Internet-to-Data-Center Traffic Policies
Table of Contents
10.2
Expand all | Collapse all
-
- What Is a Data Center Best Practice Security Policy?
- Why Do I Need a Data Center Best Practice Security Policy?
- Data Center Best Practice Methodology
- How Do I Deploy a Data Center Best Practice Security Policy?
- How to Assess Your Data Center
-
- Create the Data Center Best Practice Antivirus Profile
- Create the Data Center Best Practice Anti-Spyware Profile
- Create the Data Center Best Practice Vulnerability Protection Profile
- Create the Data Center Best Practice File Blocking Profile
- Create the Data Center Best Practice WildFire Analysis Profile
- Use Cortex XDR Agent to Protect Data Center Endpoints
- Create Data Center Traffic Block Rules
- Order the Data Center Security Policy Rulebase
- Maintain the Data Center Best Practice Rulebase
- Use Palo Alto Networks Assessment and Review Tools
Internet-to-Data-Center Traffic Policies
Secure traffic from the internet to your data center.
Configure Security policy, Decryption policy,
and Denial-of-Service (DoS) Protection policy for traffic from the
internet to the data center.
- Create
application allow list Security policy rules for internet-to-data-center traffic to control
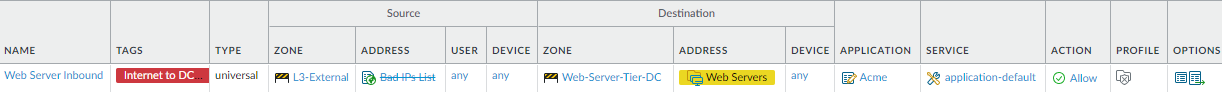
and secure partner, contractor, and customer access. Protect against downloading malware from an infected external client or placing malware on an external server from an infected data center server. Create allow rules for applications required for business purposes and create an External Dynamic List (EDL) to block bad IP addresses. For each rule, configure Log at Session End on the Actions tab and set up Log Forwarding to track and analyze rule violations.This example restricts the applications and destinations for internet-to-data-center traffic, and uses the Negate option to prevent communication with the Bad IPs List EDL.
![]() Create similar rules for traffic from the internet to other server groups (if allowed) and other applications. Make each rule specific to limit access to only the required applications and servers.
Create similar rules for traffic from the internet to other server groups (if allowed) and other applications. Make each rule specific to limit access to only the required applications and servers. - Create Decryption policy rules for
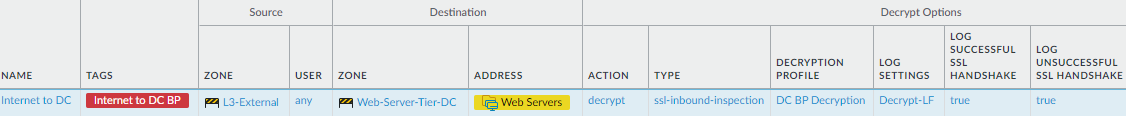
internet-to-data-center-traffic to decrypt allowed traffic. Configure SSL Inbound Inspection (and import the destination server certificates into the firewall) to decrypt partner, contractor, and customer traffic that Security policy rules allow for internet-to-data-center traffic. This example shows the Decryption policy for the preceding Security policy rule.
![]() Create Decryption rules to match traffic that internet-to-data-center Security policy rules allow.
Create Decryption rules to match traffic that internet-to-data-center Security policy rules allow. - Create
internet-to-data-center DoS Protection policy rules to protect
sensitive servers from Denial-of-Service (DoS) attacks by limiting
the number of connections-per-second (CPS) the firewall allows to
the servers to prevent a SYN flood attack. Attackers target the web server tier because if they take it down, they prevent most legitimate access to the data center. Apply a classified DoS Protection policy rule with a DoS Protection profile that limits the incoming CPS to prevent traffic spikes that can affect server performance and availability.
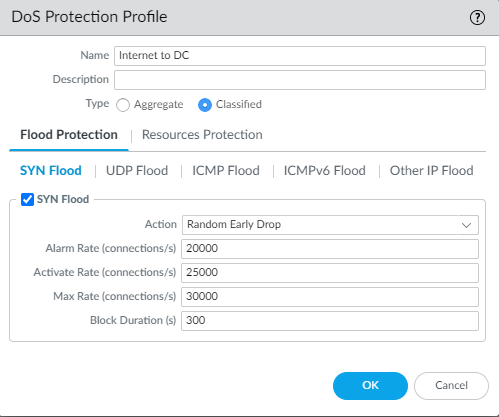
- Create a classified DoS Protection profile to protect the web server tier and prevent SYN flood attacks. The CPS thresholds you set depend on the baseline peak CPS rate.
![]()
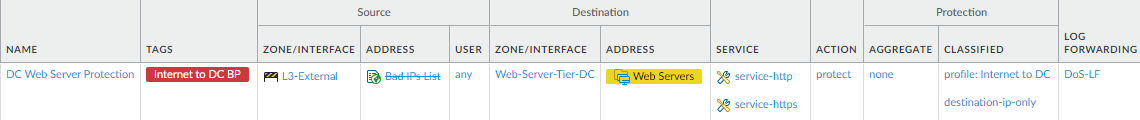
- Create a DoS Protection policy rule to specify the web servers you’re protecting and apply the classified DoS Protection profile to it.
![]() To protect against SYN flood attacks from internal sources, create a separate DoS Protection policy rule that specifies your internal zones as the source zone instead of L3-External. Separate rules for external and internal attack sources provides separate reporting that makes investigating attack attempts easier.
To protect against SYN flood attacks from internal sources, create a separate DoS Protection policy rule that specifies your internal zones as the source zone instead of L3-External. Separate rules for external and internal attack sources provides separate reporting that makes investigating attack attempts easier. - In addition, configure Packet Buffer Protection for each data center zone to protect the firewall from single-session DoS attacks that can cause legitimate traffic to drop.