Create Internet-to-Data-Center Decryption Policy Rules
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- What Is a Data Center Best Practice Security Policy?
- Why Do I Need a Data Center Best Practice Security Policy?
- Data Center Best Practice Methodology
- How Do I Deploy a Data Center Best Practice Security Policy?
- How to Assess Your Data Center
-
- Create the Data Center Best Practice Antivirus Profile
- Create the Data Center Best Practice Anti-Spyware Profile
- Create the Data Center Best Practice Vulnerability Protection Profile
- Create the Data Center Best Practice File Blocking Profile
- Create the Data Center Best Practice WildFire Analysis Profile
- Use Cortex XDR Agent to Protect Data Center Endpoints
- Create Data Center Traffic Block Rules
- Order the Data Center Security Policy Rulebase
- Maintain the Data Center Best Practice Rulebase
- Use Palo Alto Networks Assessment and Review Tools
End-of-Life (EoL)
Create Internet-to-Data-Center Decryption Policy Rules
Create rules that decrypt partner, vendor, customer,
and other third-party traffic from the internet to the data center
so you can inspect the traffic and protect your most valuable assets
against malware and other threats.
Create Decryption policy rules to provide
visibility into traffic that enters the data center from the internet
so that you can apply Security policy to that traffic. When you
create a Security policy rule that allows access to a set of data
center servers, create a decryption policy rule to decrypt that
traffic. In Create Internet-to-Data-Center Application Allow Rules,
we created a Security policy rule that allows access from internet
to the web server tier in the data center, using only allowed applications.
Here we create a decryption policy rule ( PoliciesDecryption) to decrypt the
traffic that this rule allows.
To decrypt traffic so that
a Security policy rule can examine it and allow or block it based
on policy, the Decryption policy rule must use the same source zone(s)
and user(s) as the analogous security policy rule, and the same
destination zone and address (often defined by a dynamic address group so that as you add
or remove servers, you can update the firewall without a commit
operation). Defining the same source and destination in the Security
policy and in the Decryption policy applies both policies to the
same traffic.
The decryption rule uses the Best Practice
data center decryption profile shown in Create
the Data Center Best Practice Decryption Profiles.
For
each rule, configure decryption logging and log forwarding.
Log as much decryption traffic as your firewall resources permit.
- Decrypt allowed traffic from the internet to data
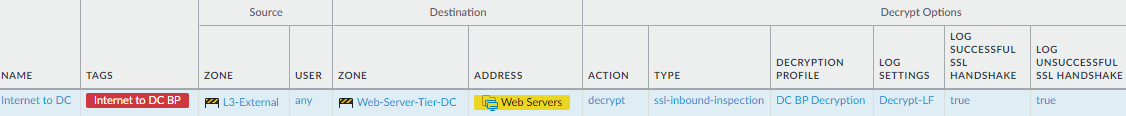
center web servers.This rule shows how to decrypt traffic from externally initiated connections to the data center. For example, the application allow rules we created enable external traffic access to the data center web serves, using only certain applications. To protect the data center web servers, decrypt traffic so the firewall can inspect it and apply threat prevention profiles.
![]() To create this rule:
To create this rule:- Specify the same source and destination as in the analogous security policy rule. In this case, the Source is the L3-External zone, and the Destination is the servers specified in the Web-Servers dynamic address group in the Web-Server-Tier-DC zone.
- On the Options tab, set the Action to Decrypt and the decryption Type to SSL Inbound Inspection. Specify the server certificate for the web servers and apply the data center best practice Decryption Profile to apply SSL Inbound Inspection and SSL Protocol Settings to the traffic.
- Create similar Decryption policy rules for traffic from the internet to any other server group, if such access is allowed, and for the other applications you allow.