Create User-to-Data-Center Authentication Policy Rules
Table of Contents
10.2
Expand all | Collapse all
-
- What Is a Data Center Best Practice Security Policy?
- Why Do I Need a Data Center Best Practice Security Policy?
- Data Center Best Practice Methodology
- How Do I Deploy a Data Center Best Practice Security Policy?
- How to Assess Your Data Center
-
- Create the Data Center Best Practice Antivirus Profile
- Create the Data Center Best Practice Anti-Spyware Profile
- Create the Data Center Best Practice Vulnerability Protection Profile
- Create the Data Center Best Practice File Blocking Profile
- Create the Data Center Best Practice WildFire Analysis Profile
- Use Cortex XDR Agent to Protect Data Center Endpoints
- Create Data Center Traffic Block Rules
- Order the Data Center Security Policy Rulebase
- Maintain the Data Center Best Practice Rulebase
- Use Palo Alto Networks Assessment and Review Tools
Create User-to-Data-Center Authentication Policy Rules
Authenticate users to prevent unauthorized access to
data and resources in the data center, including using multi-factor
authentication for access to sensitive systems and data.
Authentication Policy rules force users
to prove that they are who they claim to be before they can access
data center services, applications, and other resources. Authentication
is especially important for protecting your most valuable assets
because if an attacker steals credentials and authenticates with
the firewall, the attacker may be able to access and compromise
any asset in your data center.
For access to sensitive servers
and for third-party user access to servers (for example, SAP development
contractors accessing SAP servers in the data center), implement Multi-Factor Authentication (MFA) to prevent
attackers from using stolen credentials to access those systems.
An Authentication policy with MFA would have prevented a number
of successful high-profile breaches over the past several years.
Before
you create Authentication Policy rules (PoliciesAuthentication), you must configure Authentication Policy dependencies
to tie the authentication method, the authentication type, how to
access the authentication server, and the use of Authentication
Portal to an Authentication Policy rule that specifies who can authenticate
on which servers using what services.
- Authenticate employee user groups and individuals
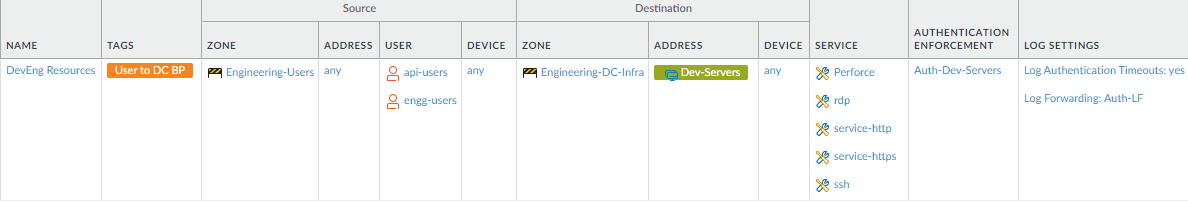
that have legitimate business reasons to use data center servers.This rule show how to authenticate user groups so that they can access services required for their business activities on the necessary servers. For example, engineers need to authenticate before they can access development servers and applications.
![]() To create this rule:
To create this rule:- Specify the engineering user groups that need to authenticate before they can access engineering servers in the data center, in this example, api-users and engg-users.
- Apply authentication for these user groups to data center development server access requests by creating a dynamic address group (Dev-Servers) for them and setting it as the Destination Address.
- Apply the Authentication rule to the services engineering groups need to use for business purposes, in this example Perforce, rdp, service-http, service-https, and ssh (developers may need to use SSH and RDP to access Linux servers and should authenticate before being allowed to access those servers). The services in your authentication rules depend on the services that the groups need to use.
- Configure an Authentication Enforcement Object (Auth-Dev-Servers) that specifies the authentication method and the Authentication Profile and add it to the rule.
- Log activity so that you can track and analyze rule violations, which may indicate an attempted attack.
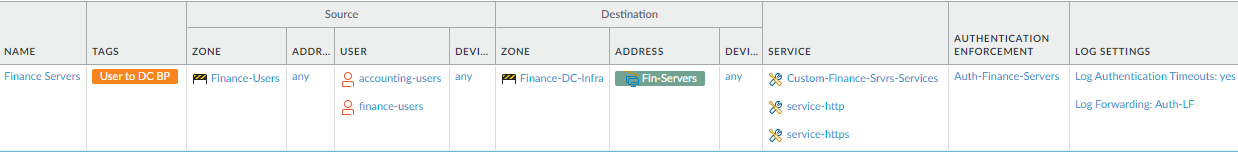
Another authentication use case is when a group requires access to a particular set of services. For example, Finance Department users need access to sensitive Payment Card Information (PCI) using particular services and should authenticate before being granted access. To authenticate users for those services, this rule uses a custom Service Group (ObjectsService Groups) that includes only services for which the firewall should authenticate Finance users.![]() To create this rule:
To create this rule:- Specify the user groups that need to authenticate before they can access finance servers in the data center, in this example, accounting-users and finance-users.
- Apply authentication for these user groups to data center finance server access requests by creating a dynamic address group (Fin-Servers) for them and setting it as the Destination Address.
- Apply the authentication rule to the services that Finance users need to use for business purposes, in this example service-http, service-https, and the services defined in the custom service group Custom-Finance-Srvrs-Services, so that users must authenticate before they can access these services.
- Configure an Authentication Enforcement Object (Auth-Finance-Servers) that specifies the authentication method and the Authentication Profile and add it to the rule.
- Log activity so that you can track and analyze rule violations, which may indicate an attempted attack.
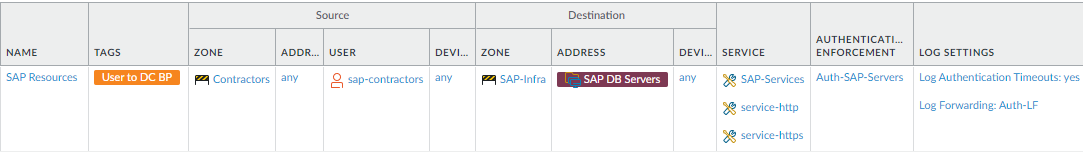
- Authenticate contractors, partners, customers, and other
non-employee groups that require data center access.This rule requires MFA for third-party user groups such as contractors, partners, and customers because you have less control over the business and security practices of their companies and personnel than you do over your employees. Requiring these users to authenticate with at least two factors protects your data center against credential theft at a third-party company.
![]() To create this rule:
To create this rule:- Apply the Authentication rule to the services SAP contractors need to use for business purposes. Create a custom service group (Sap-Services) to define the ports on which SAP contractors can authenticate and add other necessary services, in this example, service-http and service-https.
- Configure an Authentication Enforcement Object (Auth-SAP-Servers) that specifies the authentication method and the Authentication Profile and add it to the rule. In this case, the authentication type must be one that supports MFA, and you must Add an MFA server profile to the Authentication Profile (Factors tab) and perform the rest of the steps to configure MFA.Configure MFA to authenticate all users and user groups that access sensitive systems to protect against attackers with stolen credentials.
- Log activity so that you can track and analyze rule violations, which may indicate an attempted attack.
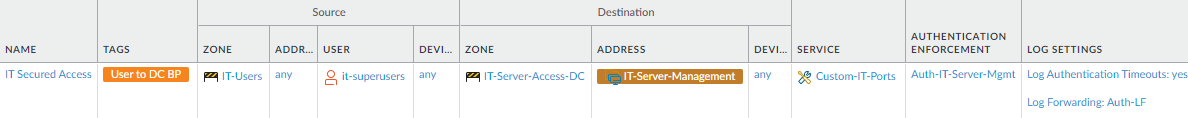
- Authenticate users who need specialized access, such
as IT personnel who need secured access to data center servers for
management and maintenance.This rule shows you how to configure authentication for users who have privileged accounts, which grant administrative access to critical systems. Because compromising the credentials of a privileged user hands an attacker the keys to your data center kingdom and its valuable assets, you need to protect against stolen credentials by requiring at least two factors of authentication to ensure that only legitimate users are granted access. This example shows how to authenticate the right IT users for access to data center server management interfaces.
![]() To create this rule:
To create this rule:- Specify the privileged account users who need to authenticate before they can access data center server management interfaces, in this example, the it-superusers group.
- Apply authentication for the user group to data center management interface access requests by creating a dynamic address group (IT-Server-Management static address group) for them and setting it as the Destination Address.
- Apply the Authentication rule to the services privileged IT personnel need to use for business purposes, in this example, the custom service group Custom-IT-Ports, which identifies all of the server management ports (which should be placed on the same subnet).
- Configure and apply an Authentication Enforcement Object (Auth-IT-Server-Mgmt in this example) that enforces requiring MFA (two factors) for authentication. Add an MFA server profile to the Authentication Profile (Factors tab) and perform the rest of the steps to configure MFA. Using MFA is critical because you need to be certain of the identity of each IT user who has a privileged account since they have access to device management.To further reduce the opportunity for an attacker to compromise the data center using stolen credentials or an opportune moment when a workstation is unattended but not locked, when you configure MFA, configure authentication timestamps for the authentication factors. With valuable data center assets, it’s best to prioritize securing services and applications.
- Log activity so that you can track and analyze rule violations.
IT personnel also manage switches, routers, and other devices in the data center. If the same group of IT users manages those resources, you can add them to the destination zone and address so that the rule authenticates IT superusers before they can access the management interfaces of those devices. If different IT user groups manage different sets of data center resources, create separate, tight security policy rules and corresponding authentication policy and decryption policy rules for each user group.Do not send credentials in cleartext. For example, if you use RADIUS, use a supported EAP method to transport credentials securely inside TLS.