Post Quantum IKE VPN Support
Table of Contents
Expand all | Collapse all
-
- Browser-Based Real User Monitoring (RUM)
- Configure Phishing Analysis
- Explicit Proxy for Colo-Connect
- Google Drive Labeling
- Identity and Access Management Enhancements
- IKE Gateway with Dynamic IPv6 Address Assignment
- IPv6 Support on Cellular Interface for PA-415-5G Firewall
- Israel and Saudi Arabia Strata Logging Service Region Support
- Strata Logging Service License with One Year Log Retention and Unlimited Storage
- Multitenant Reports
- NPTv6 with Dynamically Assigned IPv6 Address Prefix
- Strata Logging Service in Device Associations
- Remote Network—High Performance Private App Access Support
- RFC6598 Mobile Users Address Pool for New Prisma Access (Managed by Strata Cloud Manager) Deployments
- Secure Integration of Third-Party Enterprise Browsers with Explicit Proxy
- Security Profile Visibility
- Simplified Application Test Configuration
- Static IP Address Enhancements for Mobile Users
- Streamlined Licensing for Strata Cloud Manager
- Support for Proxy ID in IPSec Transport Mode
- Test an Enterprise DLP Data Profile Using Dry Run Mode
- Wildcard FQDN Configuration for Security Policies in ZTNA Connector
- ZTNA Connector for Onboarding Applications
- Configure Split DNS for GlobalProtect App on iOS Endpoints
-
- 25,000 Remote Network and 50,000 IKE Gateway Support
- Private IP Address Visibility and Enforcement for Agent Based Proxy Traffic
- Bandwidth Consumption Modifications
- Best Gateway Selection Criteria
- Endpoint DLP
- Enhanced Report Management in Strata Cloud Manager
- Enhancements for Authentication Using Smart Cards
- Explicit Proxy China Support
- Explicit Proxy Support for Advanced Services
- IP Address Optimization for Explicit Proxy Users- Proxy Deployments
- Improved Security with Enhanced Auto VPN Configuration for Large Enterprises
- Improvements for Multi Authentication CIE Experience
- Intelligent Internal Host Detection
- Multiple Virtual Routers Support on SD-WAN Branch
- Multitenant Application Monitoring Update
- New Check Box for Overriding Security Checks
- New Prisma Access Cloud Management Location
- PA-455-5G Next-Generation Firewall
- Panorama CloudConnector Plugin 2.1.0
- Preventing DoS Attacks from Internet with Enhanced DoS and PBP Configurations
- Prisma Access Browser Visibility
- Remote Browser Isolation in China
- Remote Networks—High Performance
- Route Summarization for Dynamic Privilege Access
- SC-NAT Support for Dynamic Privilege Access
- SD-WAN on 5G Cellular Interface
- Simplified Prisma Access Private App Connectivity
- Simplify Prisma Access SaaS Connectivity with IP Optimization for Mobile Users and Explicit Proxy Deployments
- Static IP Address Enhancements for Mobile Users
- TLS 1.3 and PubSub Support for Traffic Replication
- View and Monitor Colo-Connect
- View Prisma Access, Dataplane, and Application and Threats Content Releases in Strata Cloud Manager and Panorama
- Wildcard Support for Split Tunnel Settings Based on the Application
- ZTNA Connector Support for Commitless App Onboarding
- CLI Support to Connect to the GlobalProtect App with SAML Authentication
-
- AI Runtime Security
- Browser Support for Remote Browser Isolation
- Cross-Scope Referenceability in Snippets
- Disable Default HIP Profiles
- Encrypted DNS for DNS Proxy and the Management Interface
- Mobile Support for Remote Browser Isolation
- Panorama to Strata Cloud Manager Migration
- Scan Support for ChatGPT Enterprise App
- Support for Deleting Connector IP Blocks
- Prisma SD-WAN Support for FedRAMP Moderate Environment
- Email DLP Enhancements
-
- Auto VPN Support for HA Devices
- Cloud NGFW Policy Management Using Strata Cloud Manager
- Connect to GlobalProtect App with IPSec Only
- Changes to Behavior for Web Traffic Handling
- Dynamic Privilege Access
- Embedded Browser Framework Upgrade
- End User Coaching
- Enhanced HIP Remediation Process Improvements
- Enhancements for Authentication Using Smart Cards-Authentication Fallback
- Enhancements for Authentication Using Smart Cards-Removal of Multiple PIN Prompts
- Global Find Using Config Search
- Intelligent Portal
- Local Configuration Management Support for Firewalls
- Manage and Share Common Configuration Using Snippet Sharing
- Native IPv6 Compatibility
- Overlapping IP Address Support
- PA-410R-5G Next-Generation Firewall
- Simplified License Activation and Default Tenant Creation
- Strata Logging Service in Strata Cloud Manager
- Third-Party CDR Integration for Remote Browser Isolation
- View and Monitor App Acceleration
- View and Monitor Native IPv6 Compatibility
- View and Monitor Third-Party Device-IDs
- ZTNA Connector Application Discovery, User-ID Across NAT, and Support for Connector IP Block Deletion
-
- Advanced DNS Security
- Advanced Threat Prevention (ATP) Support on CN-Series Firewall
- Advanced Threat Prevention: Support for Zero-day Exploit Prevention
- App Acceleration Support for Additional Apps
- Authorized Support Center Support View
- Bulk Configuration
- Business Continuity During Mergers and Acquisitions
- Calgary and South Africa Central Compute Locations
- CIE (SAML) Authentication using Embedded Web-view
- Configuration File Compression
- Dynamic DNS Registration Support for Mobile Users—GlobalProtect
- Explicit Proxy Forwarding Profiles with Multiple PAC File Support
- Explicit Proxy SAML Authentication Improvements
- Explicit Proxy Support for South Africa Central Location
- Fast-Session Delete
- FedRAMP Moderate
- FQDNs for Remote Network and Service Connection IPSec Tunnels
- GlobalProtect Portal and Gateway Support for TLSv1.3
- GlobalProtect Proxy Enhancements
- GlobalProtect Support for PAN-OS-11.2-DHCP-Based IP Address Assignments
- GTP Support for Intelligent Security
- Increased Maximum Number of Security Rules for PA-3400 Series Firewalls
- IPSec Serviceability
- Local Deep Learning for Advanced Threat Prevention
- Monitor Bandwidth on SD-WAN Devices
- NGFW Clustering of PA-7500 Series Firewalls
- OOXML Support for WildFire Inline ML
- PA-410R Next-Generation Firewall
- PA-450R-5G Next-Generation Firewall
- PAN-OS 11.0, 11.1, and 11.2 Dataplane Support
- PAN-OS 11.2 Support for Panoramas That Manage Prisma Access
- Post Quantum Hybrid Key Exchange VPN
- Prisma Access Internal Gateway
- Remote Network Tunnel Automation API
- Static IP Address Allocation for Mobile Users
- Strata Cloud Manager Connectivity Using Port 443
- TLSv1.3 Support for HSM Integration with SSL Inbound Inspection
- User-ID for CN-Series
- User-ID Across NAT
- Virtual Systems Support on VM-Series Firewall
- Intelligent Traffic Offload - Layer 3 (Dynamic Routing) Support on VM-Series Firewall
- Intelligent Traffic Offload - NAT Support on VM-Series Firewall
- Zero Touch Provisioning (ZTP) Onboarding Enhancements
- View Preferred and Base Releases of PAN-OS Software
-
- Additional Private Link Types
- Additional SD-WAN Hubs in VPN Cluster
- Aggregate Ethernet Interface Usability Enhancement
- App SLA Assurance Enhancements
- Branch Gateway
- Configuration Indicator
- Device Onboarding Rules
- External Gateway Integration for Prisma Access and On-Premises NGFWs
- Enhanced Incident Management
- Enterprise DLP Migrator
- Prisma SD-WAN OSPF
- SDDC — Megaport (VFF)
- Site Template Enhancements
- Software Cut-through based Offload on CN-Series Firewall
- Software Cut Through Support for PA-400 and PA-1400 Series Firewalls
- Subscription Usage Visibility for Prisma SD-WAN
- Support for Additional System Applications
- Support for Configurable Layer 3 Reachability Probes
- Standard VPN Enhancements for DC to DC
- Strata Cloud Manager: Activity Insights
- Strata Cloud Manager: Command Center
- SVI Operational Enhancements
- Trusted IP List
- View Only Administrator Role Enhancement
- VRF- Support for Standard VPN, NTP, Syslog, and SNMP
- Web Proxy for Cloud-Managed Firewalls
-
- Authenticate LSVPN Satellite with Serial Number and IP Address Method
- Private Key Export in Certificate Management
- Clone a Snippet
- Security Checks
- Disable Tunnel Reoptimization
- DNS Reachability
- GlobalProtect Portal and Gateway
- IP Optimization for Mobile Users - GlobalProtect Deployments
- License Enforcement for Mobile Users (Enhancements)
- Multiple Virtual Routers Support on SD-WAN Hubs
- Native SASE Integration with Prisma SD-WAN
- New Prisma Access Cloud Management Location
- Normalized Username Formats
- PAN-OS Software Patch Deployment
- Policy Analyzer
- Saudi Arabia Compute Location
- Site Template Configuration
- TACACS+ Accounting
- Tenant Moves and Acquisitions
- Traceability and Control of Post-Quantum Cryptography in Decryption
- User Session Inactivity Timeout
-
- FedRAMP High "In Process" Requirements and Activation
- License Activation Changes
- Performance Policy with Forward Error Correction (FEC)
- View and Monitor ZTNA Connector Access Objects
- Software Cut-Through Support for PA-3400 and PA-5400 Series Firewalls
- Persistent NAT for DIPP
- ZTNA Connector Wildcard and FQDN Support for Applications and Additional Diagnostic Tools
-
- 5G Cellular Interface for IPv4
- Advanced WildFire Inline Cloud Analysis
- API Key Certificate
- App Acceleration in Prisma Access
- ARM Support on VM-Series Firewall
- Authentication Exemptions for Explicit Proxy
- BGP MRAI Configuration Support
- Cloud Managed Support for Prisma Access China
- Configuration Audit Enhancements
- Strata Logging Service with CN-Series Firewall
- Device-ID Visibility and Policy Rule Recommendations in PAN-OS
- Dynamic IPv6 Address Assignment on the Management Interface
- Dynamic Routing in CN-Series HSF
- Enhanced IoT Policy Recommendation Workflow for Strata Cloud Manager
- Enhanced SaaS Tenants Control
- Exclude All Explicit Proxy Traffic from Authentication
- GlobalProtect Portal and Gateway Support for TLSv1.3
- IKEv2 Certificate Authentication Support for Stronger Authentication
- Improved Throughput with Lockless QoS
- Incident Dampening
- Increased Device Management Capacity for the Panorama Virtual Appliance
- Inline Security Checks
- Integrate Prisma Access with Microsoft Defender for Cloud Apps
- Intelligent Security with PFCP for N6 and SGI Use Cases
- IoT Security: Device Visibility and Automatic Policy Rule Recommendations
- IoT Security Support for CN-Series
- IP Protocol Scan Protection
- IPSec VPN Monitoring
- IPv6 for BGP Support
- Layer 2 Switching Capabilities in ION 3200
- Link Aggregation Support on VM-Series
- Maximum of 500 Remote Networks Per 1 Gbps IPSec Termination Node
- New Platform Support for Web Proxy
- New Template Variables
- PA-415-5G Next-Generation Firewall
- PA-450R Next-Generation Firewall
- PA-455 Next-Generation Firewall
- PA-5445 Next-Generation Firewall
- PA-7500 Next-Generation Firewall
- Policy Rulebase Management Using Tags
- Post Quantum IKE VPN Support
- PPPoE Client for IPv6
- Public Cloud SD-WAN High Availability (HA)
- Remote Browser Isolation
- Secure Copy Protocol (SCP) Support
- Security Checks
- Service Connection Identity Redistribution Management
- Service Provider Backbone Integration
- Session Resiliency for the VM-Series on Public Clouds
- SNMP-based Discovery for IoT
- SNMP Network Discovery for IoT Security
- Strata Cloud Manager: Application Name Updates
- Support for Strata Logging Service Switzerland Region
- TACACS+ Accounting
- Throughput Enhancements for Web Proxy
- TLSv1.3 Support for Administrative Access Using SSL/TLS Service Profiles
- Traceability and Control of Post-Quantum Cryptography in Decryption
- Traffic Replication Remote Network and Strata Cloud Manager Support
- Used-for-HA Capability on Layer 3 Interfaces
- VM-Series Device Management
- View and Monitor App Acceleration
- View and Monitor Remote Browser Isolation
- Virtual Routing Forwarding for WAN Segmentation
-
- Cloud IP-Tag Collection
- Config Version Snapshot
- Create a Custom Path Quality Profile
- Delete a Snippet
- Web Proxy for Cloud-Managed Firewalls
- High-Bandwidth Private App Access with Colo-Connect
- Integrate Prisma Access with Microsoft Defender for Cloud Apps
- Introducing ADEM APIs
- Log Viewer Usability Enhancements
- New Predefined BGP Redistribution Profile
- New Prisma Access Cloud Management Location
- Refresh Pre Shared Keys for Auto VPN
- Strata Logging Service Regional Support
- Troubleshoot NGFW Connectivity and Policy Enforcement Anomalies
-
- High-Bandwidth Private App Access with Colo-Connect
- Traffic Replication and PCAP Support
- Third-Party Device-ID in Prisma Access
- New and Remapped Prisma Access Locations and Compute Locations
- Transparent SafeSearch Support
- Private IP Visibility and Enforcement for Explicit Proxy Traffic Originating from Remote Networks
- Service Provider Backbone Integration
- Cloud Management of NGFWs
- Feature Adoption Dashboard
- Best Practices Dashboard
- Compliance Summary Dashboard
- Security Posture Insights Dashboard
- Advanced Threat Prevention Dashboard
- Custom Dashboard
- Device Health Dashboard
- Incidents and Alerts
- NGFW SDWAN Dashboard
- Capacity Analyzer
- Enhancements to CDSS Dashboard
-
- Conditional Connect Method for GlobalProtect
- Enhanced Split Tunnel Configuration
- Prisma Access Explicit Proxy Connectivity in GlobalProtect for Always-On Internet Security
- Host Information Profile (HIP) Exceptions for Patch Management
- Host Information Profile (HIP) Process Remediation
- License Activation
Post Quantum IKE VPN Support
RFC 8784 support provides post quantum resistance for quantum attacks on IKE
VPNs.
Post-quantum VPNs resist attacks based on quantum computing and post-quantum
cryptography (PQC). Palo Alto Networks post-quantum VPN support enables you to
configure quantum-resistant IKEv2 VPNs and is based on the RFC 8784 standard to maximize interoperability with
other vendors' equipment and with future standards. Multiple government agencies
around the world, including the NSA and NIAP, recommend implementing RFC 8784 to
improve quantum resistance. Implementing RFC 8784 is the simplest way to create
quantum-resistant VPNs because you don't need to upgrade crypto elements.
Addressing the quantum threat immediately is critical to defend against Harvest Now, Decrypt Later attacks that target
long-lived data because the development of cryptographically relevant quantum
computers (CRQCs) will vastly reduce the amount of time required to break classical
encryption.
Configuring quantum-resistant VPNs can prevent attackers from recording critical
encrypted key material and thus prevent them from decrypting the data even if they
steal it. If you have long-lived data, start planning now for the threat posed by
quantum computers and quantum cryptography and for your network's transition to a
post-quantum world. The first step is to make your VPN connections
quantum-resistant.
RFC 8784 provides a transition from today's classical cryptography to PQC.
Quantum-resistant VPNs based on RFC 8784 enable using post-quantum pre-shared keys
(PPKs) that are not transmitted with the data, so harvesting attacks fail because
they don't capture the key material that they need to decrypt the data later. A PPK
is a complex, strong hexadecimal string that you statically program into the IKE
peers at the ends of the VPN tunnel.
Adding a static PPK that's delivered out-of-band to the classical Diffie-Hellman (DH)
key prevents Shor's algorithm from cracking the key
because the key is no longer based on prime numbers. RFC 8784 enables using long,
strong PPKs that meet the NIST Category 5 security level.
In addition, RFC 8784 provides the backward compatibility to fall back to classical
cryptography if a peer can't support FRC 8784, so the implementation doesn't risk
refusing legitimate connections. Palo Alto Networks implementation of RFC 8784
provides flexibility and quantum resistance for your IKEv2 VPNs:
- You can add up to ten post-quantum (PQ) PPKs to each IKEv2 VPN. Each PQ PPK is associated with a PPK KeyID, which uniquely identifies the PPK, so you can configure up to ten PPK + KeyID pairs. You can configure PPKs yourself or use a built-in tool to generate strong PPK strings. Configuring multiple active PPKs enables the firewall that initiates the IKEv2 peering to randomly select one of the active PPKs to use with the peer.
- You can configure PPK strings from 16-64 bytes (32-128 characters) in length. For best security, use PPK strings that are at least 32 bytes (64 characters) in length.
- You can set the Negotiation Mode to control the ciphers used to establish the connection:
- Mandatory—Require that the responding peer use RFC 8784 and abort the connection if it only uses classical cryptography.
- Preferred—Allow the initiating device to fall back to classical cryptography if the peer doesn't support RFC 8784.
- You can activate and deactivate individual PQ PPKs, so if a PQ PPK is lost or exposed, you can disable it and remove it from the negotiation pool.
In addition to implementing RFC 8784 now:
- Migrate to tougher cipher suites. Follow RFC 6379 for Suite B Cryptographic Suites for IPsec, upgrade ciphers to Suite-B GCM-256, and avoid using weaker AES-128-bit algorithms.
- Upgrade to larger hash sizes such as SHA-384 or SHA-512. Don't use MD5 or SHA-1.
- Upgrade your CA to larger RSA key sizes. Use 4096-bit RSA key sizes and migrate VPN certificate authentication to new certificates.
The following example topology shows three VPN termination sites. Sites A and C
support post-quantum VPNs based on RFC 8784. Site B supports only classical VPNs.
Site A must be able to communicate with both Site B and Site C.
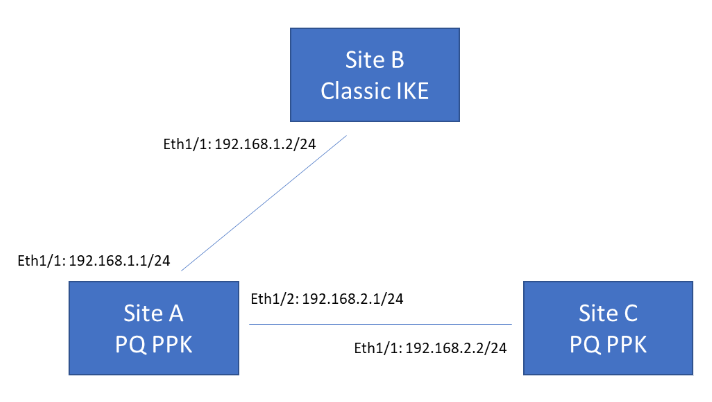
Site A uses both Mandatory and Preferred negotiation modes. When Site A communicates
with Site B, which only supports classical cryptography, Site A falls back to
classical negotiation. When Site A communicates with Site C, Site A uses a PQ PPK
because Site C supports using PQ PPKs.
