Deploying the VM-Series Firewall on Tencent Cloud
Table of Contents
11.1
Expand all | Collapse all
-
- VM-Series Deployments
- VM-Series in High Availability
- IPv6 Support on Public Cloud
- Enable Jumbo Frames on the VM-Series Firewall
- Hypervisor Assigned MAC Addresses
- Custom PAN-OS Metrics Published for Monitoring
- Interface Used for Accessing External Services on the VM-Series Firewall
- PacketMMAP and DPDK Driver Support
- Enable NUMA Performance Optimization on the VM-Series
- Enable ZRAM on the VM-Series Firewall
- Additional XFF IP Logging
-
- Licensing and Prerequisites for Virtual Systems Support on VM-Series
- System Requirements for Virtual Systems Support on VM-Series
- Enable Multiple Virtual Systems Support on VM-Series Firewall
- Enable Multiple Virtual Systems Support on VM-Series in Panorama Console
- Enable Multiple Virtual Systems Support Using Bootstrap Method
-
- VM-Series Firewall Licensing
- Create a Support Account
- Serial Number and CPU ID Format for the VM-Series Firewall
- Use Panorama-Based Software Firewall License Management
-
- Activate Credits
- Create a Deployment Profile
- Activate the Deployment Profile
- Manage a Deployment Profile
- Register the VM-Series Firewall (Software NGFW Credits)
- Provision Panorama
- Migrate Panorama to a Software NGFW License
- Transfer Credits
- Renew Your Software NGFW Credits
- Deactivate License (Software NGFW Credits)
- Delicense Ungracefully Terminated Firewalls
- Set the Number of Licensed vCPUs
- Customize Dataplane Cores
- Migrate a Firewall to a Flexible VM-Series License
-
- Generate Your OAuth Client Credentials
- Manage Deployment Profiles Using the Licensing API
- Create a Deployment Profile Using the Licensing API
- Update a Deployment Profile Using the Licensing API
- Get Serial Numbers Associated with an Authcode Using the API
- Deactivate a VM-Series Firewall Using the API
- What Happens When Licenses Expire?
-
- Supported Deployments on VMware vSphere Hypervisor (ESXi)
-
- Plan the Interfaces for the VM-Series for ESXi
- Provision the VM-Series Firewall on an ESXi Server
- Perform Initial Configuration on the VM-Series on ESXi
- Add Additional Disk Space to the VM-Series Firewall
- Use VMware Tools on the VM-Series Firewall on ESXi and vCloud Air
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Use the VM-Series CLI to Swap the Management Interface on ESXi
- Configure Link Aggregation Control Protocol
- ESXi Simplified Onboarding
-
-
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (North-South)
- Components of the VM-Series Firewall on NSX-T (North-South)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Deploy the VM-Series Firewall
- Direct Traffic to the VM-Series Firewall
- Apply Security Policy to the VM-Series Firewall on NSX-T
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Extend Security Policy from NSX-V to NSX-T
-
- Components of the VM-Series Firewall on NSX-T (East-West)
- VM-Series Firewall on NSX-T (East-West) Integration
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (East-West)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Add a Service Chain
- Direct Traffic to the VM-Series Firewall
- Apply Security Policies to the VM-Series Firewall on NSX-T (East-West)
- Use vMotion to Move the VM-Series Firewall Between Hosts
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Create Dynamic Address Groups
- Create Dynamic Address Group Membership Criteria
- Generate Steering Policy
- Generate Steering Rules
- Delete a Service Definition from Panorama
- Migrate from VM-Series on NSX-T Operation to Security Centric Deployment
- Extend Security Policy from NSX-V to NSX-T
- Use In-Place Migration to Move Your VM-Series from NSX-V to NSX-T
-
-
- Deployments Supported on AWS
-
- Planning Worksheet for the VM-Series in the AWS VPC
- Launch the VM-Series Firewall on AWS
- Launch the VM-Series Firewall on AWS Outpost
- Create a Custom Amazon Machine Image (AMI)
- Encrypt EBS Volume for the VM-Series Firewall on AWS
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable CloudWatch Monitoring on the VM-Series Firewall
- Publish ENA Network Performance Metrics to AWS CloudWatch
- VM-Series Firewall Startup and Health Logs on AWS
- Simplified Onboarding of VM-Series Firewall on AWS
- Use AWS Secrets Manager to Store VM-Series Certificates
- AWS Shared VPC Monitoring
- Use Case: Secure the EC2 Instances in the AWS Cloud
- Use Case: Use Dynamic Address Groups to Secure New EC2 Instances within the VPC
-
- Intelligent Traffic Offload
- Software Cut-through Based Offload
-
- Deployments Supported on Azure
- Deploy the VM-Series Firewall from the Azure Marketplace (Solution Template)
- Simplified Onboarding of VM-Series Firewall on Azure
- Deploy the VM-Series Firewall from the Azure China Marketplace (Solution Template)
- Deploy the VM-Series with the Azure Gateway Load Balancer
- Create a Custom VM-Series Image for Azure
- Deploy the VM-Series Firewall on Azure Stack
- Deploy the VM-Series Firewall on Azure Stack HCI
- Enable Azure Application Insights on the VM-Series Firewall
- Azure Health Monitoring
- Set up Active/Passive HA on Azure
- Use Azure Key Vault to Store VM-Series Certificates
- Use the ARM Template to Deploy the VM-Series Firewall
-
- About the VM-Series Firewall on Google Cloud Platform
- Supported Deployments on Google Cloud Platform
- Create a Custom VM-Series Firewall Image for Google Cloud Platform
- Prepare to Set Up VM-Series Firewalls on Google Public Cloud
-
- Deploy the VM-Series Firewall from Google Cloud Platform Marketplace
- Management Interface Swap for Google Cloud Platform Load Balancing
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable Google Stackdriver Monitoring on the VM Series Firewall
- Enable VM Monitoring to Track VM Changes on Google Cloud Platform (GCP)
- Use Dynamic Address Groups to Secure Instances Within the VPC
- Use Custom Templates or the gcloud CLI to Deploy the VM-Series Firewall
- Enable Session Resiliency on VM-Series for GCP
- Google Cloud Network Security Integration (NSI) with VM-Series Firewalls
- Secure Boot Support for VM-Series on GCP
-
- Prepare Your ACI Environment for Integration
-
-
- Create a Virtual Router and Security Zone
- Configure the Network Interfaces
- Configure a Static Default Route
- Create Address Objects for the EPGs
- Create Security Policy Rules
- Create a VLAN Pool and Domain
- Configure an Interface Policy for LLDP and LACP for East-West Traffic
- Establish the Connection Between the Firewall and ACI Fabric
- Create a VRF and Bridge Domain
- Create an L4-L7 Device
- Create a Policy-Based Redirect
- Create and Apply a Service Graph Template
-
- Create a VLAN Pool and External Routed Domain
- Configure an Interface Policy for LLDP and LACP for North-South Traffic
- Create an External Routed Network
- Configure Subnets to Advertise to the External Firewall
- Create an Outbound Contract
- Create an Inbound Web Contract
- Apply Outbound and Inbound Contracts to the EPGs
- Create a Virtual Router and Security Zone for North-South Traffic
- Configure the Network Interfaces
- Configure Route Redistribution and OSPF
- Configure NAT for External Connections
-
-
- Choose a Bootstrap Method
- VM-Series Firewall Bootstrap Workflow
- Bootstrap Package
- Bootstrap Configuration Files
- Bootstrapping VM-Series in Virtual Metadata Collector Mode
- Generate the VM Auth Key on Panorama
- Create the bootstrap.xml File
- Prepare the Licenses for Bootstrapping
- Prepare the Bootstrap Package
- Bootstrap the VM-Series Firewall on AWS
- Bootstrap the VM-Series Firewall on Azure
- Bootstrap the VM-Series Firewall on Azure Stack HCI
- Bootstrap the VM-Series Firewall on Google Cloud Platform
- Verify Bootstrap Completion
- Bootstrap Errors
Deploying the VM-Series Firewall on Tencent Cloud
This is the procedure to deploy the VM-Series firewall on Tencent Cloud web console.
Following are the steps to deploy the VM-Series firewall on the Tencent cloud:
- Begin with creating a VPC and Subnets on Tencent Cloud. Perform the following steps:By default, the Tencent cloud webpage is in Chinese language. Translate the webpage to English, and then proceed with the deployment procedure.
- Go to the Tencent console and click Log In.
![]()
- Click Sub-user.
![]()
- Enter your Sub-User login credentials.
- Click Login.
- Click Console.
![]()
- Go to Private Networks > New.
![]()
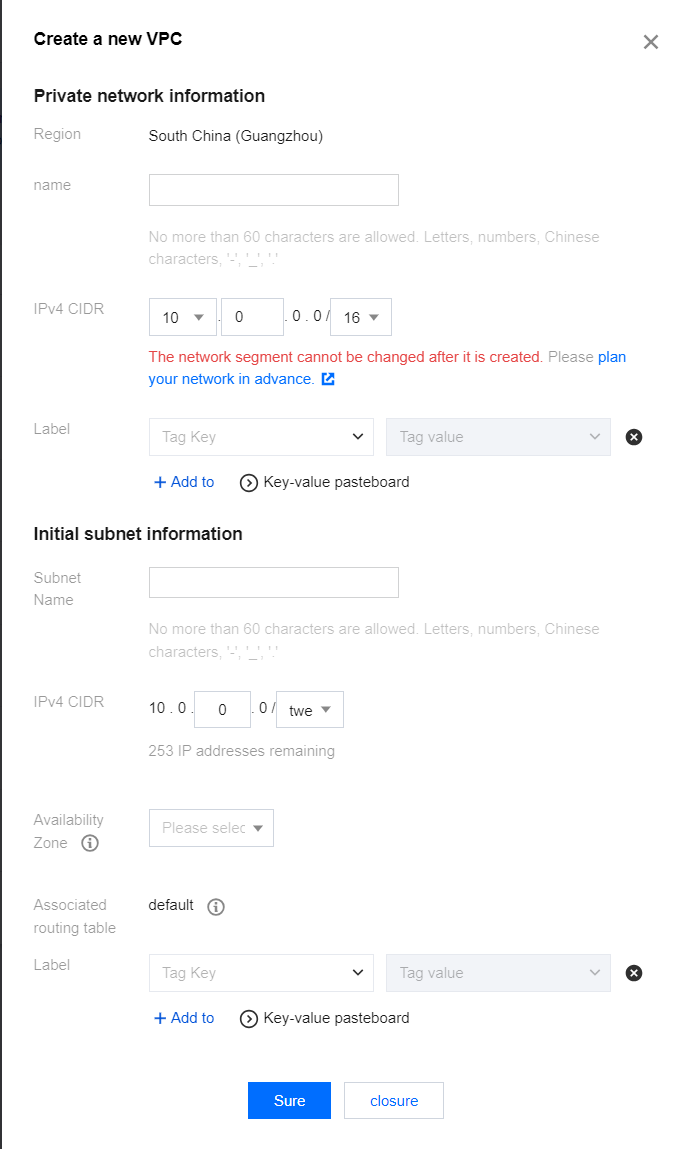
- In the Private Network > Information section, enter the VPC name and CIDR details.
![]()
- In the Initial Subnet Information section, enter the subnet name and IP address details.
- Click Save.
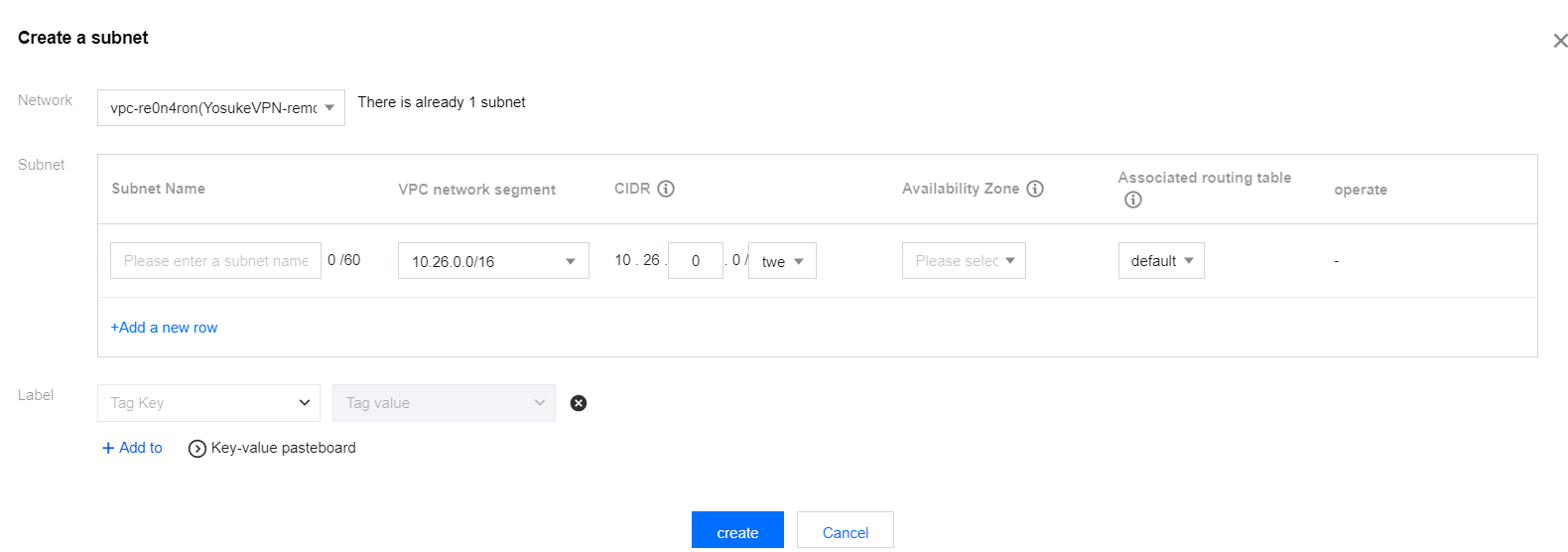
To create Subnets, perform the following steps:- In the Private Network menu, click subnets.
![]()
- Click New.
- Select your VPC.
- Enter the subnet Name and Availability zone.
- Click Save.
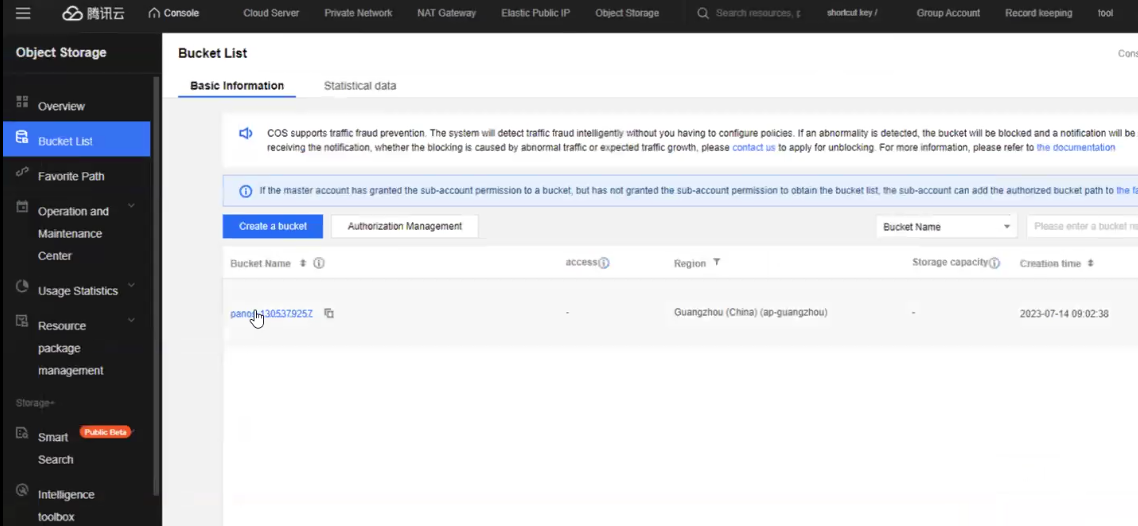
You must create at least 3 subnets namely management, untrust, and trust subnets for your VPC.Upload the PA-VM qcow2 image file on the Tencent Cloud.You must have Panorama version 10.2.1 or above.- In your Tencent console, click Object Storage.
- Go to Bucket List > Upload Files > Select Files.
![]()
- Select the image file from your local machine, and then click Upload.
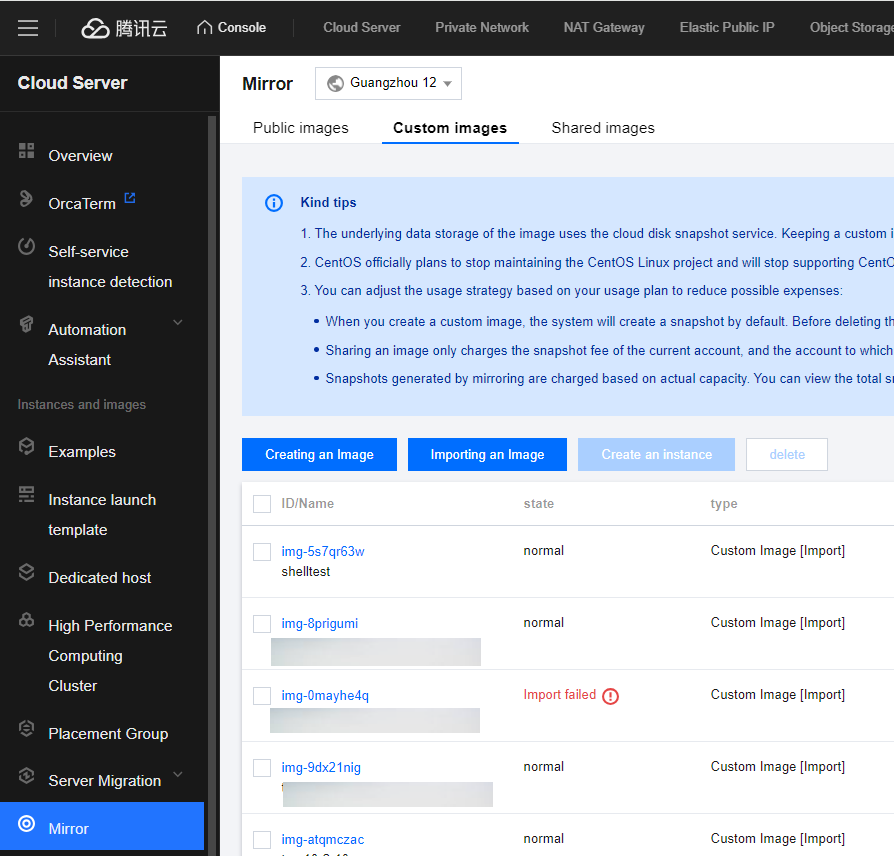
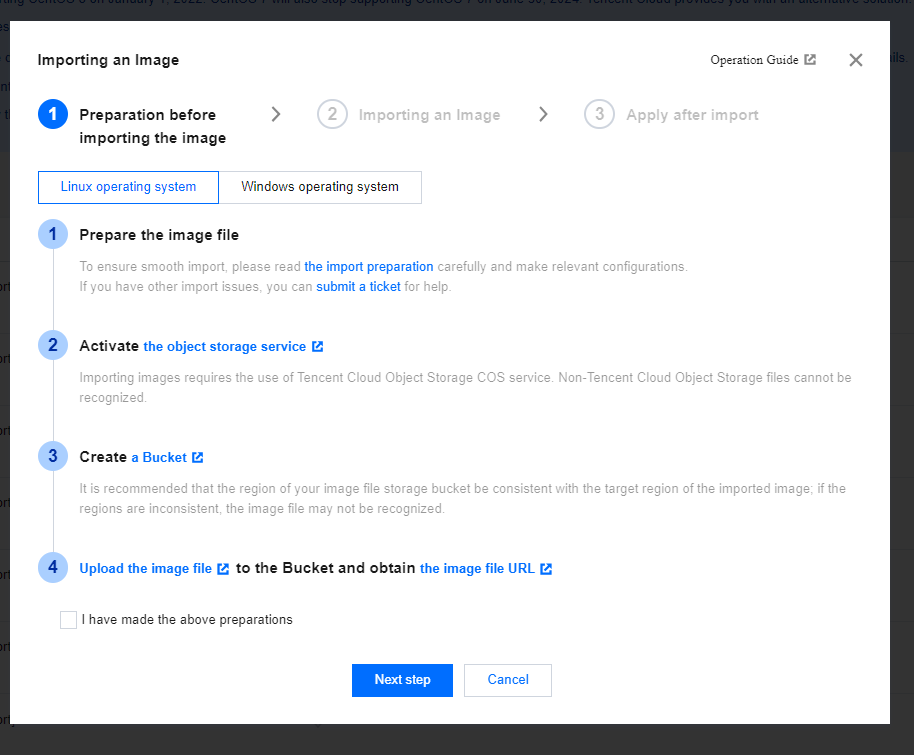
Import the image file on the cloud server.- Go to the Cloud server > Mirror > Import an image.
![]()
- Select the I have made the above preparations checkbox.
![]()
- Click Next Step.
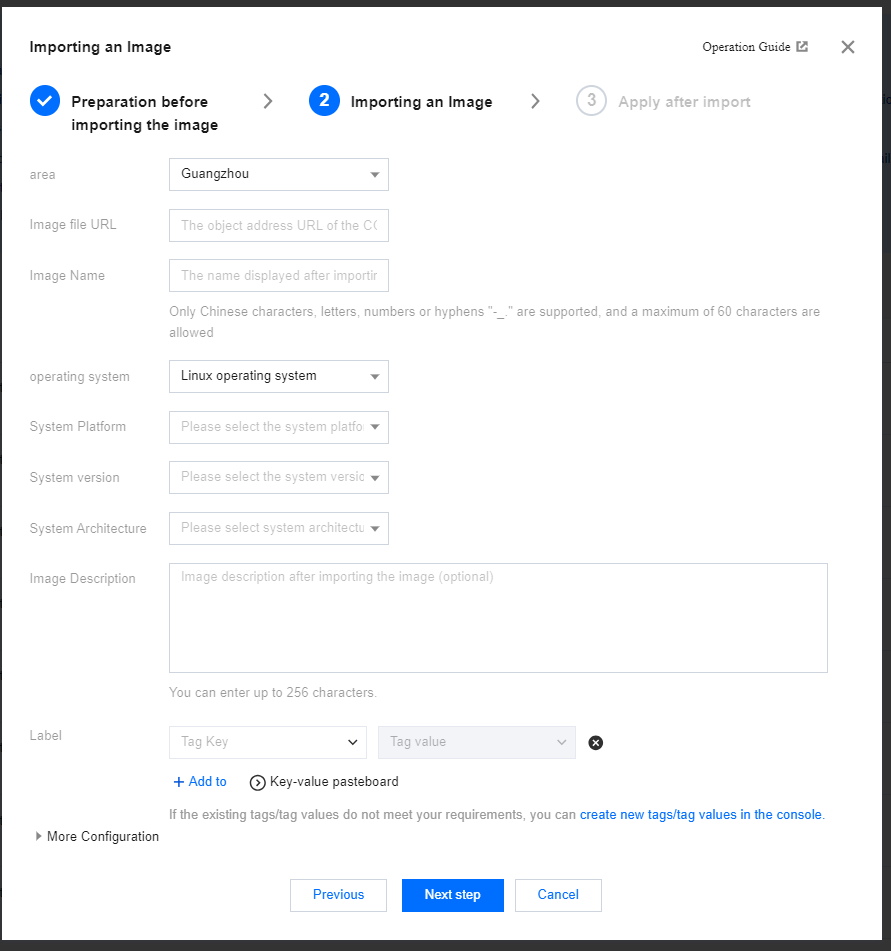
- Enter the Region.
![]()
- Enter the Name and Image file URL.To copy the temporary link to the image file:
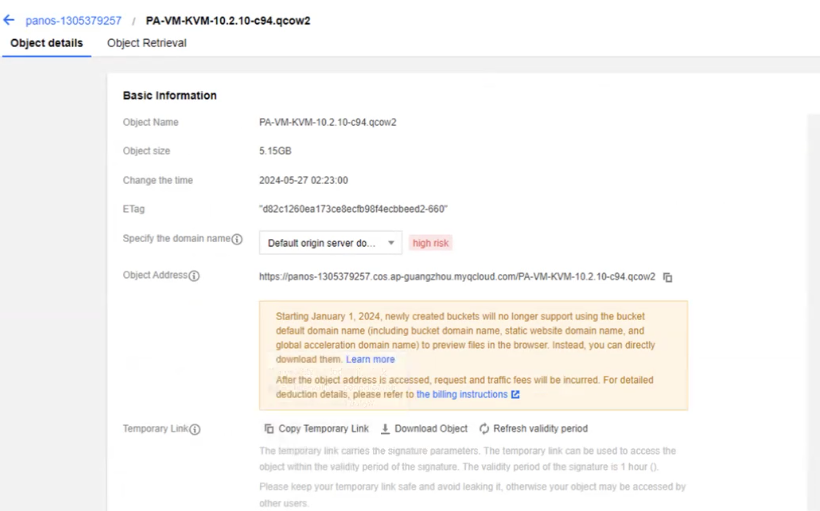
- Go to your image file, click Details.
![]()
- Copy the temporary link shown on the screen.
- Go to your image file, click Details.
- Select Other Linux as the Operating System option.
- Select 64-bit for System Structure.
- Select the Enable Forced Import checkbox.
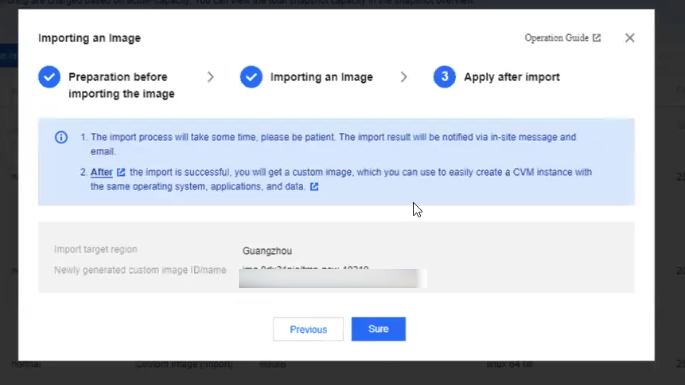
- Click Next Step.
- Click Sure.
![]()
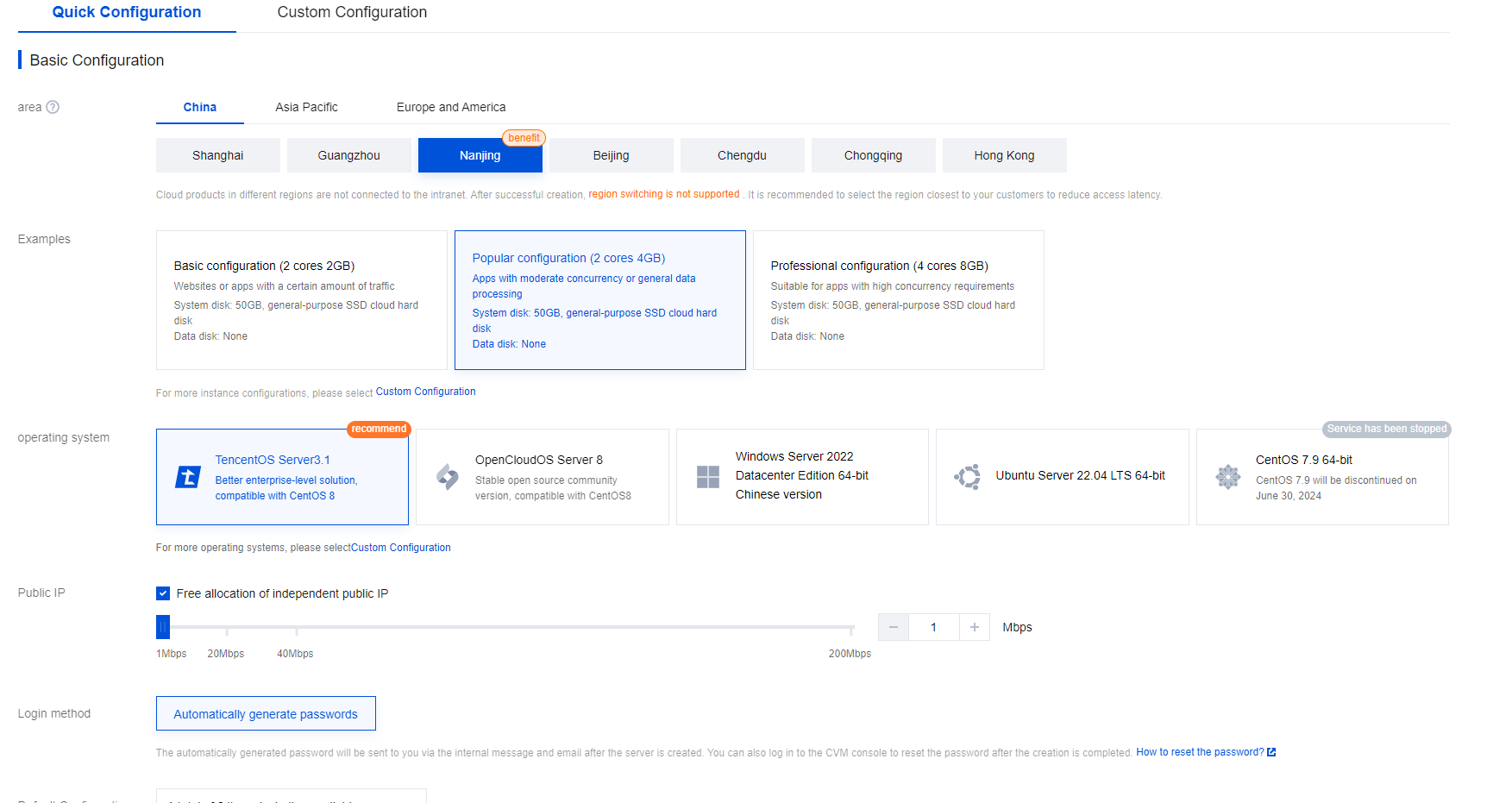
Create a VM-Series firewall instance.- Go to your VM-Series image file and click Create Instance.
- Click Sure.
- In the Basic Configuration section, select your Billing Model and Region.
![]()
- Select your instance, and click Next Step.
- In the Network and Bandwidth section, select your VPC and subnet.
- (Optional) Select the Manually assigning IP address checkbox to manually allocate the IP address out of the subnet.
- Select Assign the Independent IP checkbox to obtain a public interface for your firewall.
- Select your Security Group.
- Enter the Instance Name.
- Click Associate the Key and select your key option.You can either create a new key or import an existing public key.
- Click Save.
- Click Next.
- Select the Terms and conditions checkbox.
- Click Activate.
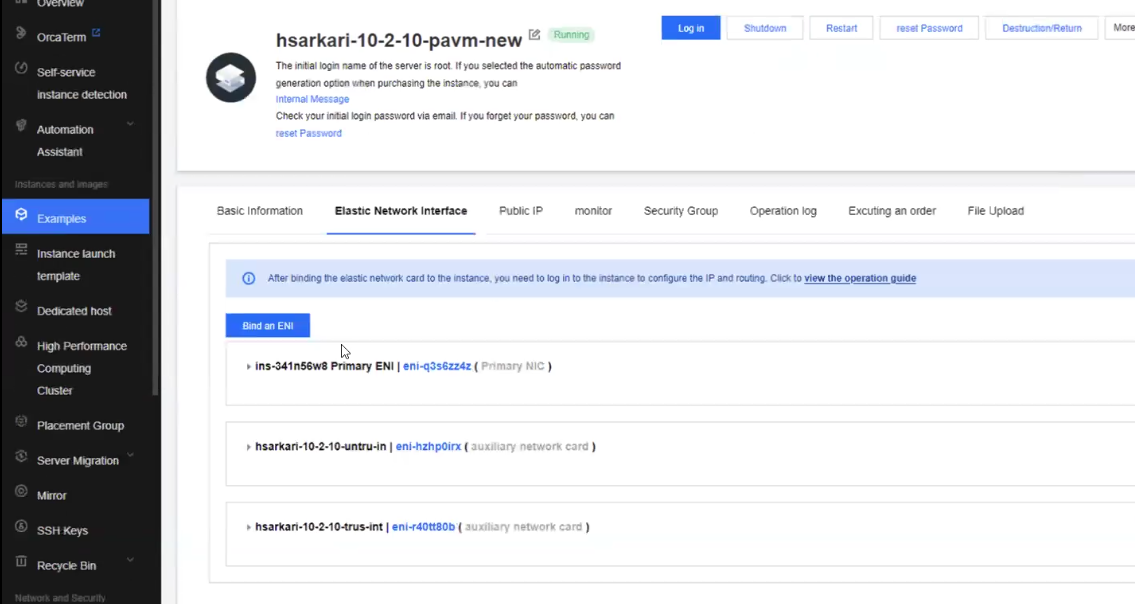
The VM-Series firewall now gets deployed. Go to Cloud Server > Examples to see the list of VM-Series firewall instances deployed.Create Elastic Network Interfaces for your VM-Series Firewall.- In the Tencent console, go to Cloud Server > Examples.
- Select your VM-Instance.
- Click the Elastic Network Interface tab.
- Click Bind an ENI.
![]() Note: By default, a VM-Series instance deployed will have one management interface.
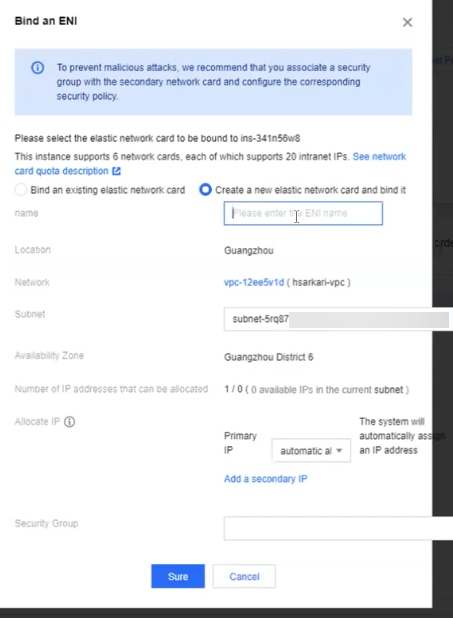
Note: By default, a VM-Series instance deployed will have one management interface. - Click Create a New Elastic Network Card.
![]()
- Enter the name and subnet for your ENI.
- Click Save.
- Ensure that you create an elastic card each for an untrust and trust interface.
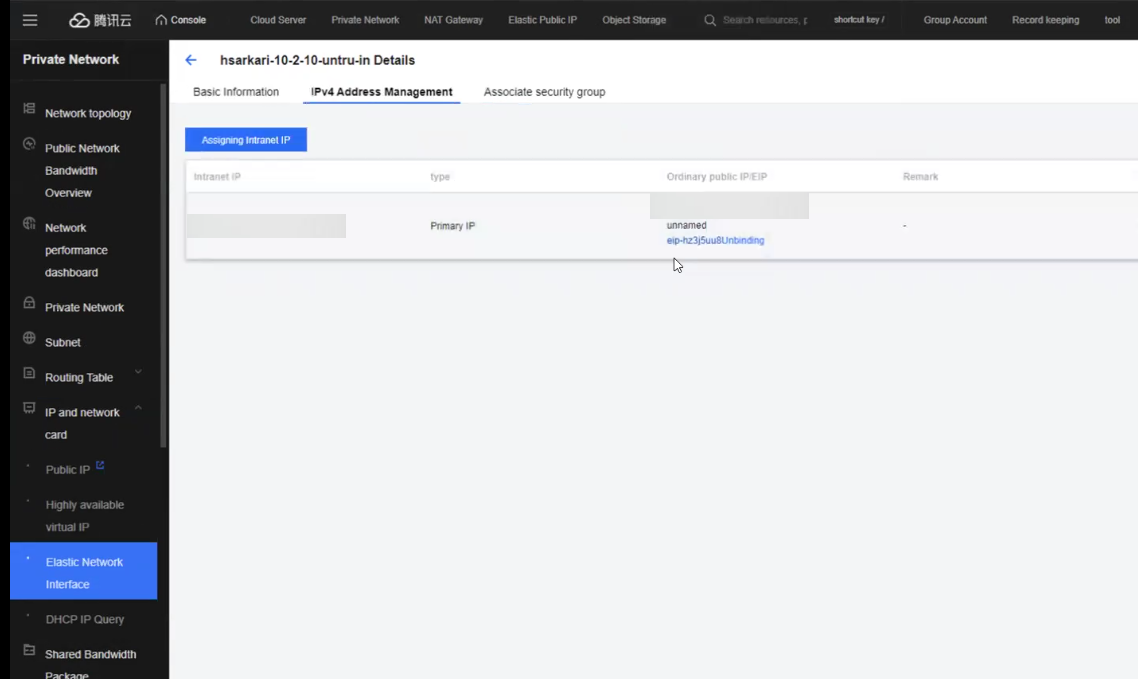
- Ensure that you bind an EIP for your untrust interface. Go to your untrust interface, go to IPV4 address management tab, click Bind an ENIP, and then Create a new one.
- Ensure that you bind an EIP on your untrust interface.
- Go to your untrust interface, and then click IPV4 Address Management tab.
![]()
- Click Binding.
- Click Create a New one and then create a new EIP and bind it to the untrust interface.
Configure the VM-Series firewall.- Log in to your VM-Series firewall web interface.
- Go to Networks > Zones.
- Click Add and create a trust zone.Repeat the above step to create an untrust zone.
- Go to Networks > Interfaces and configure the Layer 3 interfaces for ethernet 1/1 and ethernet 1/2.
- Commit your changes.Verify that the firewall is passing traffic. Select Monitor > Session Browser and verify that you are seeing new sessions.