Memory for Panorama on Alibaba Cloud
- Increase CPUs and Memory for Panorama on AWS
- Increase CPUs and Memory for Panorama on Azure
- Increase CPUs and Memory for Panorama on Google Cloud Platform
- Increase CPUs and Memory for Panorama on Hyper-V
- Increase CPUs and Memory for Panorama on KVM
- Increase CPUs and Memory for Panorama on Oracle Cloud Infrastructure (OCI)
- Complete the Panorama Virtual Appliance Setup
-
- Convert Your Evaluation Panorama to a Production Panorama with Local Log Collector
- Convert Your Evaluation Panorama to a Production Panorama without Local Log Collector
- Convert Your Evaluation Panorama to VM-Flex Licensing with Local Log Collector
- Convert Your Evaluation Panorama to VM-Flex Licensing without Local Log Collector
- Convert Your Production Panorama to an ELA Panorama
-
- Register Panorama
- Activate a Panorama Support License
- Activate/Retrieve a Firewall Management License when the Panorama Virtual Appliance is Internet-connected
- Activate/Retrieve a Firewall Management License when the Panorama Virtual Appliance is not Internet-connected
- Activate/Retrieve a Firewall Management License on the M-Series Appliance
- Install the Panorama Device Certificate
-
- Panorama, Log Collector, Firewall, and WildFire Version Compatibility
- Install Updates for Panorama in an HA Configuration
- Install Updates for Panorama with an Internet Connection
- Install Updates for Panorama When Not Internet-Connected
- Install Updates Automatically for Panorama without an Internet Connection
- Migrate Panorama Logs to the New Log Format
-
- Migrate from a Panorama Virtual Appliance to an M-Series Appliance
- Migrate a Panorama Virtual Appliance to a Different Hypervisor
- Migrate from an M-Series Appliance to a Panorama Virtual Appliance
- Migrate from an M-100 Appliance to an M-500 Appliance
- Migrate from an M-100 or M-500 Appliance to an M-200 or M-600 Appliance
-
- Configure an Admin Role Profile
- Configure an Access Domain
-
- Configure a Panorama Administrator Account
- Configure Local or External Authentication for Panorama Administrators
- Configure a Panorama Administrator with Certificate-Based Authentication for the Web Interface
- Configure an Administrator with SSH Key-Based Authentication for the CLI
- Configure RADIUS Authentication for Panorama Administrators
- Configure TACACS+ Authentication for Panorama Administrators
- Configure SAML Authentication for Panorama Administrators
-
- Add a Firewall as a Managed Device
-
- Add a Device Group
- Create a Device Group Hierarchy
- Create Objects for Use in Shared or Device Group Policy
- Revert to Inherited Object Values
- Manage Unused Shared Objects
- Manage Precedence of Inherited Objects
- Move or Clone a Policy Rule or Object to a Different Device Group
- Push a Policy Rule to a Subset of Firewalls
- Manage the Rule Hierarchy
- Manage the Master Key from Panorama
- Redistribute Data to Managed Firewalls
-
- Add Standalone WildFire Appliances to Manage with Panorama
- Remove a WildFire Appliance from Panorama Management
-
-
- Configure a Cluster and Add Nodes on Panorama
- Configure General Cluster Settings on Panorama
- Remove a Cluster from Panorama Management
- Configure Appliance-to-Appliance Encryption Using Predefined Certificates Centrally on Panorama
- Configure Appliance-to-Appliance Encryption Using Custom Certificates Centrally on Panorama
- View WildFire Cluster Status Using Panorama
- Upgrade a Cluster Centrally on Panorama with an Internet Connection
- Upgrade a Cluster Centrally on Panorama without an Internet Connection
-
-
- Manage Licenses on Firewalls Using Panorama
-
- Supported Updates
- Schedule a Content Update Using Panorama
- Upgrade Log Collectors When Panorama Is Internet-Connected
- Upgrade Log Collectors When Panorama Is Not Internet-Connected
- Upgrade Firewalls When Panorama Is Internet-Connected
- Upgrade Firewalls When Panorama Is Not Internet-Connected
- Upgrade a ZTP Firewall
- Revert Content Updates from Panorama
-
- Preview, Validate, or Commit Configuration Changes
- Enable Automated Commit Recovery
- Compare Changes in Panorama Configurations
- Manage Locks for Restricting Configuration Changes
- Add Custom Logos to Panorama
- Use the Panorama Task Manager
- Reboot or Shut Down Panorama
- Configure Panorama Password Profiles and Complexity
-
-
- Verify Panorama Port Usage
- Resolve Zero Log Storage for a Collector Group
- Replace a Failed Disk on an M-Series Appliance
- Replace the Virtual Disk on an ESXi Server
- Replace the Virtual Disk on vCloud Air
- Migrate Logs to a New M-Series Appliance in Log Collector Mode
- Migrate Logs to a New M-Series Appliance in Panorama Mode
- Migrate Logs to a New M-Series Appliance Model in Panorama Mode in High Availability
- Migrate Logs to the Same M-Series Appliance Model in Panorama Mode in High Availability
- Migrate Log Collectors after Failure/RMA of Non-HA Panorama
- Regenerate Metadata for M-Series Appliance RAID Pairs
- View Log Query Jobs
- Troubleshoot Commit Failures
- Troubleshoot Registration or Serial Number Errors
- Troubleshoot Reporting Errors
- Troubleshoot Device Management License Errors
- Troubleshoot Automatically Reverted Firewall Configurations
- Complete Content Update When Panorama HA Peer is Down
- View Task Success or Failure Status
- Downgrade from Panorama 10.0
End-of-Life (EoL)
Push a Policy Rule to a Subset of Firewalls
A policy target allows you to
specify the firewalls in a device group to which to push policy
rules. It allows you to exclude one or more firewalls or virtual
systems, or to apply a rule only to specific firewalls or virtual systems
in a device group.
As your rulebase evolves and you push new
or modified rules to firewalls, changes and audit information get
lost over time unless they are archived at the time the rule is
created or modified. Use the audit comment archive to view the audit
comment and configuration log history of a selected rule, as well
to compare two policy rule versions to see how the rule changed.
The audit comment history for a rule pushed from Panorama is viewable
only from the Panorama management server. However, you can view
the audit comments in the configurations logs forwarded to Panorama
from managed firewalls. However, the audit comment archive is not
viewable for rules created or modified locally on the firewall.
To ensure that audit comments are captured at the time a rule is
created or modified, Enforce Policy Rule, Description,
Tag and Audit Comment.
The ability to target a rule
enables you to keep policies centralized on Panorama. Targeted rules
allow you to define the rules (as either shared or device group
pre- or post-rules) on Panorama and improve visibility and efficiency
when managing the rules (see Device
Group Policies). The audit comment archive adds further visibility
by allowing you to track how and why your policy rules change over
time so you can audit the rule evolution over the course of the
rule lifecycle.
- (Best Practice) Enforce audit comments
for policy rules.Although this step is optional, it is a best practice to enforce audit comments for policy rules to ensure that you capture the reason for creating or modifying the rule. This also helps maintain an accurate rule history for auditing purposes.
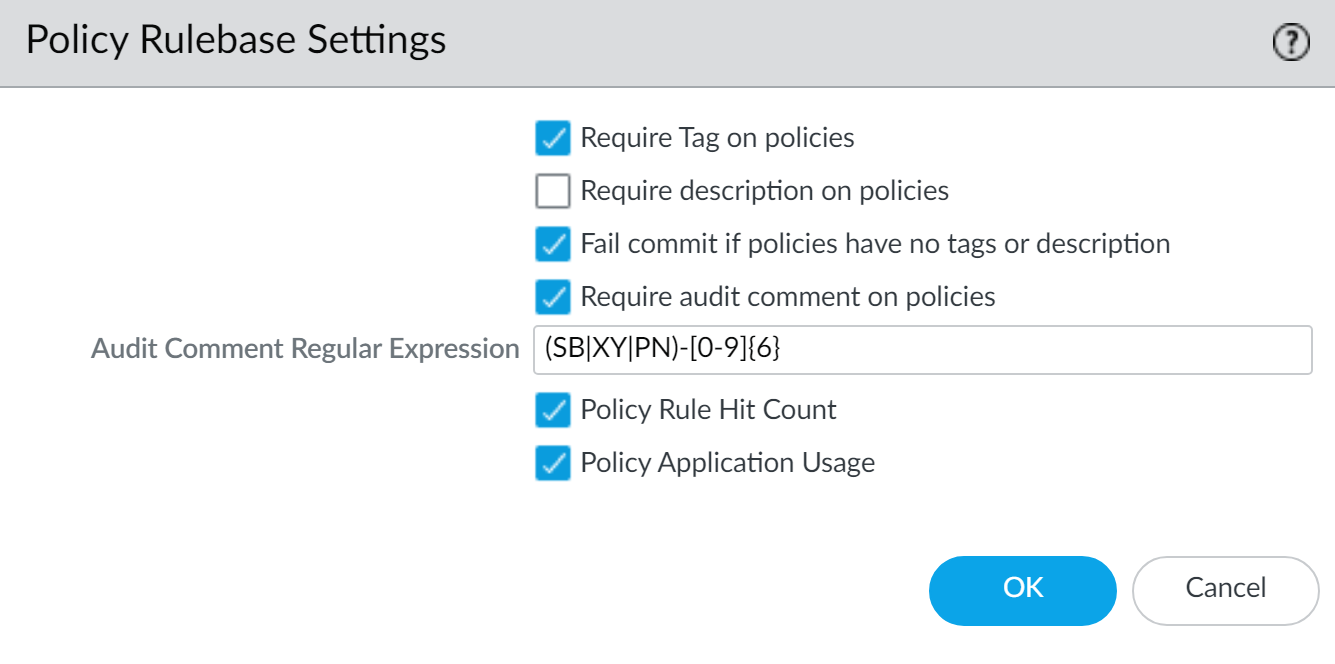
- Select PanoramaSetupManagement and edit the Policy Rulebase Settings.
- Enable the option to Require audit comment on policies.
- Configure the Audit Comment Regular Expression to
specify the audit comment format.When creating or modifying a rule, require audit comments to adhere to a specific format based on your business and auditing needs by specifying letter and number expressions. For example, you can use this setting to specify regular expressions to match your ticketing number formats:
- [0-9]{<Number of digits>}—Requires the audit comment to contain a minimum number of digits ranging from 0 to 9. For example, [0-9]{6} requires a minimum of 6 digit numerical expression with numbers 0 to 9. Configure the minimum number of digits as needed.
- <Letter Expression>—Requires the audit comment to contain a letter expression. For example, Reason for Change- requires that the administrator to begin the audit comment with this letter expression.
- <Letter Expression>-[0-9]{<Number of digits>}—Requires the audit comment to contain a set character prefix with a minimum number of digits ranging from 0 to 9. For example, SB-[0-9]{6} requires the audit comment format to begin with SB-, followed by a minimum 6 digit numerical expression with numbers 0 to 9 such as SB-012345.
- (<Letter Expression>)|(<Letter Expression>)|(<Letter Expression>)|-[0-9]{<Number of digits>}—Requires the audit comment to contain a prefix using one of the configured set of letter expressions with a minimum number of digits ranging from 0 to 9. For example, (SB|XY|PN)-[0-9]{6} requires the audit comment format begin with SB-, XY-, or PN- followed by a minimum 6 digit numerical expression with numbers 0 to 9 such as SB-012345, XY-654321, or PN-012543.
- Click OK to apply the new policy
rulebase settings.
![]()
- Select Commit and Commit to Panorama.
- Create a rule.In this example, we define a pre-rule in the Security rulebase that permits users on the internal network to access the servers in the DMZ.
- On the Policies tab and select the Device Group for which you want to define a rule.
- Select the rulebase. For this example, select PoliciesSecurityPre-Rules and Add a rule.
- In the General tab, enter a descriptive rule Name and enter an Audit Comment.
- In the Source tab, set the Source Zone to Trust.
- In the Destination tab, set the Destination Zone to DMZ.
- In the Service/ URL Category tab, set the Service to application-default.
- In the Actions tab, set the Action to Allow.
- Leave all the other options set to their default values.
- Target the rule to include or exclude a subset of firewalls.To apply the rule to a selected set of firewalls:
- Select the Target tab in the Policy Rule dialog.
- Select the firewalls to which you want to apply the
rule.If you do not select firewalls to target, the rule is added to all of the (unchecked) firewalls in the device group.By default, although the check box for the virtual systems in the device group is disabled, all virtual systems will inherit the rule on commit unless you select one or more virtual systems to which you want the rule to apply.
- (Optional) To exclude a subset of firewalls
from inheriting the rule, Install on all but specified
devices and select the firewalls you want to exclude.If you Install on all but specified devices and do not select any firewalls, the rule is not added to any of the firewalls in the device group.
- Click OK to add the rule.
- Commit and push the configuration changes.
- Select CommitCommit and Push and Edit Selections in the Push Scope.
- Select Device Groups, select the device group where you added the rule, and click OK.
- Commit and Push your changes to the Panorama configuration and to device groups.
- Troubleshoot Policy Rule Traffic Match to verify that the rules allow and deny traffic as the intended.