Create Data-Center-to-Internet Decryption Policy Rules
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- What Is a Data Center Best Practice Security Policy?
- Why Do I Need a Data Center Best Practice Security Policy?
- Data Center Best Practice Methodology
- How Do I Deploy a Data Center Best Practice Security Policy?
- How to Assess Your Data Center
-
- Create the Data Center Best Practice Antivirus Profile
- Create the Data Center Best Practice Anti-Spyware Profile
- Create the Data Center Best Practice Vulnerability Protection Profile
- Create the Data Center Best Practice File Blocking Profile
- Create the Data Center Best Practice WildFire Analysis Profile
- Use Cortex XDR Agent to Protect Data Center Endpoints
- Create Data Center Traffic Block Rules
- Order the Data Center Security Policy Rulebase
- Maintain the Data Center Best Practice Rulebase
- Use Palo Alto Networks Assessment and Review Tools
End-of-Life (EoL)
Create Data-Center-to-Internet Decryption Policy Rules
Create rules that decrypt update, certificate checking,
and any other traffic from data center servers to internet servers
so that you can inspect the traffic and protect your most valuable
assets against malware and other threats.
Create Decryption policy rules to provide
visibility into traffic from data center servers to the internet.
Decrypt all traffic from data center servers to the internet. The
only accounts initiating connections to the internet from inside
the data center are service accounts and most of this traffic pertains
to software updates, so there are no privacy issues to consider.
It’s important to decrypt and inspect this traffic because if an update
server is compromised, data center servers could download malware
and propagate it through the software update process. Inspecting
the traffic and applying the best practice threat prevention profiles
protects your data center against malware that could otherwise be
downloaded from a legitimate update server, using a legitimate application.
In Create Data-Center-to-Internet Application Allow Rules,
we created Security policy rules that allow data center servers
to initiate connections with internet update servers to update operating
system software, DNS, NTP, and to check certificates. Here we create
analogous Decryption policy rules to decrypt the traffic that the
update Security policy rules allow.
Do not decrypt
traffic to certificate revocation servers (online responders). Online
Certificate Status Protocol (OCSP) traffic usually uses HTTP, so
the traffic is cleartext and not encrypted. In addition, SSL Forward
Proxy Decryption may break the update process because the firewall acts
as a man-in-the-middle proxy and replaces the client certificate
with a proxy certificate, which the OCSP responder may not accept
as valid.
The decryption policy rules share some common
elements in regard to these traffic flows:
- When you create a Decryption policy rule, the objective is to decrypt traffic so that a Security policy rule can examine it and allow or block it based on policy. To accomplish that, the Decryption policy rule must use the same source zone(s) and user(s) as the analogous security policy rule, and the same destination zone and address (often defined by a dynamic address group so that as you add or remove servers, you can update the firewall without a commit operation). Defining the same source and destination in the Security policy and in the Decryption policy applies both policies to the same traffic.
- The Action for all of these rules is decrypt.
- For each rule, configure decryption logging and log forwarding. Log as much decryption traffic as your firewall resources permit.
- All of these decryption rules use the Best Practice data center decryption profile shown in Create the Data Center Best Practice Decryption Profiles.
In
many cases, the Decryption policy rule examples include a custom
URL category (ObjectsCustom
ObjectsURL Category)
to narrow the scope of traffic to decrypt. Each Decryption policy
rule uses the same custom URL category (and source and destination)
as the analogous Security policy rule so that the Decryption and
Security policies apply to exactly the same traffic. The combination
of App-ID and a custom URL category enables the firewall to decrypt
only the traffic the rule allows, which saves processing cycles
by not decrypting traffic that the firewall will block. (Decryption
must happen before Security policy rule evaluation.)
- Decrypt traffic between data center servers and
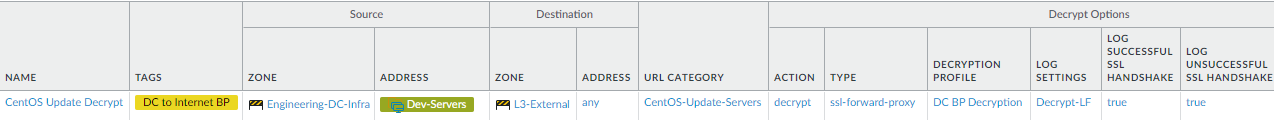
software update servers on the internet.This rule shows how to decrypt data center server software update traffic to provide visibility into threats that may be present on internet update servers so the firewall can block them. This example decrypts allowed traffic between data center servers and CentOS update servers on the internet based on the analogous application allow rule we created in Create Data-Center-to-Internet Application Allow Rules.
![]() To create this rule:
To create this rule:- Specify the same source and destination as in the analogous Security policy rule. In this case, the source is the Dev-Servers dynamic address group in the Engineering-DC-Infra zone, and the destination is the internet (L3-External zone).
- Specify the same custom URL category as in the analogous Security policy rule ( CentOS-Update-Servers) to narrow the scope of decryption to only traffic that the rule allows so that the firewall doesn’t waste cycles decrypting traffic that it will drop.
- On the Options tab, set the Action to Decrypt and the decryption Type to SSL Forward Proxy. Apply the data center best practice Decryption Profile to apply SSL Forward Proxy and SSL Protocol Settings to the traffic.
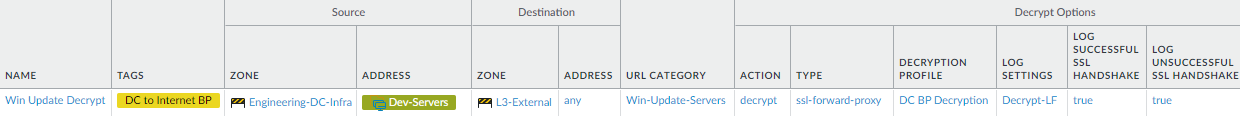
Create a similar Decryption policy rule for the allowed data center traffic of each group of data center servers that needs to connect to internet update servers, based on the same source and destination, and same custom URL category, as the analogous Security policy rule. For example, the Decryption policy rule for data center servers that need to communicate with Microsoft Windows update servers, based on the analogous Security policy rule, looks like this:![]()
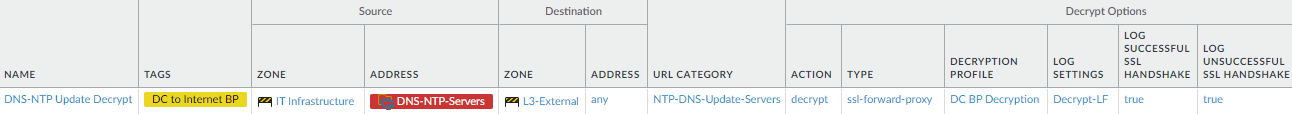
- Decrypt traffic between data center servers and NTP and
DNS update servers on the internet.This rule shows how to decrypt data center server NTP and DNS update traffic to provide visibility into threats that may be present on these internet servers so the firewall can block them. This example decrypts allowed traffic based on the analogous application allow rule we created in Create Data-Center-to-Internet Application Allow Rules.
![]() To create this rule:
To create this rule:- Specify the same source and destination as in the analogous Security policy rule. In this case, the source is the DNS-NTP-Servers dynamic address group in the IT Infrastructure zone, and the destination is the internet ( L3-External zone).
- Specify the same custom URL category as in the analogous Security policy rule ( NTP-DNS-Update-Servers) to narrow the scope of decryption to only traffic that the rule allows.
- On the Options tab, set the Action to Decrypt and the decryption Type to SSL Forward Proxy. Apply the data center best practice Decryption Profile to apply SSL Forward Proxy and SSL Protocol Settings to the traffic.