Create the Data Center Best Practice Vulnerability Protection Profile
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- What Is a Data Center Best Practice Security Policy?
- Why Do I Need a Data Center Best Practice Security Policy?
- Data Center Best Practice Methodology
- How Do I Deploy a Data Center Best Practice Security Policy?
- How to Assess Your Data Center
-
- Create the Data Center Best Practice Antivirus Profile
- Create the Data Center Best Practice Anti-Spyware Profile
- Create the Data Center Best Practice Vulnerability Protection Profile
- Create the Data Center Best Practice File Blocking Profile
- Create the Data Center Best Practice WildFire Analysis Profile
- Use Cortex XDR Agent to Protect Data Center Endpoints
- Create Data Center Traffic Block Rules
- Order the Data Center Security Policy Rulebase
- Maintain the Data Center Best Practice Rulebase
- Use Palo Alto Networks Assessment and Review Tools
End-of-Life (EoL)
Create the Data Center Best Practice Vulnerability Protection Profile
Protect your data center from attacks such as buffer
overflows, illegal code execution, and other attempts to exploit vulnerabilities.
Attach a Vulnerability Protection profile to all
security policy rules that allow traffic. The Vulnerability Protection
profile protects against buffer overflows, illegal code execution,
and other attempts to exploit client- and server-side vulnerabilities
to breach and move laterally through the data center network.
Clone the predefined strict Vulnerability Protection profile.
To ensure availability for business-critical applications, take safe transition steps as
you move from your current state to the best practice profile. For
the best practice profile, for each rule except simple-client-informational and simple-server-informational,
double-click the Rule Name and change Packet
Capture from disable to single-packet to
enable packet capture (PCAP) for each rule so
you can track down the source of potential attacks. Don’t change
the rest of the settings. Download content updates automatically
and install them as soon as possible so that the signature set is
always up-to-date.
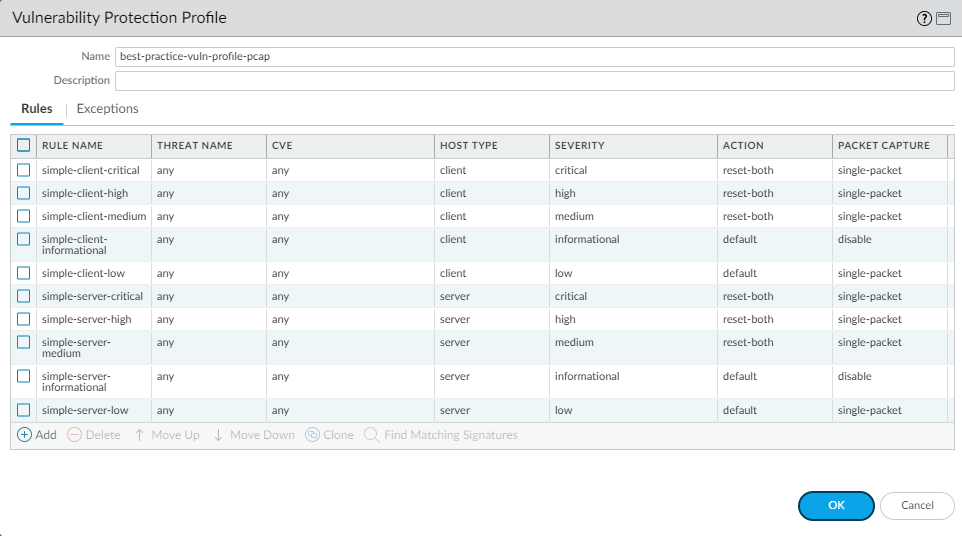
Don’t enable PCAP for informational activity because it generates
a relatively high volume of that traffic and it’s not particularly
useful compared to potential threats. Apply extended PCAP (as opposed
to single PCAP) to high-value traffic to which you apply the alert Action.
Apply PCAP using the same logic you use to decide what traffic to
log—take PCAPs of the traffic you log. Apply single PCAP to traffic
you block. The default number of packets that extended PCAP records
and sends to the management plane is five packets, which is the
recommended value. In most cases, capturing five packets provides
enough information to analyze the threat. If too much PCAP traffic
is sent to the management plane, then capturing more than five packets
may result in dropping PCAPs.
The reason to attach the best practice Vulnerability Protection
profile to all security policy rules that allow traffic is because if
you don’t have strict vulnerability protection, attackers can leverage
client- and server-side vulnerabilities to compromise the data center.
For example:
- Intra data center traffic—A strict Vulnerability Protection profile, along with the Antivirus profile, helps prevent attackers from using exploits to leverage vulnerabilities and spread malware and hacking tools laterally between servers inside the data center network.
- Traffic from the data center to the internet—Vulnerability protection helps prevent infected data center servers from compromising internet servers.
- Traffic from the internet to the data center—A strict Vulnerability Protection profile blocks attempts to compromise data center servers with server-side vulnerabilities. If a server is compromised, vulnerability protection helps prevent the infected server from serving exploits to clients, isolating the infection and protecting your partners and customers from watering hole attacks. Vulnerability protection also stops brute force attacks using the Block IP action. When brute force attack signatures trigger the action, the firewall blocks the attacker’s IP address for a configured period of time. If the brute force attack resumes after the time period expires, the signatures again trigger the blocking action. The brute force attack may continue, but it never succeeds.
