Remove Cloud Identity Agent Certificates
Table of Contents
Expand all | Collapse all
-
- Cloud Identity Engine Attributes
- Collect Custom Attributes with the Cloud Identity Engine
- View Directory Data
- Cloud Identity Engine User Context
- Create a Cloud Dynamic User Group
- Configure Third-Party Device-ID
- Configure an IP Tag Cloud Connection
- View Mappings and Tags
- Configure Dynamic Privilege Access in the Cloud Identity Engine
- Send Cortex XDR Risk Signals to Okta
- Configure SSF Okta Receiver as a Risk Connection
- Configure the Secrets Vault
-
- Set Up Password Authentication
-
- Configure Azure as an IdP in the Cloud Identity Engine
- Configure Okta as an IdP in the Cloud Identity Engine
- Configure PingOne as an IdP in the Cloud Identity Engine
- Configure PingFederate as an IdP in the Cloud Identity Engine
- Configure Google as an IdP in the Cloud Identity Engine
- Configure a SAML 2.0-Compliant IdP in the Cloud Identity Engine
- Set Up a Client Certificate
- Configure an OIDC Authentication Type
- Set Up an Authentication Profile
- Configure Cloud Identity Engine Authentication on the Firewall or Panorama
- Configure the Cloud Identity Engine as a Mapping Source on the Firewall or Panorama
- Configure Dynamic Privilege Access in the Cloud Identity Engine
- Get Help
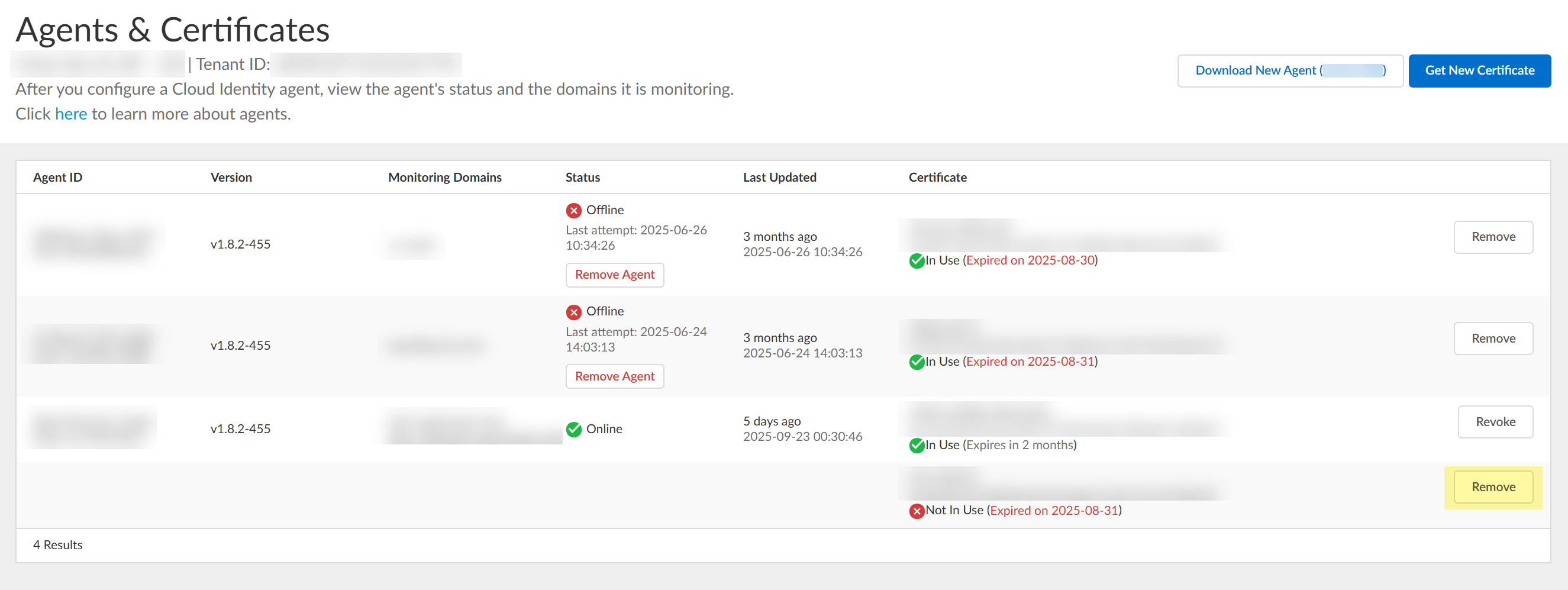
Remove Cloud Identity Agent Certificates
If the Cloud Identity agent’s certificate is compromised, remove the compromised
certificate and generate a new certificate.
- Log in to the hub and select Cloud Identity Engine.Select the tenant associated with the agent with the compromised certificate.From the Cloud Identity Engine app, select Agents & Certificates.Remove the certificate.
![]() Delete Obsolete Cloud Identity Agent Certificates to remove the previous certificate.Generate a new certificate to Authenticate the Agent and the Cloud Identity Engine and install it on the agent host.
Delete Obsolete Cloud Identity Agent Certificates to remove the previous certificate.Generate a new certificate to Authenticate the Agent and the Cloud Identity Engine and install it on the agent host.