Deploy the VM-Series Firewall on Azure Stack
Table of Contents
Expand all | Collapse all
-
- VM-Series Deployments
- VM-Series in High Availability
- Enable Jumbo Frames on the VM-Series Firewall
- Hypervisor Assigned MAC Addresses
- Custom PAN-OS Metrics Published for Monitoring
- Interface Used for Accessing External Services on the VM-Series Firewall
- PacketMMAP and DPDK Driver Support
- Enable NUMA Performance Optimization on the VM-Series
- Enable ZRAM on the VM-Series Firewall
-
- VM-Series Firewall Licensing
- Create a Support Account
- Serial Number and CPU ID Format for the VM-Series Firewall
- Use Panorama-Based Software Firewall License Management
-
- Maximum Limits Based on Tier and Memory
- Activate Credits
- Create a Deployment Profile
- Activate the Deployment Profile
- Manage a Deployment Profile
- Register the VM-Series Firewall (Software NGFW Credits)
- Provision Panorama
- Migrate Panorama to a Software NGFW License
- Transfer Credits
- Renew Your Software NGFW Credits
- Amend and Extend a Credit Pool
- Deactivate License (Software NGFW Credits)
- Delicense Ungracefully Terminated Firewalls
- Set the Number of Licensed vCPUs
- Customize Dataplane Cores
- Migrate a Firewall to a Flexible VM-Series License
-
- Generate Your OAuth Client Credentials
- Manage Deployment Profiles Using the Licensing API
- Create a Deployment Profile Using the Licensing API
- Update a Deployment Profile Using the Licensing API
- Get Serial Numbers Associated with an Authcode Using the API
- Deactivate a VM-Series Firewall Using the API
- What Happens When Licenses Expire?
-
- Supported Deployments on VMware vSphere Hypervisor (ESXi)
-
- Plan the Interfaces for the VM-Series for ESXi
- Provision the VM-Series Firewall on an ESXi Server
- Perform Initial Configuration on the VM-Series on ESXi
- Add Additional Disk Space to the VM-Series Firewall
- Use VMware Tools on the VM-Series Firewall on ESXi and vCloud Air
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Use the VM-Series CLI to Swap the Management Interface on ESXi
-
-
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (North-South)
- Components of the VM-Series Firewall on NSX-T (North-South)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Deploy the VM-Series Firewall
- Direct Traffic to the VM-Series Firewall
- Apply Security Policy to the VM-Series Firewall on NSX-T
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Extend Security Policy from NSX-V to NSX-T
-
- Components of the VM-Series Firewall on NSX-T (East-West)
- VM-Series Firewall on NSX-T (East-West) Integration
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (East-West)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Add a Service Chain
- Direct Traffic to the VM-Series Firewall
- Apply Security Policies to the VM-Series Firewall on NSX-T (East-West)
- Use vMotion to Move the VM-Series Firewall Between Hosts
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Create Dynamic Address Groups
- Create Dynamic Address Group Membership Criteria
- Generate Steering Policy
- Generate Steering Rules
- Delete a Service Definition from Panorama
- Migrate from VM-Series on NSX-T Operation to Security Centric Deployment
- Extend Security Policy from NSX-V to NSX-T
- Use In-Place Migration to Move Your VM-Series from NSX-V to NSX-T
-
-
- Deployments Supported on AWS
-
- Planning Worksheet for the VM-Series in the AWS VPC
- Launch the VM-Series Firewall on AWS
- Launch the VM-Series Firewall on AWS Outpost
- Create a Custom Amazon Machine Image (AMI)
- Encrypt EBS Volume for the VM-Series Firewall on AWS
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable CloudWatch Monitoring on the VM-Series Firewall
- VM-Series Firewall Startup and Health Logs on AWS
- Simplified Onboarding of VM-Series Firewall on AWS
-
- AWS Shared VPC Monitoring
- Use Case: Secure the EC2 Instances in the AWS Cloud
- Use Case: Use Dynamic Address Groups to Secure New EC2 Instances within the VPC
-
-
- What Components Does the VM-Series Auto Scaling Template for AWS (v2.0) Leverage?
- How Does the VM-Series Auto Scaling Template for AWS (v2.0 and v2.1) Enable Dynamic Scaling?
- Plan the VM-Series Auto Scaling Template for AWS (v2.0 and v2.1)
- Customize the Firewall Template Before Launch (v2.0 and v2.1)
- Launch the VM-Series Auto Scaling Template for AWS (v2.0)
- SQS Messaging Between the Application Template and Firewall Template
- Stack Update with VM-Series Auto Scaling Template for AWS (v2.0)
- Modify Administrative Account and Update Stack (v2.0)
-
- Launch the Firewall Template (v2.1)
- Launch the Application Template (v2.1)
- Create a Custom Amazon Machine Image (v2.1)
- VM-Series Auto Scaling Template Cleanup (v2.1)
- SQS Messaging Between the Application Template and Firewall Template (v2.1)
- Stack Update with VM-Series Auto Scaling Template for AWS (v2.1)
- Modify Administrative Account (v2.1)
- Change Scaling Parameters and CloudWatch Metrics (v2.1)
-
-
- Intelligent Traffic Offload
-
- Deployments Supported on Azure
- Deploy the VM-Series Firewall from the Azure Marketplace (Solution Template)
- Simplified Onboarding of VM-Series Firewall on Azure
- Deploy the VM-Series Firewall from the Azure China Marketplace (Solution Template)
- Deploy the VM-Series with the Azure Gateway Load Balancer
- Create a Custom VM-Series Image for Azure
- Deploy the VM-Series Firewall on Azure Stack
- Deploy the VM-Series Firewall on Azure Stack HCI
- Deploy VM-Series on Azure Stack Edge
- Enable Azure Application Insights on the VM-Series Firewall
- Set up Active/Passive HA on Azure
- Use the ARM Template to Deploy the VM-Series Firewall
-
- About the VM-Series Firewall on Google Cloud Platform
- Supported Deployments on Google Cloud Platform
- Prepare to Set Up VM-Series Firewalls on Google Public Cloud
- Create a Custom VM-Series Firewall Image for Google Cloud Platform
-
- Deploy the VM-Series Firewall from Google Cloud Platform Marketplace
- Management Interface Swap for Google Cloud Platform Load Balancing
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable Google Stackdriver Monitoring on the VM Series Firewall
- Enable VM Monitoring to Track VM Changes on Google Cloud Platform (GCP)
- Use Dynamic Address Groups to Secure Instances Within the VPC
- Use Custom Templates or the gcloud CLI to Deploy the VM-Series Firewall
-
- Prepare Your ACI Environment for Integration
-
-
- Create a Virtual Router and Security Zone
- Configure the Network Interfaces
- Configure a Static Default Route
- Create Address Objects for the EPGs
- Create Security Policy Rules
- Create a VLAN Pool and Domain
- Configure an Interface Policy for LLDP and LACP for East-West Traffic
- Establish the Connection Between the Firewall and ACI Fabric
- Create a VRF and Bridge Domain
- Create an L4-L7 Device
- Create a Policy-Based Redirect
- Create and Apply a Service Graph Template
-
- Create a VLAN Pool and External Routed Domain
- Configure an Interface Policy for LLDP and LACP for North-South Traffic
- Create an External Routed Network
- Configure Subnets to Advertise to the External Firewall
- Create an Outbound Contract
- Create an Inbound Web Contract
- Apply Outbound and Inbound Contracts to the EPGs
- Create a Virtual Router and Security Zone for North-South Traffic
- Configure the Network Interfaces
- Configure Route Redistribution and OSPF
- Configure NAT for External Connections
-
-
- Choose a Bootstrap Method
- VM-Series Firewall Bootstrap Workflow
- Bootstrap Package
- Bootstrap Configuration Files
- Generate the VM Auth Key on Panorama
- Create the bootstrap.xml File
- Prepare the Licenses for Bootstrapping
- Prepare the Bootstrap Package
- Bootstrap the VM-Series Firewall on AWS
- Bootstrap the VM-Series Firewall on Azure
- Bootstrap the VM-Series Firewall on Azure Stack HCI
- Bootstrap the VM-Series Firewall on Google Cloud Platform
- Verify Bootstrap Completion
- Bootstrap Errors
Deploy the VM-Series Firewall on Azure Stack
Azure Stack is Microsoft’s Azure cloud within your own
datacenter. Deploy the firewall to secure your workloads in your Azure
Stack (on-premise) implementation and shift into the public Azure
cloud as needed.
You can deploy the VM-Series firewall on Azure
Stack to secure inter-subnet traffic between applications in a multi-tier
architecture and outbound traffic from servers within your Azure
Stack deployment. If you want to use the VM-Series firewall as a
gateway that secures inbound traffic destined to the servers within
your Azure Stack deployment, you must deploy a NAT appliance in
front of the firewall that receives inbound traffic and forwards
it to the firewall. The NAT appliance is required because on Azure
Stack you cannot assign a public IP address to a non-primary interface
of a virtual machine, such as the VM-Series firewall.
The
VM-Series firewall on Azure stack does not have support for bootstrapping,
Azure Application Insights, or the Azure Security Center integration.
Unlike
on public Azure, you do not have a solution template to deploy the
VM-Series firewall on Azure Stack. Therefore, you must use an ARM
template to deploy the VM-Series firewall. To get started, you can
use the community supported sample ARM template on GitHub, and then
develop your own ARM template for production deployments.
All VM-Series firewall interfaces must be assigned an
IPv4 address when deployed in a public cloud environment.
- Download marketplace items from Azure to AzureStack.To deploy the VM-Series firewall on Azure Stack, you need access to the BYOL offer of the VM-Series firewall PAN-OS image (8.1 or later). You can download the image directly from the Azure Marketplace to Azure Stack in a connected deployment.Access the Azure Stack portal.Your Azure Stack operator (either a service provider or an administrator in your organization), should provide the correct URL to access the portal.Deploy the VM-Series firewall.A solution template for the VM-Series firewall is not available on Azure Stack. Therefore, you must reference the image that you downloaded in the previous step, in an ARM template to deploy the VM-Series firewall. To get started, you can deploy the sample ARM template that is available on GitHub under the community supported policy:
- Get the sample Azure Stack GitHub template.
- Select azurestackdeploy.json to view the contents.
- Click Raw and copy the contents of the JSON file.
Deploy the sample GitHub template.You can deploy the firewall in a existing resource group that is empty or into a new resource group. The default VNet in the template is 192.168.0.0/16, and it deploys a VM-Series firewall has three network interfaces, one management interface on 192.168.0.0/24 subnet and two dataplane interfaces on 192.168.1.0/24 and 192.168.2.0/24 subnets. You can customize these subnets to match your needs.- Log in to the Azure Stack portal.
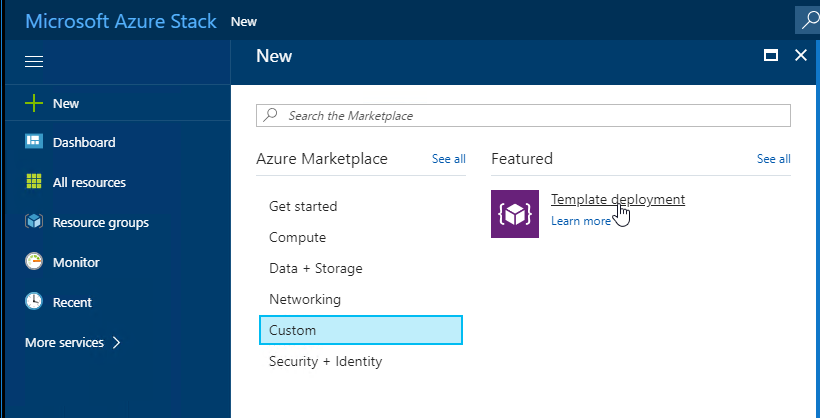
- Select NewCustomTemplate deployment.
![]()
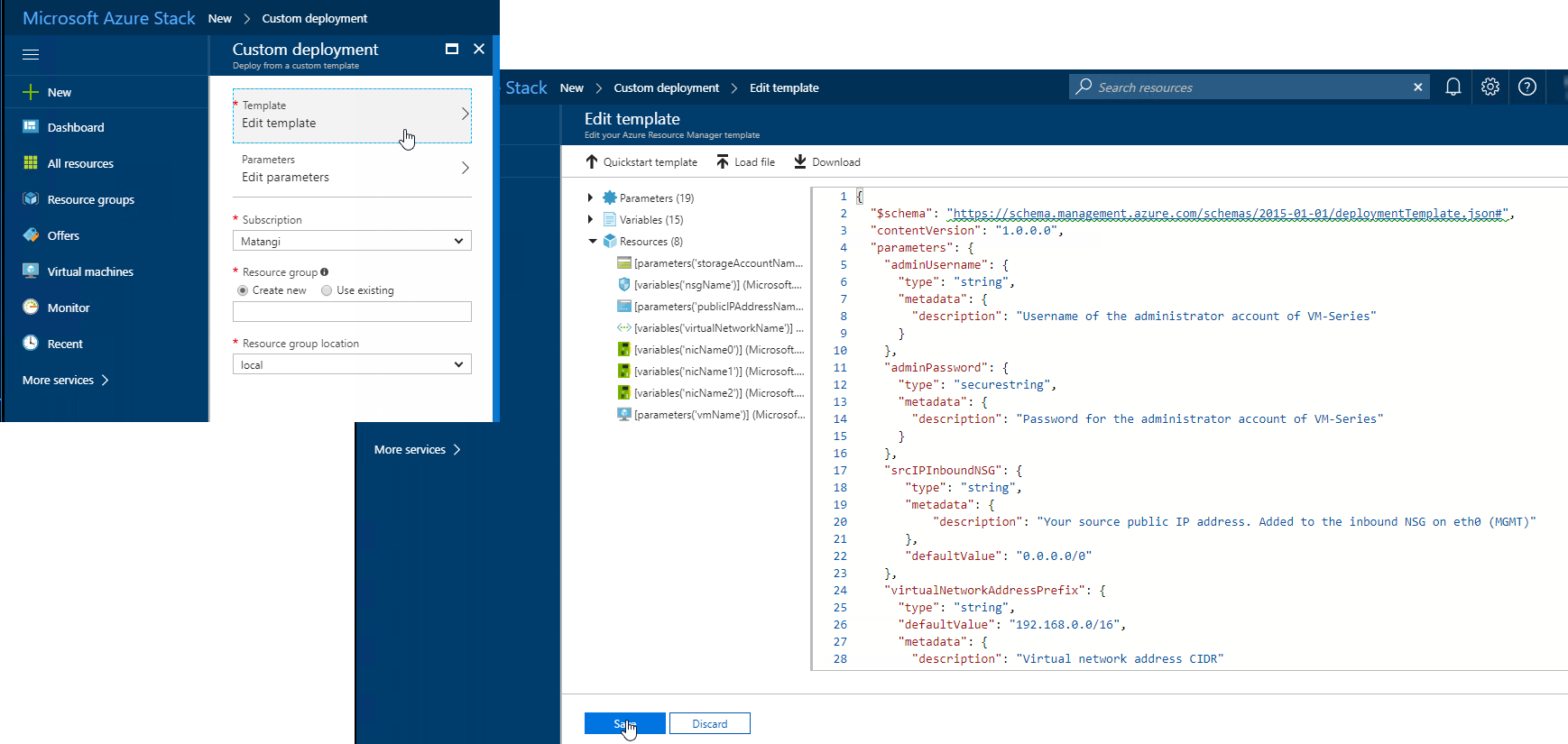
- Edit template, delete all existing content in the template, and paste the JSON template contents you copied earlier andSave.
![]()
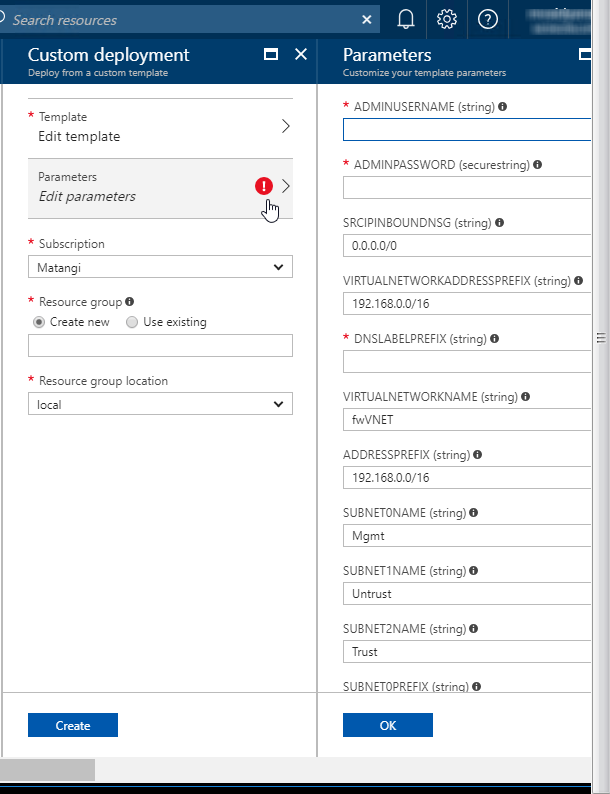
- Edit parameters, enter the values for the required parameters and modify the defaults if you need to, then click OK.
![]()
- Choose the Subscription you want to use, and then click OK.
- Choose an existing Resource Group that is empty or create a new one, and click OK.
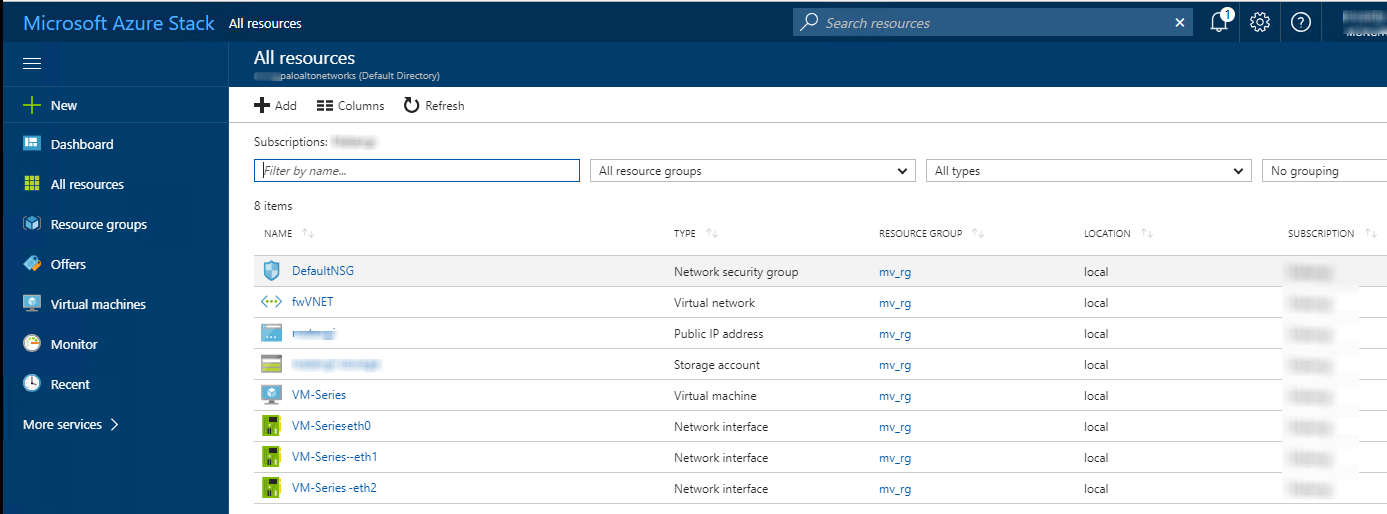
- Click Create. A new tile on the dashboard displays the progress of the template deployment.
![]()
Next Steps:- Log in to the web interface of the firewall.Using a secure connection (https) from your web browser, log in to the DNS name for the firewall. Enter the username/password you defined earlier. You will see a certificate warning; that is okay. Continue to the web page.Activate the licenses on the VM-Series firewall.
- On the firewall web interface, select DeviceLicenses and select Activate feature using authentication code.
- Enter the capacity auth-code that you registered on the support portal. The firewall will connect to the update server (updates.paloaltonetworks.com), and download the license and reboot automatically.
- Log back in to the web interface on the Dashboard, confirm that a valid Serial# displays.The VM Mode displays as Microsoft Azure.If the term Unknown displays, it means the device is not licensed. To view traffic logs on the firewall, you must install a valid capacity license.