Orchestrate a VM-Series Firewall Deployment in Azure
Table of Contents
11.1
Expand all | Collapse all
-
- VM-Series Deployments
- VM-Series in High Availability
- IPv6 Support on Public Cloud
- Enable Jumbo Frames on the VM-Series Firewall
- Hypervisor Assigned MAC Addresses
- Custom PAN-OS Metrics Published for Monitoring
- Interface Used for Accessing External Services on the VM-Series Firewall
- PacketMMAP and DPDK Driver Support
- Enable NUMA Performance Optimization on the VM-Series
- Enable ZRAM on the VM-Series Firewall
- Additional XFF IP Logging
-
- Licensing and Prerequisites for Virtual Systems Support on VM-Series
- System Requirements for Virtual Systems Support on VM-Series
- Enable Multiple Virtual Systems Support on VM-Series Firewall
- Enable Multiple Virtual Systems Support on VM-Series in Panorama Console
- Enable Multiple Virtual Systems Support Using Bootstrap Method
-
- VM-Series Firewall Licensing
- Create a Support Account
- Serial Number and CPU ID Format for the VM-Series Firewall
- Use Panorama-Based Software Firewall License Management
-
- Activate Credits
- Create a Deployment Profile
- Activate the Deployment Profile
- Manage a Deployment Profile
- Register the VM-Series Firewall (Software NGFW Credits)
- Provision Panorama
- Migrate Panorama to a Software NGFW License
- Transfer Credits
- Renew Your Software NGFW Credits
- Deactivate License (Software NGFW Credits)
- Delicense Ungracefully Terminated Firewalls
- Set the Number of Licensed vCPUs
- Customize Dataplane Cores
- Migrate a Firewall to a Flexible VM-Series License
-
- Generate Your OAuth Client Credentials
- Manage Deployment Profiles Using the Licensing API
- Create a Deployment Profile Using the Licensing API
- Update a Deployment Profile Using the Licensing API
- Get Serial Numbers Associated with an Authcode Using the API
- Deactivate a VM-Series Firewall Using the API
- What Happens When Licenses Expire?
-
- Supported Deployments on VMware vSphere Hypervisor (ESXi)
-
- Plan the Interfaces for the VM-Series for ESXi
- Provision the VM-Series Firewall on an ESXi Server
- Perform Initial Configuration on the VM-Series on ESXi
- Add Additional Disk Space to the VM-Series Firewall
- Use VMware Tools on the VM-Series Firewall on ESXi and vCloud Air
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Use the VM-Series CLI to Swap the Management Interface on ESXi
- Configure Link Aggregation Control Protocol
- ESXi Simplified Onboarding
-
-
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (North-South)
- Components of the VM-Series Firewall on NSX-T (North-South)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Deploy the VM-Series Firewall
- Direct Traffic to the VM-Series Firewall
- Apply Security Policy to the VM-Series Firewall on NSX-T
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Extend Security Policy from NSX-V to NSX-T
-
- Components of the VM-Series Firewall on NSX-T (East-West)
- VM-Series Firewall on NSX-T (East-West) Integration
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (East-West)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Add a Service Chain
- Direct Traffic to the VM-Series Firewall
- Apply Security Policies to the VM-Series Firewall on NSX-T (East-West)
- Use vMotion to Move the VM-Series Firewall Between Hosts
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Create Dynamic Address Groups
- Create Dynamic Address Group Membership Criteria
- Generate Steering Policy
- Generate Steering Rules
- Delete a Service Definition from Panorama
- Migrate from VM-Series on NSX-T Operation to Security Centric Deployment
- Extend Security Policy from NSX-V to NSX-T
- Use In-Place Migration to Move Your VM-Series from NSX-V to NSX-T
-
-
- Deployments Supported on AWS
-
- Planning Worksheet for the VM-Series in the AWS VPC
- Launch the VM-Series Firewall on AWS
- Launch the VM-Series Firewall on AWS Outpost
- Create a Custom Amazon Machine Image (AMI)
- Encrypt EBS Volume for the VM-Series Firewall on AWS
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable CloudWatch Monitoring on the VM-Series Firewall
- Publish ENA Network Performance Metrics to AWS CloudWatch
- VM-Series Firewall Startup and Health Logs on AWS
- Simplified Onboarding of VM-Series Firewall on AWS
- Use AWS Secrets Manager to Store VM-Series Certificates
- AWS Shared VPC Monitoring
- Use Case: Secure the EC2 Instances in the AWS Cloud
- Use Case: Use Dynamic Address Groups to Secure New EC2 Instances within the VPC
-
- Intelligent Traffic Offload
- Software Cut-through Based Offload
-
- Deployments Supported on Azure
- Deploy the VM-Series Firewall from the Azure Marketplace (Solution Template)
- Simplified Onboarding of VM-Series Firewall on Azure
- Deploy the VM-Series Firewall from the Azure China Marketplace (Solution Template)
- Deploy the VM-Series with the Azure Gateway Load Balancer
- Create a Custom VM-Series Image for Azure
- Deploy the VM-Series Firewall on Azure Stack
- Deploy the VM-Series Firewall on Azure Stack HCI
- Enable Azure Application Insights on the VM-Series Firewall
- Azure Health Monitoring
- Set up Active/Passive HA on Azure
- Use Azure Key Vault to Store VM-Series Certificates
- Use the ARM Template to Deploy the VM-Series Firewall
-
- About the VM-Series Firewall on Google Cloud Platform
- Supported Deployments on Google Cloud Platform
- Create a Custom VM-Series Firewall Image for Google Cloud Platform
- Prepare to Set Up VM-Series Firewalls on Google Public Cloud
-
- Deploy the VM-Series Firewall from Google Cloud Platform Marketplace
- Management Interface Swap for Google Cloud Platform Load Balancing
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable Google Stackdriver Monitoring on the VM Series Firewall
- Enable VM Monitoring to Track VM Changes on Google Cloud Platform (GCP)
- Use Dynamic Address Groups to Secure Instances Within the VPC
- Use Custom Templates or the gcloud CLI to Deploy the VM-Series Firewall
- Enable Session Resiliency on VM-Series for GCP
- Google Cloud Network Security Integration (NSI) with VM-Series Firewalls
- Secure Boot Support for VM-Series on GCP
-
- Prepare Your ACI Environment for Integration
-
-
- Create a Virtual Router and Security Zone
- Configure the Network Interfaces
- Configure a Static Default Route
- Create Address Objects for the EPGs
- Create Security Policy Rules
- Create a VLAN Pool and Domain
- Configure an Interface Policy for LLDP and LACP for East-West Traffic
- Establish the Connection Between the Firewall and ACI Fabric
- Create a VRF and Bridge Domain
- Create an L4-L7 Device
- Create a Policy-Based Redirect
- Create and Apply a Service Graph Template
-
- Create a VLAN Pool and External Routed Domain
- Configure an Interface Policy for LLDP and LACP for North-South Traffic
- Create an External Routed Network
- Configure Subnets to Advertise to the External Firewall
- Create an Outbound Contract
- Create an Inbound Web Contract
- Apply Outbound and Inbound Contracts to the EPGs
- Create a Virtual Router and Security Zone for North-South Traffic
- Configure the Network Interfaces
- Configure Route Redistribution and OSPF
- Configure NAT for External Connections
-
-
- Choose a Bootstrap Method
- VM-Series Firewall Bootstrap Workflow
- Bootstrap Package
- Bootstrap Configuration Files
- Bootstrapping VM-Series in Virtual Metadata Collector Mode
- Generate the VM Auth Key on Panorama
- Create the bootstrap.xml File
- Prepare the Licenses for Bootstrapping
- Prepare the Bootstrap Package
- Bootstrap the VM-Series Firewall on AWS
- Bootstrap the VM-Series Firewall on Azure
- Bootstrap the VM-Series Firewall on Azure Stack HCI
- Bootstrap the VM-Series Firewall on Google Cloud Platform
- Verify Bootstrap Completion
- Bootstrap Errors
Orchestrate a VM-Series Firewall Deployment in Azure
Learn how to orchestrate a VM-Series firewall deployment
in Azure.
You can create a maximum of ten orchestrated
deployments. Additionally, each orchestrated deployment supports
up to 100 front-end applications.
Azure China and Azure
Government are not supported.
- Create a service principal.Onboard your created service principal credentials to give the Panorama Plugin permissions to make necessary API calls to orchestrate your deployment
- Select SetupService PrincipalAdd.
- Enter a Name and an optional Description to identify the service account.
- Enter the Subscription ID for the Azure subscription you want to monitor.You must login to your Azure portal to get this subscription ID.
- Enter the Client ID.The client ID is the Application ID associated with your Azure Active Directory application.
- Enter the Client Secret and re-enter it to confirm.
- Enter the Tenant ID.The tenant ID is the Directory ID you saved when you set up the Active Directory application.
- Click Validate to verify that the keys and IDs you entered are valid, and Panorama can communicate with the Azure subscription using the API.It can take up to a minute to validate. You can update the page to check your progress.
- When the service principal is valid, commit your changes.The commit ensures the service principal is available when you configure the deployment.
![]()
![]()
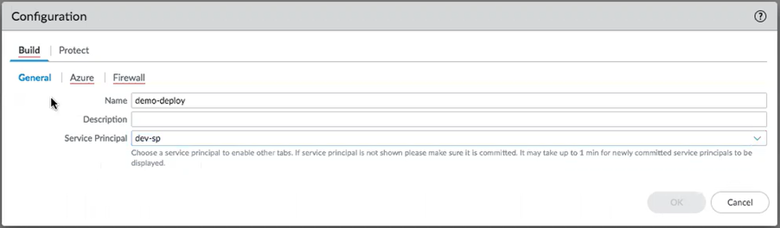
Configure your Azure deploymenet.- Select Deployments and Add a configuration.Select BuildGeneral.
- Supply a Name and an optional Description.
- Choose a service principal from the drop list.You must select a valid service principal to enable the Azure tab.If you don’t see your service principal, return to Step 1 and ensure the service principal is valid and committed.
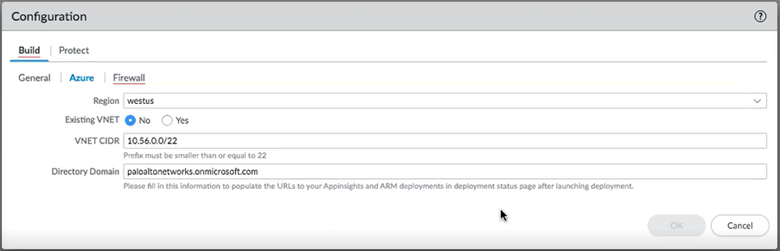
![]() On the BuildAzure tab, select a region.The drop list is dynamic—it lists all regions that have a Palo Alto Networks VM-Series Next Generation Firewall image.
On the BuildAzure tab, select a region.The drop list is dynamic—it lists all regions that have a Palo Alto Networks VM-Series Next Generation Firewall image.- Existing VNET.
- Select No to create a new VNET.The plugin uses the VNET CIDR and Directory Domain to create a VNET for you.
- Select Yes to indicate an existing VNET.
- VNET CIDR—Enter your CIDR range. The prefix must be smaller than or equal to /22. For example, 192.168.0.0/22.
- Directory Domain—See Find Your Azure Directory Domain Name. This string is part of the URL for all resources in the subscription, and it helps the plugin link to your deployments.
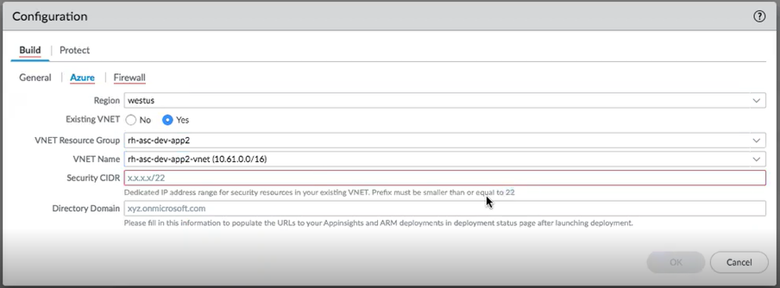
![]() If you selectYes the plugin asks for the VNET Resource Group, the VNET Name, the Security CIDR, and the Directory Domain.
If you selectYes the plugin asks for the VNET Resource Group, the VNET Name, the Security CIDR, and the Directory Domain.- VNET Resource Group—Choose from a list of all resource groups in your selected region.
- VNET Name—Choose from a list of VNETS in your chosen resource group.
- Security CIDR—Enter your CIDR range. The prefix must be smaller than or equal to /22. For example, 192.168.0.0/22.
- Directory Domain—See Find Your Azure Directory Domain Name. This string is part of the URL for all resources in the subscription, and it helps the plugin link to your deployments.
The VNET Resource Group and VNET name help the plugin locate your existing VNET. Anything the plugin deploys goes into a resource group that the plugin manages.![]() Configure the VM-Series firewall stacks for your deployment.You can deploy the Hub stack to protect Outbound/East-West traffic. You can deploy the Inbound stack to protect inbound traffic. You can also deploy both stacks if all traffic flows need to be protected.The configuration parameters are the same for both stacks.
Configure the VM-Series firewall stacks for your deployment.You can deploy the Hub stack to protect Outbound/East-West traffic. You can deploy the Inbound stack to protect inbound traffic. You can also deploy both stacks if all traffic flows need to be protected.The configuration parameters are the same for both stacks.- License Type—Select BYOL, Bundle 1, or Bundle 2.
- License Authcode—(BYOL only). Enter the authcode sent in your Welcome letter.
- VM Size
- The drop list displays the VM sizes that correlate with the authcode you entered.
- Bundle1 or Bundle2—Choose any VM size.
Existing Device Group—The device group must be unique across both stacks and deployments. That is, you need a separate dedicated device group for each stack in each deployment.If you select No the plugin creates a device group.If you select Yes, select an existing device group from the dropdown list.- Min Firewalls— A value between 1 and 25 for a VMSS.
- Max Firewall— A value between 1 and 25 for a VMSS.
Select BuildFirewallBasic to configure information common to both Stacks.For Image Type, select Marketplace Image or Custom Image.- Image—(custom image only) The dropdown list displays all images in your chosen resource group.
- Software Version—(Marketplace Image) Only valid software versions are displayed. Consult the Compatibility Matrix for the minimum PAN-OS version.
- Username—The administrator user name for the firewall you create. The name must be legal for both VM-Series firewall and Azure. Refer to What are the user name requirments when creating a VM?
- Password—The administrator password for the firewall you create. The password must meet the character and length requirements (31 characters) for both VM-Series firewall and Azure. Refer to What are the password requirements when creating a VM?.
- Confirm Password—Re-enter your password.
- Primary Panorama IP—Specify the Panorama IP address the firewall can use to connect to the Panorama when it boots up. Choose between the public or private IP address displayed in the dropdown list, or type in the Panorama IP address.
- Secondary Panorama IP—(Only if Panorama is in HA setup.) Specify the Secondary Panorama IP the firewall can use to connect to the Panorama when it boots up. Choose from dropdown list or type in the correct IP.
- Configure Device Certificate PIN. Because these values are encrypted you must enter and confirm each value.
- Device Certificate PIN ID—The device certificate ID.
- Confirm Device Certificate PIN ID
- Device Certificate PIN Value—The certificate PIN value.
- Confirm Device Certificate PIN Value
Select BuildFirewallAdvanced optional default values.Check Advanced to edit the default values.- Autoscaling Metric—Default is Data Plane CPU Util Percent.
- Scale In Threshold—Accept the default or define a scale in thresholdt.
- Scale Out Threshold—Accept the default or define a scale in threshold.
- Jumbo Frame—Disabled by default.
Click OK and commit your changes. Refresh the page until you can see the Deploy button, and click Deploy to launch the deployment. Once the deployment starts, information is written to the Deployments page.Deployment takes 15-20 minutes to complete.If there is an entry in the Deployment Status column, click the hyperlink to view the deployment details.The possible status messages are:- Commit changes—You have added a deployment for the first time but have not yet committed the changes.Every configuration change for the deployment must be committed so that the plugin can pick up your changes.
- Deploying—The plugin is deploying or updating the deployment. For more information, click the hyperlink to view the detailed status.
- Failure—Deployment has failed. Click the hyperlink and view the Detailed Status for the Security stack.
- Not Deployed—The plugin is ready to deploy the configuration, but the deployment has not begun.
- Success—The plugin has successfully deployed the Security stack and the firewalls have connected to Panorama. The firewalls can pass traffic.
- Warning—Deployment has successfully finished but something external to the deployment has failed. For example, you might see this message:FWs have not connected after 20 minutes of the deployment completing.Click the hyperlink and view the Security stack.
Once the deployment is deployed, the plugin allows you to modify a certain subset of parameters. Once the changes have been made, you must do a commit before clicking the Redeploy button. When an update happens, the plugin makes sure the Panorama config is created and accurate.- Deploy—After you commit your initial configuration, select Deploy to launch the deployment.
- Redeploy—Modify a deployment, commit your changes, and select Redeploy.You must commit changes to the deployment before you click Redeploy.
- Undeploy—Delete a deployment, but keep the configuration so it can be redeployed at a later time.
To remove an existing deployment and its configuration, check a deployment and select Delete at the bottom of the Deployments page.Select AzureDeployments to view deployment status.- The Resource Group column displays resource groups the plugin has created.
- The firewall’s management interface uses the Firewall Access IP to connect to Panorama. You must whitelist this address to ensure that Panorama can connect with Panorama to get the needed configuration.If Panorama is deployed in a Public Cloud, make sure to add the Firewall Access IP to the Panorama security group.See Ports Used for Panorama to determine which ports you need to open to allow traffic.
- Open the link in the Deployment Status column for additional details for each stack.
- Hub-Stack—The Hub stack Public IP matches the Firewall Access IP in the deployment summary because the NAT gateway is the same for egress traffic from the deployment and the management traffic from the firewalls.All outbound and East-West traffic should be routed to the Egress Private IP for inspection. You can direct traffic to this address if you configured UDRs.
- Inbound-Stack—The Private IP is the address on the Azure internal load balancer that fronts the firewalls. You can direct traffic to this address if you are configuring UDRs.
- Follow the links to view deployment information and Application Insights on Azure.
- The Deployment details can show Success, Warning, and Failure messages
Configure inbound protection for backend TCP/UDP applications.The public load balancer that fronts the inbound firewall stack is the entry point for any back-end UDP or TCP applications. Add the following configuration to allow the plugin to manage the necessary load balancer and firewall configuration to route to your backend application.- Select AzureDeployments and select your deployment.Select the Protect tab and click Add.Supply the application Name and choose a Protocol.Enter the protection details:
- Frontend IP Type—Select one of New Public IP, Existing Frontend, and Existing Public IP.If you select Existing Frontend, the Frontend Name lists all known front ends on the load balancer.
- Resource Group—(Existing Public IP only) From the dropdown list, select the resource group where your desired frontend IP address exists.
- IP Name—(Existing Public IP only) Use to map IP to a frontend on the load balancer, configure the load balancer, and create a NAT rule.
- Frontend Port—Add the frontend port that should be configured to receive traffic on the public load balancer.
- Backend IP—Add the IP address of your backend application.
- Backend Port—Add the port your backend application is expecting to receive traffic on.
Click OK.Commit to add the configuration on the load balancer and push to the firewalls.