Advanced DNS Security Powered by Precision AI®
Enable Advanced DNS Security (Strata Cloud Manager)
Table of Contents
Enable Advanced DNS Security (Strata Cloud Manager)
- Use the credentials associated with your Palo Alto Networks support account and log in to the Strata Cloud Manager on the hub.Verify that a DNS Security and a Threat Prevention license is active. Select ConfigurationNGFW and Prisma AccessOverview and click the license usage terms link in the License panel. You should see green check marks next to the following security services: Antivirus, Anti-Spyware, Vulnerability Protection, and DNS Security.Update or create a new DNS Security profile to enable real-time Advanced DNS Security queries. Typically, this is your existing DNS Security profile used for the DNS Security configuration.
- Select an existing DNS Security profile or Add a new one (ConfigurationNGFW and Prisma AccessSecurity ServicesDNS Security).
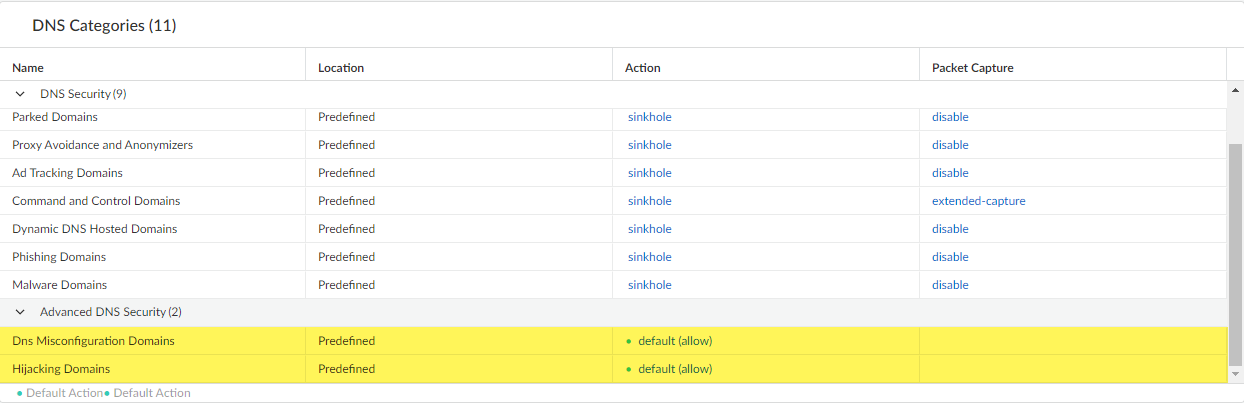
- Select your DNS Security profile and then go to DNS Categories.
![]()
- For each Advanced DNS Security domain category, specify a policy Action to take when a corresponding domain type is detected. There are currently two analysis engines available: DNS Misconfiguration Domains and Hijacking Domains.Policy Action Options:
- allow—The DNS query is allowed.You can configure Strata Cloud Manager to generate an alert when the applicable domain type is detected by setting the action to allow and the log severity to informational.
- block—The DNS query is blocked.
- sinkhole—Forges a DNS response for a DNS query targeting a detected malicious domain. This directs the resolution of the malicious domain name to a specific IP address (referred to as the Sinkhole IP), which is embedded as the response. The default Sinkhole IP address is set to access a Palo Alto Networks server. Palo Alto Networks can automatically refresh this IP address through content updates.
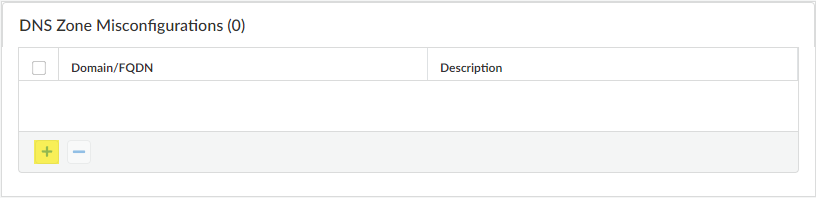
(Optional) Specify any public-facing parent domains within your organization that you want Advanced DNS Security to analyze and monitor for the presence of misconfigured domains. Misconfigured domains are inadvertently created by domain owners who point alias records to third party domains using CNAME, MX, NS record types, using entries that are no longer valid, allowing an attacker to take over the domain by registering the expired or unused domains.TLDs (top-level domains) and root level domains cannot be added to the DNS Zone Misconfigurations list.- Select a DNS Security profile (ConfigurationNGFW and Prisma AccessSecurity ServicesDNS Security) that contains an Advanced DNS Security configuration.
- In the DNS Zone Misconfigurations section, add public-facing parent domains with an optional description to assist you in identifying domain usage or ownership within your organization.Entries must have a "." contained in the domain using the following format (e.g. paloaltonetworks.com), otherwise it gets parsed as a hostname, which is considered a private domain.
![]()
- Click OK to exit and save the DNS Security security profile.
(Optional) Monitor activity on Strata Cloud Manager for DNS queries that have been detected using Advanced DNS Security. DNS Security Categories analyzed using Advanced DNS Security real-time analysis of the DNS response packet have the prefix ‘adns’ followed by the category. For example, adns-dnsmisconfig, whereby ‘dnsmisconfig’ indicates the supported DNS category type. If the DNS domain category was determined by analyzing the DNS request packet, the specified category is displayed with the prefix ‘dns’ followed by the category. For example, ‘dns-grayware.’- Access the Advanced DNS Security test domains to verify that the policy action for a given threat type is being enforced.Select Log Viewer. You can filter the threat logs based on the specific type of Advanced DNS Security domain category, for example threat_category.value = 'adns-hijacking', whereby the variable adns-hijacking indicates DNS queries that have been categorized as a malicious DNS hijacking attempt by Advanced DNS Security. The following Advanced DNS Security threat categories available in the logs:Advanced DNS Security Categories
- DNS Hijacking—adns-hijackingDNS Hijacking domains have a threat ID of (UTID: 109,004,100).
- DNS
Misconfiguration—adns-dnsmisconfigDNS Misconfiguration domains have three threats IDs, which correspond to three variants of DNS misconfiguration domains types: dnsmisconfig_zone (UTID: 109,004,200), dnsmisconfig_zone_dangling (UTID: 109,004,201), and dnsmisconfig_claimable_nx (UTID: 109,004,202). You can constrain the search by cross-referencing a Threat-ID value that corresponds to a specific DNS misconfiguration domain type. For example, threat_category.value = 'adns-dnsmisconfig' and Threat ID = 109004200, whereby 109004200 indicates the Threat ID of a DNS misconfiguration domain that does not route traffic to an active domain due to a DNS server configuration issue.
DNS Categories analyzed using Advanced DNS Security enhanced response analysis.- DNS —adns-benign
- Malware Domains —adns-malware
- Command and Control Domains—adns-c2
- Phishing Domains—adns-phishing
- Dynamic DNS Hosted Domains—adns-ddns
- Newly Registered Domains—adns-new-domain
- Grayware Domains—adns-grayware
- Parked Domains—adns-parked
- Proxy Avoidance and Anonymizers—adns-proxy
- Ad Tracking Domains—adns-adtracking
If the DNS query does not complete within the specified timeout period for Advanced DNS Security, the DNS Security categorization will be used, when possible. In those instances, the legacy notation for the category is used, for example, instead of adns-malware, it will be categorized as dns-malware, indicating that the DNS Security categorization value was used.Select a log entry to view the details of the DNS query.The DNS Category is displayed under the General pane of the detailed log view. In addition, you can see other aspects if the threat, including the origin URL, the specific threat type, and associated characteristics.(Optional) Retrieve a list of misconfigured domains and hijacked domains detected by the Advanced DNS Security service. The misconfigured domains are based on the public-facing parent domain entries added to DNS Zone Misconfigurations. This is available as a request through AI Canvas.