Create a Custom L3 & L4 Vulnerability Signature
Table of Contents
Expand all | Collapse all
-
- About Custom Application Signatures
- Create a Custom Application Signature
- Create a Custom L3 & L4 Vulnerability Signature
- Import a Custom Threat Signature from Snort and Suricata Rules
- Test a Custom Signature
- Custom Signature Pattern Requirements
- Testing Pattern Performance Impact
-
-
- dhcp-req-chaddr
- dhcp-req-ciaddr
- dhcp-rsp-chaddr
- dhcp-rsp-ciaddr
- dns-req-addition-section
- dns-req-answer-section
- dns-req-authority-section
- dns-req-header
- dns-req-protocol-payload
- dns-req-section
- dns-rsp-addition-section
- dns-rsp-answer-section
- dns-rsp-authority-section
- dns-rsp-header
- dns-rsp-protocol-payload
- dns-rsp-ptr-answer-data
- dns-rsp-queries-section
- email-headers
- file-data
- file-elf-body
- file-flv-body
- file-html-body
- file-java-body
- file-mov-body
- file-office-content
- file-pdf-body
- file-riff-body
- file-swf-body
- file-tiff-body
- file-unknown-body
- ftp-req-params
- ftp-req-protocol-payload
- ftp-rsp-protocol-payload
- ftp-rsp-banner
- ftp-rsp-message
- gdbremote-req-context
- gdbremote-rsp-context
- giop-req-message-body
- giop-rsp-message-body
- h225-payload
- http-req-cookie
- http-req-headers
- http-req-host-header
- http-req-host-ipv4-address-found
- http-req-host-ipv6-address-found
- http-req-message-body
- http-req-mime-form-data
- http-req-ms-subdomain
- http-req-origin-headers
- http-req-params
- http-req-uri
- http-req-uri-path
- http-req-user-agent-header
- http-rsp-headers
- http-rsp-non-2xx-response-body
- http-rsp-reason
- icmp-req-code
- icmp-req-data
- icmp-req-type
- icmp-req-protocol-payload
- icmp-rsp-data
- icmp-rsp-protocol-payload
- icmp-req-possible-custom-payload
- ike-req-headers
- ike-rsp-headers
- ike-req-payload-text
- ike-rsp-payload-text
- imap-req-cmd-line
- imap-req-first-param
- imap-req-params-after-first-param
- imap-req-protocol-payload
- imap-rsp-protocol-payload
- irc-req-params
- irc-req-prefix
- jpeg-file-scan-data
- jpeg-file-segment-data
- jpeg-file-segment-header
- ldap-req-searchrequest-baseobject
- ldap-rsp-searchresentry-objectname
- ms-ds-smb-req-share-name
- ms-ds-smb-req-v1-create-filename
- ms-ds-smb-req-v2-create-filename
- msrpc-req-bind-data
- mssql-db-req-body
- netbios-dg-req-protocol-payload
- netbios-dg-rsp-protocol-payload
- netbios-ns-req-protocol-payload
- netbios-ns-rsp-protocol-payload
- nettcp-req-context
- oracle-req-data-text
- pe-dos-headers
- pe-file-header
- pe-optional-header
- pe-section-header
- pe-body-data
- pop3-req-protocol-payload
- pop3-rsp-protocol-payload
- pre-app-req-data
- pre-app-rsp-data
- rtmp-req-message-body
- rtsp-req-headers
- rtsp-req-uri-path
- sip-req-headers
- snmp-req-community-text
- smtp-req-argument
- smtp-rsp-content
- smtp-req-protocol-payload
- smtp-rsp-protocol-payload
- ssh-req-banner
- ssh-rsp-banner
- ssl-req-certificate
- ssl-req-chello-sni
- ssl-req-client-hello
- ssl-req-protocol-payload
- ssl-req-random-bytes
- ssl-rsp-cert-subjectpublickey
- ssl-rsp-certificate
- ssl-rsp-protocol-payload
- ssl-rsp-server-hello
- tcp-context-free
- telnet-req-client-data
- telnet-rsp-server-data
- udp-context-free
- unknown-req-tcp-payload
- unknown-rsp-tcp-payload
- unknown-req-udp-payload
- unknown-rsp-udp-payload
-
- dnp3-req-func-code
- dnp3-req-object-type
- dns-rsp-tcp-over-dns
- dns-rsp-txt-found
- ftp-req-params-len
- http-req-connect-method
- http-req-content-length
- http-req-cookie-length
- http-req-dst-port
- http-req-header-length
- http-req-param-length
- http-req-no-host-header
- http-req-no-version-string-small-pkt
- http-req-simple-request
- http-req-uri-path-length
- http-req-uri-tilde-count-num
- http-rsp-code
- http-rsp-content-length
- http-rsp-total-headers-len
- iccp-req-func-code
- ike-req-payload-type
- ike-rsp-payload-type
- ike-req-payload-length
- ike-rsp-payload-length
- ike-version
- imap-req-cmd-param-len
- imap-req-first-param-len
- imap-req-param-len-from-second
- irc-req-protocol-payload
- irc-rsp-protocol-payload
- ntlm-req-auth-v1
- ntlm-req-auth-v2
- open-vpn-req-protocol-payload
- pfcp-req-msg-type
- pfcp-rsp-msg-type
- smtp-req-helo-argument-length
- smtp-req-mail-argument-length
- smtp-req-rcpt-argument-length
- sctp-req-ppid
- ssl-req-client-hello-ext-type
- ssl-req-client-hello-missing-sni
- ssl-rsp-version
- stun-req-attr-type
- panav-rsp-zip-compression-ratio
- Context Qualifiers
-
Create a Custom L3 & L4 Vulnerability Signature
You can create custom threat signatures (vulnerability)
based on Layer3 and Layer4 header fields (such as IP flags, acknowledgment
numbers, etc). This enables you to provide user-created vulnerability
signature coverage for old and deprecated TCP/IP stacks used in
embedded / IoT devices that normally would not have any existing
threat signature coverage.
Custom L3 & L4 vulnerability
signatures are expressed through your Zone and Zone Protection profile
configuration. You must specify how the firewall responds when it
detects a threat.
- Log in to the PAN-OS web interface.Select DeviceSetupSession and enable L3 & L4 Header Inspection globally on the firewall.
![]() Create a Zone Protection profile and configure your L3 & L4 header inspection settings.
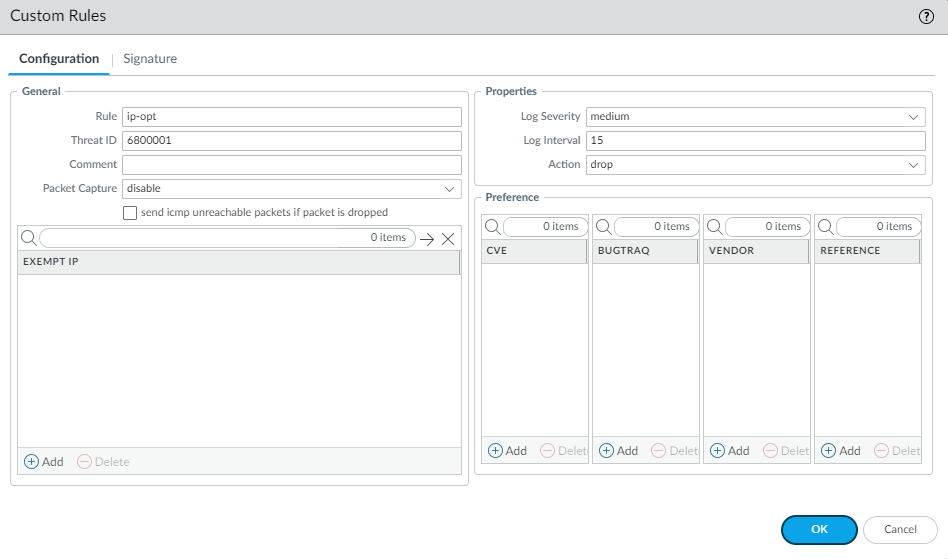
Create a Zone Protection profile and configure your L3 & L4 header inspection settings.- Select NetworkNetwork ProfilesZone Protection and either select an existing profile or Add a new profile.If you are creating a new zone protection profile, enter a Name for the profile and an optional Description.Select L3 & L4 Header Inspection to define your custom vulnerability signatures.Add new custom rules by defining the configuration and signature details for each entry, which are performed in their respective tabs: Configuration and Signature.Under Configuration, fill out the following required fields in the General, Properties, and Reference section.
![]()
- Rule—Specify the custom rule name.
- Threat ID—Enter a numeric ID between 41000 and 45000 or 6800001 and 6900000.
- Comment—Optionally, add a description of the custom rule.
- Packet Capture—Select a packet capture setting.Optionally, select send icmp unreachable packets if packet is dropped to send an ICMP unreachable response to the client upon packet loss.
- Exempt IP—Enter the IP address(es) for which you do not want the custom rule to apply to.
- Log Severity—Select the severity of the threat.
- Log Interval—Indicates how frequently an event is logged.
- Action—Choose the action to take when there is a custom signatures match. Options include alert, drop, reset-client, reset-server, and reset-both. Refer to Security Policy Actions for more information about these action settings.
- Reference—Add references to provide context or related information about the custom threat signature. You can add CVEs, Bugtraq citations, 3rd party vendor IDs, or reference links to additional analysis or background information.
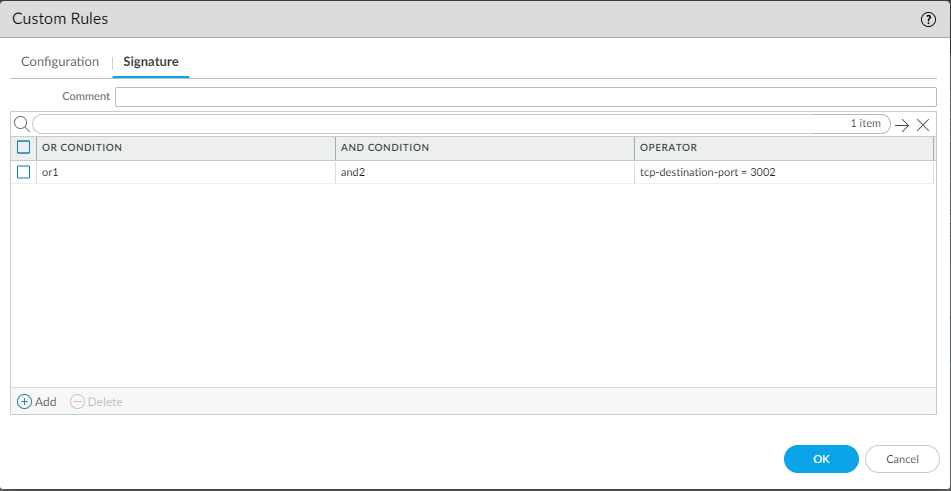
From the Signature tab, provide a name or description of the custom vulnerability under Comment. After specifying a name, select Add to provide the custom signature details.![]()
- Specify a matching Or Condition. When finished, select Add to configure an And Condition and the associated values in a new window.
![]()
- If you select a Less Than or Greater Than operator, specify a Context and a Value. The Equal To operator additionally has Mask and Negate options. Click OK when you have finished configuring the new and condition.
![]()
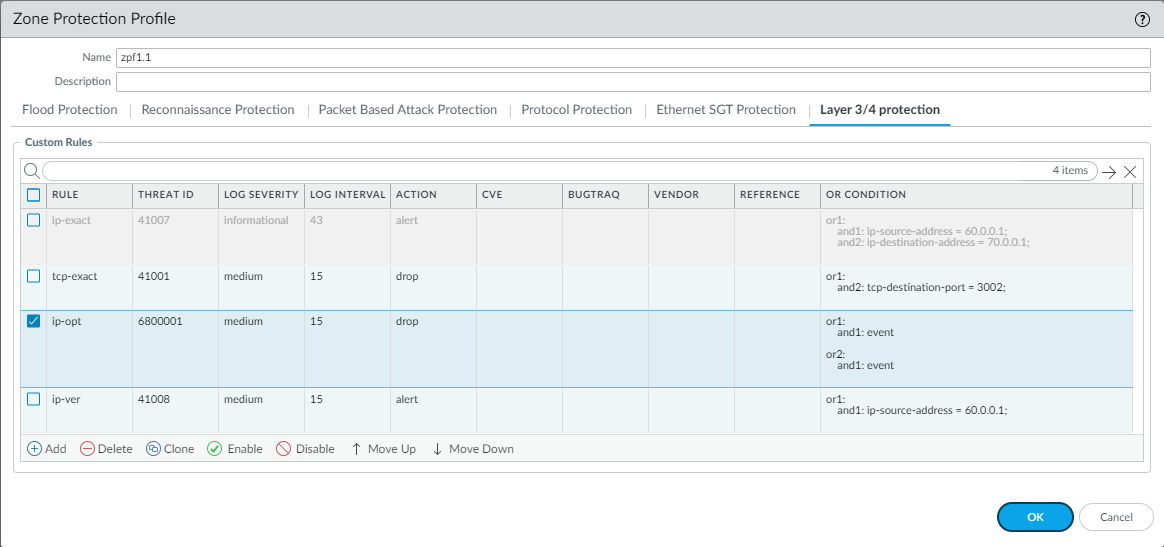
Repeat for each matching condition that you want to add.Click OK and review your signatures. Click OK again to return to the zone protection profile.From the L3 & L4 Header Inspection tab, you can reorder, disable, and clone the custom rule entries as necessary. Click OK to exit the zone protection profile.![]() Apply the Zone Protection profile to a security zone that is assigned to interfaces you want to protect.
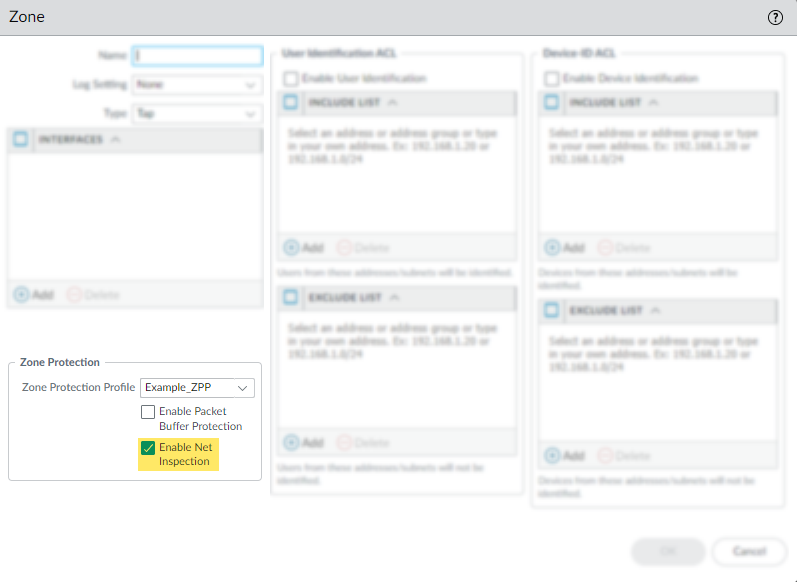
Apply the Zone Protection profile to a security zone that is assigned to interfaces you want to protect.- Select NetworkZones and select the zone where you want to assign the Zone Protection profile.Add the Interfaces belonging to the zone.For Zone Protection Profile, select the profile you just created.Select Enable Net Inspection to enable the L3 & L4 header inspection configuration settings.
![]() Click OK.Commit your changes.
Click OK.Commit your changes.