Data-Center-to-Internet Traffic Policies
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- What Is a Data Center Best Practice Security Policy?
- Why Do I Need a Data Center Best Practice Security Policy?
- Data Center Best Practice Methodology
- How Do I Deploy a Data Center Best Practice Security Policy?
- How to Assess Your Data Center
-
- Create the Data Center Best Practice Antivirus Profile
- Create the Data Center Best Practice Anti-Spyware Profile
- Create the Data Center Best Practice Vulnerability Protection Profile
- Create the Data Center Best Practice File Blocking Profile
- Create the Data Center Best Practice WildFire Analysis Profile
- Use Cortex XDR Agent to Protect Data Center Endpoints
- Create Data Center Traffic Block Rules
- Order the Data Center Security Policy Rulebase
- Maintain the Data Center Best Practice Rulebase
- Use Palo Alto Networks Assessment and Review Tools
End-of-Life (EoL)
Data-Center-to-Internet Traffic Policies
Configure Security policy and Decryption policy
for traffic from the data center to the internet.
- Create data-center-to-internet allow rules to
protect connections to external servers. Data center servers may obtain software updates or certificate status from servers on the internet. The greatest risk is connecting to the wrong server. Create strict allow rules for updates to limit the reachable external servers and the allowed applications (on default ports only). This prevents infected data center servers from phoning home and prevents data exfiltration using legitimate applications such as FTP, HTTP, or DNS on non-standard ports. In addition, use the File Blocking profile’s Direction control to block outbound update files so you only allow downloading for software update files.For each rule, apply best practice Security profiles and configure Log at Session End on the Actions tab.Work with engineering and other groups that update software to log and analyze web browsing sessions to define the URLs to which developers connect for updates.
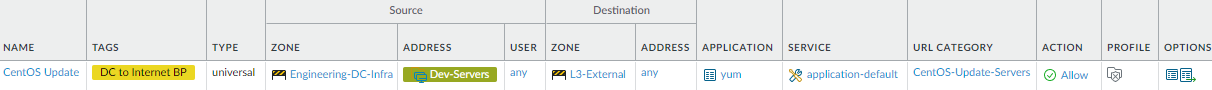
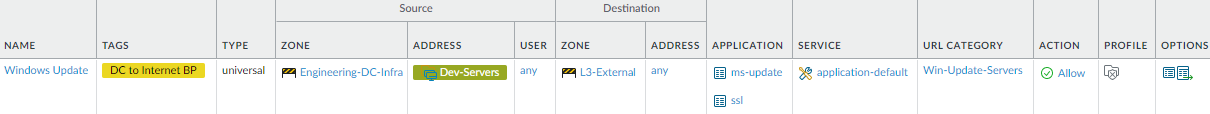
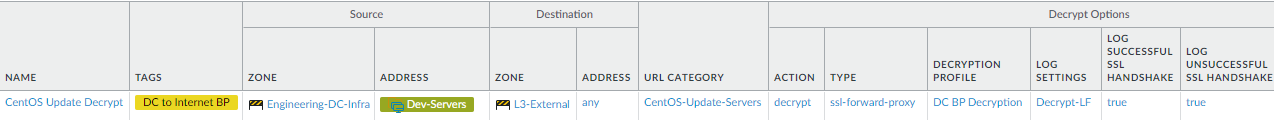
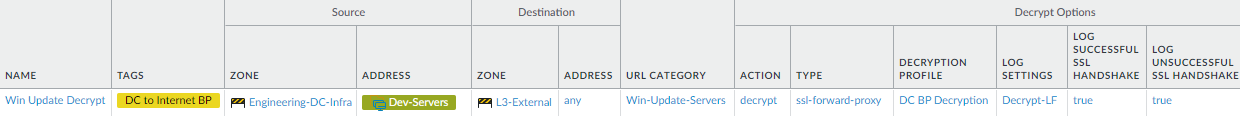
- These examples allow engineering servers to communicate with CentOS update servers (CentOS-Update-Servers custom URL Category) using the yum application and with Microsoft update servers (Win-Update-Servers custom URL Category) using the ms-update application (you must also allow ssl because ms-update has a dependency on SSL).
![]()
![]()
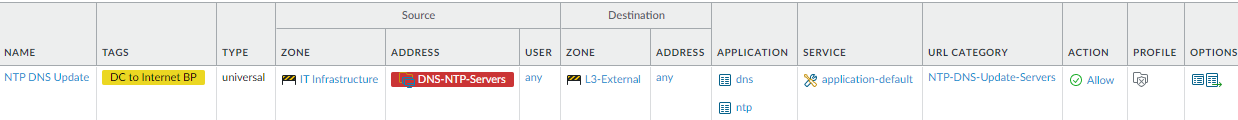
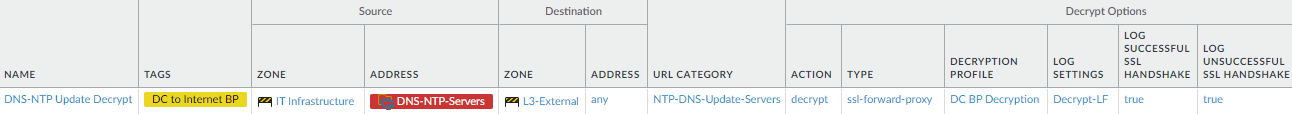
- Allow access to DNS and NTP updates (NTP DNS Update Servers custom URL Category).Block access to external DNS servers at the internet gateway to prevent DNS traffic from going out on the internet to public servers. Allow access only to sanctioned DNS servers and use the DNS Security service to prevent connections to malicious DNS servers.
![]()
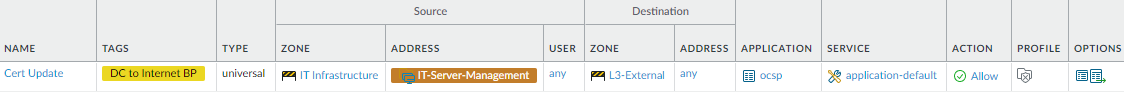
- Allow connecting to an internet Online Certificate Status Protocol (OCSP) Responder to check the revocation status of authentication certificates and ensure they are valid. When you configure a certificate profile on the firewall, set up CRL status verification as a fallback method for OCSP in case the OCSP Responder is unreachable.
![]()
- Create data-center-to-internet Decryption policy
rules to decrypt the traffic allowed in the preceding Security policy
rules. A compromised update server could download malware and propagate it through the software update process, so decrypting traffic to gain visibility is critical. Because only service accounts initiate update traffic and update traffic has no personal or sensitive information, there are no privacy issues.Don’t decrypt traffic to OCSP certificate revocation servers because the traffic usually uses HTTP, so it’s not encrypted. In addition, SSL Forward Proxy decryption may break the update process because the firewall acts as a proxy and replaces the client certificate with a proxy certificate, which the OCSP responder may not accept as valid.
- Decrypt traffic between data center and update servers. These two examples decrypt the CentOS and Windows update traffic allowed by the analogous Security policy rules in the preceding step.
![]()
![]()
- Decrypt traffic between data center servers and NTP and DNS update servers. This example decrypts the update traffic allowed by the analogous Security policy rule in the preceding step.
![]()