Create Intra-Data-Center Decryption Policy Rules
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- What Is a Data Center Best Practice Security Policy?
- Why Do I Need a Data Center Best Practice Security Policy?
- Data Center Best Practice Methodology
- How Do I Deploy a Data Center Best Practice Security Policy?
- How to Assess Your Data Center
-
- Create the Data Center Best Practice Antivirus Profile
- Create the Data Center Best Practice Anti-Spyware Profile
- Create the Data Center Best Practice Vulnerability Protection Profile
- Create the Data Center Best Practice File Blocking Profile
- Create the Data Center Best Practice WildFire Analysis Profile
- Use Cortex XDR Agent to Protect Data Center Endpoints
- Create Data Center Traffic Block Rules
- Order the Data Center Security Policy Rulebase
- Maintain the Data Center Best Practice Rulebase
- Use Palo Alto Networks Assessment and Review Tools
End-of-Life (EoL)
Create Intra-Data-Center Decryption Policy Rules
Create rules that decrypt east-west traffic between data
center servers so you can inspect the traffic and protect your most
valuable resources against malware and other threats.
Why decrypt traffic inside the data center?
After all, there are no users and the data center is a safe environment
deep inside the secure network. But nothing could be farther from
the truth. The data center is a perfect place for attackers to hide
precisely because many people think the data center is safe and
don’t look there. But the same basic tenet that’s true in the rest
of the network holds true in the data center: you can’t protect
yourself against what you can’t see. Decrypt encrypted data center
traffic so that the firewall can inspect traffic, control access,
make threats visible, and protect your valuable assets.
Some
data center traffic is unencrypted (cleartext). Don’t enable decryption
on cleartext flows because there is nothing to decrypt.
In Create Intra-Data-Center Application Allow Rules,
we created Security policy rules that allow servers involved with
Finance Department applications that are in different application
tiers to communicate with each other. Here we create analogous Decryption
policy rules to decrypt the traffic that those rules allow.
For
each rule, configure decryption logging and log forwarding.
Log as much decryption traffic as your firewall resources permit.
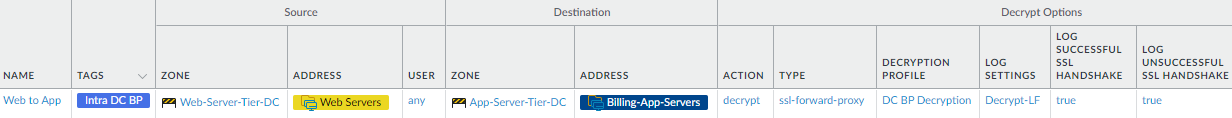
- Decrypt finance application traffic between the
web server tier and the application server tier.This rule decrypts the traffic flowing between the web server tier and the application server tier for the Finance department’s billing servers so that the firewall can see the traffic and protect the servers in each tier against potential threats.
![]() To create this rule:
To create this rule:- Specify the same source and destination as in the analogous Security policy rule. In this example, the source is the Web-Servers dynamic address group in the Web-Server-Tier-DC zone, and the destination is the Billing-App-Servers in the App-Server-Tier-DC zone.
- On the Options tab, set the Action to Decrypt and the decryption Type to SSL Forward Proxy. Apply the data center best practice Decryption Profile to apply SSL Forward Proxy and SSL Protocol Settings to the traffic.
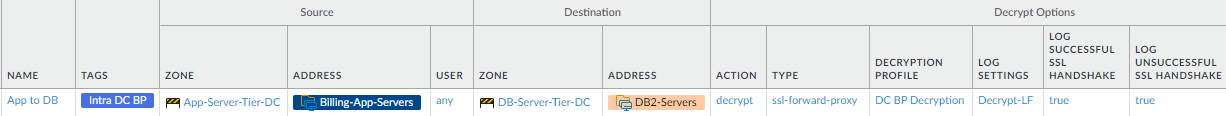
- Decrypt finance application traffic between the application
server tier and the database server tier.This rule decrypts the traffic flowing between the application server tier and the database server tier for the Finance department’s billing servers so that the firewall can see the traffic and protect the servers in each tier against potential threats.
![]() To create this rule:
To create this rule:- Specify the same source and destination as in the analogous Security policy rule. In this example, the source is the Billing-App-Servers dynamic address group in the App-Server-Tier-DC zone, and the destination is the DB2-Servers in the DB-Server-Tier-DC zone.
- On the Options tab, set the Action to Decrypt and the decryption Type to SSL Forward Proxy. Apply the data center best practice Decryption Profile to apply SSL Forward Proxy and SSL Protocol Settings to the traffic.