Templates and Template Stacks
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- Determine Panorama Log Storage Requirements
-
- Setup Prerequisites for the Panorama Virtual Appliance
- Perform Initial Configuration of the Panorama Virtual Appliance
- Set Up The Panorama Virtual Appliance as a Log Collector
- Set Up the Panorama Virtual Appliance with Local Log Collector
- Set up a Panorama Virtual Appliance in Panorama Mode
- Set up a Panorama Virtual Appliance in Management Only Mode
-
- Preserve Existing Logs When Adding Storage on Panorama Virtual Appliance in Legacy Mode
- Add a Virtual Disk to Panorama on an ESXi Server
- Add a Virtual Disk to Panorama on vCloud Air
- Add a Virtual Disk to Panorama on Alibaba Cloud
- Add a Virtual Disk to Panorama on AWS
- Add a Virtual Disk to Panorama on Azure
- Add a Virtual Disk to Panorama on Google Cloud Platform
- Add a Virtual Disk to Panorama on Hyper-V
- Add a Virtual Disk to Panorama on KVM
- Add a Virtual Disk to Panorama on Oracle Cloud Infrastructure (OCI)
- Mount the Panorama ESXi Server to an NFS Datastore
-
- Increase CPUs and Memory for Panorama on an ESXi Server
- Increase CPUs and Memory for Panorama on vCloud Air
- Increase CPUs and Memory for Panorama on Alibaba Cloud
- Increase CPUs and Memory for Panorama on AWS
- Increase CPUs and Memory for Panorama on Azure
- Increase CPUs and Memory for Panorama on Google Cloud Platform
- Increase CPUs and Memory for Panorama on Hyper-V
- Increase CPUs and Memory for Panorama on KVM
- Increase CPUs and Memory for Panorama on Oracle Cloud Infrastructure (OCI)
- Complete the Panorama Virtual Appliance Setup
-
- Convert Your Evaluation Panorama to a Production Panorama with Local Log Collector
- Convert Your Evaluation Panorama to a Production Panorama without Local Log Collector
- Convert Your Evaluation Panorama to VM-Flex Licensing with Local Log Collector
- Convert Your Evaluation Panorama to VM-Flex Licensing without Local Log Collector
- Convert Your Production Panorama to an ELA Panorama
-
- Register Panorama
- Activate a Panorama Support License
- Activate/Retrieve a Firewall Management License when the Panorama Virtual Appliance is Internet-connected
- Activate/Retrieve a Firewall Management License when the Panorama Virtual Appliance is not Internet-connected
- Activate/Retrieve a Firewall Management License on the M-Series Appliance
- Install the Panorama Device Certificate
-
- Panorama, Log Collector, Firewall, and WildFire Version Compatibility
- Install Updates for Panorama in an HA Configuration
- Install Updates for Panorama with an Internet Connection
- Install Updates for Panorama When Not Internet-Connected
- Install Updates Automatically for Panorama without an Internet Connection
- Migrate Panorama Logs to the New Log Format
-
- Migrate from a Panorama Virtual Appliance to an M-Series Appliance
- Migrate a Panorama Virtual Appliance to a Different Hypervisor
- Migrate from an M-Series Appliance to a Panorama Virtual Appliance
- Migrate from an M-100 Appliance to an M-500 Appliance
- Migrate from an M-100 or M-500 Appliance to an M-200 or M-600 Appliance
-
- Configure an Admin Role Profile
- Configure an Access Domain
-
- Configure a Panorama Administrator Account
- Configure Local or External Authentication for Panorama Administrators
- Configure a Panorama Administrator with Certificate-Based Authentication for the Web Interface
- Configure an Administrator with SSH Key-Based Authentication for the CLI
- Configure RADIUS Authentication for Panorama Administrators
- Configure TACACS+ Authentication for Panorama Administrators
- Configure SAML Authentication for Panorama Administrators
-
- Add a Firewall as a Managed Device
-
- Add a Device Group
- Create a Device Group Hierarchy
- Create Objects for Use in Shared or Device Group Policy
- Revert to Inherited Object Values
- Manage Unused Shared Objects
- Manage Precedence of Inherited Objects
- Move or Clone a Policy Rule or Object to a Different Device Group
- Push a Policy Rule to a Subset of Firewalls
- Manage the Rule Hierarchy
- Manage the Master Key from Panorama
- Redistribute Data to Managed Firewalls
-
- Add Standalone WildFire Appliances to Manage with Panorama
- Remove a WildFire Appliance from Panorama Management
-
-
- Configure a Cluster and Add Nodes on Panorama
- Configure General Cluster Settings on Panorama
- Remove a Cluster from Panorama Management
- Configure Appliance-to-Appliance Encryption Using Predefined Certificates Centrally on Panorama
- Configure Appliance-to-Appliance Encryption Using Custom Certificates Centrally on Panorama
- View WildFire Cluster Status Using Panorama
- Upgrade a Cluster Centrally on Panorama with an Internet Connection
- Upgrade a Cluster Centrally on Panorama without an Internet Connection
-
-
- Manage Licenses on Firewalls Using Panorama
-
- Supported Updates
- Schedule a Content Update Using Panorama
- Upgrade Log Collectors When Panorama Is Internet-Connected
- Upgrade Log Collectors When Panorama Is Not Internet-Connected
- Upgrade Firewalls When Panorama Is Internet-Connected
- Upgrade Firewalls When Panorama Is Not Internet-Connected
- Upgrade a ZTP Firewall
- Revert Content Updates from Panorama
-
- Preview, Validate, or Commit Configuration Changes
- Enable Automated Commit Recovery
- Compare Changes in Panorama Configurations
- Manage Locks for Restricting Configuration Changes
- Add Custom Logos to Panorama
- Use the Panorama Task Manager
- Reboot or Shut Down Panorama
- Configure Panorama Password Profiles and Complexity
-
-
- Verify Panorama Port Usage
- Resolve Zero Log Storage for a Collector Group
- Replace a Failed Disk on an M-Series Appliance
- Replace the Virtual Disk on an ESXi Server
- Replace the Virtual Disk on vCloud Air
- Migrate Logs to a New M-Series Appliance in Log Collector Mode
- Migrate Logs to a New M-Series Appliance in Panorama Mode
- Migrate Logs to a New M-Series Appliance Model in Panorama Mode in High Availability
- Migrate Logs to the Same M-Series Appliance Model in Panorama Mode in High Availability
- Migrate Log Collectors after Failure/RMA of Non-HA Panorama
- Regenerate Metadata for M-Series Appliance RAID Pairs
- View Log Query Jobs
- Troubleshoot Commit Failures
- Troubleshoot Registration or Serial Number Errors
- Troubleshoot Reporting Errors
- Troubleshoot Device Management License Errors
- Troubleshoot Automatically Reverted Firewall Configurations
- Complete Content Update When Panorama HA Peer is Down
- View Task Success or Failure Status
- Downgrade from Panorama 10.0
End-of-Life (EoL)
Templates and Template Stacks
Overview of template and template stack configuration
functionality.
You use templates and template stacks to configure the
settings that enable firewalls to operate on the network. Templates
are the basic building blocks you use to configure the Network and Device tabs
on Panorama™. You can use templates to define interface and zone
configurations, to manage the server profiles for logging and syslog
access, or to define VPN configurations. Template stacks give you
the ability to layer multiple templates and create a combined configuration.
Template stacks simplify management because they allow you to define
a common base configuration for all devices attached to the template
stack and they give you the ability to layer templates to create
a combined configuration. This enables you to define templates with
location- or function-specific settings and then stack the templates
in descending order of priority so that firewalls inherit the settings
based on the order of the templates in the stack.
Both templates and template stacks support variables. Variables
allow you to create placeholder objects with their value specified
in the template or template stack based on your configuration needs.
Create a template or template stack variable to replace IP addresses,
Group IDs, and interfaces in your configurations. Template variables
are inherited by the template stack and you can override them to
create a template stack variable. However, templates do not inherit
variables defined in the template stack. When a variable is defined
in the template or template stack and pushed to the firewall, the
value defined for the variable is displayed on the firewall.
Use templates to accommodate firewalls that have unique settings.
Alternatively, you can push a broader, common base configuration
and then override certain pushed settings with firewall-specific
values on individual firewalls. When you override a setting on the
firewall, the firewall saves that setting to its local configuration and
Panorama no longer manages the setting. To restore template values
after you override them, use Panorama to force the template or template
stack configuration onto the firewall. For example, after you define
a common NTP server in a template and override the NTP server configuration
on a firewall to accommodate a local time zone, you can later revert
to the NTP server defined in the template.
When defining a template stack, consider assigning firewalls
that are the same hardware model and require access to similar network
resources, such as gateways and syslog servers. This enables you
to avoid the redundancy of adding every setting to every template
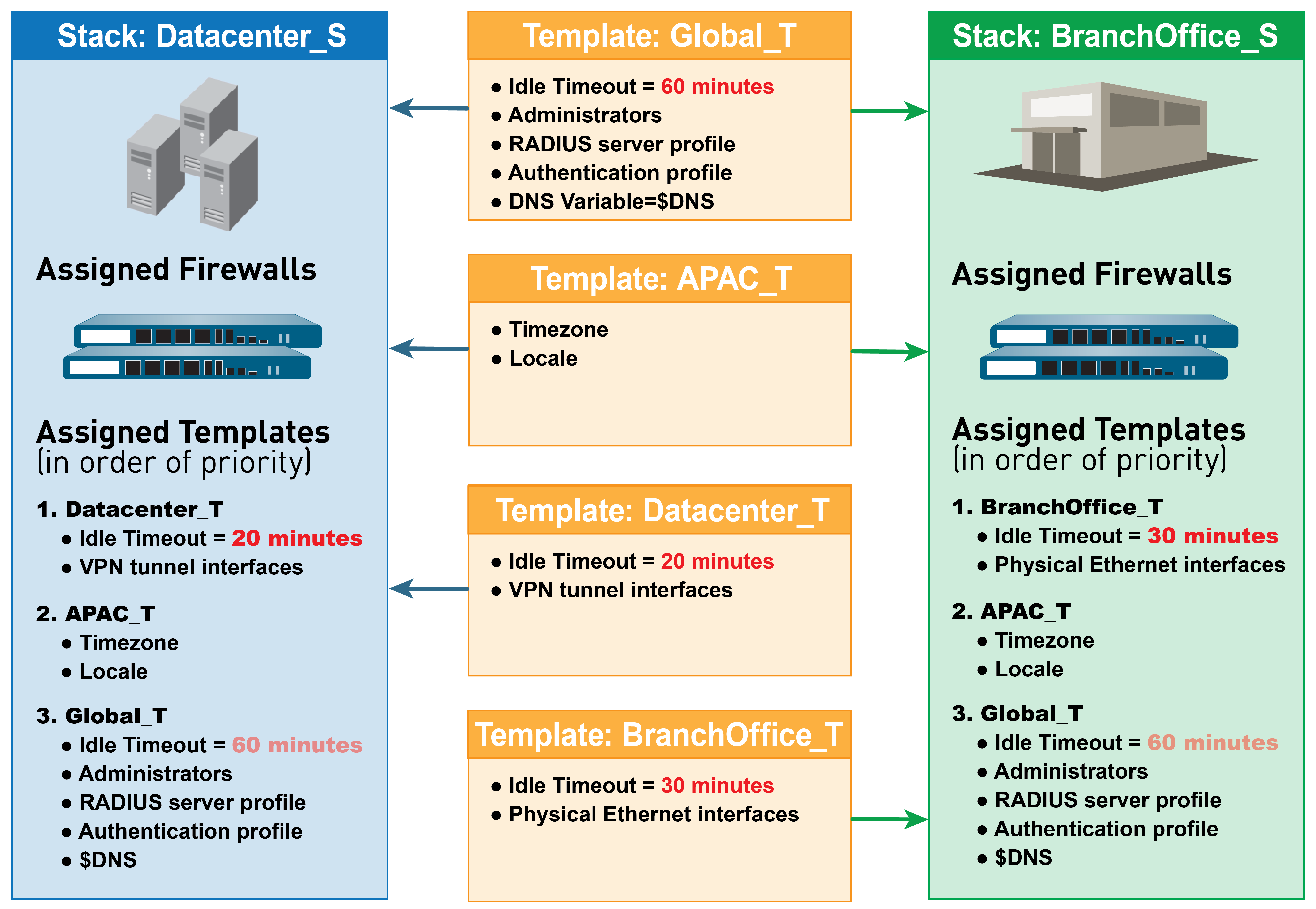
stack. The following figure illustrates an example configuration
in which you assign data center firewalls in the Asia-Pacific (APAC)
region to a stack with global settings, one template with APAC-specific
settings, and one template with data center-specific settings. To
manage firewalls in an APAC branch office, you can then re-use the
global and APAC-specific templates by adding them to another stack
that includes a template with branch-specific settings. Templates
in a stack have a configurable priority order that ensures Panorama
pushes only one value for any duplicate setting. Panorama evaluates
the templates listed in a stack configuration from top to bottom
with higher templates having priority. The following figure illustrates
a data center stack in which the data center template has a higher
priority than the global template: Panorama pushes the idle timeout
value from the data center template and ignores the value from the
global template.
You cannot use templates or template stacks to set firewall modes:
virtual private network (VPN) mode, multiple virtual systems (multi-vsys)
mode, or operational modes (normal or FIPS-CC mode). For details,
see Template
Capabilities and Exceptions. However, you can assign firewalls
that have non-matching modes to the same template or stack. In such
cases, Panorama pushes mode-specific settings only to firewalls
that support those modes. As an exception, you can configure Panorama
to push the settings of the default vsys in a template to firewalls
that don’t support virtual systems or that don’t have any virtual
systems configured.
For the relevant procedures, see Manage
Templates and Template Stacks.
