What Components Does the VM-Series Auto Scaling Template for AWS (v2.0) Leverage?
Table of Contents
Expand all | Collapse all
-
- VM-Series Deployments
- VM-Series in High Availability
- Enable Jumbo Frames on the VM-Series Firewall
- Hypervisor Assigned MAC Addresses
- Custom PAN-OS Metrics Published for Monitoring
- Interface Used for Accessing External Services on the VM-Series Firewall
- PacketMMAP and DPDK Driver Support
-
- VM-Series Firewall Licensing
- Create a Support Account
- Serial Number and CPU ID Format for the VM-Series Firewall
-
- Activate Credits
- Transfer Credits
- Create a Deployment Profile
- Manage a Deployment Profile
- Provision Panorama
- Migrate Panorama to a Software NGFW License
- Renew Your Software NGFW Credits
- Amend and Extend a Credit Pool
- Deactivate License (Software NGFW Credits)
- Delicense Ungracefully Terminated Firewalls
- Create and Apply a Subscription-Only Auth Code
- Migrate to a Flexible VM-Series License
-
- Generate Your OAuth Client Credentials
- Manage Deployment Profiles Using the Licensing API
- Create a Deployment Profile Using the Licensing API
- Update a Deployment Profile Using the Licensing API
- Get Serial Numbers Associated with an Authcode Using the API
- Deactivate a VM-Series Firewall Using the API
- Use Panorama-Based Software Firewall License Management
- What Happens When Licenses Expire?
- Install a Device Certificate on the VM-Series Firewall
-
- Supported Deployments on VMware vSphere Hypervisor (ESXi)
-
- Plan the Interfaces for the VM-Series for ESXi
- Provision the VM-Series Firewall on an ESXi Server
- Perform Initial Configuration on the VM-Series on ESXi
- Add Additional Disk Space to the VM-Series Firewall
- Use VMware Tools on the VM-Series Firewall on ESXi and vCloud Air
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Use the VM-Series CLI to Swap the Management Interface on ESXi
-
-
- VM-Series Firewall for NSX-V Deployment Checklist
- Install the VMware NSX Plugin
- Apply Security Policies to the VM-Series Firewall
- Steer Traffic from Guests that are not Running VMware Tools
- Add a New Host to Your NSX-V Deployment
- Dynamically Quarantine Infected Guests
- Migrate Operations-Centric Configuration to Security-Centric Configuration
- Use Case: Shared Compute Infrastructure and Shared Security Policies
- Use Case: Shared Security Policies on Dedicated Compute Infrastructure
- Dynamic Address Groups—Information Relay from NSX-V Manager to Panorama
-
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (North-South)
- Components of the VM-Series Firewall on NSX-T (North-South)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Deploy the VM-Series Firewall
- Direct Traffic to the VM-Series Firewall
- Apply Security Policy to the VM-Series Firewall on NSX-T
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Extend Security Policy from NSX-V to NSX-T
-
- Components of the VM-Series Firewall on NSX-T (East-West)
- VM-Series Firewall on NSX-T (East-West) Integration
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (East-West)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Add a Service Chain
- Direct Traffic to the VM-Series Firewall
- Apply Security Policies to the VM-Series Firewall on NSX-T (East-West)
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Extend Security Policy from NSX-V to NSX-T
- Use Migration Coordinator to Move Your VM-Series from NSX-V to NSX-T
-
-
- Deployments Supported on AWS
-
- Planning Worksheet for the VM-Series in the AWS VPC
- Launch the VM-Series Firewall on AWS
- Launch the VM-Series Firewall on AWS Outpost
- Create a Custom Amazon Machine Image (AMI)
- Encrypt EBS Volume for the VM-Series Firewall on AWS
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable CloudWatch Monitoring on the VM-Series Firewall
- VM-Series Firewall Startup and Health Logs on AWS
- Use Case: Secure the EC2 Instances in the AWS Cloud
- Use Case: Use Dynamic Address Groups to Secure New EC2 Instances within the VPC
-
-
- What Components Does the VM-Series Auto Scaling Template for AWS (v2.0) Leverage?
- How Does the VM-Series Auto Scaling Template for AWS (v2.0 and v2.1) Enable Dynamic Scaling?
- Plan the VM-Series Auto Scaling Template for AWS (v2.0 and v2.1)
- Customize the Firewall Template Before Launch (v2.0 and v2.1)
- Launch the VM-Series Auto Scaling Template for AWS (v2.0)
- SQS Messaging Between the Application Template and Firewall Template
- Stack Update with VM-Series Auto Scaling Template for AWS (v2.0)
- Modify Administrative Account and Update Stack (v2.0)
-
- Launch the Firewall Template (v2.1)
- Launch the Application Template (v2.1)
- Create a Custom Amazon Machine Image (v2.1)
- VM-Series Auto Scaling Template Cleanup (v2.1)
- SQS Messaging Between the Application Template and Firewall Template (v2.1)
- Stack Update with VM-Series Auto Scaling Template for AWS (v2.1)
- Modify Administrative Account (v2.1)
- Change Scaling Parameters and CloudWatch Metrics (v2.1)
-
-
- Enable the Use of a SCSI Controller
- Verify PCI-ID for Ordering of Network Interfaces on the VM-Series Firewall
-
- Deployments Supported on Azure
- Deploy the VM-Series Firewall from the Azure Marketplace (Solution Template)
- Deploy the VM-Series Firewall from the Azure China Marketplace (Solution Template)
- Deploy the VM-Series Firewall on Azure Stack
- Enable Azure Application Insights on the VM-Series Firewall
- Set up Active/Passive HA on Azure
- Use the ARM Template to Deploy the VM-Series Firewall
-
- About the VM-Series Firewall on Google Cloud Platform
- Supported Deployments on Google Cloud Platform
- Create a Custom VM-Series Firewall Image for Google Cloud Platform
- Prepare to Set Up VM-Series Firewalls on Google Public Cloud
-
- Deploy the VM-Series Firewall from Google Cloud Platform Marketplace
- Management Interface Swap for Google Cloud Platform Load Balancing
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable Google Stackdriver Monitoring on the VM Series Firewall
- Enable VM Monitoring to Track VM Changes on GCP
- Use Dynamic Address Groups to Secure Instances Within the VPC
- Locate VM-Series Firewall Images in the GCP Marketplace
-
- Prepare Your ACI Environment for Integration
-
-
- Create a Virtual Router and Security Zone
- Configure the Network Interfaces
- Configure a Static Default Route
- Create Address Objects for the EPGs
- Create Security Policy Rules
- Create a VLAN Pool and Domain
- Configure an Interface Policy for LLDP and LACP for East-West Traffic
- Establish the Connection Between the Firewall and ACI Fabric
- Create a VRF and Bridge Domain
- Create an L4-L7 Device
- Create a Policy-Based Redirect
- Create and Apply a Service Graph Template
-
- Create a VLAN Pool and External Routed Domain
- Configure an Interface Policy for LLDP and LACP for North-South Traffic
- Create an External Routed Network
- Configure Subnets to Advertise to the External Firewall
- Create an Outbound Contract
- Create an Inbound Web Contract
- Apply Outbound and Inbound Contracts to the EPGs
- Create a Virtual Router and Security Zone for North-South Traffic
- Configure the Network Interfaces
- Configure Route Redistribution and OSPF
- Configure NAT for External Connections
-
-
- Choose a Bootstrap Method
- VM-Series Firewall Bootstrap Workflow
- Bootstrap Package
- Bootstrap Configuration Files
- Generate the VM Auth Key on Panorama
- Create the bootstrap.xml File
- Prepare the Licenses for Bootstrapping
- Prepare the Bootstrap Package
- Bootstrap the VM-Series Firewall on AWS
- Bootstrap the VM-Series Firewall on Azure
- Bootstrap the VM-Series Firewall on Google Cloud Platform
- Verify Bootstrap Completion
- Bootstrap Errors
End-of-Life (EoL)
What Components Does the VM-Series Auto Scaling Template for AWS (v2.0) Leverage?
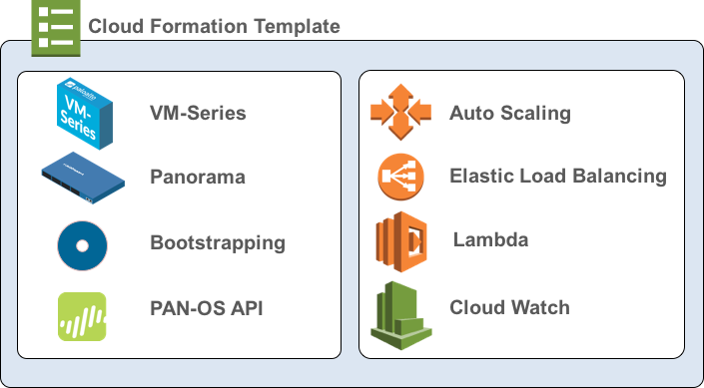
The VM-Series Auto Scaling template for AWS includes the following
building blocks:
Building Block | Description |
|---|---|
| Firewall template (Palo Alto Networks officially
supported template) | The firewall-v2.0.template deploys
a new VPC with subnets, route tables, an AWS NAT gateway, two Availability
Zones (AZs), and security groups required for routing traffic across
these AZs. This version 2.0 template also deploys an external ALB,
and an ASG with a VM-Series firewall in each AZ. Due to the
many variations in a production environment that includes but is
not limited to a specific number components, such as subnets, availability
zones, route tables, and security groups. You must deploy the firewall-v2.0.template in
a new VPC. VM-Series Auto Scaling template for AWS does
not deploy Panorama and Panorama is optional. Panorama provides
ease of policy management and central visibility. If you want to
use Panorama to manage the VM-Series firewalls that the solution
deploys, you can either use an M-Series appliance or Panorama virtual
appliance inside your corporate network or you can use a Panorama
virtual appliance on AWS. This solution includes an
AWS NAT gateway that the firewalls use to initiate outbound requests
for retrieving updates, connecting to Panorama, and publishing metrics
to AWS CloudWatch. |
| Application template (Community supported
template) | The application template deploys an NLB
and an ASG with a web server in each AZ. Because the NLB has a unique
IP address for each AZ and the NAT policy rule on the firewalls
must reference a single IP address, there is one ASG for each of
the two AZs. All firewalls in an ASG use an identical configuration. Version
2.0 of the auto scaling solution includes two application templates:
|
| Lambda functions | AWS Lambda provides robust, event-driven
automation without the need for complex orchestration software.
In the firewall-v2.0.template, AWS Lambda monitors
a Simple Queue Service (SQS) to learn about NLBs that publish to
the queue. When the Lambda function detects a new NLB, it creates
a new NAT policy rule and applies it to the VM-Series firewalls within
the ASG. The firewalls have a NAT policy rule for each application and
the firewalls use the NAT policy rule (that maps the port to NLB
IP address) to forward traffic to the NLB in front of the application
web servers. You need to create the Security policy
rule to allow or deny application traffic for your deployment. The
sample bootstrap.xml file does not include
any Security policy rules. You should use Panorama to centrally manage
your firewalls and simplify creating Security policy rules. There
are additional functions:
To learn more about the
Lambda functions, refer to http://paloaltonetworks-aws-autoscale-2-0.readthedocs.io/en/latest/ |
| Bootstrap files The bootstrap.xml
file provided in the GitHub repository is provided for testing and evaluation
only. For a production deployment, you must modify the sample credentials
in the bootstrap.xml prior to launch. | This solution requires the init-cfg.txt
file and the bootstrap.xml file so that the VM-Series firewall has
the basic configuration for handling traffic.
|
To deploy the solution, see Launch
the VM-Series Auto Scaling Template for AWS (v2.0).
