OOXML Support for WildFire Inline ML
Table of Contents
Expand all | Collapse all
-
- Advanced WildFire Support for EML Files
- Advanced WildFire Dashboard Enhancements
- Mach-O Support for WildFire Inline ML
- Advanced WildFire Public Sector Cloud
- Advanced WildFire Government Cloud
- WildFire Italy Cloud
- WildFire Spain Cloud
- WildFire Saudi Arabia Cloud
- WildFire Israel Cloud
- WildFire South Africa Cloud
- WildFire South Korea Cloud
- WildFire Qatar Cloud
- WildFire France Cloud
- WildFire Taiwan Cloud
- WildFire Indonesia Cloud
- WildFire Poland Cloud
- WildFire Switzerland Cloud
- Advanced WildFire Support for Intelligent Run-time Memory Analysis
- Shell Script Analysis Support for Wildfire Inline ML
- Standalone WildFire API Subscription
- WildFire India Cloud
- MSI, IQY, and SLK File Analysis
- MS Office Analysis Support for Wildfire Inline ML
- WildFire Germany Cloud
- WildFire Australia Cloud
- Executable and Linked Format (ELF) Analysis Support for WildFire Inline ML
- Global URL Analysis
- WildFire Canada Cloud
- WildFire UK Cloud
- HTML Application and Link File Analysis
- Recursive Analysis
- Perl Script Analysis
- WildFire U.S. Government Cloud
- Real Time WildFire Verdicts and Signatures for PDF and APK Files
- Batch File Analysis
- Real Time WildFire Verdicts and Signatures for PE and ELF Files
- Real Time WildFire Verdicts and Signatures for Documents
- Script Sample Analysis
- ELF Malware Test File
- Email Link Analysis Enhancements
- Sample Removal Request
- Updated WildFire Cloud Data Retention Period
- DEX File Analysis
- Network Traffic Profiling
- Additional Malware Test Files
- Dynamic Unpacking
- Windows 10 Analysis Environment
- Archive (RAR/7z) and ELF File Analysis
- WildFire Analysis of Blocked Files
- WildFire Phishing Verdict
OOXML Support for WildFire Inline ML
To access the new OOXML (Open Office XML) file analysis classification engine for
WildFire Inline ML, be sure to
download and install the latest PAN-OS content release. PAN-OS Applications and
Threats content release 8825 and later allows firewalls operating PAN-OS 11.1.3
and later to detect and prevent malicious OOXML files from entering your network
in real-time using Inline ML. For more information about the update, refer to
the Applications and Threat Content Release Notes.
To download the release notes, log in to the Palo Alto Networks Support Portal,
click Dynamic Updates and select the release notes listed under Apps +
Threats.
WildFire now supports a new office file type analysis classification engine for WildFire Inline ML: OOXML (Open Office
XML). This enables you to configure your firewall to detect and prevent malicious
Office Open XML files from entering your network in real-time by applying machine
learning (ML) analytics. WildFire Inline ML dynamically detects
malicious files of specific types by evaluating various file details to formulate a
high probability classification of a file. This protection extends to currently
unknown as well as future variants of threats that match characteristics that Palo
Alto Networks identified as malicious. To take advantage of WildFire inline ML, you
must have an active WildFire subscription. If you do not have WildFire Inline ML
enabled on your firewall, refer to WildFire Inline ML for more
information.
- Update your existing Antivirus Security profile to enable the OOXML real-time WildFire analysis classification engine.
- Select an existing Antivirus Profile or Add a new one (Objects > Security Profiles > Antivirus).
- Configure your Antivirus profile.
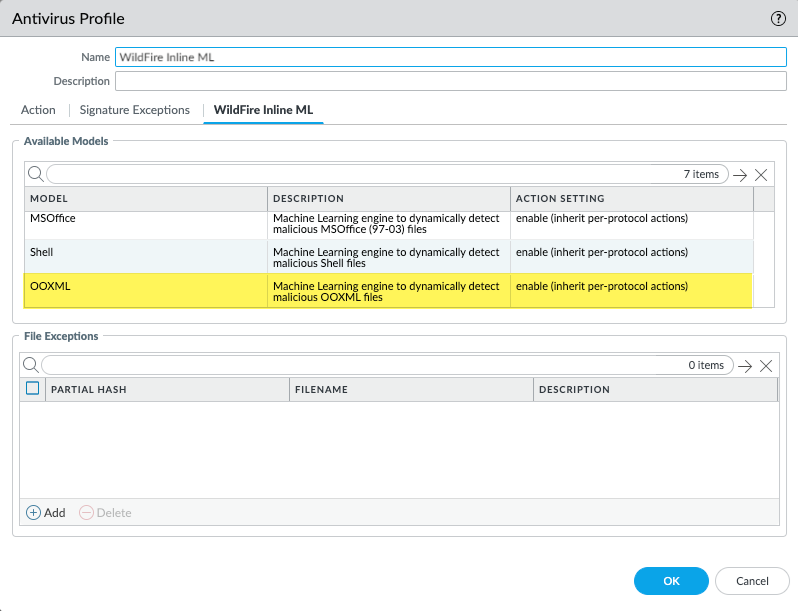
- Select WildFire Inline ML and apply an Action Setting for the new WildFire inline ML model. This enforces WildFire inline ML Actions settings for each protocol on a per-model basis. In addition to the currently available classification engines, OOXML should now be available. If this model is unavailable, verify that you have content release 8825 or later installed on the firewall.
![]()
- enable (inherit per-protocol actions)—WildFire inspects traffic according to your selections in the WildFire Inline ML Action column in the decoders section of the Action tab.
- alert-only (override more strict actions to alert)—WildFire inspects traffic according to your selections in the WildFire Inline ML Action column in the decoders section of the Action tab and overrides any action with a severity level higher than alert (drop, reset-client, reset-server, reset-both) alert, which allows traffic to pass while still generating and saving an alert in the threat logs.
- disable (for all protocols)—WildFire allows traffic to pass without any policy action.
- Click OK to exit the Antivirus Profile configuration dialog and Commit your new settings.
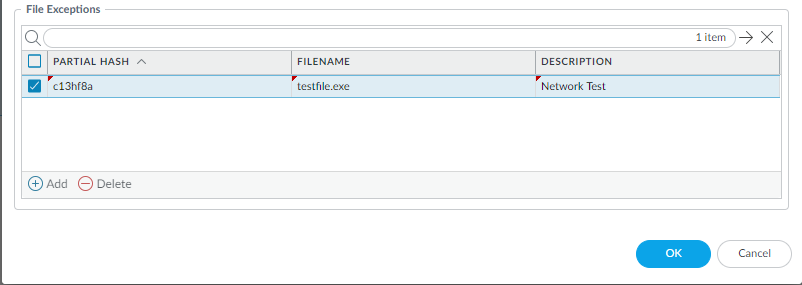
(Optional) Add file exceptions to your Antivirus Security profile if you encounter false-positives. This is typically done for users who are not forwarding files to WildFire for analysis. You can add the file exception details directly to the exception list or by specifying a file from the threat logs.If your firewall WildFire Analysis security profile is configured to forward MS Office files (which also includes OOXML for standard WildFire analysis), false-positives are automatically corrected as they are received. If you continue to see ml-virus alerts for files that have been classified as benign by WildFire Analysis, please contact Palo Alto Networks Support.- Add file exceptions directly to the exceptions list.
- Select Objects > Security Profiles > Antivirus.
- Select an Antivirus profile for which you want to exclude specific files and then select WildFire Inline ML.
- Add the hash, filename, and description of the file that you want to exclude from enforcement.
![]()
- Click OK to save the Antivirus profile and then Commit your changes.
- Add file exceptions from threat logs entries.
- Select Monitor > Logs > Threat and filter the logs for the ml-virus threat type. Select a threat log for a file for which you wish to create a file exception.
- Go to the Detailed Log View and scroll to Details and then Create Exception.
- Add a Description and click OK to add the file exception.
- You can find the new file exception in the File Exceptions list (ObjectsSecurity ProfilesAntivirusWildFire Inline ML.
(Optional) See Configure WildFire Inline ML for information about testing your firewall’s connection to the inline ML cloud service and viewing related logs.