Migrate a Firewall HA Pair to Panorama Management
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- Determine Panorama Log Storage Requirements
-
- Setup Prerequisites for the Panorama Virtual Appliance
- Perform Initial Configuration of the Panorama Virtual Appliance
- Set Up The Panorama Virtual Appliance as a Log Collector
- Set Up the Panorama Virtual Appliance with Local Log Collector
- Set up a Panorama Virtual Appliance in Panorama Mode
- Set up a Panorama Virtual Appliance in Management Only Mode
-
- Preserve Existing Logs When Adding Storage on Panorama Virtual Appliance in Legacy Mode
- Add a Virtual Disk to Panorama on an ESXi Server
- Add a Virtual Disk to Panorama on vCloud Air
- Add a Virtual Disk to Panorama on Alibaba Cloud
- Add a Virtual Disk to Panorama on AWS
- Add a Virtual Disk to Panorama on Azure
- Add a Virtual Disk to Panorama on Google Cloud Platform
- Add a Virtual Disk to Panorama on Hyper-V
- Add a Virtual Disk to Panorama on KVM
- Add a Virtual Disk to Panorama on Oracle Cloud Infrastructure (OCI)
- Mount the Panorama ESXi Server to an NFS Datastore
-
- Increase CPUs and Memory for Panorama on an ESXi Server
- Increase CPUs and Memory for Panorama on vCloud Air
- Increase CPUs and Memory for Panorama on Alibaba Cloud
- Increase CPUs and Memory for Panorama on AWS
- Increase CPUs and Memory for Panorama on Azure
- Increase CPUs and Memory for Panorama on Google Cloud Platform
- Increase CPUs and Memory for Panorama on Hyper-V
- Increase CPUs and Memory for Panorama on KVM
- Increase CPUs and Memory for Panorama on Oracle Cloud Infrastructure (OCI)
- Complete the Panorama Virtual Appliance Setup
-
- Convert Your Evaluation Panorama to a Production Panorama with Local Log Collector
- Convert Your Evaluation Panorama to a Production Panorama without Local Log Collector
- Convert Your Evaluation Panorama to VM-Flex Licensing with Local Log Collector
- Convert Your Evaluation Panorama to VM-Flex Licensing without Local Log Collector
- Convert Your Production Panorama to an ELA Panorama
-
- Register Panorama
- Activate a Panorama Support License
- Activate/Retrieve a Firewall Management License when the Panorama Virtual Appliance is Internet-connected
- Activate/Retrieve a Firewall Management License when the Panorama Virtual Appliance is not Internet-connected
- Activate/Retrieve a Firewall Management License on the M-Series Appliance
- Install the Panorama Device Certificate
-
- Panorama, Log Collector, Firewall, and WildFire Version Compatibility
- Install Updates for Panorama in an HA Configuration
- Install Updates for Panorama with an Internet Connection
- Install Updates for Panorama When Not Internet-Connected
- Install Updates Automatically for Panorama without an Internet Connection
- Migrate Panorama Logs to the New Log Format
-
- Migrate from a Panorama Virtual Appliance to an M-Series Appliance
- Migrate a Panorama Virtual Appliance to a Different Hypervisor
- Migrate from an M-Series Appliance to a Panorama Virtual Appliance
- Migrate from an M-100 Appliance to an M-500 Appliance
- Migrate from an M-100 or M-500 Appliance to an M-200 or M-600 Appliance
-
- Configure an Admin Role Profile
- Configure an Access Domain
-
- Configure a Panorama Administrator Account
- Configure Local or External Authentication for Panorama Administrators
- Configure a Panorama Administrator with Certificate-Based Authentication for the Web Interface
- Configure an Administrator with SSH Key-Based Authentication for the CLI
- Configure RADIUS Authentication for Panorama Administrators
- Configure TACACS+ Authentication for Panorama Administrators
- Configure SAML Authentication for Panorama Administrators
-
- Add a Firewall as a Managed Device
-
- Add a Device Group
- Create a Device Group Hierarchy
- Create Objects for Use in Shared or Device Group Policy
- Revert to Inherited Object Values
- Manage Unused Shared Objects
- Manage Precedence of Inherited Objects
- Move or Clone a Policy Rule or Object to a Different Device Group
- Push a Policy Rule to a Subset of Firewalls
- Manage the Rule Hierarchy
- Manage the Master Key from Panorama
- Redistribute Data to Managed Firewalls
-
- Add Standalone WildFire Appliances to Manage with Panorama
- Remove a WildFire Appliance from Panorama Management
-
-
- Configure a Cluster and Add Nodes on Panorama
- Configure General Cluster Settings on Panorama
- Remove a Cluster from Panorama Management
- Configure Appliance-to-Appliance Encryption Using Predefined Certificates Centrally on Panorama
- Configure Appliance-to-Appliance Encryption Using Custom Certificates Centrally on Panorama
- View WildFire Cluster Status Using Panorama
- Upgrade a Cluster Centrally on Panorama with an Internet Connection
- Upgrade a Cluster Centrally on Panorama without an Internet Connection
-
-
- Manage Licenses on Firewalls Using Panorama
-
- Supported Updates
- Schedule a Content Update Using Panorama
- Upgrade Log Collectors When Panorama Is Internet-Connected
- Upgrade Log Collectors When Panorama Is Not Internet-Connected
- Upgrade Firewalls When Panorama Is Internet-Connected
- Upgrade Firewalls When Panorama Is Not Internet-Connected
- Upgrade a ZTP Firewall
- Revert Content Updates from Panorama
-
- Preview, Validate, or Commit Configuration Changes
- Enable Automated Commit Recovery
- Compare Changes in Panorama Configurations
- Manage Locks for Restricting Configuration Changes
- Add Custom Logos to Panorama
- Use the Panorama Task Manager
- Reboot or Shut Down Panorama
- Configure Panorama Password Profiles and Complexity
-
-
- Verify Panorama Port Usage
- Resolve Zero Log Storage for a Collector Group
- Replace a Failed Disk on an M-Series Appliance
- Replace the Virtual Disk on an ESXi Server
- Replace the Virtual Disk on vCloud Air
- Migrate Logs to a New M-Series Appliance in Log Collector Mode
- Migrate Logs to a New M-Series Appliance in Panorama Mode
- Migrate Logs to a New M-Series Appliance Model in Panorama Mode in High Availability
- Migrate Logs to the Same M-Series Appliance Model in Panorama Mode in High Availability
- Migrate Log Collectors after Failure/RMA of Non-HA Panorama
- Regenerate Metadata for M-Series Appliance RAID Pairs
- View Log Query Jobs
- Troubleshoot Commit Failures
- Troubleshoot Registration or Serial Number Errors
- Troubleshoot Reporting Errors
- Troubleshoot Device Management License Errors
- Troubleshoot Automatically Reverted Firewall Configurations
- Complete Content Update When Panorama HA Peer is Down
- View Task Success or Failure Status
- Downgrade from Panorama 10.0
End-of-Life (EoL)
Migrate a Firewall HA Pair to Panorama Management
Procedure for migrating a firewall HA pair, active/active
or active/passive, to Panorama management in Panorama 10.0.
- Plan the migration.See the checklist in Plan the Transition to Panorama Management.
- Disable
configuration synchronization between the HA peers.Repeat these steps for both firewalls in the HA pair.
- Log in to the web interface on each firewall, select DeviceHigh AvailabilityGeneral and edit the Setup section.
- Clear Enable Config Sync and click OK.
- Commit the configuration changes on each firewall.
- Connect each firewall to Panorama.If Panorama is already receiving logs from these firewalls, you do not need to perform this step. Continue to Step 5.Repeat these steps for both firewalls in the HA pair.
- Log in to the web interface on each firewall, select DeviceSetupManagement and edit the Panorama Settings.
- In the Panorama Servers fields, enter the IP addresses of the Panorama management servers, confirm Panorama Policy and Objects and Device and Network Template are enabled and select OK.
- Commit the configuration changes on each firewall.
- Add each firewall as a managed device.If Panorama is already receiving logs from these firewalls, you do not need to perform this step. Continue to Step 5.
- Log in to the Panorama Web Interface, select PanoramaManaged Devices and click Add.
- Enter the serial number of each firewall and click OK.
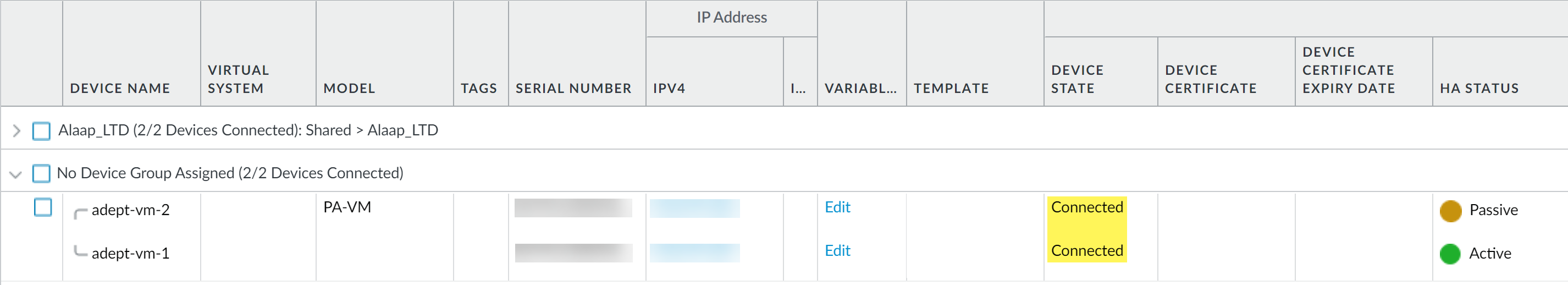
- Select CommitCommit to Panorama and Commit your changes.
- Verify that the Device State for each firewall is Connected.
![]()
- Import each firewall configuration
into Panorama.Do no push any device group or template stack configuration to your managed firewalls in this step. Pushing the device group and template stack configuration during this step wipes the local firewall HA configuration in the next steps.If you later decide to re-import a firewall configuration, first remove the firewall device groups and template to which it is a member. If the device group and template names are the same as the firewall hostname, then you can delete the device group and template before re-importing the firewall configuration or use the Device Group Name Prefix fields to enter a new name for the device group and template created by the re-import. Additionally, firewalls don’t lose logs when you remove them from device groups or templates.
- From
Panorama, select PanoramaSetupOperations,
click Import device configuration to Panorama,
and select the Device.Panorama can’t import a configuration from a firewall that is assigned to an existing device group or template stack.
- (Optional) Edit the Template Name. The default value is the firewall name. You can’t use the name of an existing template or template stack.
- (Optional) Edit the Device Group names.
For a multi-vsys firewall, each device group has a vsys name by
default, so add a character string as a Device Group Name Prefix
for each. Otherwise, the default value is the firewall name. You
can’t use the names of existing device groups.The Imported devices’ shared objects into Panorama’s shared context check box is selected by default, which means Panorama compares imports objects that belong to the Shared location in the firewall to Shared in Panorama. If an imported object is not in the Shared context of the firewall, it is applied to each device group being imported. If you clear the check box, Panorama copies will not compare imported objects, and apply all shared firewall objects into device groups being imported instead of Shared. This could create duplicate objects, so selecting the check box is a best practice in most cases. To understand the consequences of importing shared or duplicate objects into Panorama, see Plan how to manage shared settings.
- Commit to Panorama.
- Select PanoramaSetupOperations and Export
or push device config bundle. Select the Device,
select OK and Push
& Commit the configuration.The Enable Config Sync setting in Step 2 must be cleared on both firewalls before you push the device group and template stack.
- Launch the Web Interface of the firewall HA peer and ensure that the configuration pushed in the previous step committed successfully. If not, Commit the changes locally on the firewall.
- Repeat Step 1-6 above on the second firewall. The process will create a device group and template stack for the firewall.
- From
Panorama, select PanoramaSetupOperations,
click Import device configuration to Panorama,
and select the Device.
- Add the HA firewall pair into the same device group and
template stack.(Firewalls in active/active configuration) It is recommended to add HA peers to the same device group but not to the same template stack because firewalls in an active/active HA configuration typically need unique network configurations. This simplifies policy management for the HA peers while reducing the operational burden of managing the network configuration of each HA peer when their network configurations are independent of each other. For example, firewalls in an active/active HA configuration often times need unique network configurations, such as unique floating IP that are used as the default gateway for hosts.Ultimately, deciding whether to add firewalls in an active/active HA configuration to the same device group and template stack is a design decision you must make when designing your configuration hierarchy.
- Select PanoramaDevice Group, select the device group of the second firewall, and remove the second firewall from the device group.
- Select the device group from which you removed the second firewall and Delete it.
- Select the device group for the first firewall, select the second firewall, click OK and Commit to Panorama to add it to the same device group as the HA peer.
- Select PanoramaTemplates, select the template stack of the second firewall, and remove the second firewall from the template stack.
- Select the template stack from which you removed the second firewall and Delete it.
- Select the template stack for the first firewall, add the second firewall, select OK and Commit to Panorama to add it to the same template stack as the HA peer.
- Remove the HA settings in the template associated
with the newly migrated firewalls.
- Select DeviceHigh Availability and select the Template containing the HA configuration.
- Select Remove All.
- Commit to Panorama.
- Push the device group and template stack configurations
to your managed firewalls.First push the device group and template stack configuration to your passive HA peer and then to the active HA peer.Pushing the imported firewall configuration from Panorama to remove local firewall configuration updates Policy rule Creation and Modified dates to reflect the date you pushed to your newly managed firewalls when you monitor policy rule usage for a managed firewall. Additionally, a new universially unique identifier (UUID) for each policy rule is created.
- Select Commit Push to Devices and Edit Selections.
- Enable (select) Merge Device Candidate Config, Include Device and Network Templates, and Force Template Values.
- Click OK.
- Push to your managed firewalls.
- Launch the Web Interface of the active HA peer and select DeviceHigh AvailabilityOperational Commands to Suspend local device.Fail over to the passive HA peer before modifying the active HA peer to maintain your security posture while completing the configuration migration.
- Launch the Web Interface of the now active HA peer and select DeviceHigh AvailabilityOperational Commands to Suspend local device.This restores the original active/passive HA peer roles.
- Select PanoramaManaged DevicesSummary, and verify that the device group and template are in sync for the passive firewall. Verify policy rules, objects and network settings on the passive firewall match the active firewall.
- Enable configuration synchronization between the HA peers.Repeat these steps for both firewalls in the HA pair if you plan on maintaining a local configuration that needs to be synchronized.
- Log in to the web interface on each firewall, select DeviceHigh AvailabilityGeneral and edit the Setup section.
- Select Enable Config Sync and click OK.
- Commit the configuration changes on each firewall.