Deploy VM-Series on Azure Stack Edge
Table of Contents
10.2
Expand all | Collapse all
-
- VM-Series Deployments
- VM-Series in High Availability
- Enable Jumbo Frames on the VM-Series Firewall
- Hypervisor Assigned MAC Addresses
- Custom PAN-OS Metrics Published for Monitoring
- Interface Used for Accessing External Services on the VM-Series Firewall
- PacketMMAP and DPDK Driver Support
- Enable NUMA Performance Optimization on the VM-Series
- Enable ZRAM on the VM-Series Firewall
-
- VM-Series Firewall Licensing
- Create a Support Account
- Serial Number and CPU ID Format for the VM-Series Firewall
- Use Panorama-Based Software Firewall License Management
-
- Maximum Limits Based on Tier and Memory
- Activate Credits
- Create a Deployment Profile
- Activate the Deployment Profile
- Manage a Deployment Profile
- Register the VM-Series Firewall (Software NGFW Credits)
- Provision Panorama
- Migrate Panorama to a Software NGFW License
- Transfer Credits
- Renew Your Software NGFW Credits
- Amend and Extend a Credit Pool
- Deactivate License (Software NGFW Credits)
- Delicense Ungracefully Terminated Firewalls
- Set the Number of Licensed vCPUs
- Customize Dataplane Cores
- Migrate a Firewall to a Flexible VM-Series License
-
- Generate Your OAuth Client Credentials
- Manage Deployment Profiles Using the Licensing API
- Create a Deployment Profile Using the Licensing API
- Update a Deployment Profile Using the Licensing API
- Get Serial Numbers Associated with an Authcode Using the API
- Deactivate a VM-Series Firewall Using the API
- What Happens When Licenses Expire?
-
- Supported Deployments on VMware vSphere Hypervisor (ESXi)
-
- Plan the Interfaces for the VM-Series for ESXi
- Provision the VM-Series Firewall on an ESXi Server
- Perform Initial Configuration on the VM-Series on ESXi
- Add Additional Disk Space to the VM-Series Firewall
- Use VMware Tools on the VM-Series Firewall on ESXi and vCloud Air
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Use the VM-Series CLI to Swap the Management Interface on ESXi
-
-
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (North-South)
- Components of the VM-Series Firewall on NSX-T (North-South)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Deploy the VM-Series Firewall
- Direct Traffic to the VM-Series Firewall
- Apply Security Policy to the VM-Series Firewall on NSX-T
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Extend Security Policy from NSX-V to NSX-T
-
- Components of the VM-Series Firewall on NSX-T (East-West)
- VM-Series Firewall on NSX-T (East-West) Integration
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (East-West)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Add a Service Chain
- Direct Traffic to the VM-Series Firewall
- Apply Security Policies to the VM-Series Firewall on NSX-T (East-West)
- Use vMotion to Move the VM-Series Firewall Between Hosts
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Create Dynamic Address Groups
- Create Dynamic Address Group Membership Criteria
- Generate Steering Policy
- Generate Steering Rules
- Delete a Service Definition from Panorama
- Migrate from VM-Series on NSX-T Operation to Security Centric Deployment
- Extend Security Policy from NSX-V to NSX-T
- Use In-Place Migration to Move Your VM-Series from NSX-V to NSX-T
-
-
- Deployments Supported on AWS
-
- Planning Worksheet for the VM-Series in the AWS VPC
- Launch the VM-Series Firewall on AWS
- Launch the VM-Series Firewall on AWS Outpost
- Create a Custom Amazon Machine Image (AMI)
- Encrypt EBS Volume for the VM-Series Firewall on AWS
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable CloudWatch Monitoring on the VM-Series Firewall
- VM-Series Firewall Startup and Health Logs on AWS
- Simplified Onboarding of VM-Series Firewall on AWS
-
- AWS Shared VPC Monitoring
- Use Case: Secure the EC2 Instances in the AWS Cloud
- Use Case: Use Dynamic Address Groups to Secure New EC2 Instances within the VPC
-
-
- What Components Does the VM-Series Auto Scaling Template for AWS (v2.0) Leverage?
- How Does the VM-Series Auto Scaling Template for AWS (v2.0 and v2.1) Enable Dynamic Scaling?
- Plan the VM-Series Auto Scaling Template for AWS (v2.0 and v2.1)
- Customize the Firewall Template Before Launch (v2.0 and v2.1)
- Launch the VM-Series Auto Scaling Template for AWS (v2.0)
- SQS Messaging Between the Application Template and Firewall Template
- Stack Update with VM-Series Auto Scaling Template for AWS (v2.0)
- Modify Administrative Account and Update Stack (v2.0)
-
- Launch the Firewall Template (v2.1)
- Launch the Application Template (v2.1)
- Create a Custom Amazon Machine Image (v2.1)
- VM-Series Auto Scaling Template Cleanup (v2.1)
- SQS Messaging Between the Application Template and Firewall Template (v2.1)
- Stack Update with VM-Series Auto Scaling Template for AWS (v2.1)
- Modify Administrative Account (v2.1)
- Change Scaling Parameters and CloudWatch Metrics (v2.1)
-
-
- Intelligent Traffic Offload
-
- Deployments Supported on Azure
- Deploy the VM-Series Firewall from the Azure Marketplace (Solution Template)
- Simplified Onboarding of VM-Series Firewall on Azure
- Deploy the VM-Series Firewall from the Azure China Marketplace (Solution Template)
- Deploy the VM-Series with the Azure Gateway Load Balancer
- Create a Custom VM-Series Image for Azure
- Deploy the VM-Series Firewall on Azure Stack
- Deploy the VM-Series Firewall on Azure Stack HCI
- Deploy VM-Series on Azure Stack Edge
- Enable Azure Application Insights on the VM-Series Firewall
- Set up Active/Passive HA on Azure
- Use the ARM Template to Deploy the VM-Series Firewall
-
- About the VM-Series Firewall on Google Cloud Platform
- Supported Deployments on Google Cloud Platform
- Prepare to Set Up VM-Series Firewalls on Google Public Cloud
- Create a Custom VM-Series Firewall Image for Google Cloud Platform
-
- Deploy the VM-Series Firewall from Google Cloud Platform Marketplace
- Management Interface Swap for Google Cloud Platform Load Balancing
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable Google Stackdriver Monitoring on the VM Series Firewall
- Enable VM Monitoring to Track VM Changes on Google Cloud Platform (GCP)
- Use Dynamic Address Groups to Secure Instances Within the VPC
- Use Custom Templates or the gcloud CLI to Deploy the VM-Series Firewall
-
- Prepare Your ACI Environment for Integration
-
-
- Create a Virtual Router and Security Zone
- Configure the Network Interfaces
- Configure a Static Default Route
- Create Address Objects for the EPGs
- Create Security Policy Rules
- Create a VLAN Pool and Domain
- Configure an Interface Policy for LLDP and LACP for East-West Traffic
- Establish the Connection Between the Firewall and ACI Fabric
- Create a VRF and Bridge Domain
- Create an L4-L7 Device
- Create a Policy-Based Redirect
- Create and Apply a Service Graph Template
-
- Create a VLAN Pool and External Routed Domain
- Configure an Interface Policy for LLDP and LACP for North-South Traffic
- Create an External Routed Network
- Configure Subnets to Advertise to the External Firewall
- Create an Outbound Contract
- Create an Inbound Web Contract
- Apply Outbound and Inbound Contracts to the EPGs
- Create a Virtual Router and Security Zone for North-South Traffic
- Configure the Network Interfaces
- Configure Route Redistribution and OSPF
- Configure NAT for External Connections
-
-
- Choose a Bootstrap Method
- VM-Series Firewall Bootstrap Workflow
- Bootstrap Package
- Bootstrap Configuration Files
- Generate the VM Auth Key on Panorama
- Create the bootstrap.xml File
- Prepare the Licenses for Bootstrapping
- Prepare the Bootstrap Package
- Bootstrap the VM-Series Firewall on AWS
- Bootstrap the VM-Series Firewall on Azure
- Bootstrap the VM-Series Firewall on Azure Stack HCI
- Bootstrap the VM-Series Firewall on Google Cloud Platform
- Verify Bootstrap Completion
- Bootstrap Errors
Deploy VM-Series on Azure Stack Edge
Secure 5G traffic within Azure Stack Edge using VM-Series firewalls.
VM-Series can now secure 5G traffic within Microsoft Azure Stack Edge. The Microsoft
Azure Stack Edge is a purpose-built
hardware-as-a-service that allows you to run workloads while gaining actionable
insights at the edge of the network, where data originates. Azure Stack Edge will
host Azure 5G Core network functions that will help the enterprise edge applications
connect either to other break-out applications or to the internet. With Palo Alto
Networks best in class 5G Security, Azure customers can now protect their 5G
connected enterprise applications using VM-Series firewalls.
See Azure Stack Edge for more information on the Azure
Stack Edge box. For the VM-Series offer on Azure Stack Edge, see VM-Series Next-Gen Firewall Edge Azure
Application.
Security Challenges in 5G and Edge Deployments
5G and edge-deployed networks have transformed enterprises and industries. These
deployments use next generation mobile technology, which guarantees reliable
networks, however they lack security against a complex and evolving threat
landscapes.
These security challenges include:
- Greater number of connected and BYOD devices increases attack vectors.
- Limited control and visibility into user traffic.
- Internet-based attacks, or from compromised management systems.
- Open source and exposed APIs.
- Resource theft.
- Network configuration attacks.
- DoS (Denial of Services) and spoofing attacks on 5G protocols.
- Limited visibility into subscribers and equipment.
- Untrusted applications and services.
Benefits of VM-Series Integration with Azure Stack Edge
5G-Native Security with VM-Series
VM-Series deployments with Azure Stack Edge provide enterprise grade security
paradigms to 5G deployments. These deployments use the following security
features:
- Realtime correlation of threats to 5G end-user application traffic. Provides security controls and enforcement to inspect tunneled end-user traffic to enterprise applications.
- Containerized 5G security. Provides for secure, highly distributed cloud-native 5G networks.
- 5G MEC security. Enables industry digitization with MEC (multi-access edge computing ), complementing 5G access networks.
The VM-Series deployment on Azure Stack Edge for enterprise 5G security protects
edge applications within the following areas:
- RAN security. SCTP stateful inspection to protect Azure 5GC from the RAN.
- GTP-U Security. Tunnel content inspection to protect the payload end-user, edge application traffic within the GTP-U tunnel.
- Internet Perimeter. Secure Inbound Outbound traffic into the remote edge, break-out application, and internet traffic at the perimeter.
The image below illustrates how VM-Series firewalls are used in Azure Stack Edge
deployments:
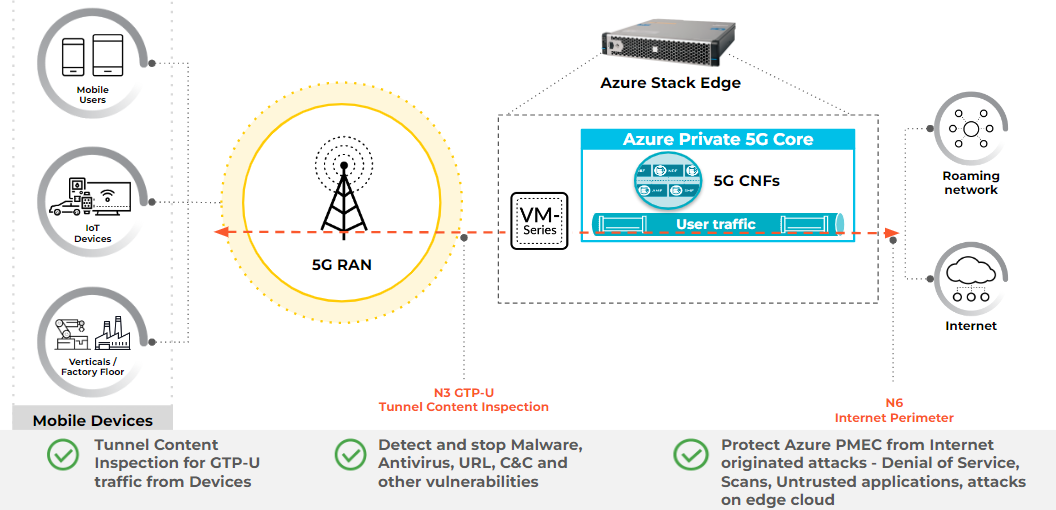
Deploy the VM-Series Firewall on Azure Stack Edge
You can deploy the VM-Series firewall on Azure Stack Edge to secure
inter-subnet traffic between applications in a multitier architecture and
outbound traffic from servers within your Azure Stack Edge deployment.
The NAT appliance is required because in Azure Stack
deployments you can't assign a public IP address to a nonprimary interface
or a virtual machine, such as the VM-Series firewall. This NAT appliance
receives inbound traffic and forwards it to the VM-Series firewall.
To deploy the VM-Series firewall on Azure Stack Edge:
- Configure a virtual switch for the management port. If Azure Private 5G Core is being coinstalled, the virtual switch for the management port will be configured as part of that installation. If you're not installing Azure Private 5G Core, use the instructions provided below.
- Add a virtual switch for the management port, for example, port 2.. For more information, see Configure virtual switches.Configure the switch as a Compute virtual switch. You don't need to configure any Kubernetes nodes or service IP addresses.Create and register an Azure Network Function Manager device resource. After performing steps 1-2, three virtual switches are available: management, LAN, and WAN. On the Azure Stack Edge GPU, LAN is port 5, and WAN is port 6. On Azure Stack Edge Pro 2, LAN is port 3 and WAN is port 4.Configure the required virtual networks on the LAN and WAN virtual switches. Add a virtual network for the firewall’s untrust1 interface on the LAN virtual switch using a nonzero VLAN ID.Add another virtual network for the firewall's untrust2 interface on the WAN virtual switch using a nonzero VLAN ID.Create a User Assigned Managed Identity with permission for Microsoft.HybridNetwork/devices/join/action on your Azure Stack Edge. The Azure Portal user will need either Owner or User Access administrator permissions on the ASE Resource Group to be able to create user assigned managed identity.Navigate to the Azure Portal Marketplace and select the version for your VM-Series firewall.In the Azure Portal Marketplace, search for VM-Series Palo Alto.Select the VM-Series Palo Alto Networks NGFW Edge Azure Application option. Choose eight CPU or the 16 CPU option from the Plan drop-down.Click Create. When you create the VM-Series firewall, the installation process guides you through the steps to configure basic information, manage details, configure network settings and the firewall. Once you complete these steps, review and create the firewall.Configure Basic information, including:
- Subscription. Select the subscription used for the Azure Stack Edge when it was deployed.Resource Group. Select a resource group specific to this deployment. If one does not exist, click Create new and use a name similar to ase-vm-series-p5gc.Region. Refer to the Microsoft Technical Team for the appropriate region.Select the Azure Network Function Manager device on which the VNF will be deployed.Application Name. Enter a name for the application.Managed Resource Group. This resource group retains the resources required by the managed app. Use the default value for this field.The Azure Portal user needs at least User Access administrator permission on the ASE Resource Group to configure the role assignment.Create a custom role with permissions for Microsoft.HybridNetwork/devices/join/action, unless one already exists. For more information, see Create or update Azure custom roles using the Azure portal.. Use the information provided in step 1 for the Microsoft.HybridNetwork/devices/join/action; the Clone a role method isn't appropriate in this context.Configure Managed Identify details. Select a managed identity. If one does not exist, create one using the portal. Ensure the managed identity uses the correct subscription and resource group.Create a user-assigned managed identity, unless one already exists. For more information, see Create a user-assigned managed identity.Assign the user-assigned managed identity the custom role from above at the scope of the Azure Stack Edge, or the Resource Group or Subscription containing the Azure Stack Edge. For more information, see User-assigned managed identity.Continue creating the VM-Series firewall using the wizard. Configure Network settings. Configure the IP addresses of the management, LAN, and WAN interfaces, along with any VLANs used in the deployment.The table below shows the interfaces and how they map to the Azure Stack Edge device and Azure Private 5G Core. Use this table to create reference designs for VM-Series deployments on Azure Stack Edge and Azure Private 5G Core.
Interface Short Name (NFM) Interface Full Name (VM-Series managed app ) Interface Name in Panorama Interface Name mapped with security zone Name Azure Stack Edge Physical port Description mgmt Management interface Management Management 1,2,3,4 This is the firewall’s management Internet Protocol, from which it communicates with Panorama in the cloud. mgmt-inspect Management interface for inspection Ethernet 1/1 trust-access 1,2,3,4 This is the IP address for providing firewall functionality to the OAM network. lan1 First LAN Interface Ethernet 1/2 trust-access 5 This is used to communicate with the RAN’s N2 interface or N2 and N3 interface. lan2 Second LAN Interface Ethernet 1/3 untrust-n2 5 This is used to communicate with the RAN’s N2 interface or N2 and N3 interface. lan3 Third LAN Interface Ethernet 1/4 untrust-n3 5 This can be used to communicate with the RAN’s N3 interface independently. wan1 First WAN Interface Ethernet 1/5 trust-core 6 This is used to communicate with the Azure Private 5G Core N6 interface. wan2 Second WAN Interface Ethernet 1/6 untrust-mgmt 6 This is used to communicate with the internet on behalf of the OAM network. wan3 3rd WAN Interface Ethernet 1/7 untrust-n6 6 This is used to communicate with the internet or other data networks on behalf of the UEs. Complete the VM-Series configuration:- Enter the VM name representing the VM-Series firewall. Use a meaningful description.Enter Custom Data. This important information is used for cloud-init parameters. It provides the VM-Series firewall with licensing information and the IP address of the Panorama server used for communication.Within the init-cfg.txt file, the Custom data format resembles the following (replace bold text with appropriate values):type=dhcp-client; hostname=panfw001; tplname=ngfw-stack; dgname=ngfw-device; op-command-modes=jumbo-frame; tplname=ngfw-stack; dgname=ngfw-device; op-command-modes=jumbo-frame;panorama-server=1.2.3.4; vm-auth-key=123456789123456; authcodes= panorama-server=1.2.3.4; vm-auth-key=123456789123456; authcodes=D1234567; timezone=UTC+3Use the vm-auth-key generated on Panorama using the command request bootstrap vm-auth-key generate lifetime 24. Use a timezone with a UTC offset value that reflects the location of the Azure Stack Edge box. You can also check the Azure Stack Edge box local time and ensure the same is reflected in UTC offset format within the custom data.Review and create the VM-Series firewall. Verify that all the settings are correct, then deploy the VM-Series firewall.After deploying the firewall on the Azure Stack Edge device verify its connection to Panorama. Check the status using the CLI of the VM-Series NGFW:admin@pa-azr-ase> show panorama-statusPanorama Server 1 : <panorama ip> Connected : yes
