Create User-to-Data-Center Decryption Policy Rules
Table of Contents
10.2
Expand all | Collapse all
-
- What Is a Data Center Best Practice Security Policy?
- Why Do I Need a Data Center Best Practice Security Policy?
- Data Center Best Practice Methodology
- How Do I Deploy a Data Center Best Practice Security Policy?
- How to Assess Your Data Center
-
- Create the Data Center Best Practice Antivirus Profile
- Create the Data Center Best Practice Anti-Spyware Profile
- Create the Data Center Best Practice Vulnerability Protection Profile
- Create the Data Center Best Practice File Blocking Profile
- Create the Data Center Best Practice WildFire Analysis Profile
- Use Cortex XDR Agent to Protect Data Center Endpoints
- Create Data Center Traffic Block Rules
- Order the Data Center Security Policy Rulebase
- Maintain the Data Center Best Practice Rulebase
- Use Palo Alto Networks Assessment and Review Tools
Create User-to-Data-Center Decryption Policy Rules
Create rules that decrypt user traffic flowing to the
data center so you can inspect the traffic and protect your most
valuable assets against malware and other threats.
Create Decryption policy rules for traffic
that enters the data center from the user population to provide
visibility so that you can inspect the traffic and safeguard your
most valuable assets. When you create a Security policy rule that
allows a group of users (or a particular user) access to a set of
data center servers, create a decryption policy rule to decrypt
that traffic.
Because the data center houses your most valuable
assets, decrypt all the data center traffic you can decrypt. Start
by decrypting traffic to the most critical servers, decrypting high-risk
traffic categories, and decrypting traffic from the least trusted
network segments (for example, prioritize decrypting third-party
traffic from partners, customers, or contractors over decrypting
traffic from a trusted internal segment), and then expand the effort
until you have applied decryption to traffic destined to all of
your data center assets. Decrypt as much traffic as you can while
retaining acceptable performance.
Exclude
Unsuitable Traffic from Data Center Decryption. Regulations
and compliance over personal information differ from country to
country and even within country regions. Different companies may
have different compliance rules about personal information. Decrypt as
much traffic as you can, but if your data center houses information
that regulations or company rules exempt from decryption, don’t
decrypt that traffic.
In Create User-to-Data-Center Application Allow Rules,
we created Security policy rules that allow DNS access, allow engineering users
to access engineering development servers, allow SAP contractor
developers to access only the SAP development servers, and allow
a particular set of IT users data center server management access.
Here we create decryption policy rules (PoliciesDecryption) to decrypt the
traffic that these rules allow.
The decryption policy rules
share some common elements in regard to these traffic flows:
- When you create a Decryption policy rule, the objective is to decrypt traffic so that a Security policy rule can examine it and allow or block it based on policy. To accomplish that, the Decryption policy rule must use the same source zone(s) and user(s) as the analogous security policy rule, and the same destination zone and address (often defined by a dynamic address group so that as you add or remove servers, you can update the firewall without a commit operation). Defining the same source and destination in the Security policy and in the Decryption policy applies both policies to the same traffic.
- The Action for all of these rules is decrypt, except in the case of sensitive personal information as shown in Step 4.
- For each rule, configure decryption logging and log forwarding. Log as much decryption traffic as your firewall resources permit.
- The decryption rules that use SSL Inbound Inspection to examine incoming traffic require the appropriate server certificate.
- All of these decryption rules use the Best Practice data center decryption profile shown in Create the Data Center Best Practice Decryption Profiles.
- Decrypt allowed traffic from employee user groups
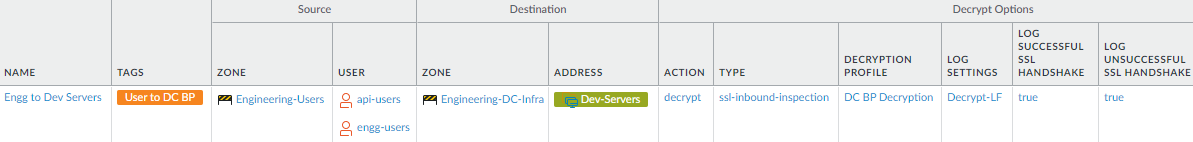
to data center servers.This rule shows how to decrypt traffic from a user group to the data center servers that the group is allowed to access to provide visibility into that traffic. For example, the application allow rules we created include a Security policy rule that allows engineering users to access development servers in the data center. To protect the development servers, decrypt incoming traffic so that the firewall can inspect it and apply threat prevention profiles.
![]() To create this rule:
To create this rule:- Specify the same source and destination as in the analogous security policy rule. In this case, the Source users are the api-users and engg-users user groups in the Engineering-Users zone, and the Destination is the servers specified in the Dev-Servers dynamic address group in the Engineering-DC-Infra zone.
- On the Options tab, set the Action to Decrypt and the decryption Type to SSL Inbound Inspection. Specify the server certificate for the development servers and apply the data center best practice Decryption Profile to apply SSL Inbound Inspection and SSL Protocol Settings to the traffic.
Create a similar Decryption policy rule for allowed data center traffic of each user group (or individual user, if applicable) based on the source zone and user group (or user) and on the destination zone and server group (as defined by the dynamic address group membership). - Decrypt allowed traffic from contractors, partners, customers,
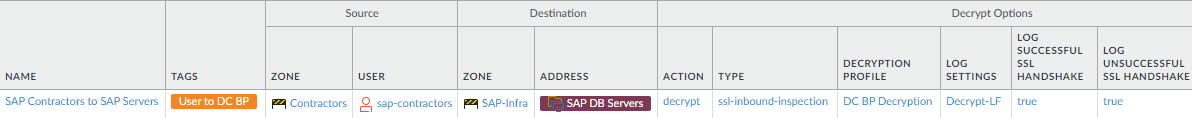
and other third-parties.This rule shows how to decrypt from third-party groups to the data center servers they are allowed to access. For example, the allow rules include a security policy rule that allows limited access for SAP developer contractors to SAP database servers in the data center. Decrypt incoming traffic so that the firewall can inspect it, apply threat prevention profiles to it, and protect the SAP data center servers.
![]() To create this rule:
To create this rule:- Specify the same source and destination of the traffic to decrypt as in the analogous security policy rule. In this case, the Source users are the sap-contractors user group in the Contractors zone, and the Destination is the servers specified in the SAP DB Servers dynamic address group in the SAP-Infra zone.
- On the Options tab, set the Action to Decrypt and the decryption Type to SSL Inbound Inspection. Specify the server certificate for the development servers and apply the data center best practice Decryption Profile to apply SSL Inbound Inspection and SSL Protocol Settings to the traffic.
Create a similar Decryption policy rule for each third-party group’s allowed data center traffic based on the source zone and user group and the destination zone and server group (as defined by the dynamic address group membership). - Decrypt privileged allowed access to data center servers
(except traffic pertaining to personal information if regulations
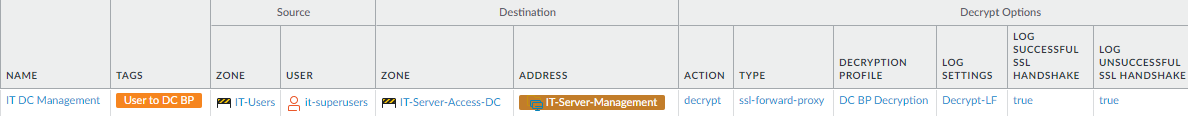
or compliance rules prohibit it).This rule shows how to decrypt traffic for privileged access because you should decrypt as much traffic as possible to provide the visibility necessary to defend the data center, no matter how much you trust the users. If you don’t decrypt allowed traffic, you can’t apply threat prevention profiles, and if the traffic conceals malware or other threats, you won’t see them. This example references the Security Policy allow rule we created previously to provide management interface access to data center servers for IT superusers.If the IT group that manages and maintains data center servers uses SSH, you can’t decrypt the SSH traffic. You can configure SSH Proxy to block SSH tunnels and prevent SSH from tunneling potentially malicious content and applications. If the IT group uses SSL, create a Decryption Policy rule using SSL Forward Proxy instead of SSL Inbound Inspection. The reason is that SSL Inbound Inspection requires the server certificate to perform decryption. Because IT manages many data center servers, creating SSL Inbound Inspection rules for each server is onerous and difficult to manage. SSL Forward Proxy decryption scales better in this use case.The following example shows the Decryption policy rule for the SSL Forward Proxy use case.
![]() To create this rule:
To create this rule:- Specify the same source and destination of the traffic to decrypt as in the analogous security policy rule. In this case, the Source users are the it-superusers user group in the IT-Users zone, and the Destination is the servers specified in the IT-Server-Management static address group in the IT-server-access-DC zone.
- On the Options tab, set the Action to Decrypt and the decryption Type to SSL Forward Proxy. Apply the data center best practice Decryption Profile to apply SSL Forward Proxy and SSL Protocol Settings to the traffic.
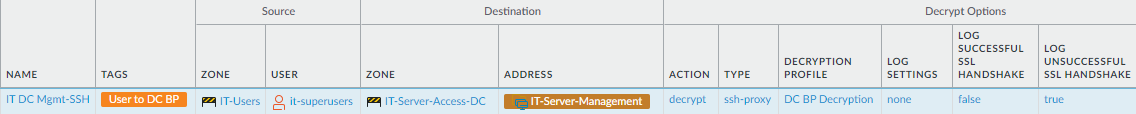
If other groups require privileged access, create a similar type of Decryption Policy rule for each group.IT personnel also manage switches, routers, and other devices in the data center. If the same group of IT users manages those resources, you can add them to the destination zone and address so that the rule decrypts traffic for connections to the management interfaces of those devices. If different IT user groups manage different sets of data center resources, create separate, tight security policy rules and corresponding decryption and authentication policy rules for each user group.The next example shows the Decryption policy rule for the SSH Proxy use case. You may also choose not to decrypt the traffic instead of using SSH Proxy decryption.![]() To create this rule:
To create this rule:- The traffic source and destination are the same as for the preceding SSL Forward Proxy use case example rule.
- On the Options tab, set the Action to Decrypt and the decryption Type to SSH Proxy. Apply the data center best practice Decryption Profile to apply SSH Proxy and SSL Protocol Settings to the traffic.IT personnel also manage data center switches, routers, and other devices. If the same group of IT users manages those resources, you can add them to the destination zone and address so that the rule decrypts traffic for connections to the management interfaces of those devices. If different IT user groups manage different sets of data center resources, create separate, tight security policy rules and corresponding decryption and authentication policy rules for each user group.
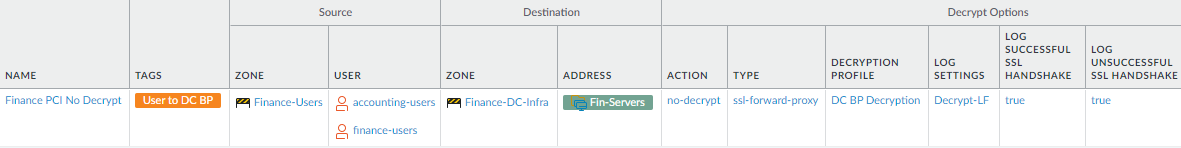
- Do not decrypt sensitive
personal information if prohibited by regulations or compliance
rules.This rule shows how to create a policy-based decryption exclusion if you need to except traffic from decryption for regulatory or compliance reasons. This example references the Security Policy allow rule we created previously to provide Finance server access for Finance users. If regulations or compliance permit you to decrypt this traffic, decrypt it so that the firewall can see the traffic and protect against threats.
![]() To create this rule:
To create this rule:- Specify the same source and destination of the traffic to decrypt as in the analogous security policy rule. In this case, the Source users are the accounting-users and finance-users user groups in the Finance-Users zone, and the Destination is the servers specified in the Fin-Servers dynamic address group in the Finance-DC-Infra zone.
- On the Options tab, set the Action to No Decrypt. Apply the data center best practice No Decryption profile to protect against certificate issues.Do not apply a No Decryption profile to TLSv1.3 traffic because the certificate information is encrypted, so the firewall cannot block sessions based on certificate information.