Create Data Center Traffic Block Rules
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- What Is a Data Center Best Practice Security Policy?
- Why Do I Need a Data Center Best Practice Security Policy?
- Data Center Best Practice Methodology
- How Do I Deploy a Data Center Best Practice Security Policy?
- How to Assess Your Data Center
-
- Create the Data Center Best Practice Antivirus Profile
- Create the Data Center Best Practice Anti-Spyware Profile
- Create the Data Center Best Practice Vulnerability Protection Profile
- Create the Data Center Best Practice File Blocking Profile
- Create the Data Center Best Practice WildFire Analysis Profile
- Use Cortex XDR Agent to Protect Data Center Endpoints
- Create Data Center Traffic Block Rules
- Order the Data Center Security Policy Rulebase
- Maintain the Data Center Best Practice Rulebase
- Use Palo Alto Networks Assessment and Review Tools
End-of-Life (EoL)
Create Data Center Traffic Block Rules
Block traffic you know you don’t want in your data center
and use block rules to discover unknown applications and users.
Before you create the application allow rules
for the four data center traffic flows, create blocking and logging
rules to block applications you don’t use in the data center, block
known bad applications, and discover applications that you may not
know are on your network. Logging blocked traffic provides information
about potential attacks to help you investigate them.
When
you discover unknown applications, decide whether they should be
allowed or whether they represent potential threats. If these rules
discover applications that should be allowed, tune the application
allow rules accordingly. If these rules discover applications that
are not legitimate, they may represent potential threats and you
can investigate them using the log information. Don’t apply Security
Profiles to block rules because the traffic they control never gets
into your network.
If you discover unknown applications
that are internal proprietary applications or other types of legitimate
applications, create a custom application for each unknown
application so that you can identify it and apply security policy to
it.
Order
the Data Center Security Policy Rulebase shows you how to
order these rules with all of the other rules we create for the
four data center traffic flows so that no rule shadows another rule.
To apply consistent security policy across multiple
data centers, you can reuse templates and template stacks so
that the same policies apply to every data center. The templates
use variables to apply device-specific values such as IP addresses,
FQDNs, etc., while maintaining a global security policy and reducing
the number of templates and template stacks you need to manage.
- Block
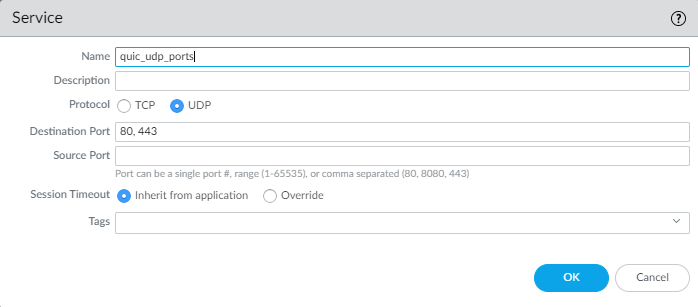
Quick UDP Internet Connections (QUIC) protocol.Chrome and some other browsers establish sessions using QUIC instead of TLS, but QUIC uses proprietary encryption that the firewall can’t decrypt, so potentially dangerous traffic may enter the network as encrypted traffic. Blocking QUIC forces the browser to fall back to TLS and enables the firewall to decrypt the traffic.Create a Security policy rule to block QUIC on its UDP service ports (80 and 443) and create a separate rule to block the QUIC application. For the rule that blocks UDP ports 80 and 443, create a Service (ObjectsServices) that includes UDP ports 80 and 443:
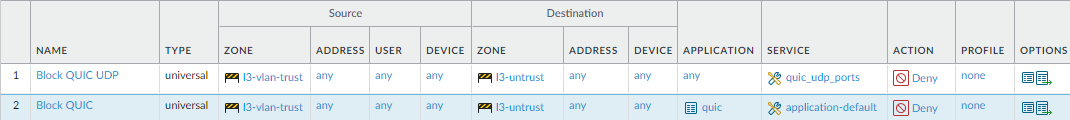
![]() Use the Service to specify the UDP ports to block for QUIC. In the second rule, block the QUIC application so that the first two rules in your rulebase block QUIC:
Use the Service to specify the UDP ports to block for QUIC. In the second rule, block the QUIC application so that the first two rules in your rulebase block QUIC:![]()
- Block all applications from user zones on the application-default
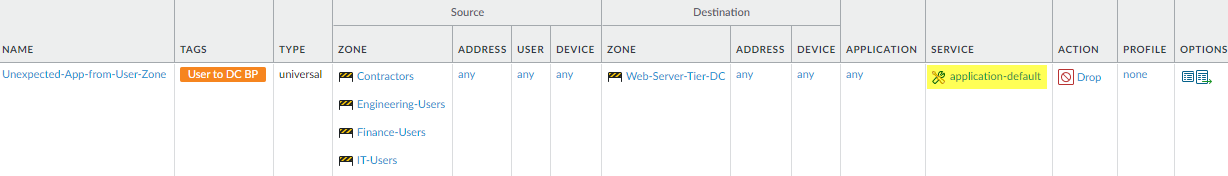
port to identify unexpected applications.This rule discovers applications that users are attempting to use and that you didn’t know were running on your data center. Monitor traffic that matches this rule to determine if it’s a potential threat or if you need to modify your allow rules to enable access to the application. Be sure to place this rule after rules that allow traffic or this rule will block traffic that you intend to allow.The rule shown after this rule is similar to this rule, except that it applies to traffic from any source, not just traffic from user zones. The reason for creating separate rules is that violations of the user-zone rule may indicate that you’re blocking a legitimate application which some users need to conduct business, so you may need to modify a rule to allow the application for a particular set of users. Violations from non-user zones may indicate a change in an application or a potential attack. Creating a separate rule for the rest of the traffic enables you to view separate logs for user traffic and for all other traffic attempting to enter the data center, which makes it easier to investigate and respond to a potential issue.This rule must precede the next rule, which applies to all traffic so that you can log and monitor attempts to use unexpected applications on application-default ports regardless of the source after you first log violations from user zones.
![]() To create this rule:
To create this rule:- The Source Zone includes all user zones and users (your deployment may have more user zones than shown in the example).
- The Destination Zone is the data center web server tier (Web-Server-Tier-DC) at the data center perimeter.
- Set the Application to any and the Service to application-default so that the rule applies to all applications running on their standard ports.
- Set the Action to Drop to silently drop the traffic without sending a signal to the client or server.
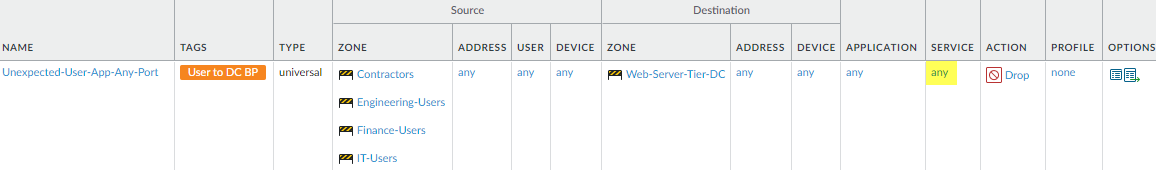
- Block all applications from user zones on any port to
identify applications running where they shouldn’t run.This rule identifies legitimate, known applications that users are attempting to run on non-standard ports as well as unknown applications for which you may need to create custom applications. Investigate the source of any traffic that matches this rule to ensure that you aren’t allowing unknown-tcp, unknown-udp, or non-syn-tcp traffic. Be sure to place this rule after rules that allow traffic or this rule will block traffic that you intend to allow.We will also create a different block rule later in this section that is similar to this rule (Unexpected-App-from-Any-Zone), except that it applies to traffic from any source, not just traffic from user zones. The reason for creating separate rules is that violations of the user-zone rule may indicate that a legitimate application which some users need to conduct business has not been designed correctly, so you may need to modify the application. Creating a separate rule for the rest of the traffic enables you to view separate logs for user traffic and for all other traffic attempting to enter the data center, which makes it easier to investigate and respond to a potential issue.
![]() To create this rule:
To create this rule:- The Source Zone includes all user zones and users (your deployment may have more user zones than shown in the example).
- The Destination Zone is the data center web server tier (Web-Server-Tier-DC) at the data center perimeter.
- Set the Application to any and the Service to any so that the rule applies to all applications running on any port.
- Set the Action to Drop to silently drop the traffic without sending a signal to the client or server.
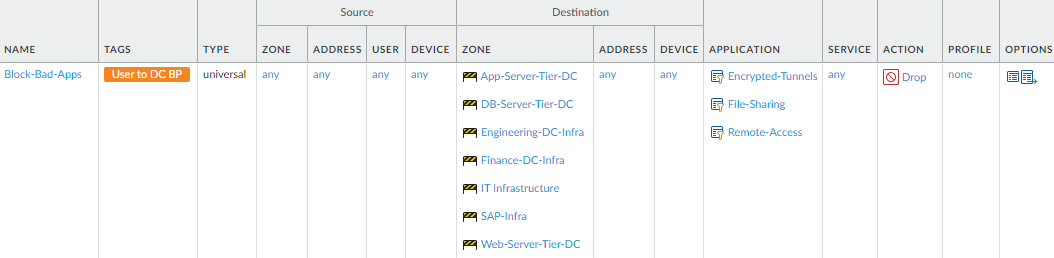
- Block applications designed to evade or bypass security,
that attackers commonly exploit, or that are not necessary in the
data center.This rule protects the data center from applications that you know you don’t want on your network. Although the goal of a best practice security policy is positive enforcement using application allow rules, explicitly blocking and logging potentially dangerous application activity such as unsanctioned file sharing applications, remote access applications, or encrypted tunnels, provides visibility into and information about potential attacks. Even after you develop a solid application allow list, keep this application blocking rule in the rulebase because logs from attempted violations help with investigations into potential attacks.Use this rule to block only applications you never want in your data center.
![]() To create this rule:
To create this rule:- Set the Source Zone, Address, User, and Device to any because you’re blocking applications that nobody should be allowed to use in the data center.
- Specify all data center zones in the Destination Zone to protect all data center servers from bad applications.
- Create an application filter for each type (category) of application you want to block and specify any additional applications. This example includes application filters for encrypted tunnels, remote access, and file sharing. Block applications that you don’t use in the data center to reduce the attack surface by eliminating unnecessary applications, which also reduces risk. The advantage of using application filters instead of application groups or listing individual applications is that filters are automatically updated, so you don’t need to maintain them as new applications come out.
- Set the Service to any to catch undesired applications on non-standard ports as well as default ports.
- Set the Action to Drop to silently drop the traffic without sending a signal to the client or server.
The application filters shown in the example rule are not a comprehensive list. Evaluate the application list you create based on How to Assess Your Data Center and add the applications you don’t want to allow to this rule. Place this blocking rule after the allow rules to allow exceptions to the rule. For example, IT needs to use remote access applications to manage data center devices, so you must allow that use of remote access applications before you block remote access applications for all other users. Another example is that you may sanction one or two file sharing applications in allow rules that precede this block rule, and the application filter in this rule then blocks all the rest of those applications. If there are sets of applications or individual applications that you never want on your network and for which there are no exceptions, you can create a specific block rule to block just those applications and place it at the top of the rulebase, above the application allow rules. However, if you do this, you must be certain that none of the blocked applications have legitimate business uses because your users will not be able to access them. - Block all applications from any zone on the application-default
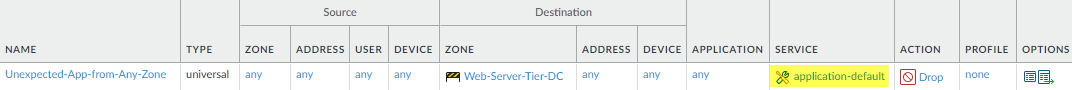
port to identify unexpected applications.This rule discovers applications from any zone that you didn’t know were running on your data center. Violations of this rule may indicate that an application has changed or may indicate a potential threat. Monitor traffic that matches this rule to determine if it’s a potential threat or if you need to modify your application allow rules. Be sure to place this rule after rules that allow traffic or this rule will block traffic that you intend to allow, and after the rule in Step 1 so that it doesn’t catch traffic from user zones.
![]() To create this rule:
To create this rule:- The Source is any to cover all of the rest of the traffic attempting to enter the data center (the rule in Step 1 blocks and identifies unexpected user applications before traffic hits this rule).
- The Destination Zone is the data center web server tier (Web-Server-Tier-DC) at the data center perimeter.
- Set the Application to any and the Service to application-default so that the rule applies to all applications running on their standard ports.
- Set the Action to Drop to silently drop the traffic without sending a signal to the client or server.
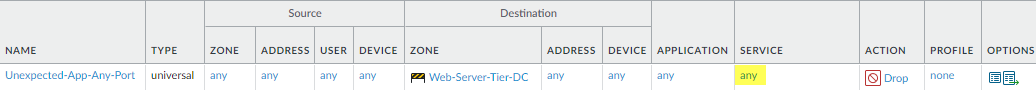
- Block all applications from any zone on any port to identify
applications running where they shouldn’t run.This rule identifies legitimate, known applications attempting to run on non-standard ports as well as unknown applications for which you may need to create custom applications. Investigate the source of any traffic that matches this rule to ensure that you aren’t allowing unknown-tcp, unknown-udp, or non-syn-tcp traffic. Be sure to place this rule after rules that allow traffic or this rule will block traffic that you intend to allow, and after the preceding rule so that it doesn’t catch traffic from user zones.
![]() To create this rule, use the same settings as in the rule Unexpected-App-from-User-Zone, except instead of specifying the user zones in the source, specify any zone to cover all of the rest of the traffic attempting to enter the data center, and set the Service to any to cover non-standard ports.
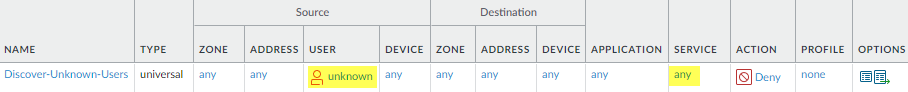
To create this rule, use the same settings as in the rule Unexpected-App-from-User-Zone, except instead of specifying the user zones in the source, specify any zone to cover all of the rest of the traffic attempting to enter the data center, and set the Service to any to cover non-standard ports. - Discover unknown users attempting to run any application,
on any port.This rule identifies gaps in User-ID coverage by finding unknown users. It also identifies compromised or embedded devices in the user community that are trying to access your data center. (Embedded devices have no user interface, for example, printers, card readers, and cameras, but adversaries can compromise these devices and use them in an attack.)
![]() This rule is almost the same as the interzone-default rule that prevents communication between zones (unless another rule allows the traffic), except instead of dropping traffic from all users, it only drops traffic from unknown users. This enables you to log rule matches separately and more easily investigate unknown users attempting to access your data center.
This rule is almost the same as the interzone-default rule that prevents communication between zones (unless another rule allows the traffic), except instead of dropping traffic from all users, it only drops traffic from unknown users. This enables you to log rule matches separately and more easily investigate unknown users attempting to access your data center.